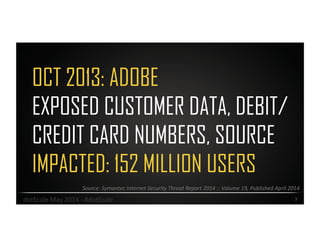
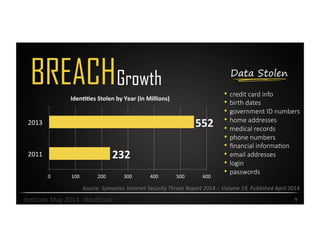
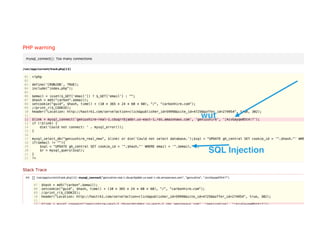
Alison Gianotto, a security and privacy advocate with extensive experience in IT and software development, discusses the escalation of cyber threats and the challenges in mitigating risks. The document highlights major data breaches, the complexity of cybersecurity strategies, and practical recommendations to improve security measures. Key suggestions include implementing risk matrices, simplifying systems, and leveraging automation and regular testing.