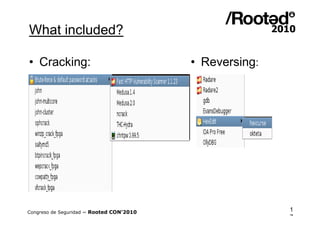
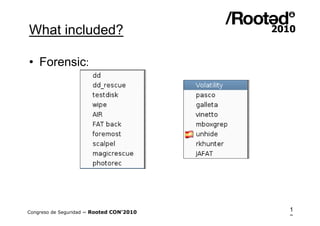
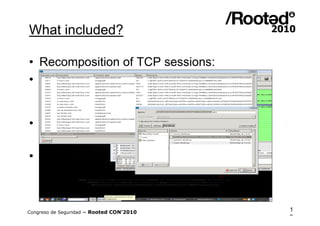
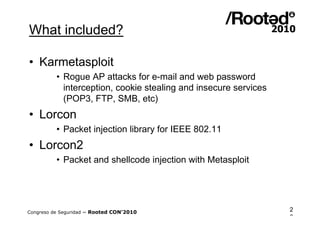
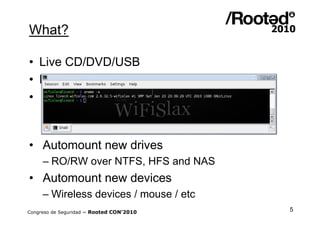
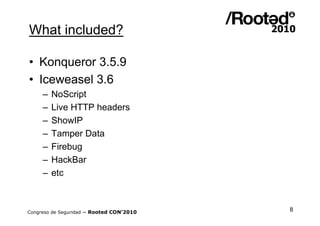
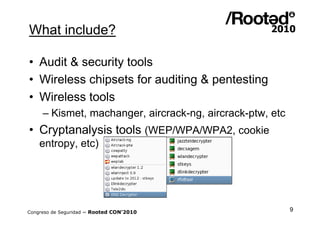
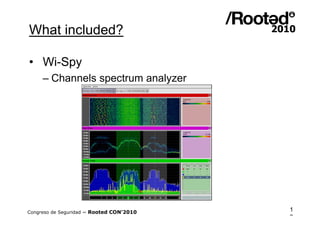
Wifislax 4.0 beta is a GNU/Linux distribution focused on security auditing, particularly wireless security, network vulnerability, and pentesting. It includes numerous tools for auditing, such as Kismet, Aircrack-ng, and Wireshark, along with support for various wireless chipsets and the ability to run as a live CD/DVD/USB. The distribution aims to improve wireless security practices and promote new security standards while being user-friendly for those less familiar with Linux.




![Aircrack-ng-patch
• Anticipating the next speaker:
• WiFiSlax 4.0 is the only distribution that is not
vulnerable to 0-day of Airodump-ng 1.0
[No more details, yet]
– Thanks to Iñaki L. ;-)
Congreso de Seguridad ~ Rooted CON’2010 1
1](https://image.slidesharecdn.com/sergiogonzalez-wifislax4-0beta-100328041723-phpapp02/85/Sergio-Gonzalez-WiFiSlax-4-0-RootedCON-2010-11-320.jpg)