Report
Share
Download to read offline
Recommended
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
Recommended
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...

Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
More Related Content
What's hot
Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...

Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...Lacoon Mobile Security
What's hot (20)
Infographic: Security for Mobile Service Providers

Infographic: Security for Mobile Service Providers
Empowering Digital Transformation in Financial Services

Empowering Digital Transformation in Financial Services
The Ultimate Security Checklist Before Launching Your Android App

The Ultimate Security Checklist Before Launching Your Android App
Desafíos de la Ciberseguridad en un ecosistema digitalmente transformado

Desafíos de la Ciberseguridad en un ecosistema digitalmente transformado
Llevando la autenticación de sus clientes a un siguiente nivel

Llevando la autenticación de sus clientes a un siguiente nivel
Enterprise secure identity in the cloud with Single Sign On and Strong Authen...

Enterprise secure identity in the cloud with Single Sign On and Strong Authen...
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)
Empowering Application Security Protection in the World of DevOps

Empowering Application Security Protection in the World of DevOps
Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...

Black Hat USA 2014 - A Practical Attack Against Virtual Desktop Infrastructur...
Cyber Ethics: Cyber Security Services | VAPT and WAPT

Cyber Ethics: Cyber Security Services | VAPT and WAPT
Viewers also liked
Viewers also liked (11)
Mobile Security - Words like Bring Your Own Device, and Federation sounds fam...

Mobile Security - Words like Bring Your Own Device, and Federation sounds fam...
Enterprise Security Architecture: From access to audit

Enterprise Security Architecture: From access to audit
Security Building Blocks of the IBM Cloud Computing Reference Architecture

Security Building Blocks of the IBM Cloud Computing Reference Architecture
Ibm security domains 2015[3]
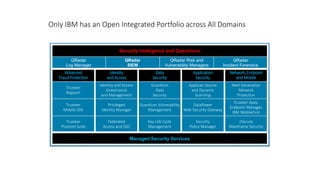
- 1. Only IBM has an Open Integrated Portfolio across All Domains Security Intelligence and Operations QRadar Log Manager QRadar SIEM QRadar Risk and Vulnerability Managers QRadar Incident Forensics Advanced FraudProtection Identity and Access Data Security Application Security Network,Endpoint and Mobile Trusteer Rapport Identity and Access Governance and Management Guardium Data Security AppScan Source and Dynamic Scanning Next Generation Network Protection Trusteer Mobile SDK Privileged Identity Manager Guardium Vulnerability Management DataPower Web Security Gateway Trusteer Apex, Endpoint Manager, IBM MobileFirst Trusteer Pinpoint Suite Federated Access and SSO Key Life Cycle Management Security Policy Manager zSecure Mainframe Security Managed Security Services