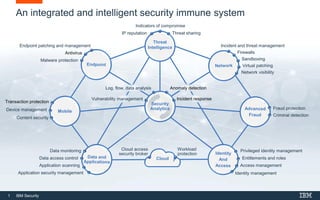
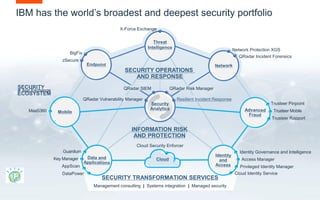
IBM offers a broad portfolio of security products and services including security analytics, threat intelligence, mobile security, cloud security, and identity and access management. Their solutions provide an integrated and intelligent security system with capabilities like indicators of compromise, firewalls, incident response, sandboxing, and network visibility. IBM has consulting and managed security services to help with security transformations. Independent analysts rank IBM as a leader in many areas of security like security information and event management, intrusion prevention, endpoint protection, identity governance, and data security.