This document discusses security and ethical challenges related to information technology. It covers several topics:
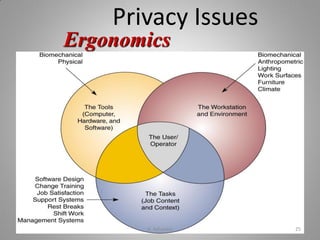
- Identifying ethical issues related to how IT affects employment, individuality, privacy, health, and solving societal problems.
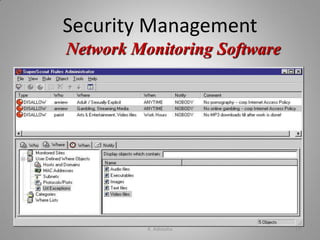
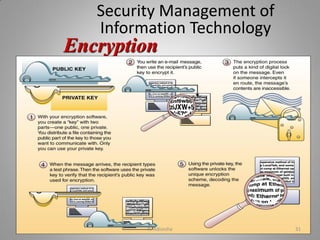
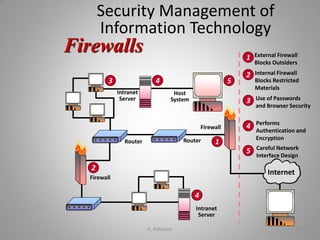
- Different types of security management strategies and defenses that can protect business IT applications.
- Ways that business managers can help reduce harmful effects and increase benefits of IT use.