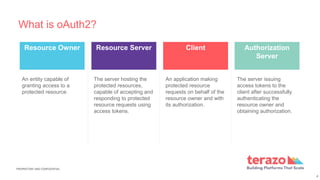
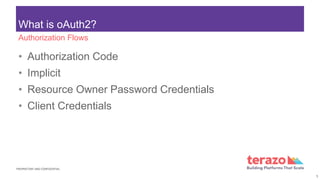
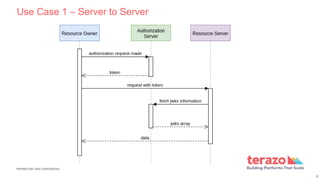
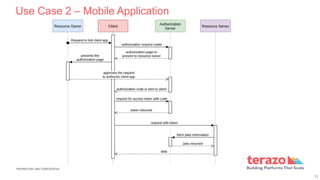
The document discusses OAuth 2.0, an authorization framework that enables third-party applications to obtain limited access to HTTP services. It outlines various components including resource owner, resource server, client, and authorization server, as well as different authorization flows like client credentials and authorization code grants. Use cases for API access include server-to-server communication and mobile application sales for agents.