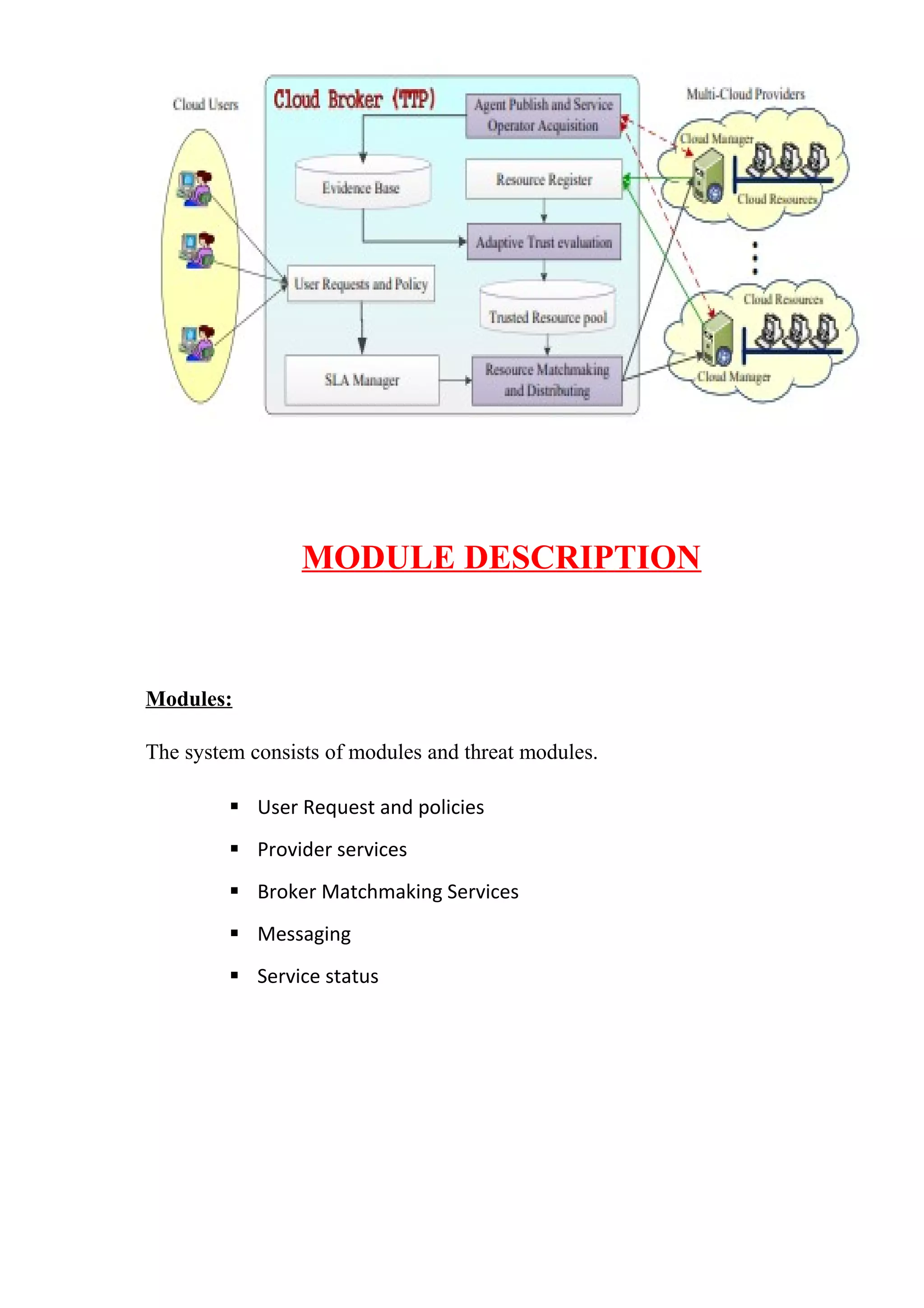
The document proposes a service operator-aware trust scheme (SOTS) for resource matchmaking across multiple clouds. SOTS uses a middleware framework to evaluate trust based on multi-dimensional resource service operators to improve dependability. The broker can efficiently select the most trusted resources in advance using an adaptive trust evaluation approach based on information entropy theory. This overcomes limitations of traditional schemes that manually weight trust factors.