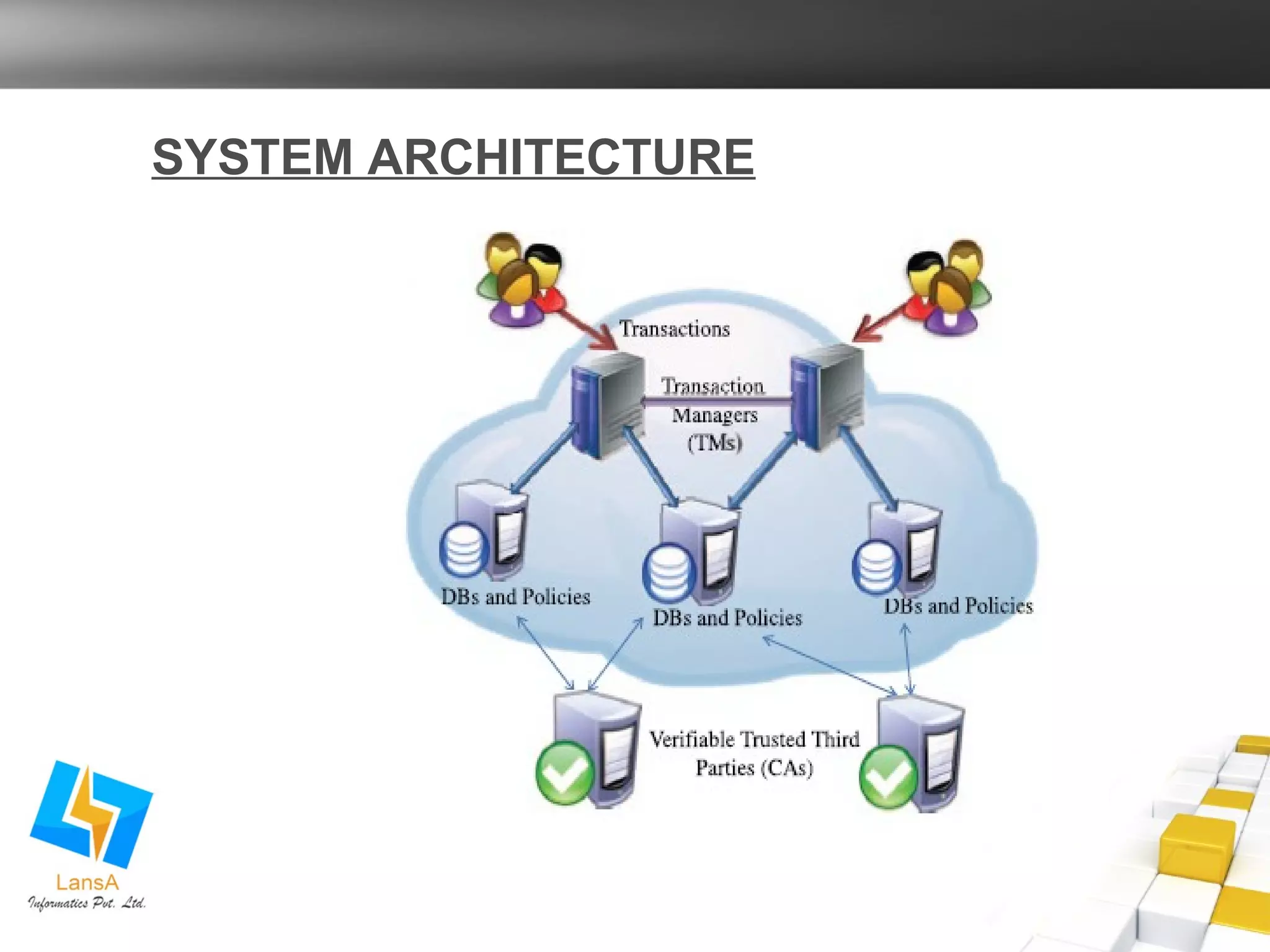
The document discusses the challenges of ensuring security and consistency in cloud-based transactional database systems, particularly when using policy-based authorization. It introduces the concept of trusted transactions and proposes a two-phase validation commit protocol to maintain trust and policy consistency. Additionally, it analyzes different enforcement approaches to help decision-makers select the most effective strategy for secure cloud transactions.