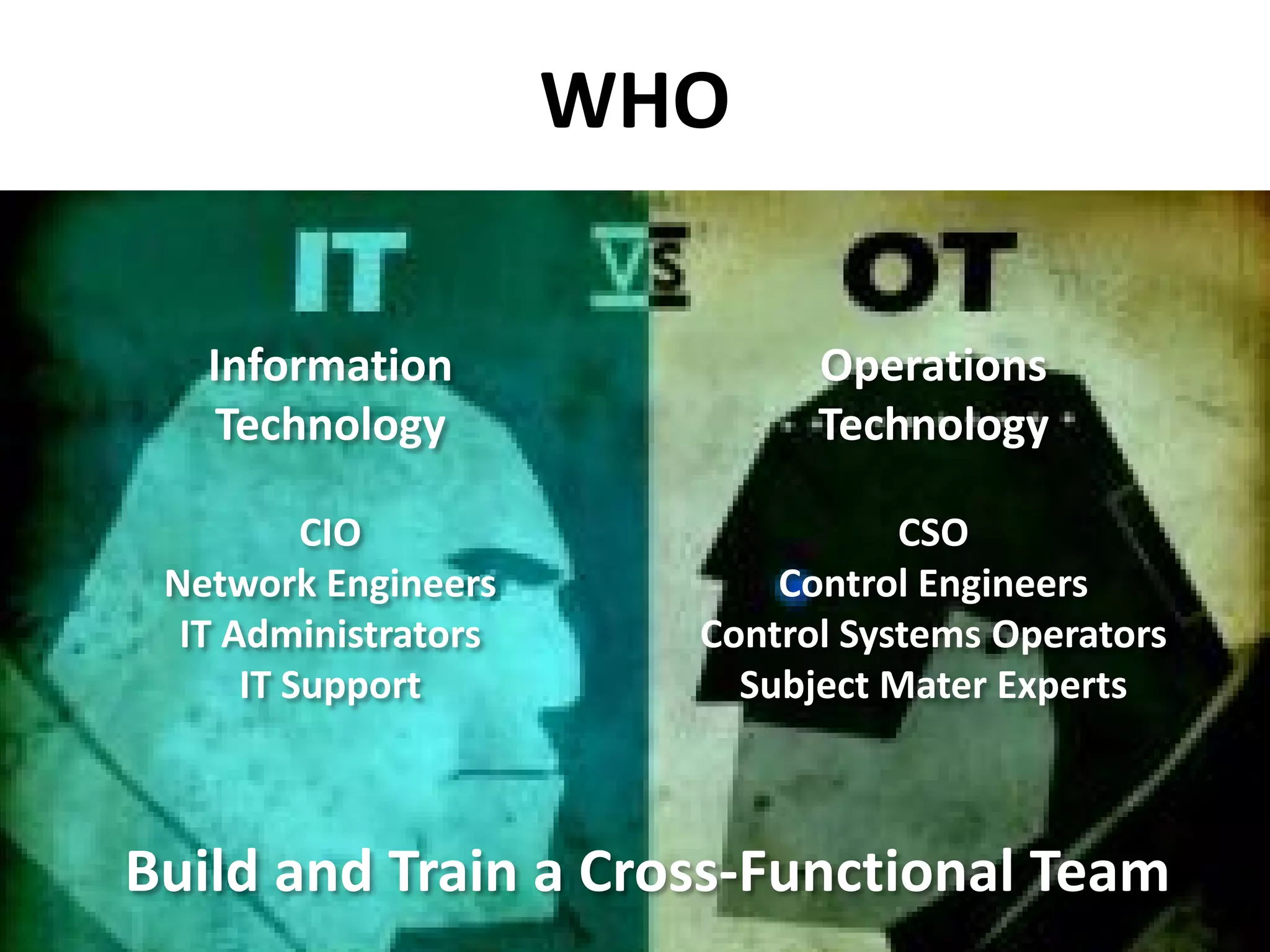
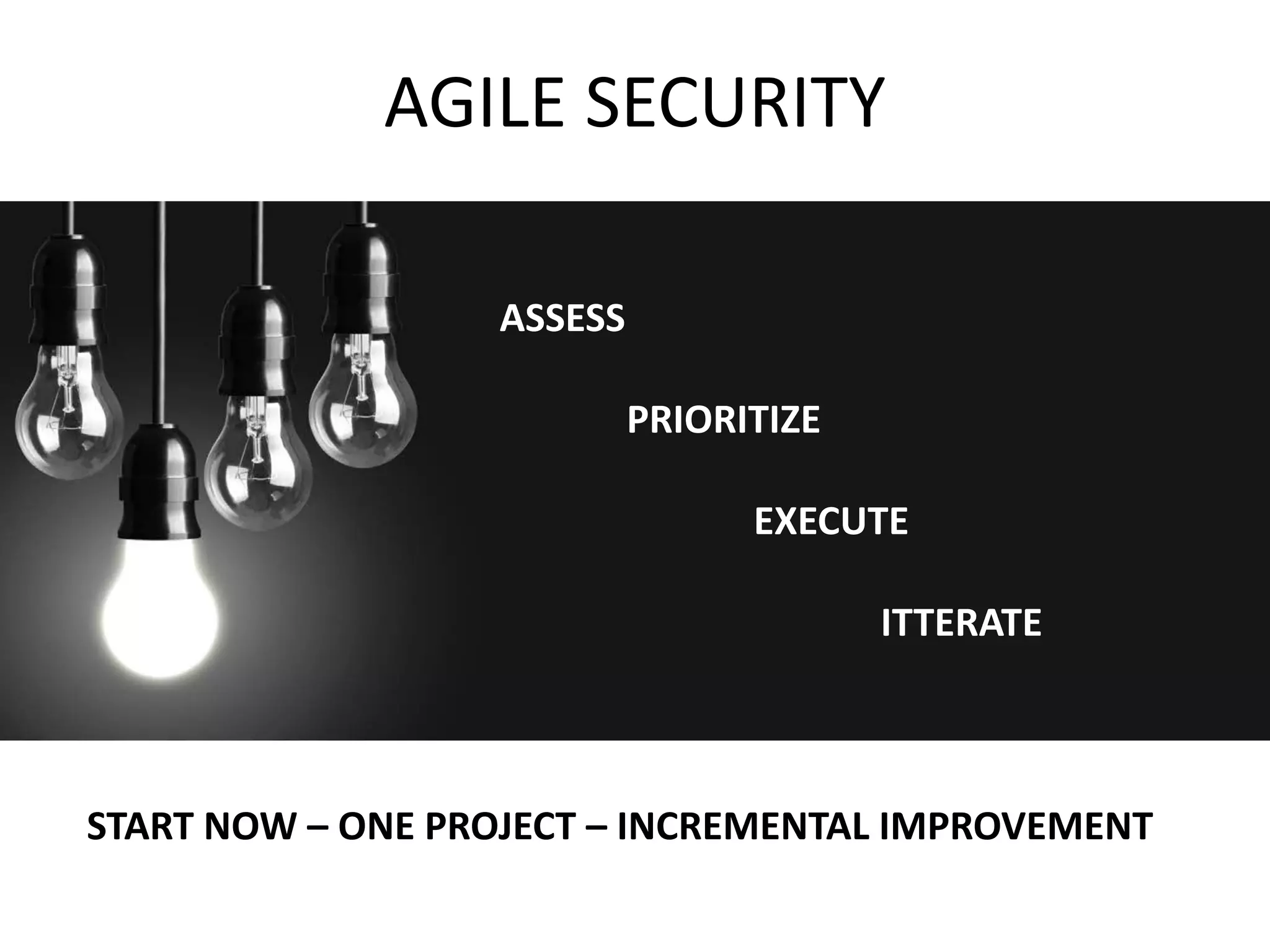
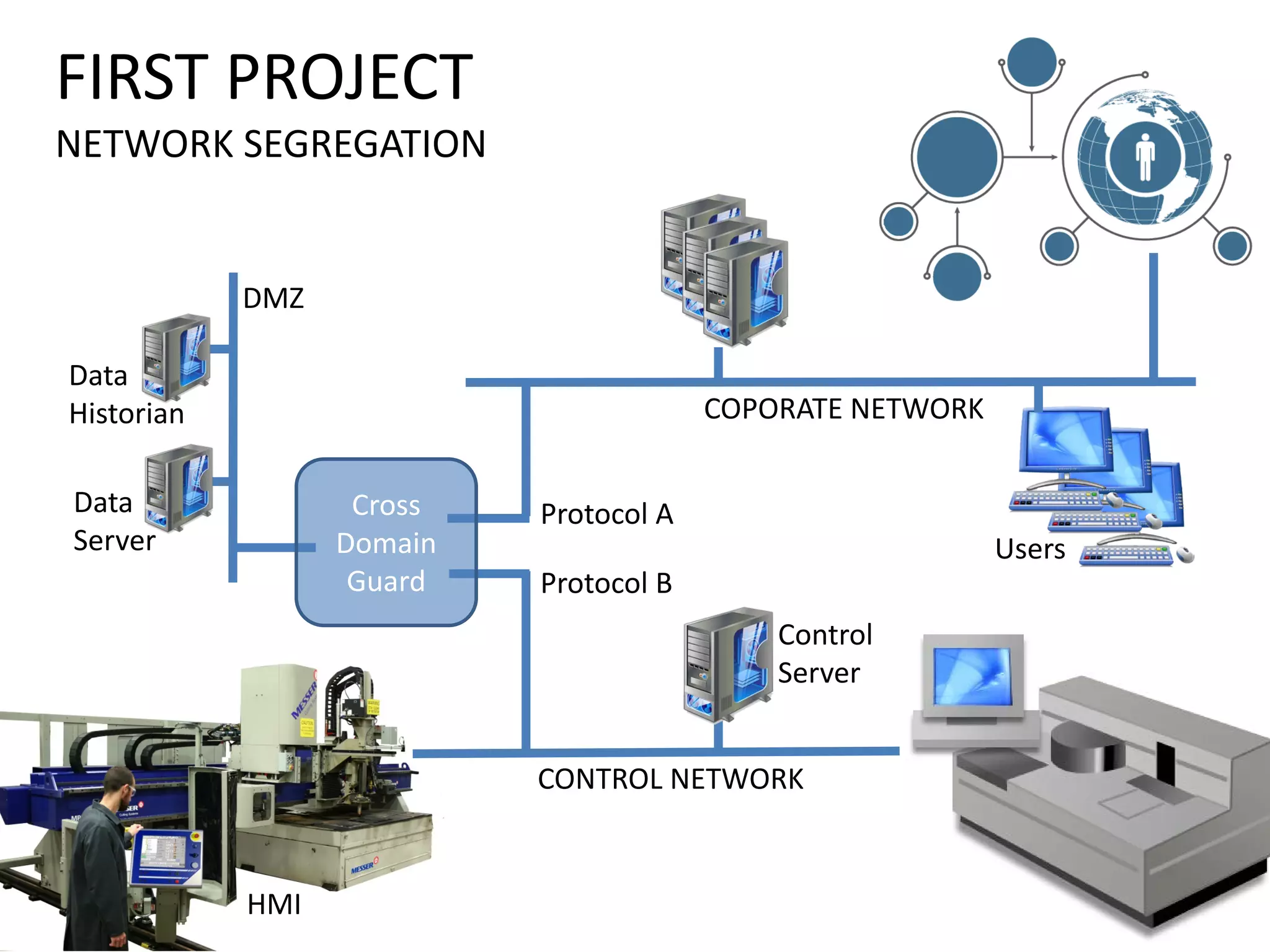
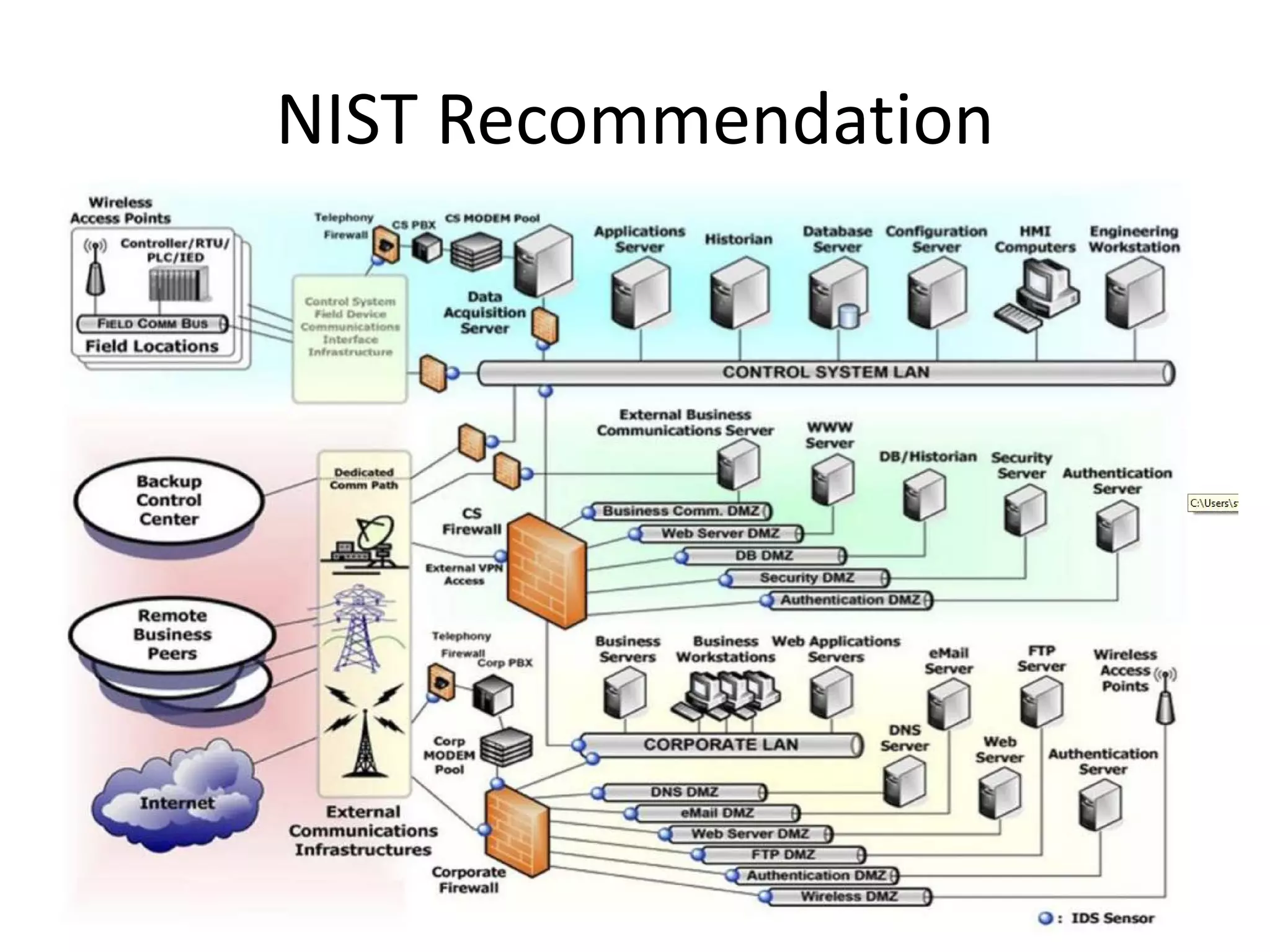
This document discusses securing the manufacturing digital thread and outlines reasons for improving security such as business stability, safety, customer requirements, and legal liabilities. It notes potential consequences of security breaches like loss of production, injury, IP theft, and damaged reputation. The document recommends assembling a cross-functional team and following an agile approach to security that starts with one project like network segregation and allows for iterative improvement.