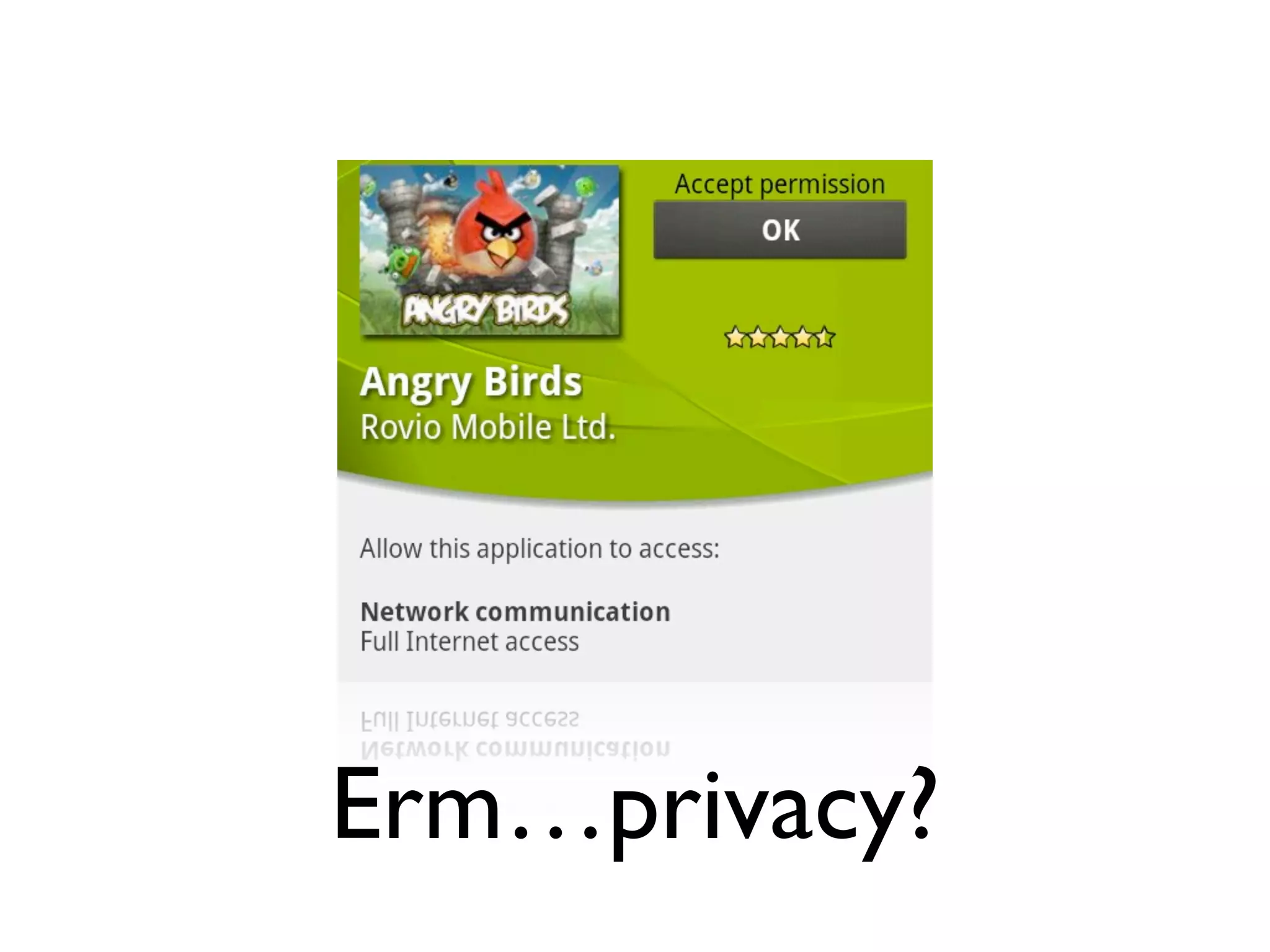
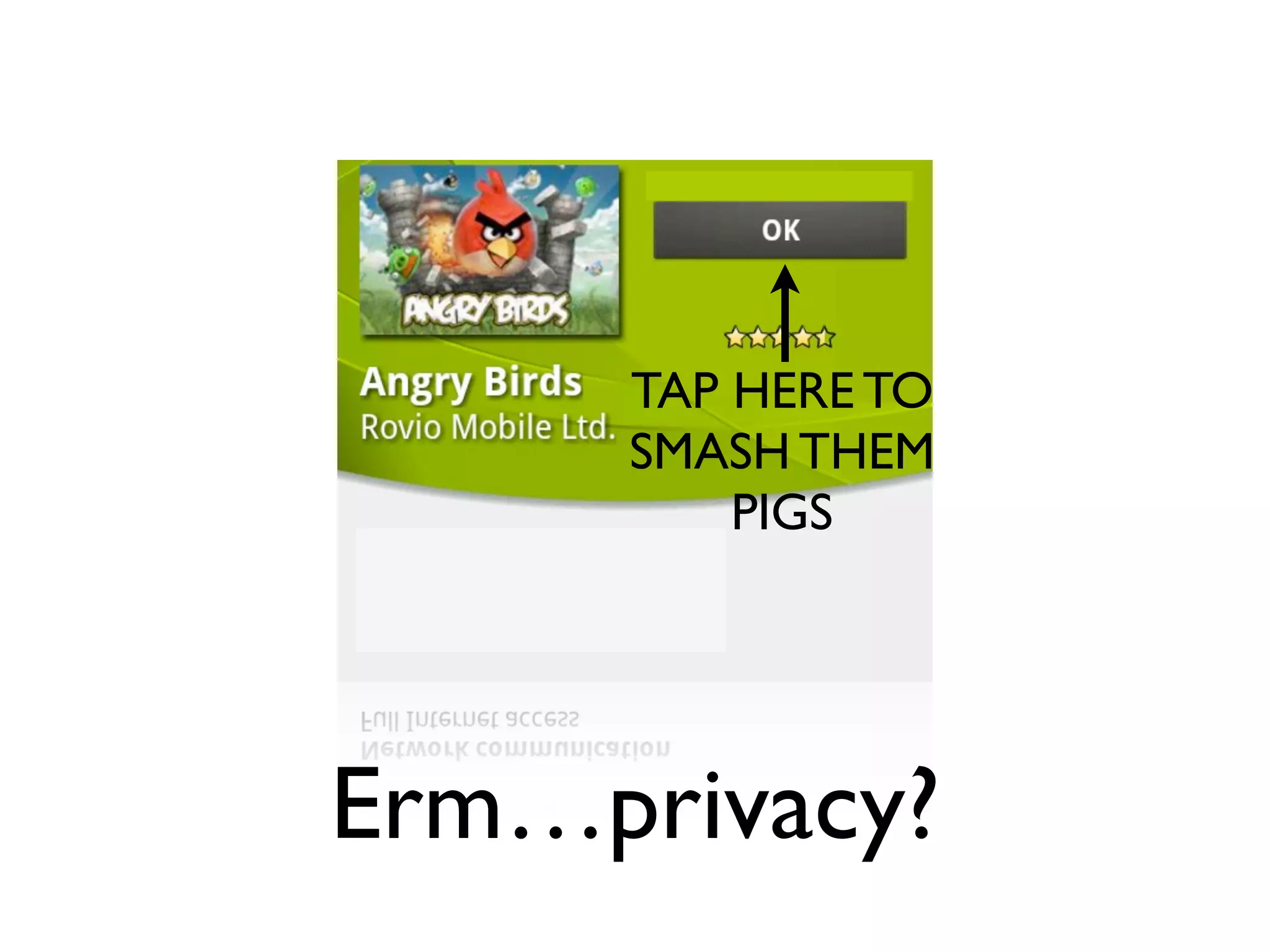
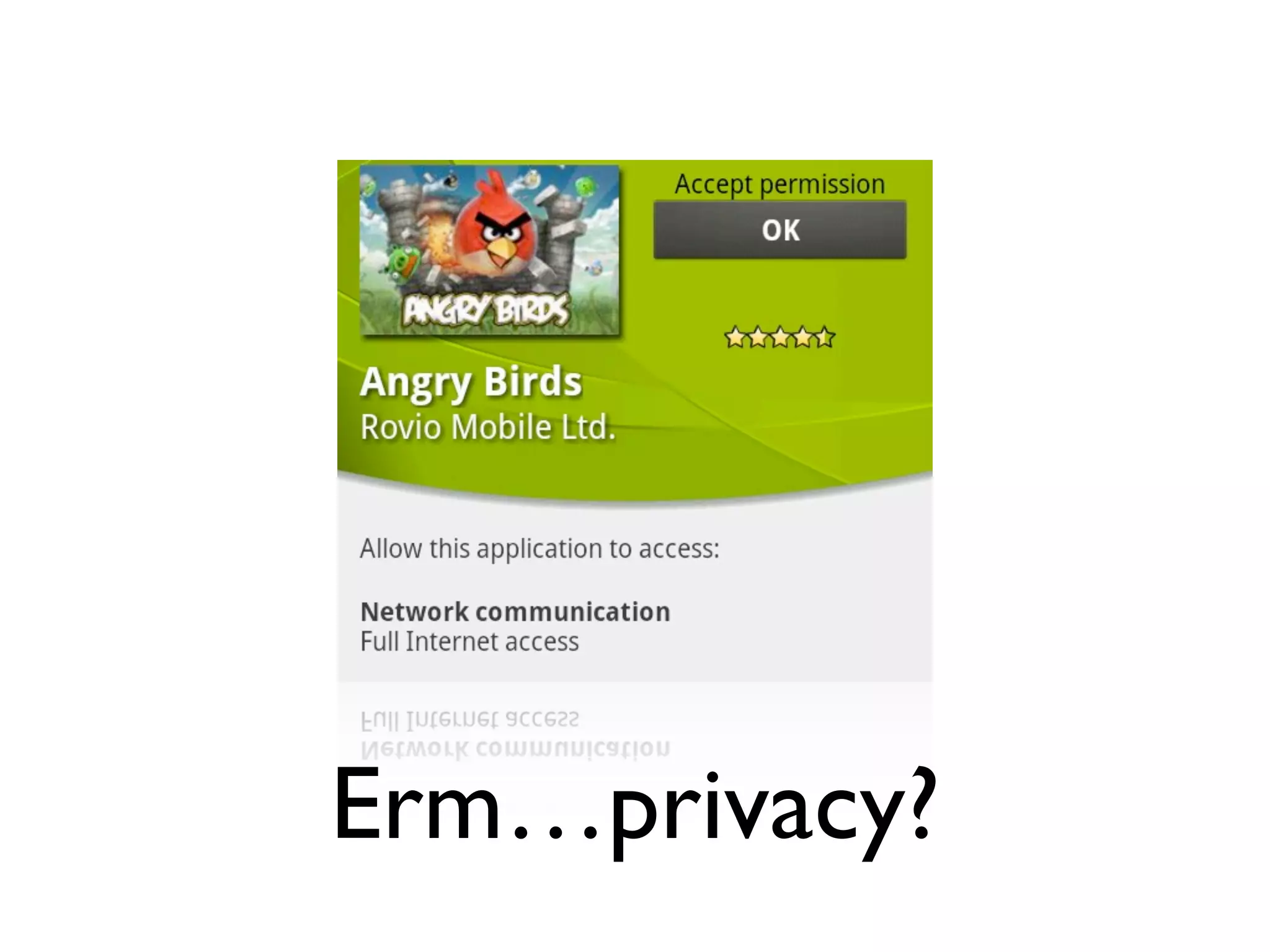
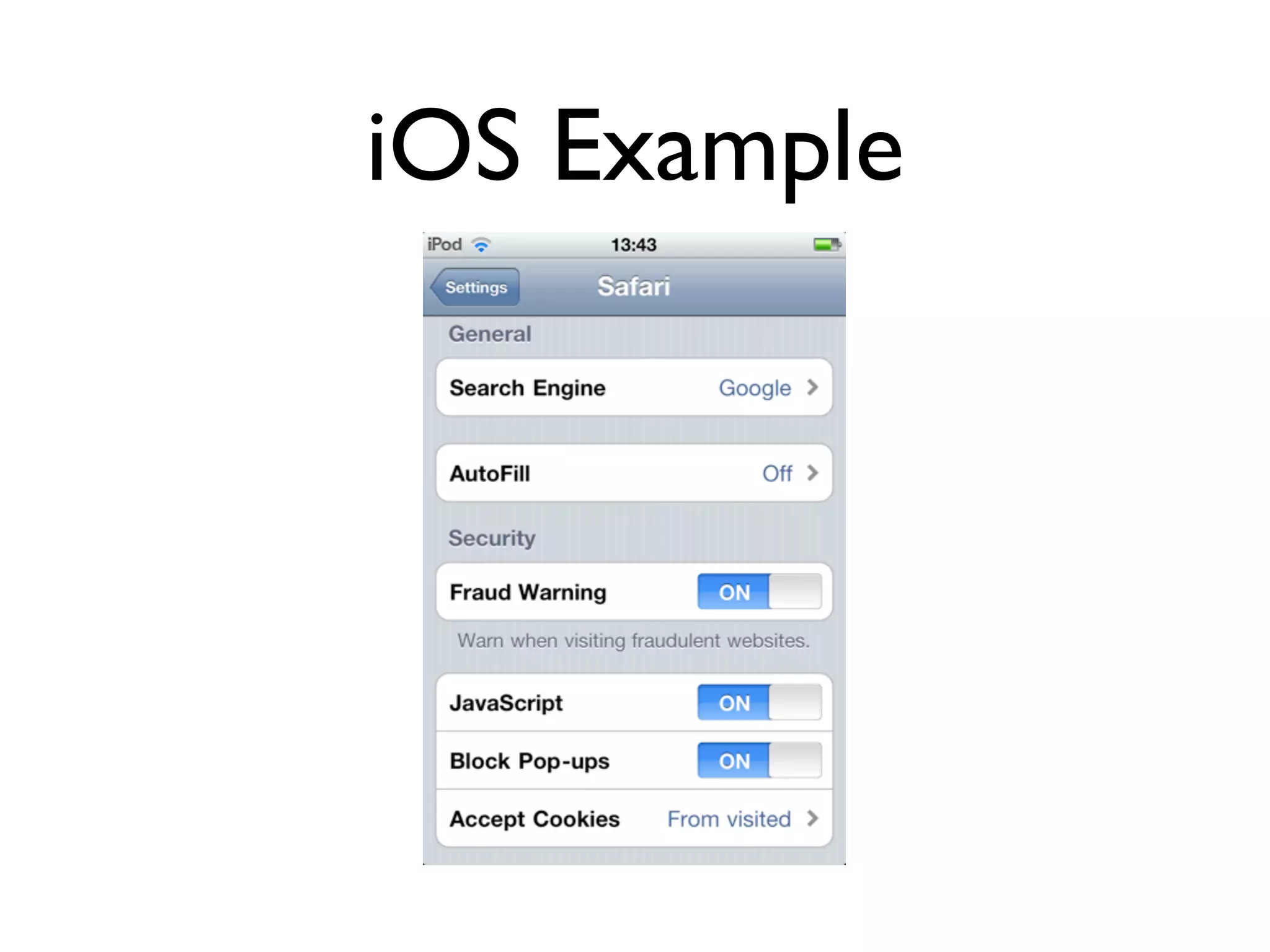
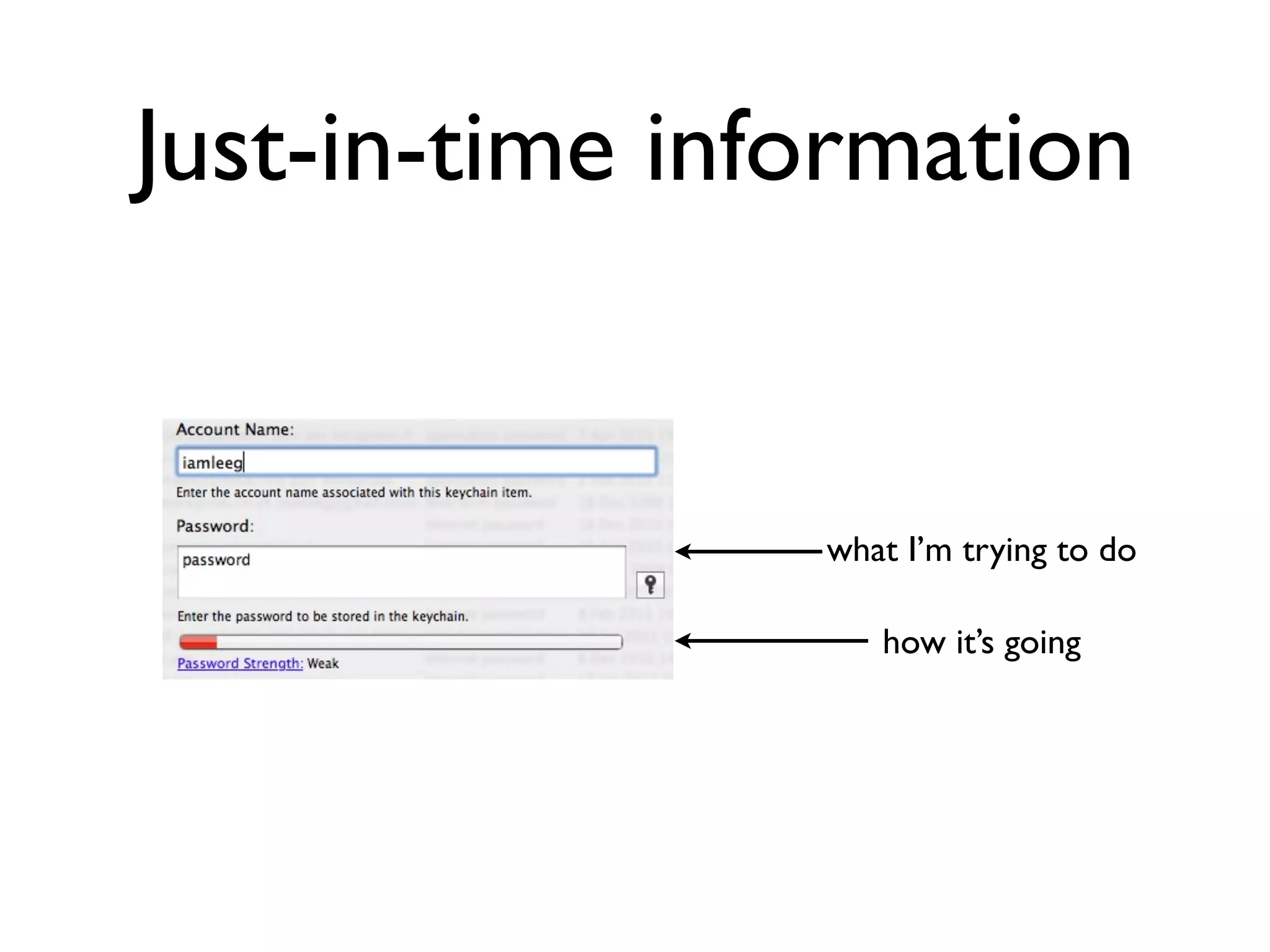
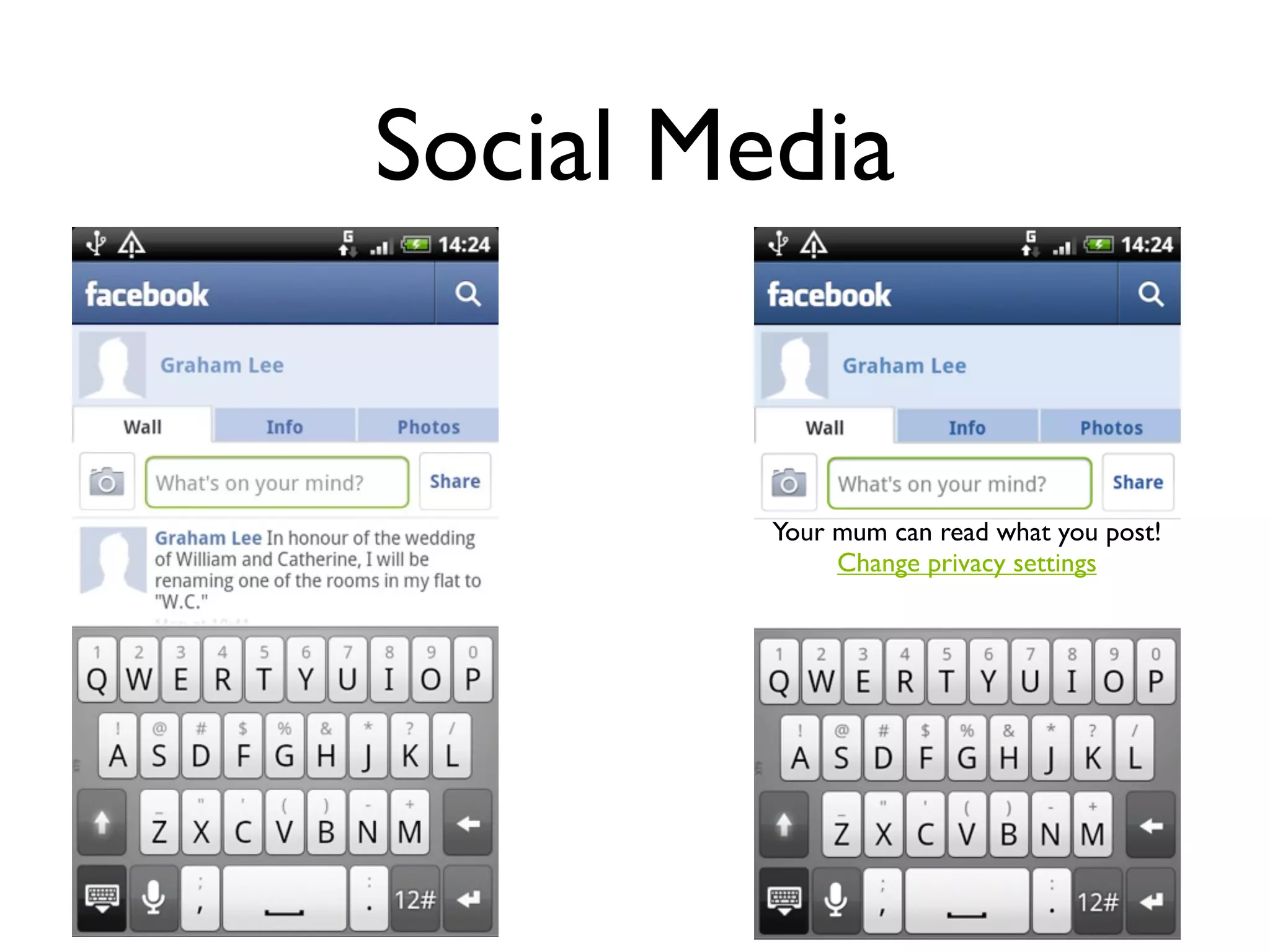
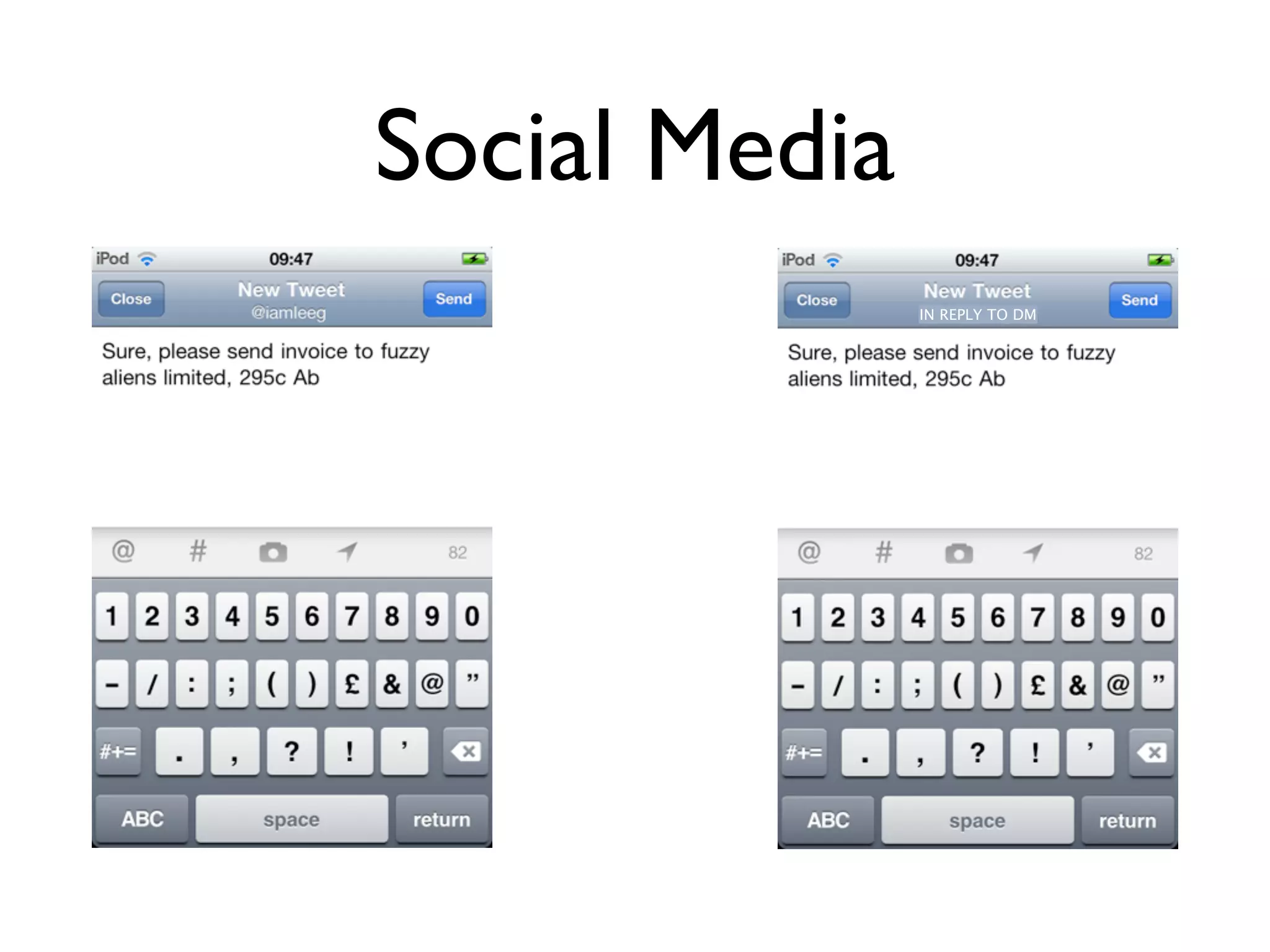
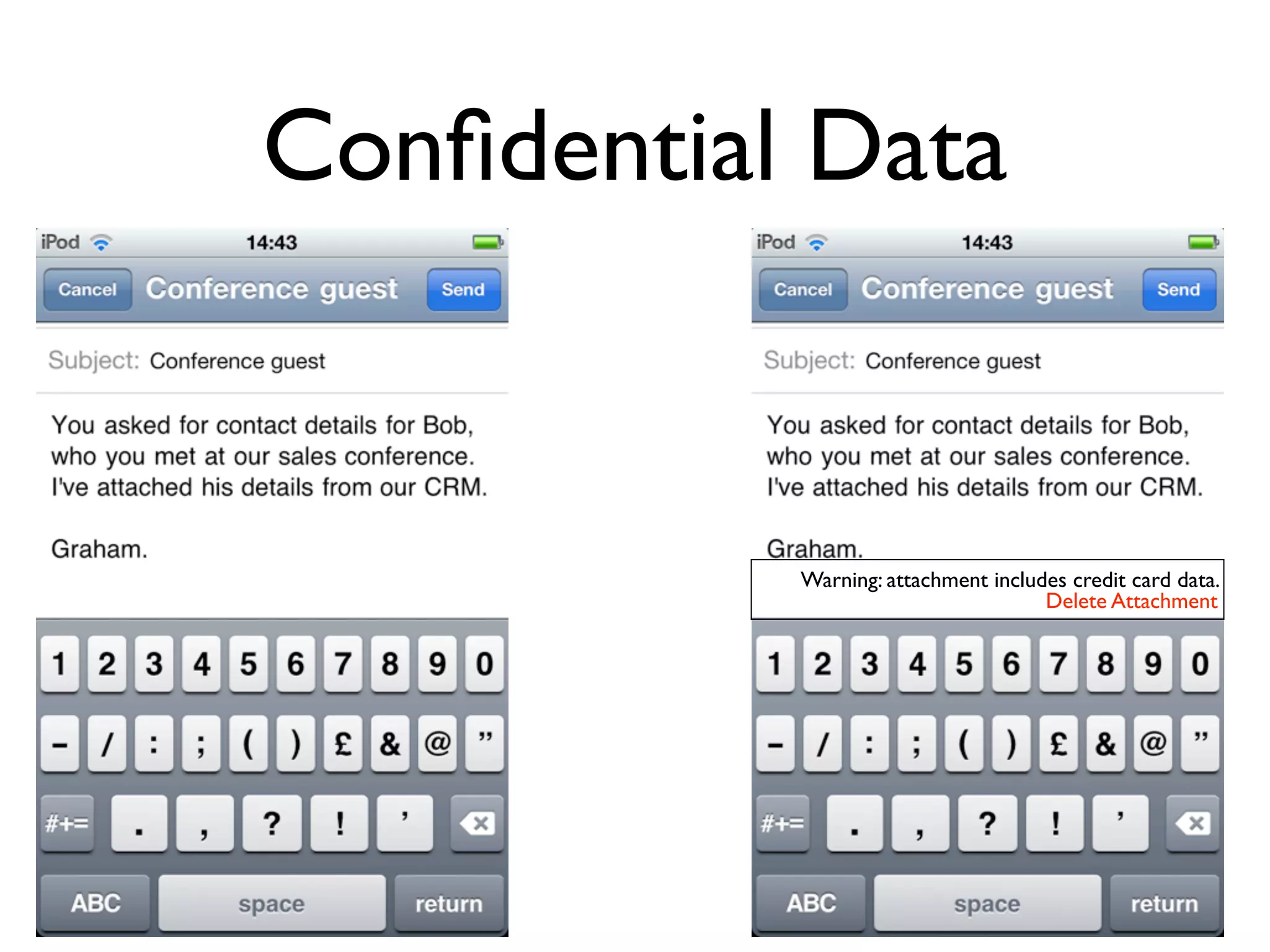
The document discusses the challenges of mobile app privacy, emphasizing that both users and developers share responsibility for protecting personal information. It highlights the inconsistency in user decision-making regarding privacy and the importance of providing digestible privacy information at the point of decision. Moreover, it suggests that affordability is central to privacy improvements and encourages collaborative efforts between users and developers.