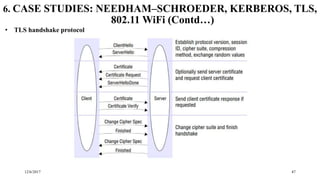
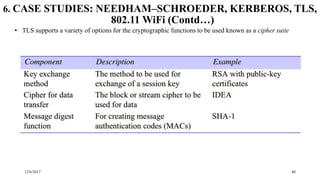
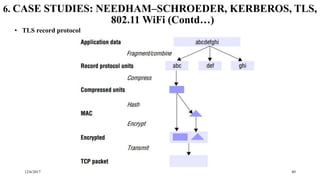
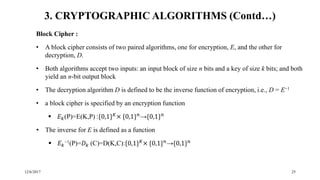
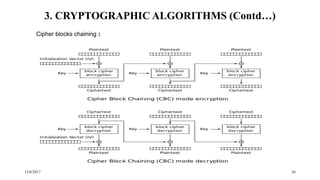
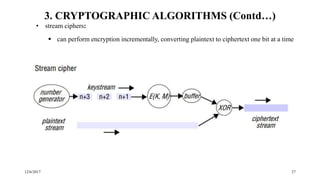
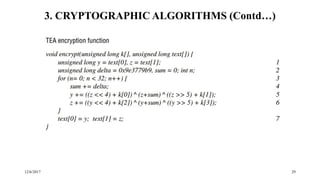
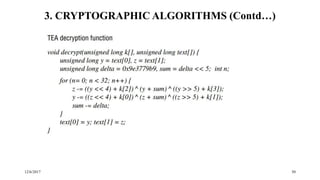
The document discusses security techniques for distributed systems. It begins with an introduction to security concepts, including threats like eavesdropping and tampering. It then provides an overview of common security techniques like cryptography, digital signatures, and certificates. Cryptography involves encrypting data using algorithms and keys. Symmetric algorithms use a shared secret key while asymmetric algorithms use public-private key pairs. The document discusses security protocols that use these techniques and then covers specific cryptographic algorithms like block ciphers and stream ciphers.























![12/6/2017 31
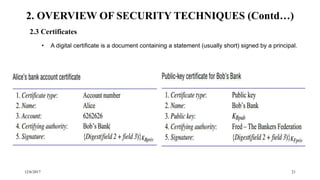
4. DIGITAL SIGNATURES
• needed in order to certify certain pieces of information
• signatures are used to meet the needs of document recipients to verify that the document is
Authentic:
Unforgeable
Non-repudiable:
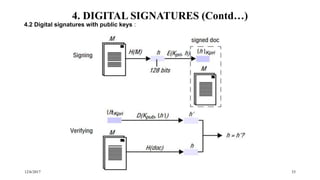
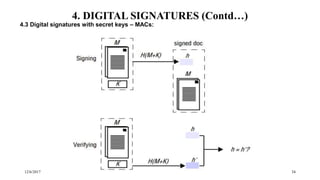
• An electronic document or message M can be signed by a principal A by encrypting a copy of M with a
key 𝐾𝐴 and attaching it to a plaintext copy of M and A’s identifier
• The signed document consists of: M, A, [𝑀] 𝐾 𝐴
• The signature can be verified by a receiver to check that it was originated by A and that its contents, M,
have not been altered.](https://image.slidesharecdn.com/security-171206142646/85/Security-31-320.jpg)