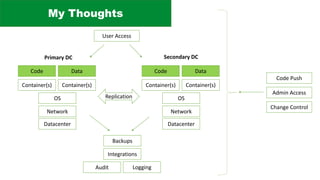
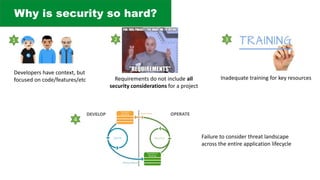
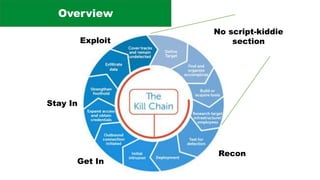
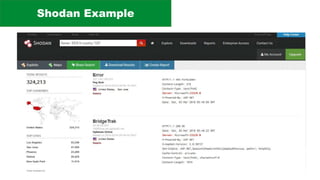
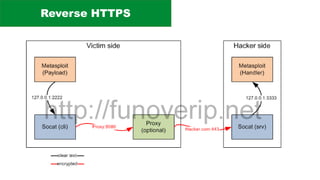
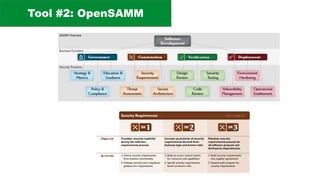
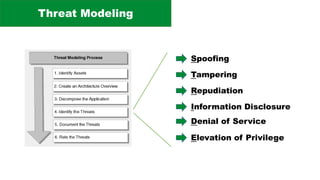
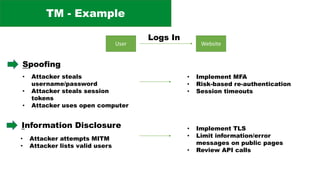
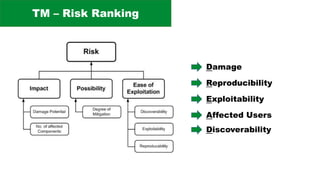
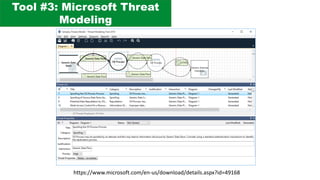
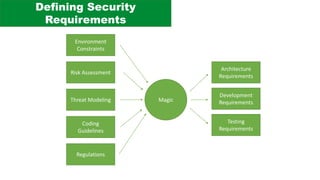
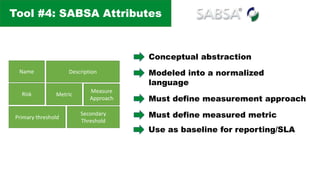
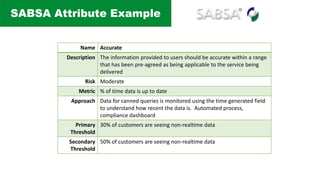
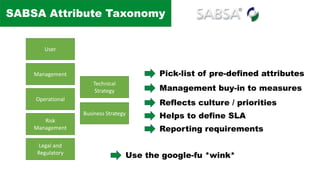
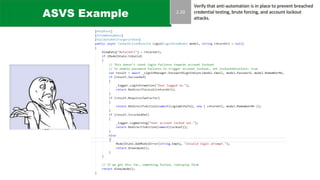
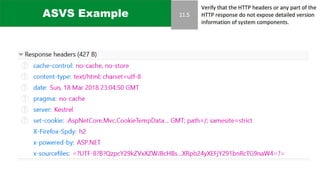
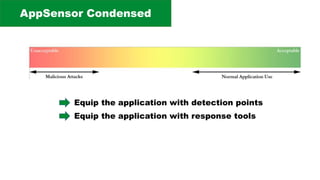
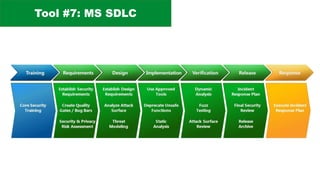
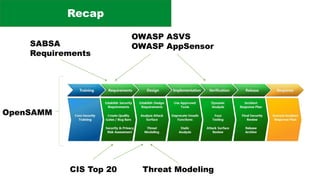
The document discusses the complexities of application security, emphasizing the importance of incorporating security considerations into the development lifecycle. It outlines various security principles and tools for developers, including threat modeling, secure coding practices, and frameworks like OWASP ASVS and Microsoft threat modeling. Furthermore, it highlights specific attack strategies and provides recommendations for mitigating risks through proper security measures and practices.