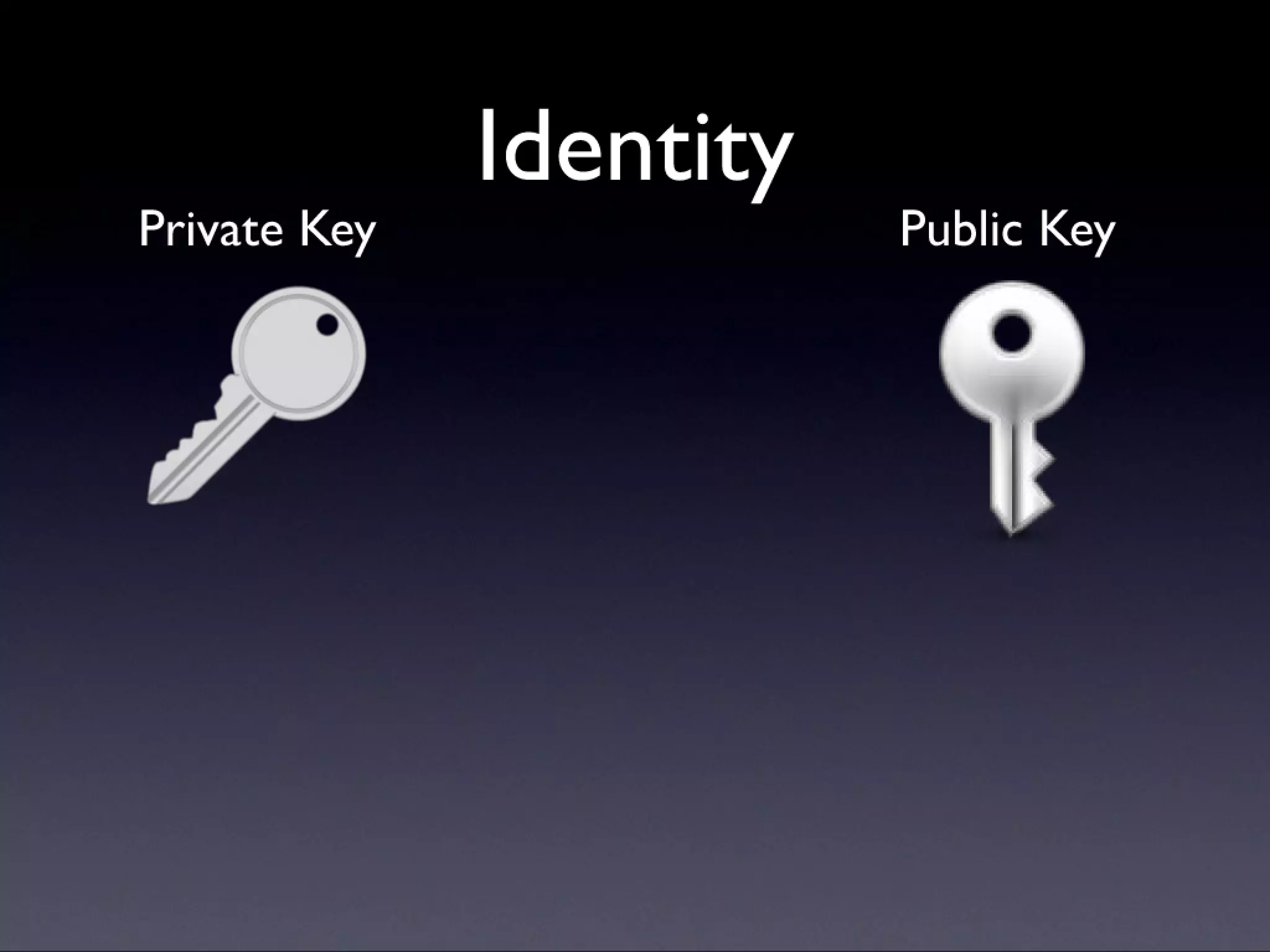
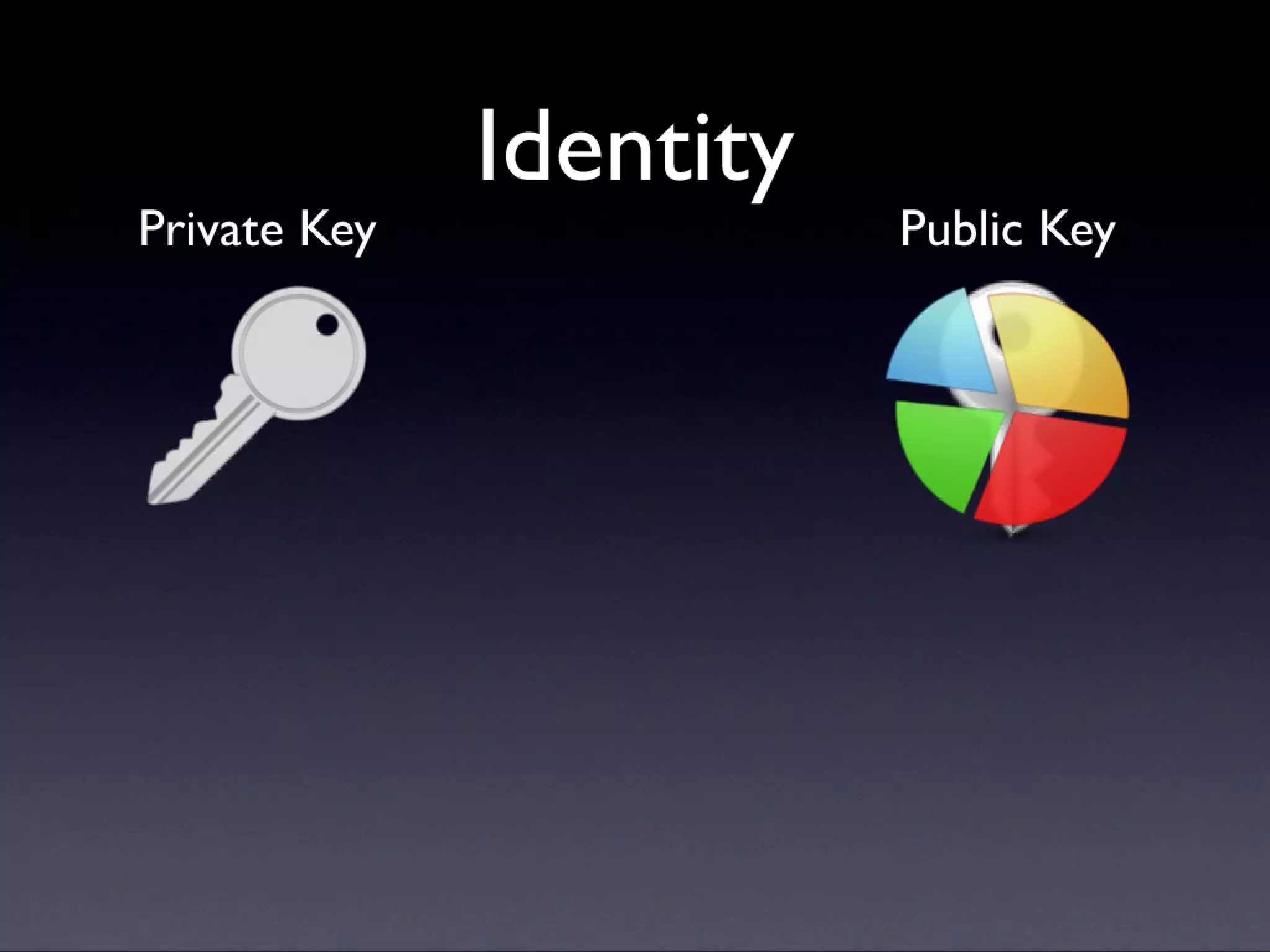
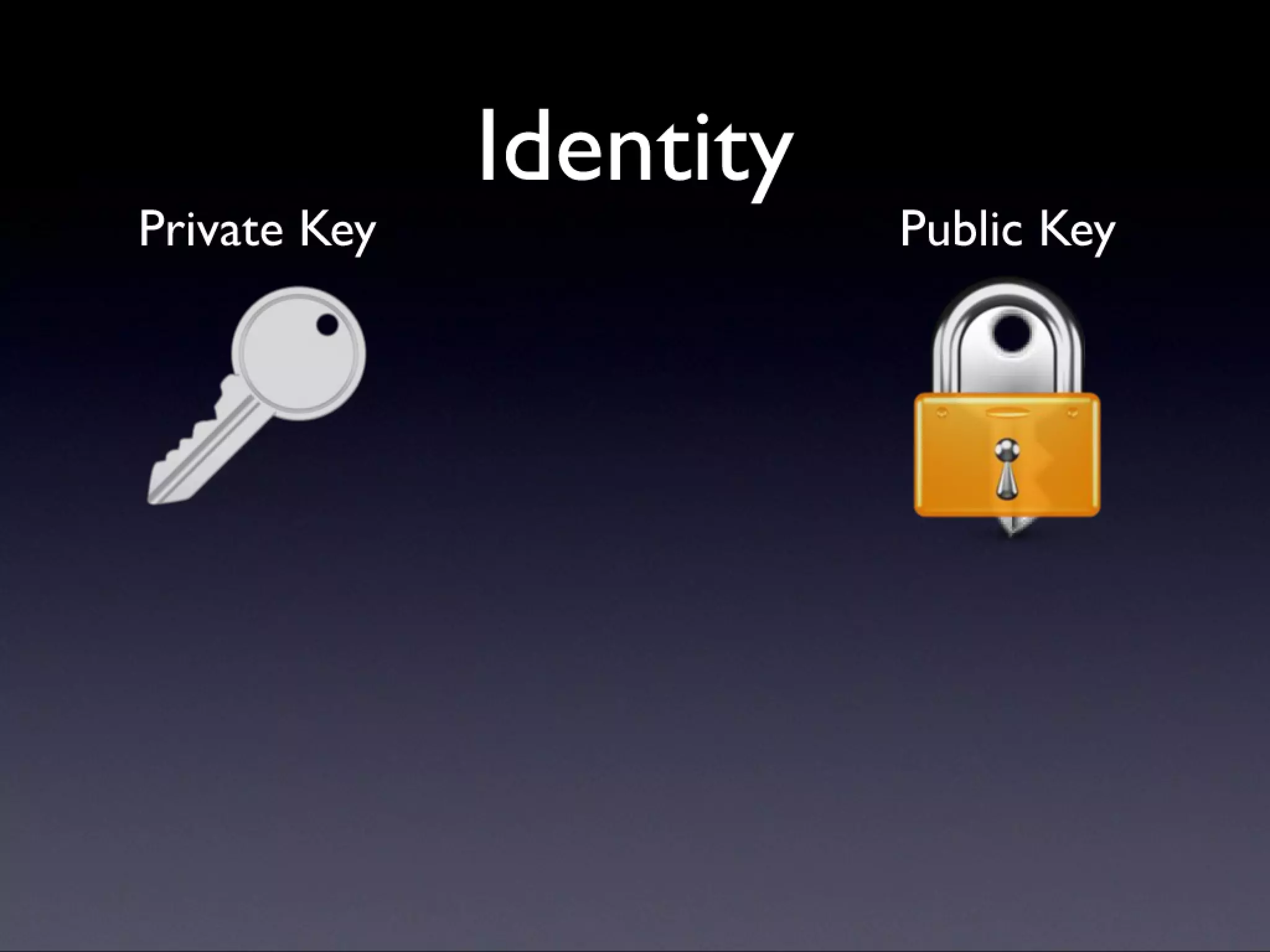
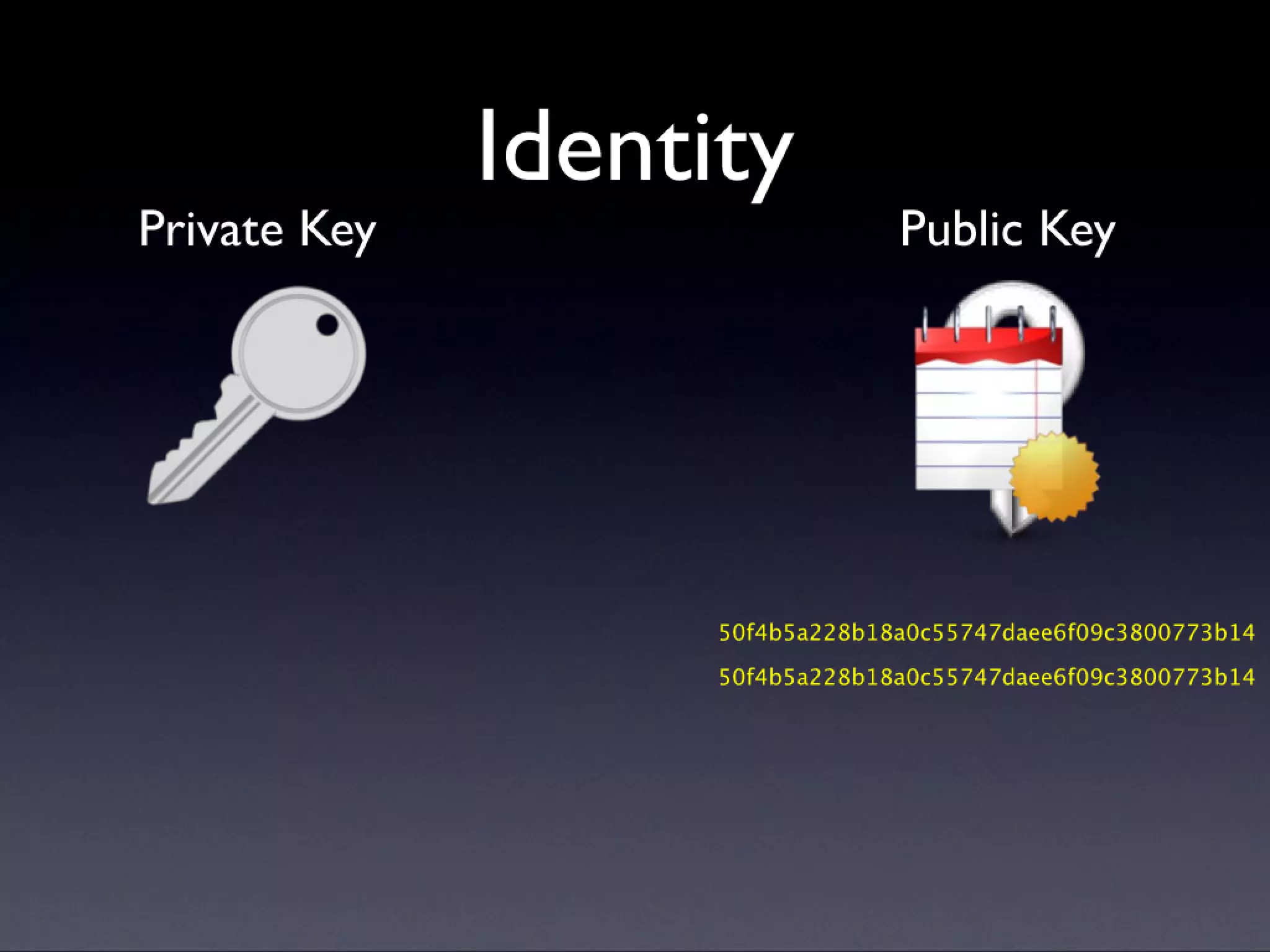
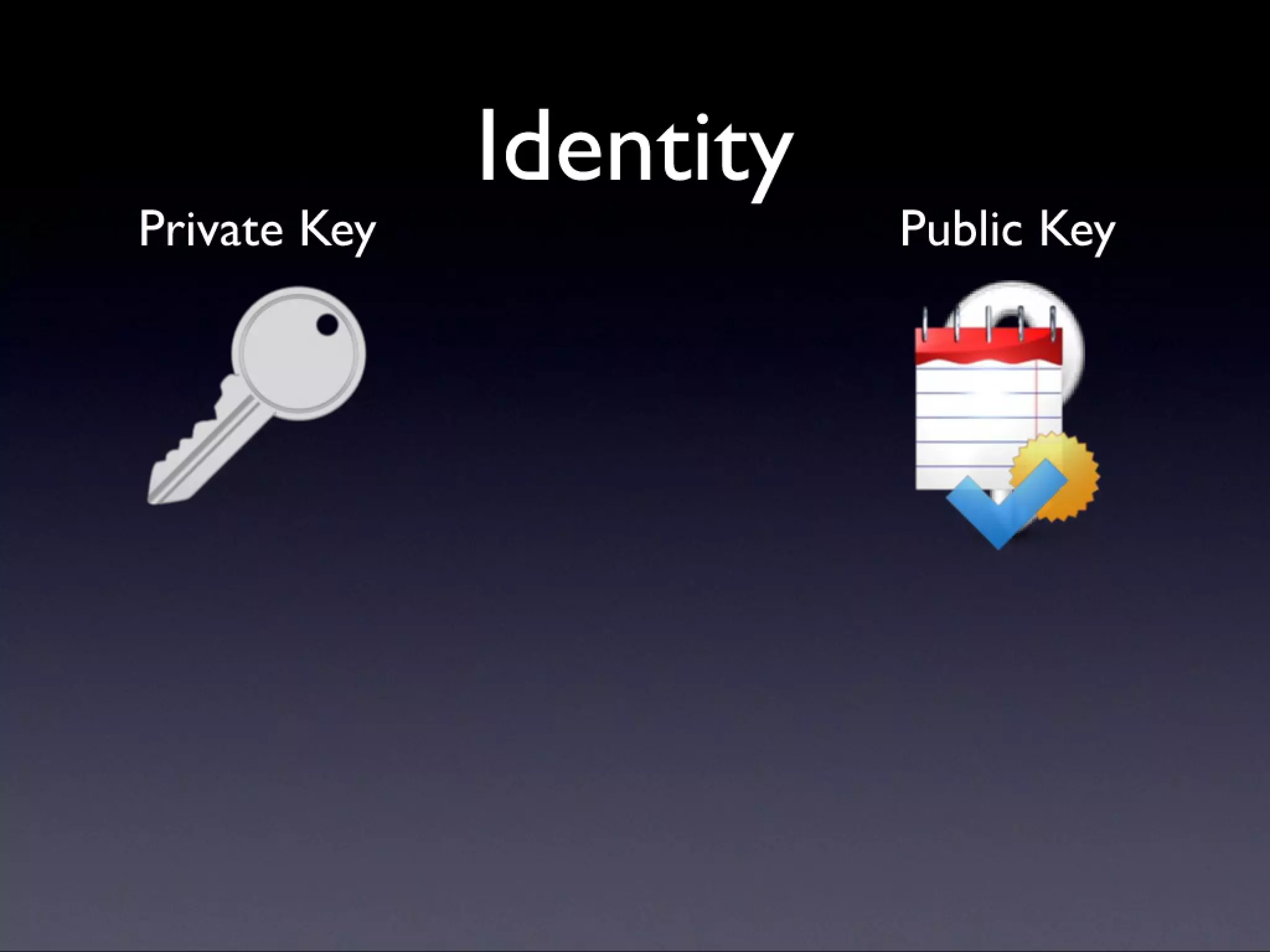
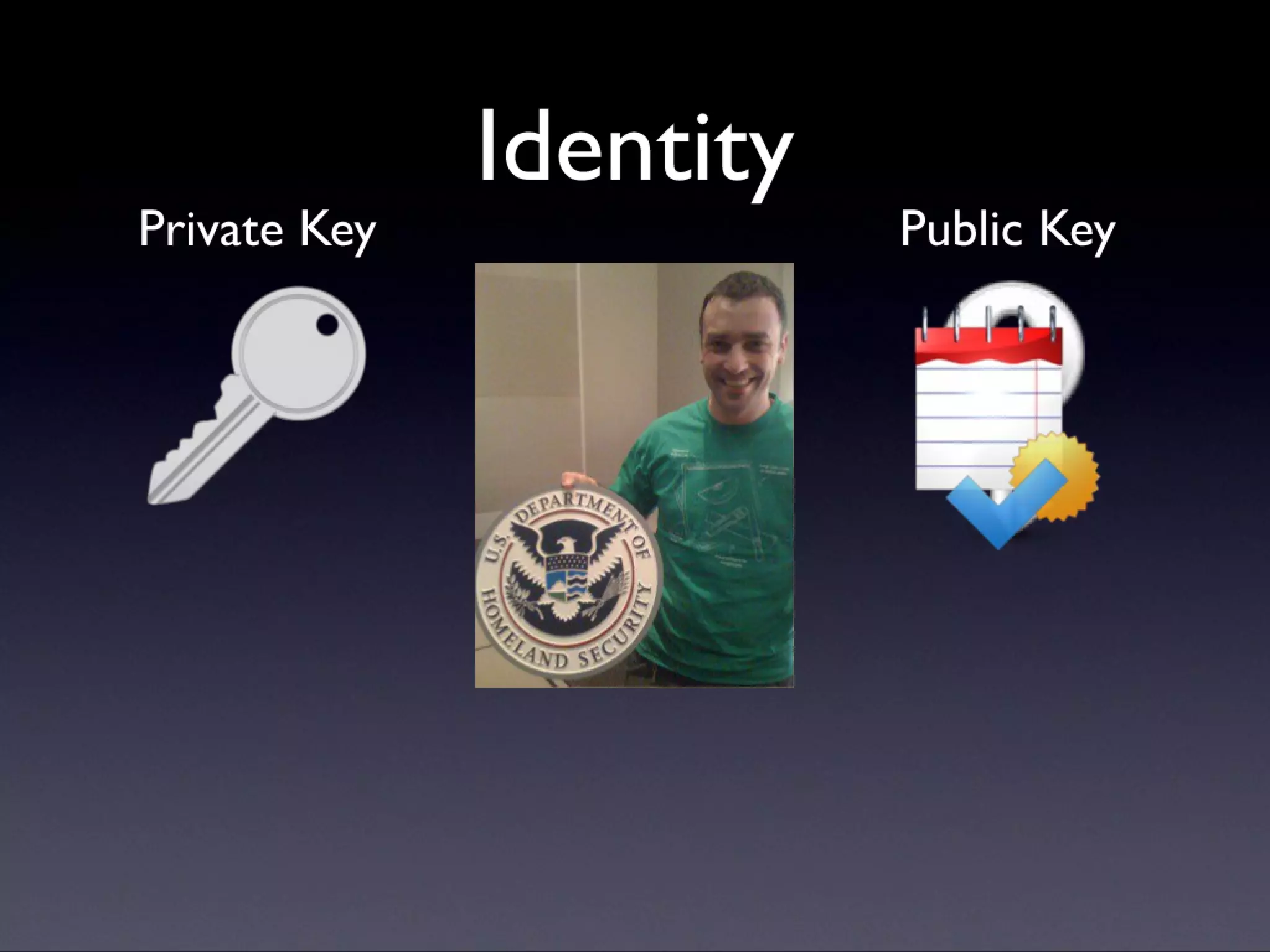
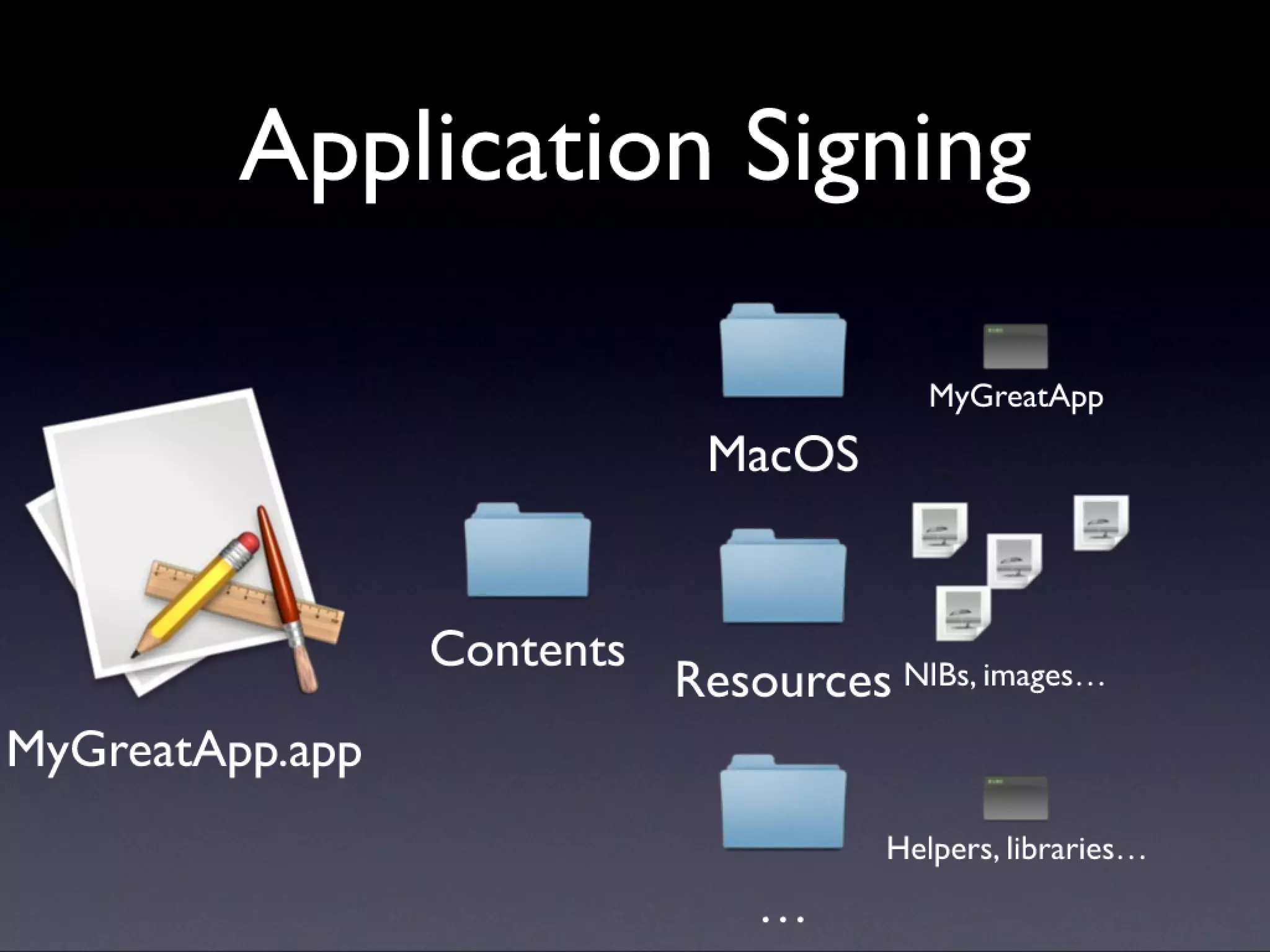
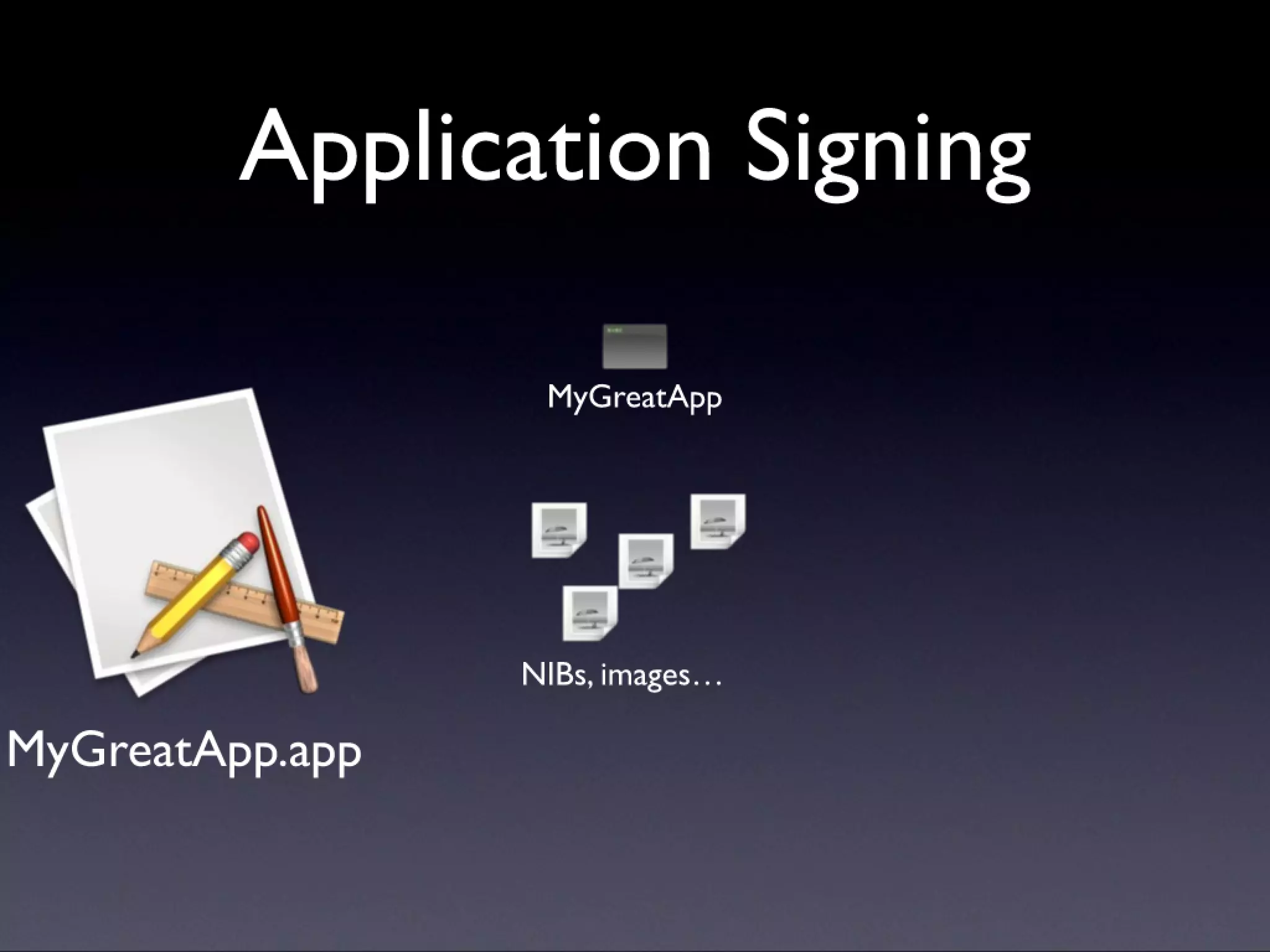
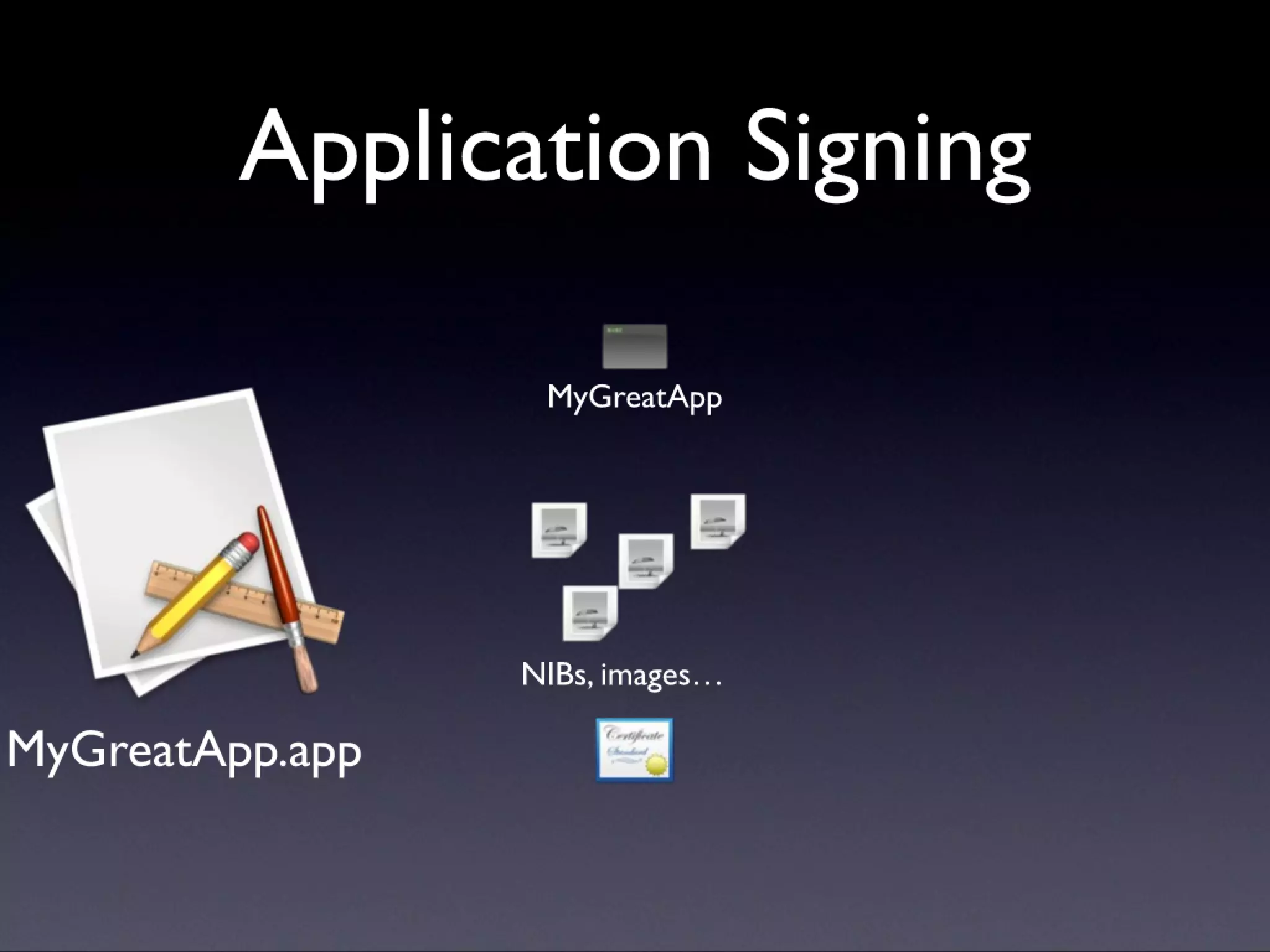
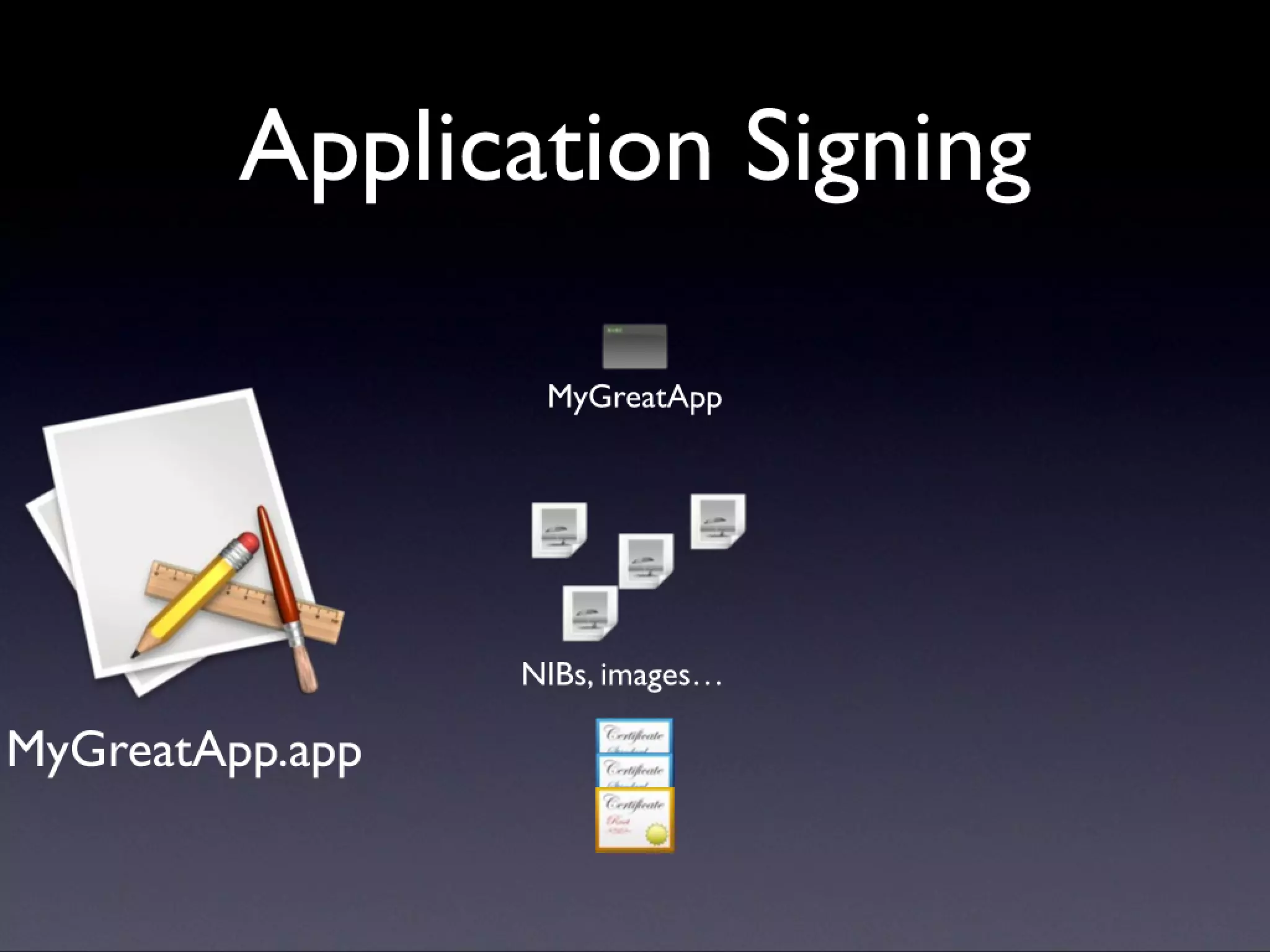
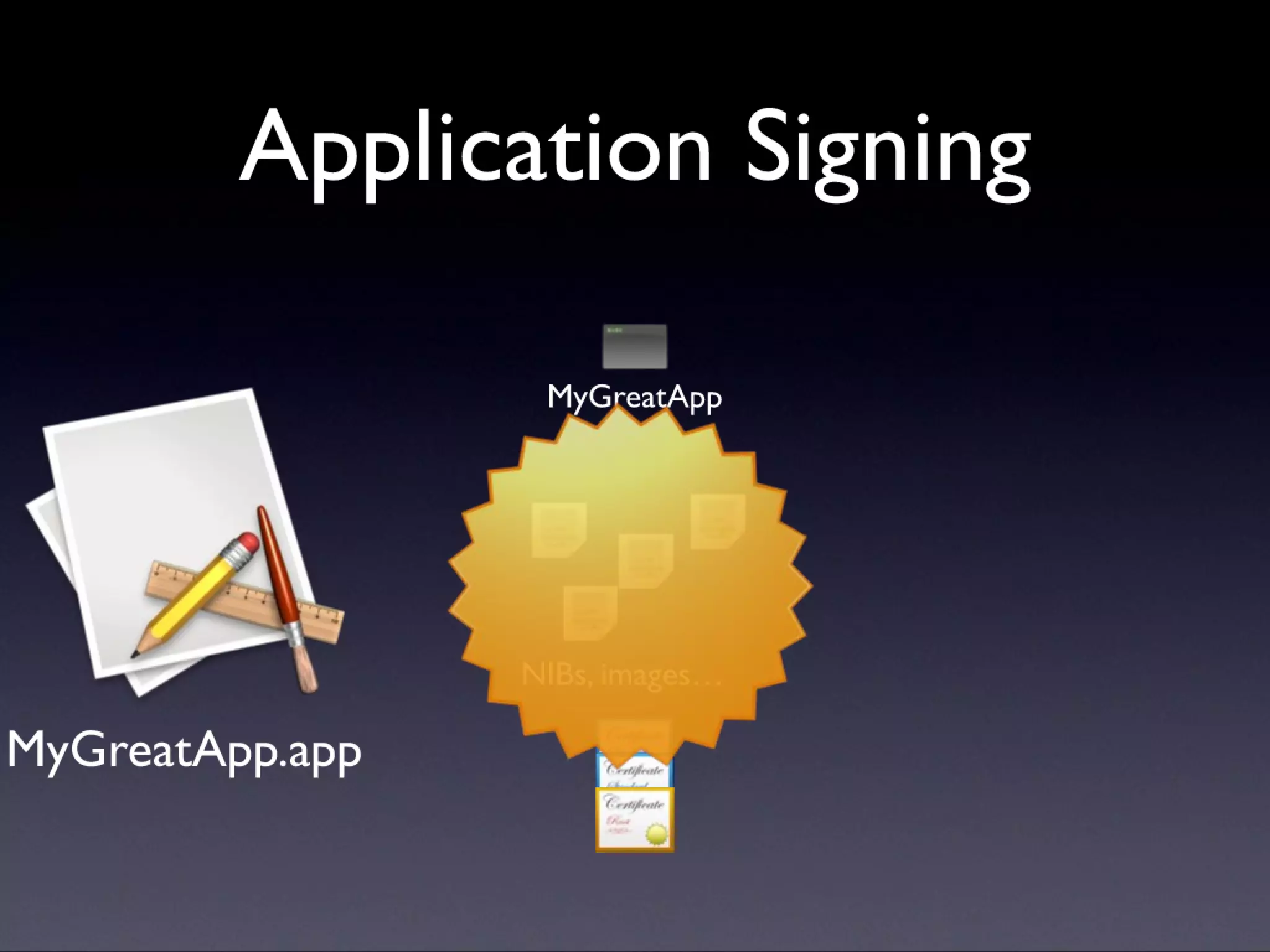
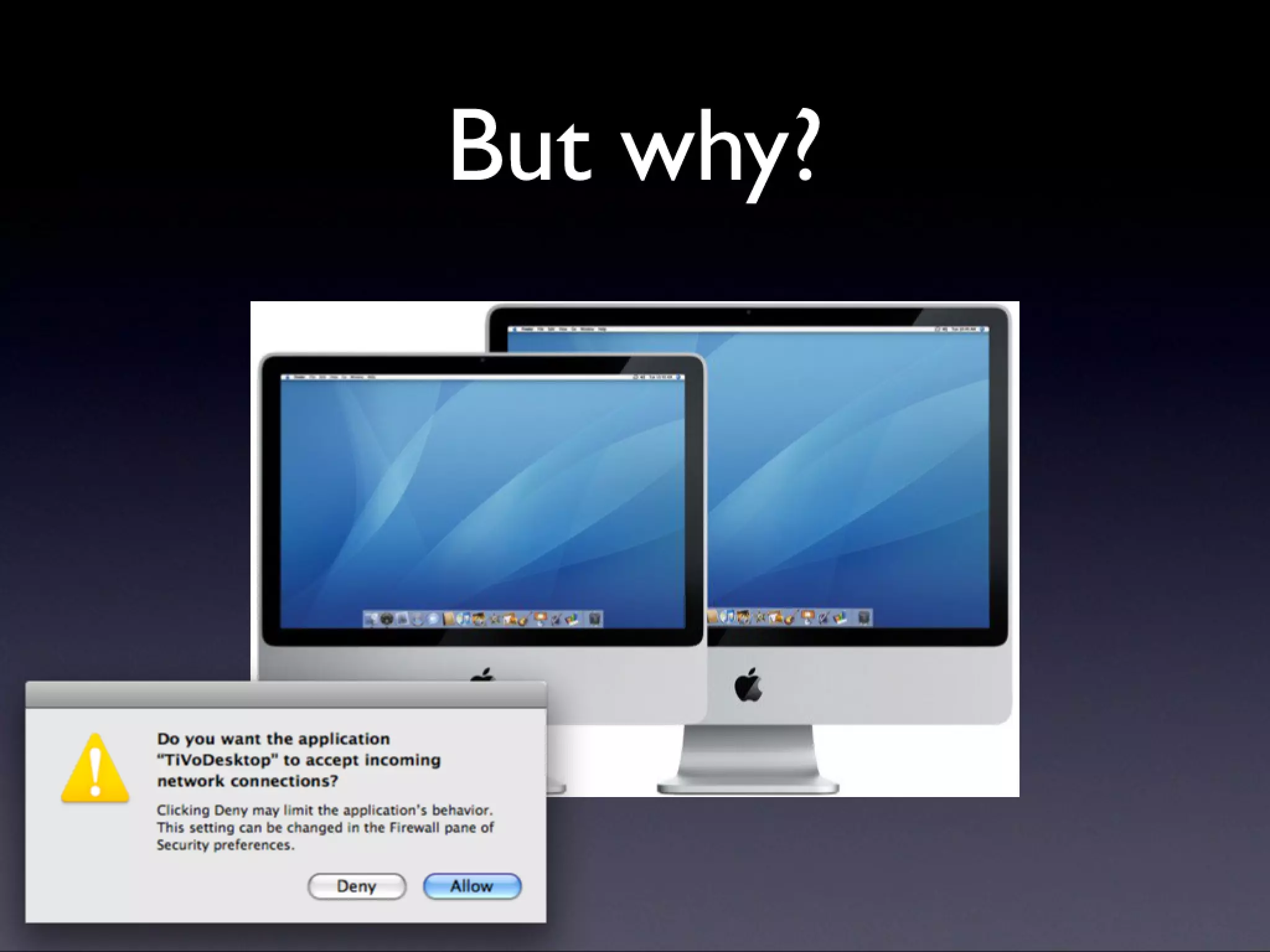
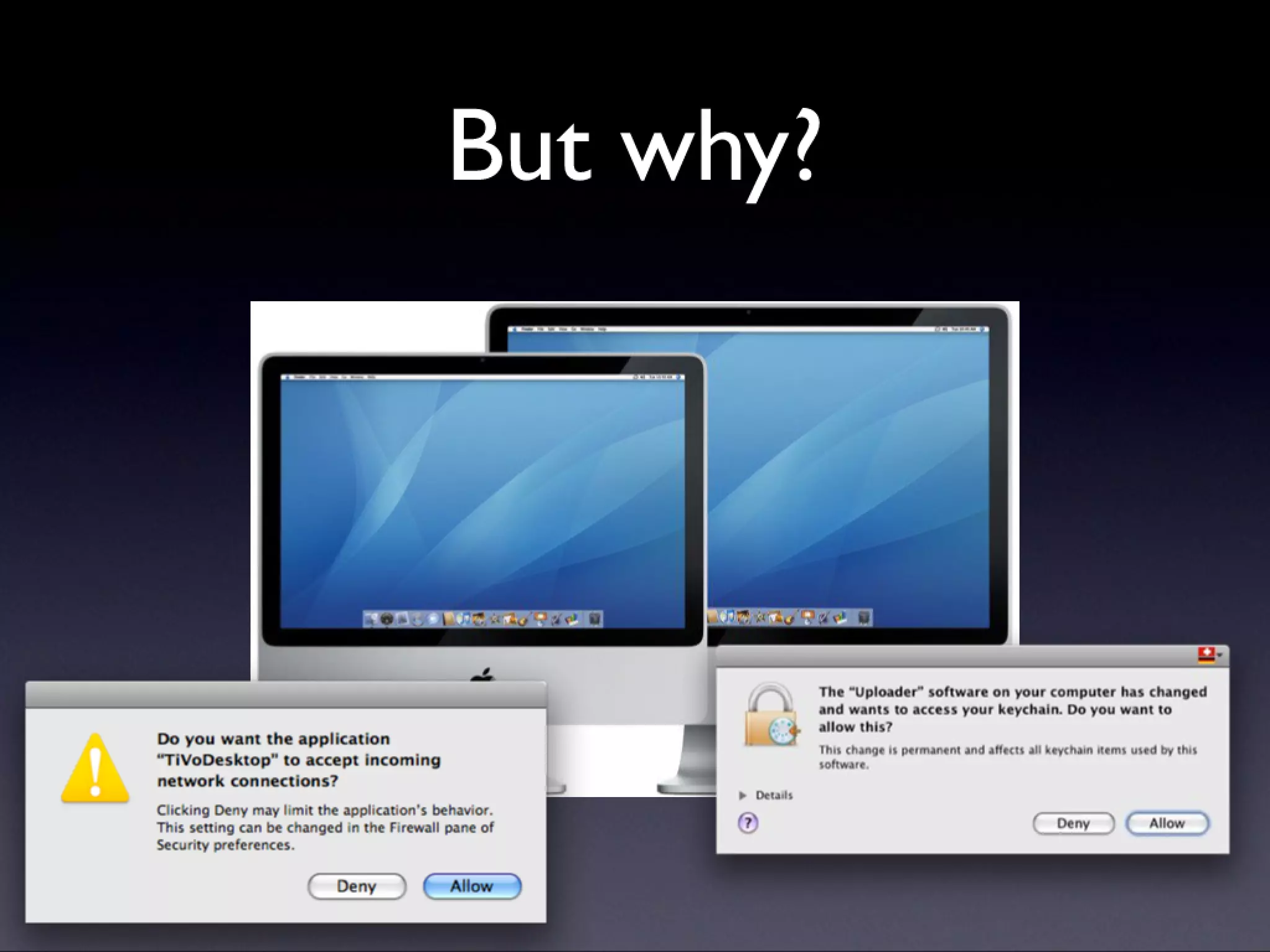
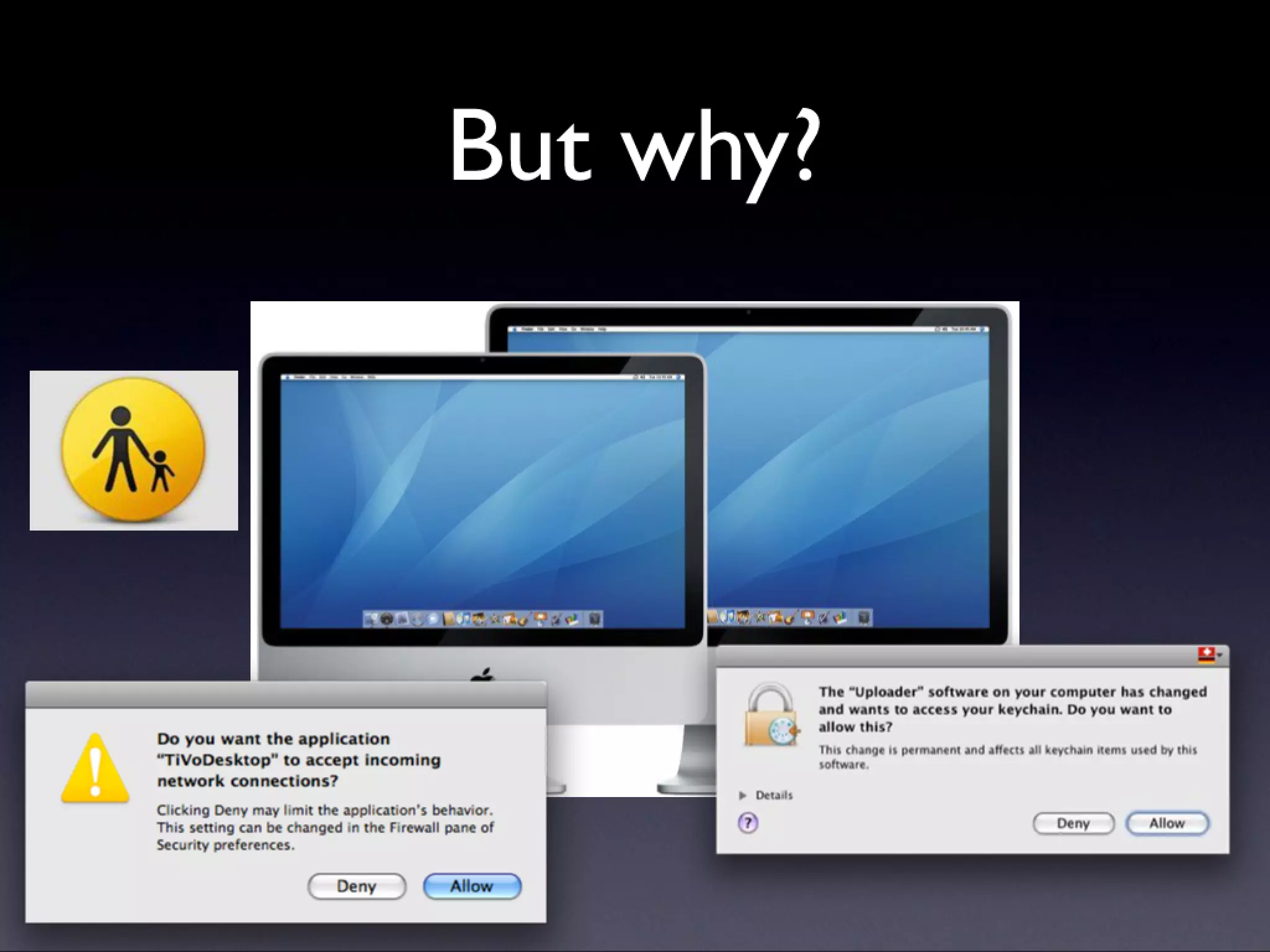
A description of how code signing works on Mac OS X, what it's capable of, and why Cocoa developers should be signing their apps. Note that this presentation was given before Apple announced the Mac app store, but the technology and concepts still apply.