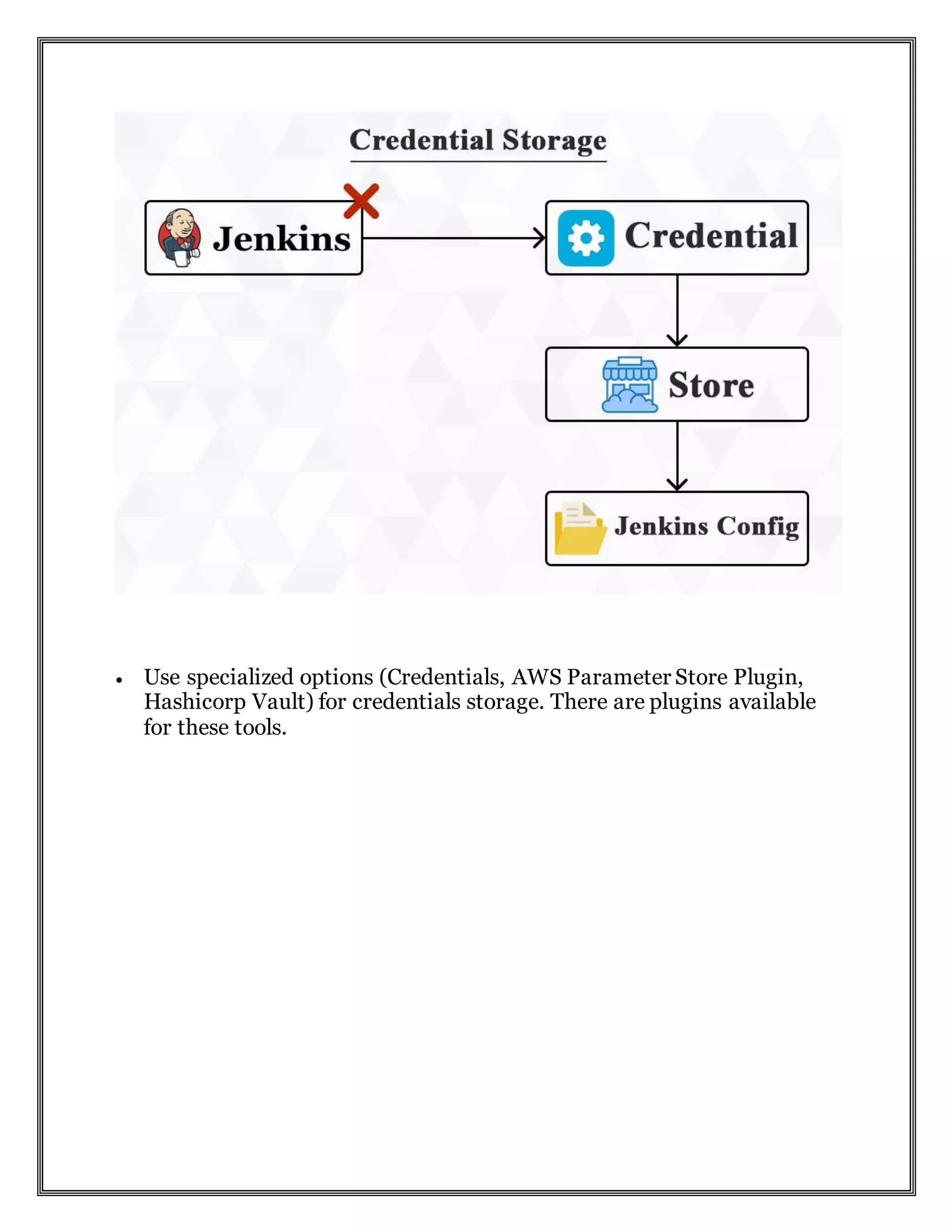
Jenkins CI requires careful security configurations beyond mere user authentication to safeguard against potential vulnerabilities. Key security practices include never storing credentials in environment variables, using specialized storage options for credentials, implementing SSL, and adhering to the principle of least privilege for access. Additional recommendations involve regular backups, job notifications, and avoiding building on a master server.