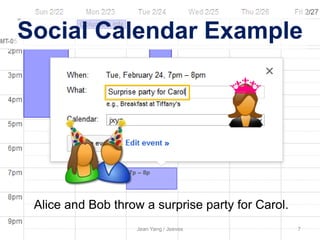
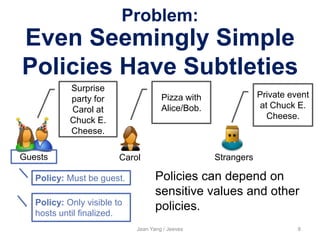
The document presents Jean Yang's approach to preventing information leaks called Jeeves. Jeeves factors out security and privacy policies from application code to reduce opportunities for leaks. Programmers specify high-level policies about how sensitive data can flow rather than handling policies within code. The Jeeves runtime then automatically enforces policies to manage how information is released based on the viewer. This allows policy-agnostic programming while still providing formal guarantees about information flow.











![.guests [ ]
Jeeves Supports
Expressive Policies
def isNotCarol(oc): return oc !=
Jean Yang / Jeeves 16
Output context can be of arbitrary type.
def isGuest(oc): return oc in .guests
A policy is an arbitrary function that takes the
output context and returns a Boolean value.
Policies can depend on sensitive values.](https://image.slidesharecdn.com/singaporedataprivacyworkshoptalk7-150723152524-lva1-app6892/85/Preventing-Information-Flow-with-Jeeves-Singapore-Data-Privacy-Workshop-16-320.jpg)














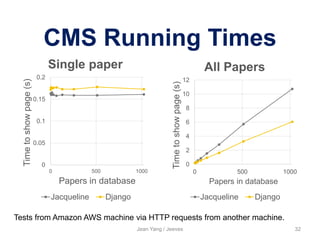
![Policy-Agnostic
Programming in Jeeves
Jean Yang / Jeeves 33
Design of a policy-
agnostic
programming
language
[POPL ‘12]
Semantics and
guarantees
[PLAS ’13]
Web framework,
and case studies
[in submission]
==
Other functionality
Policies
Sensitive
values](https://image.slidesharecdn.com/singaporedataprivacyworkshoptalk7-150723152524-lva1-app6892/85/Preventing-Information-Flow-with-Jeeves-Singapore-Data-Privacy-Workshop-33-320.jpg)


