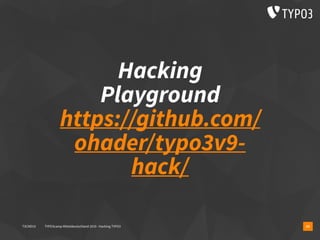
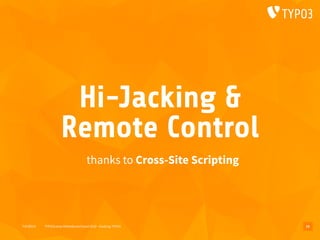
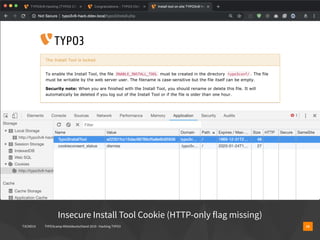
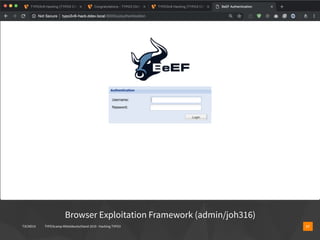
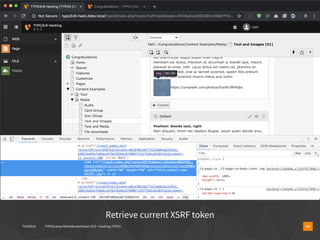
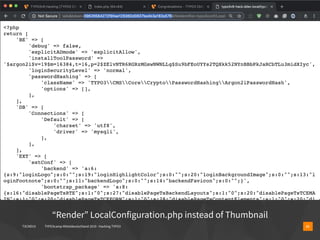
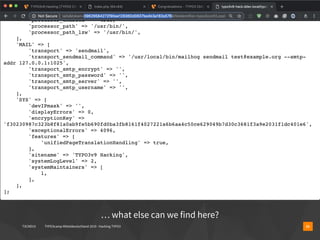
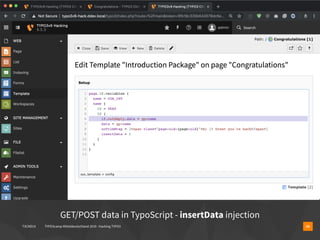
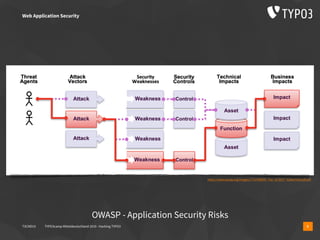
The document presents a talk by Oliver Hader at Typo3Camp Mitteldeutschland 2019, focusing on web application security, particularly vulnerabilities associated with Typo3. It covers the Open Web Application Security Project's top vulnerabilities, SQL injection examples, and security misconfigurations in Typo3 installations. Hader emphasizes the importance of security awareness and contributions to the Typo3 security team for improved core and extension security.






![T3CMD19 TYPO3camp Mitteldeutschland 2019 - Hacking TYPO3
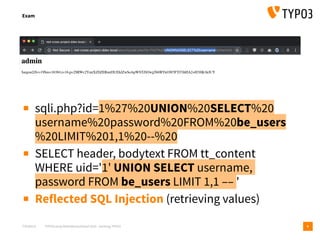
Exam
8
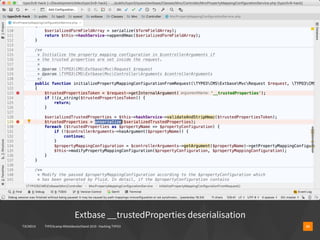
▪ $contentId = $_GET['id'] ?? 1;
▪ $statement = $connection->query($q="
▪ SELECT header,bodytext FROM tt_content
▪ WHERE uid='$contentId'
▪ ");
▪ $content = $statement->fetch();](https://image.slidesharecdn.com/hackingtypo3-190126095022/85/Hacking-TYPO3-v9-8-320.jpg)
![T3CMD19 TYPO3camp Mitteldeutschland 2019 - Hacking TYPO3
Exam
10
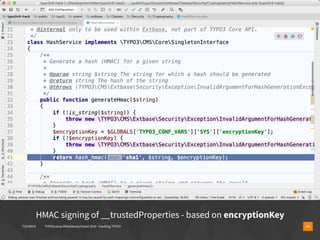
▪ $contentId = $_GET['id'] ?? 1;
▪ // alright, what shall we do here?
▪ $contentId = htmlspecialchars($contentId);
▪ $statement = $connection->query($q="
▪ SELECT header,bodytext FROM tt_content
▪ WHERE uid='$contentId'
▪ ");
▪ $content = $statement->fetch();](https://image.slidesharecdn.com/hackingtypo3-190126095022/85/Hacking-TYPO3-v9-10-320.jpg)
![T3CMD19 TYPO3camp Mitteldeutschland 2019 - Hacking TYPO3
Exam
11
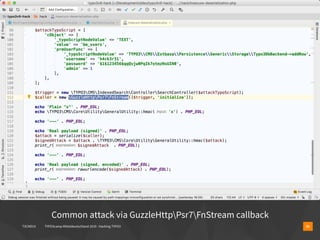
▪ $contentId = $_GET['id'] ?? 1;
▪ // alright, what shall we do here?
▪ $contentId = escapeshellarg($contentId);
▪ $statement = $connection->query($q="
▪ SELECT header,bodytext FROM tt_content
▪ WHERE uid='$contentId'
▪ ");
▪ $content = $statement->fetch();](https://image.slidesharecdn.com/hackingtypo3-190126095022/85/Hacking-TYPO3-v9-11-320.jpg)
![T3CMD19 TYPO3camp Mitteldeutschland 2019 - Hacking TYPO3
Exam
12
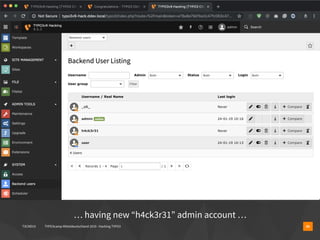
▪ $contentId = $_GET['id'] ?? 1;
▪ // alright, what shall we do here?
▪ $contentId = $connection->quote(contentId);
▪ $statement = $connection->query($q="
▪ SELECT header,bodytext FROM tt_content
▪ WHERE uid='$contentId'
▪ ");
▪ $content = $statement->fetch();](https://image.slidesharecdn.com/hackingtypo3-190126095022/85/Hacking-TYPO3-v9-12-320.jpg)
![T3CMD19 TYPO3camp Mitteldeutschland 2019 - Hacking TYPO3
Exam
13
▪ $contentId = $_GET['id'] ?? 1;
▪ // alright, what shall we do here?
▪ $contentId = (int)contentId;
▪ $statement = $connection->query($q="
▪ SELECT header,bodytext FROM tt_content
▪ WHERE uid='$contentId'
▪ ");
▪ $content = $statement->fetch();](https://image.slidesharecdn.com/hackingtypo3-190126095022/85/Hacking-TYPO3-v9-13-320.jpg)