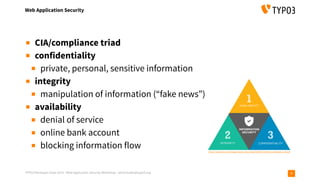
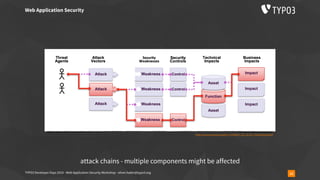
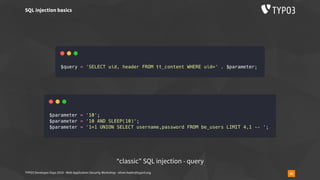
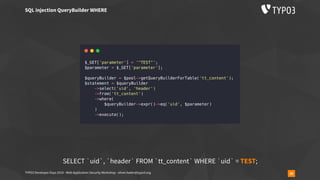
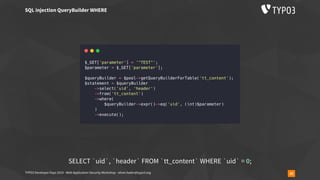
The document outlines a web application security workshop led by Oliver Hader during the TYPO3 Developer Days 2019, focusing on various attack techniques such as XSS, SQL injection, and insecure deserialization. Participants are introduced to attack tools, vulnerability scoring, and best practices for reporting security issues. The workshop emphasizes the importance of confidentiality, integrity, and availability in web application security.









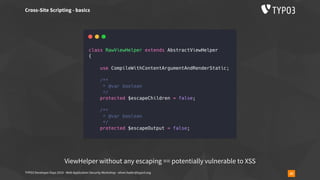
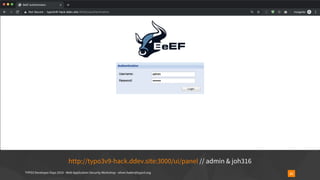
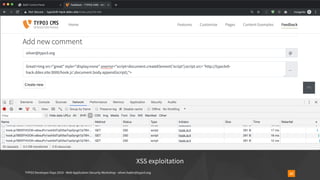
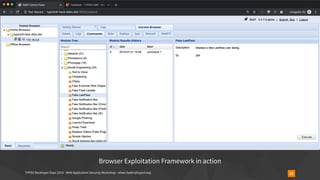
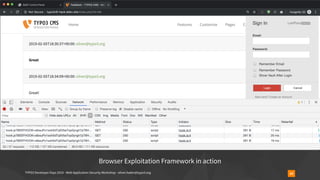







![TYPO3 Developer Days 2019 - Web Application Security Workshop - oliver.hader@typo3.org
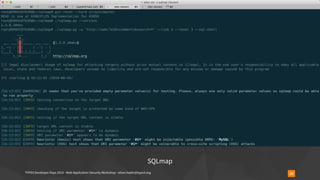
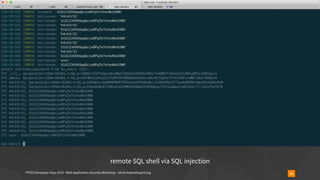
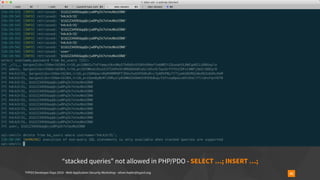
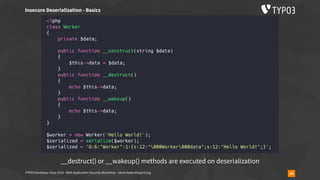
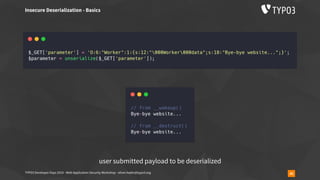
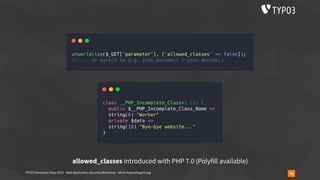
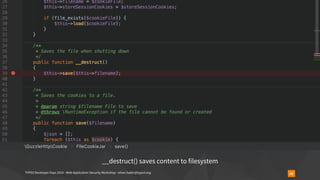
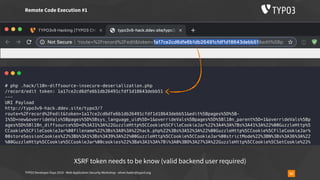
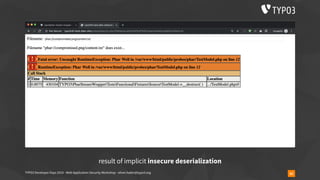
Insecure Deserialization - TYPO3-CORE-SA-2019-020
47
▪ https://typo3.org/security/advisory/typo3-core-sa-2019-020/
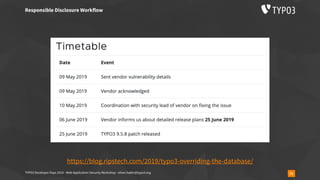
▪ https://blog.ripstech.com/2019/typo3-overriding-the-database/
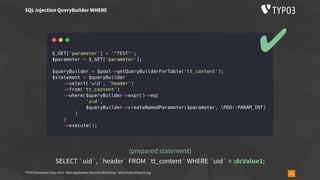
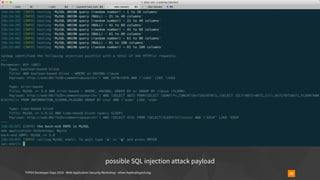
▪ overrideVals[<table>][l10n_diffsource]=<serialized payload>
▪ addressed on June 25th, 2019](https://image.slidesharecdn.com/securityworkshop-190804170933/85/Web-Application-Security-Workshop-T3DD19-47-320.jpg)
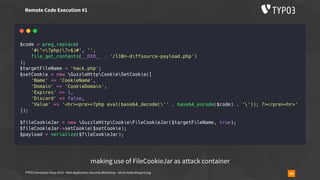
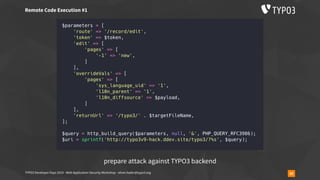
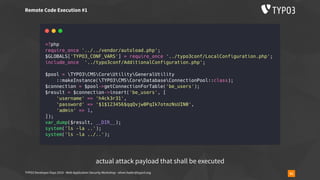
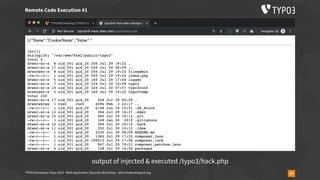
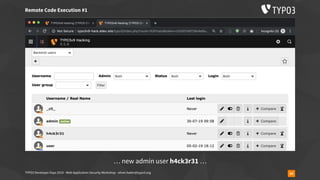



![TYPO3 Developer Days 2019 - Web Application Security Workshop - oliver.hader@typo3.org 59
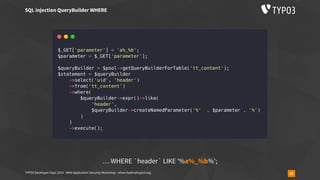
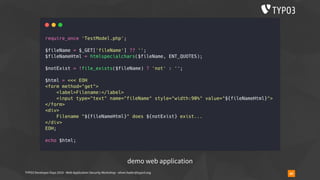
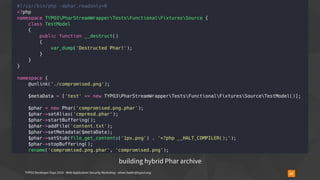
▪ usually used like
require_once('phar://bundle.phar/vendor/autoload.php');
$service = new BundleService();
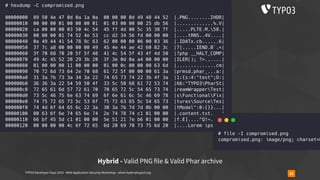
▪ Phar archives are vulnerable to insecure deserialisation
▪ all Phar archives in every PHP version (since 5.3)
▪ using “phar://“ stream wrapper is required here
▪ however, applies to regular file calls as well
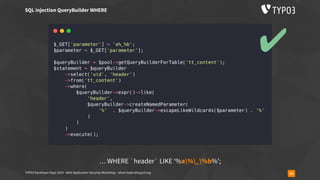
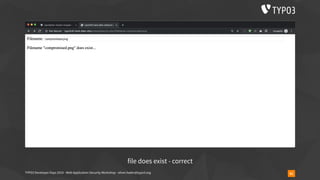
▪ is_file(), file_exists(), fopen(), file_get_contents(), …
▪ is_file($_GET[‘fileName’]) // … user submitted data](https://image.slidesharecdn.com/securityworkshop-190804170933/85/Web-Application-Security-Workshop-T3DD19-59-320.jpg)








![TYPO3 Developer Days 2019 - Web Application Security Workshop - oliver.hader@typo3.org
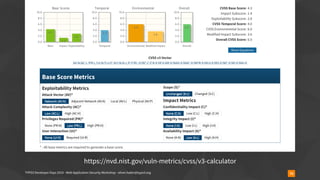
CVSSv3 example #1
76
▪ CVE-2013-1937
▪ phpMyAdmin Reflected Cross-site Scripting Vulnerability
▪ “Reflected cross-site scripting (XSS) vulnerabilities are present on
the tbl_gis_visualization.php page in phpMyAdmin 3.5.x, before
version 3.5.8. These allow remote attackers to inject arbitrary
JavaScript or HTML via the (1) visualizationSettings[width] or (2)
visualizationSettings[height] parameters.”](https://image.slidesharecdn.com/securityworkshop-190804170933/85/Web-Application-Security-Workshop-T3DD19-76-320.jpg)