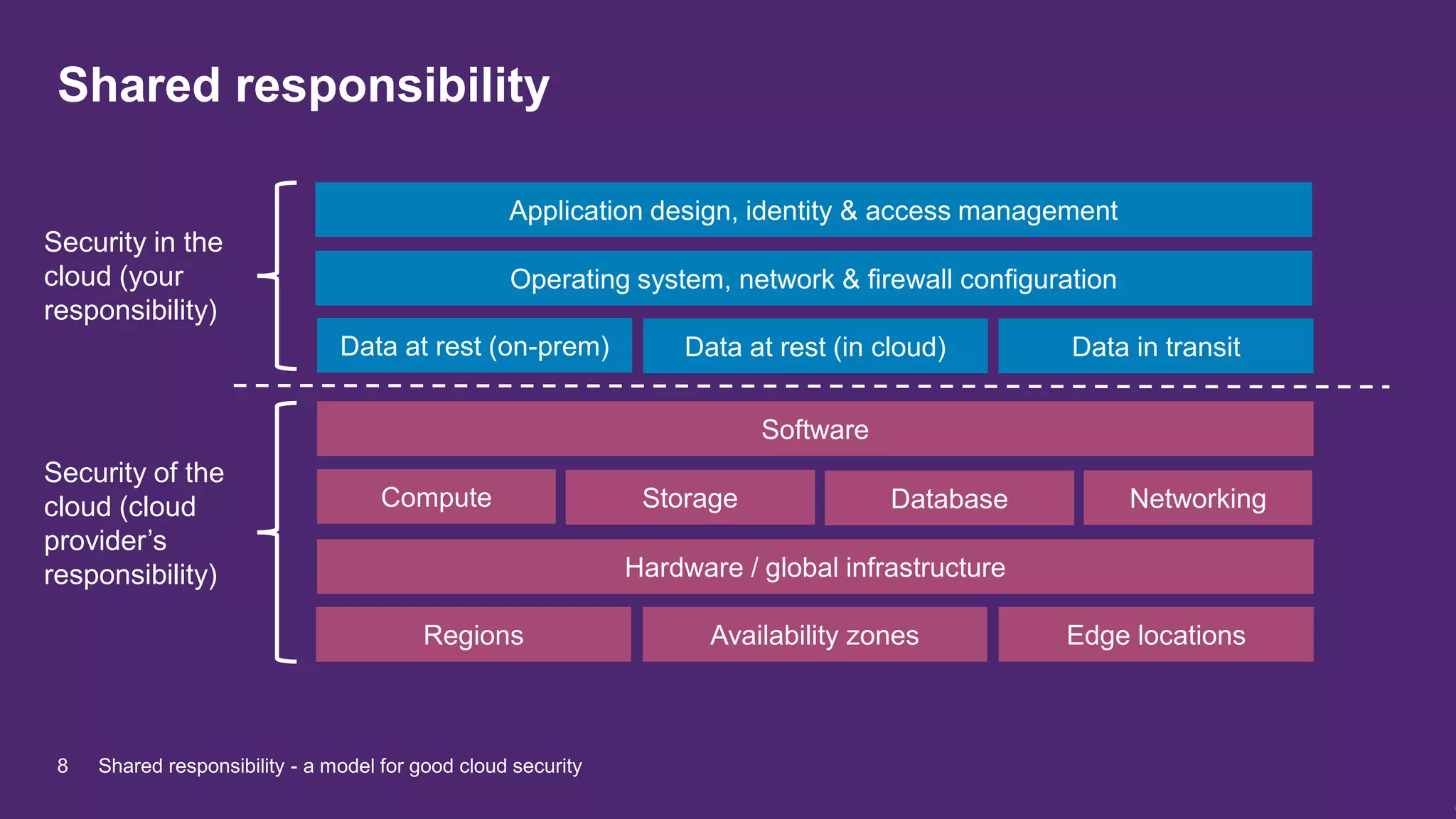
The document discusses the shared responsibility model for cloud security, emphasizing the need for organizations to understand the division of security responsibilities between themselves and cloud providers like AWS, Microsoft, and Google. It highlights case studies from various organizations that illustrate the integration of cloud services into their operations, and stresses the importance of securing data both at rest and in transit. Key takeaways include leveraging existing security tools, following best practices, and ensuring compliance while building resilient cloud solutions.



![“We now have a unified API as a basis for designing, testing, and
deploying the next generation of machine learning and digital
services in the hospital for our young patients. This will also enable
rapid and easier collaboration with our international paediatric
hospital partners to share specialised tools to improve patient
outcomes and experience.”
“Partnering with Microsoft on the Azure API for Fast Healthcare
Interoperability Resources (FHIR) allows us to scale out and
accelerate our customers’ use of [data]. The managed service is a
great additional component […] bringing research and innovation
closer to clinical impact.”
Professor Neil Sebire, Chief Research Information Officer
Great Ormond Street Hospital
Rodrigo Barnes, CTO
Aridhia
4 Shared responsibility - a model for good cloud security](https://image.slidesharecdn.com/ap-secconf-presentation-191107120339/75/Shared-responsibility-a-model-for-good-cloud-security-4-2048.jpg)