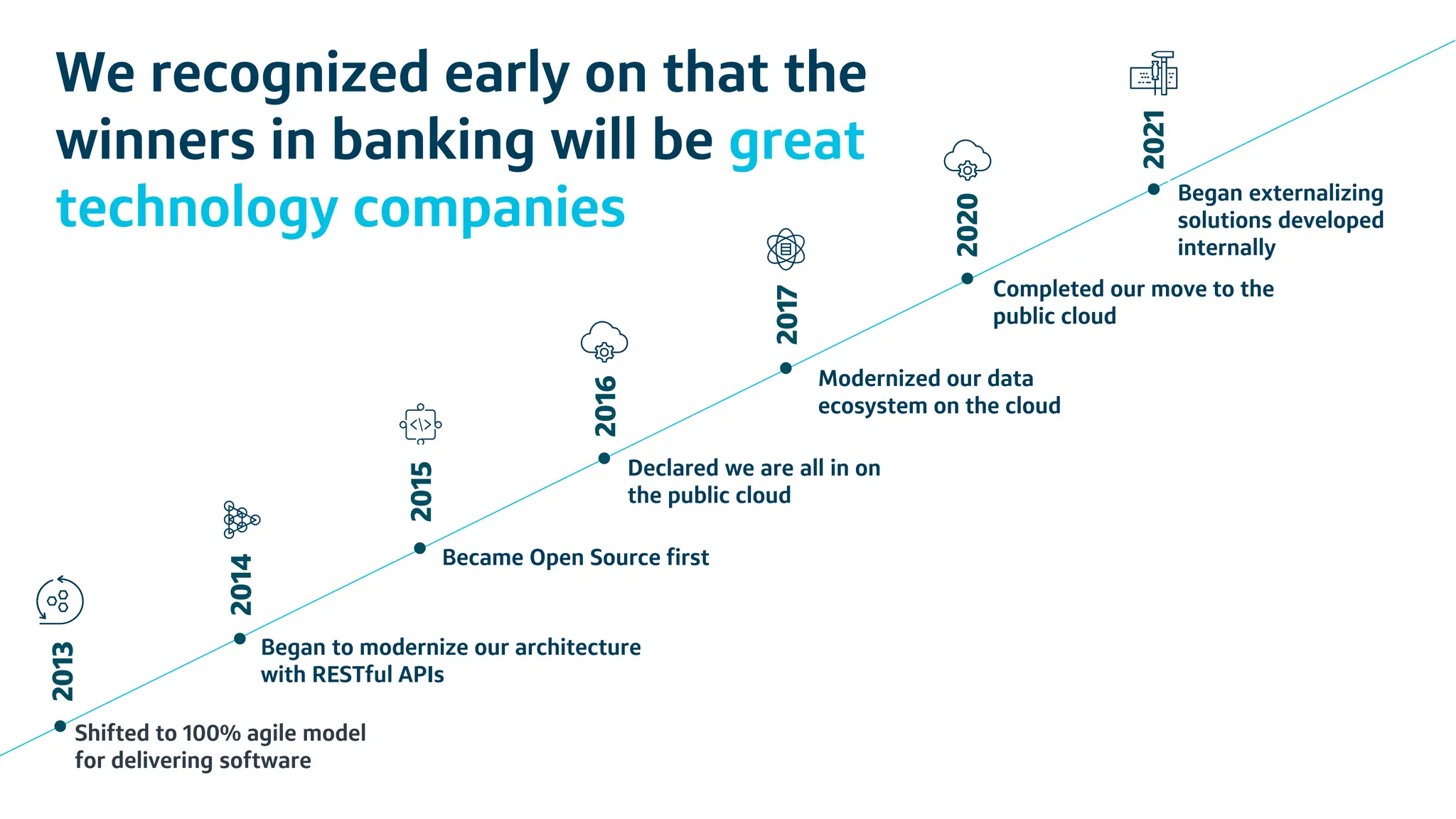
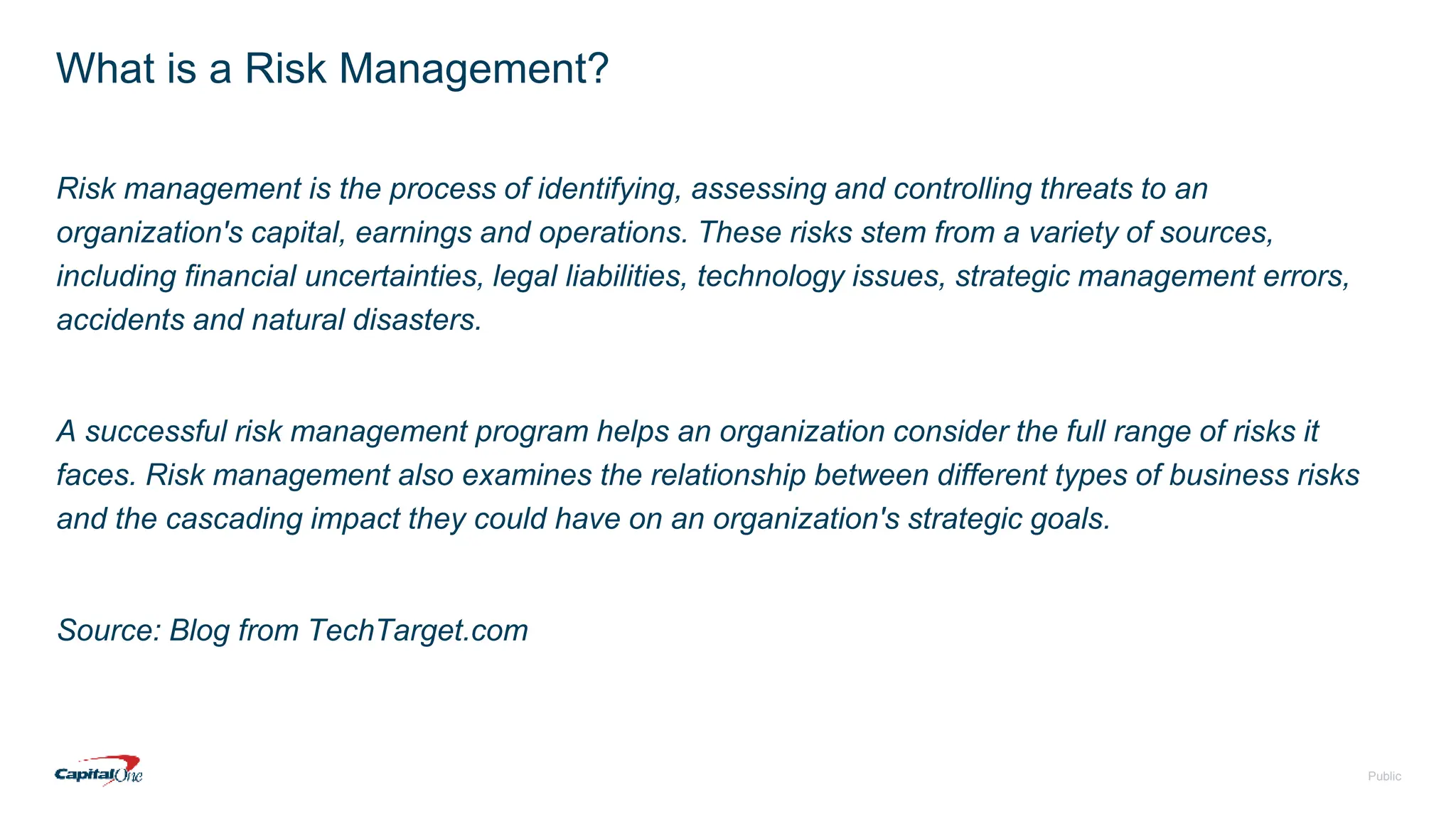
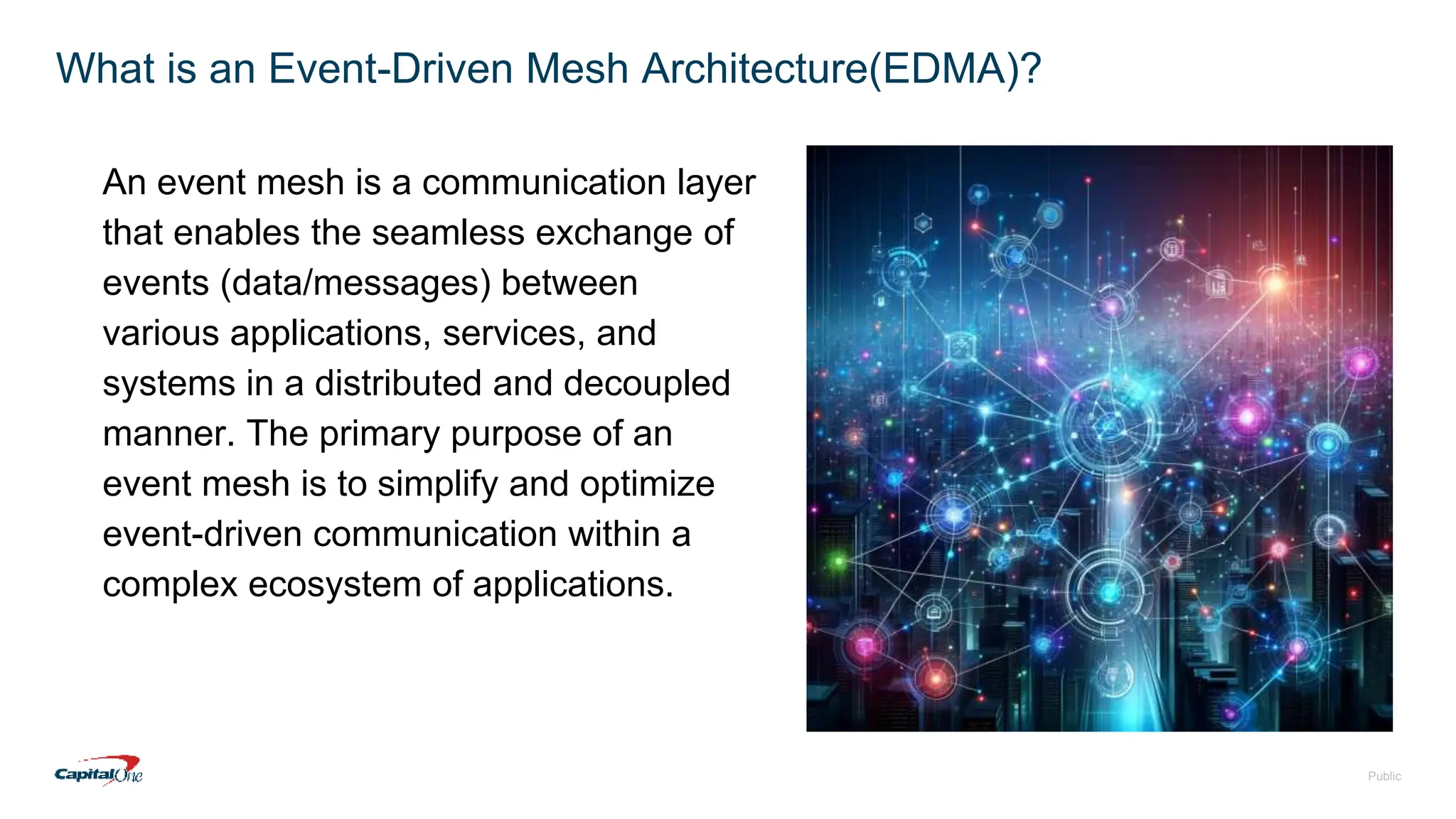
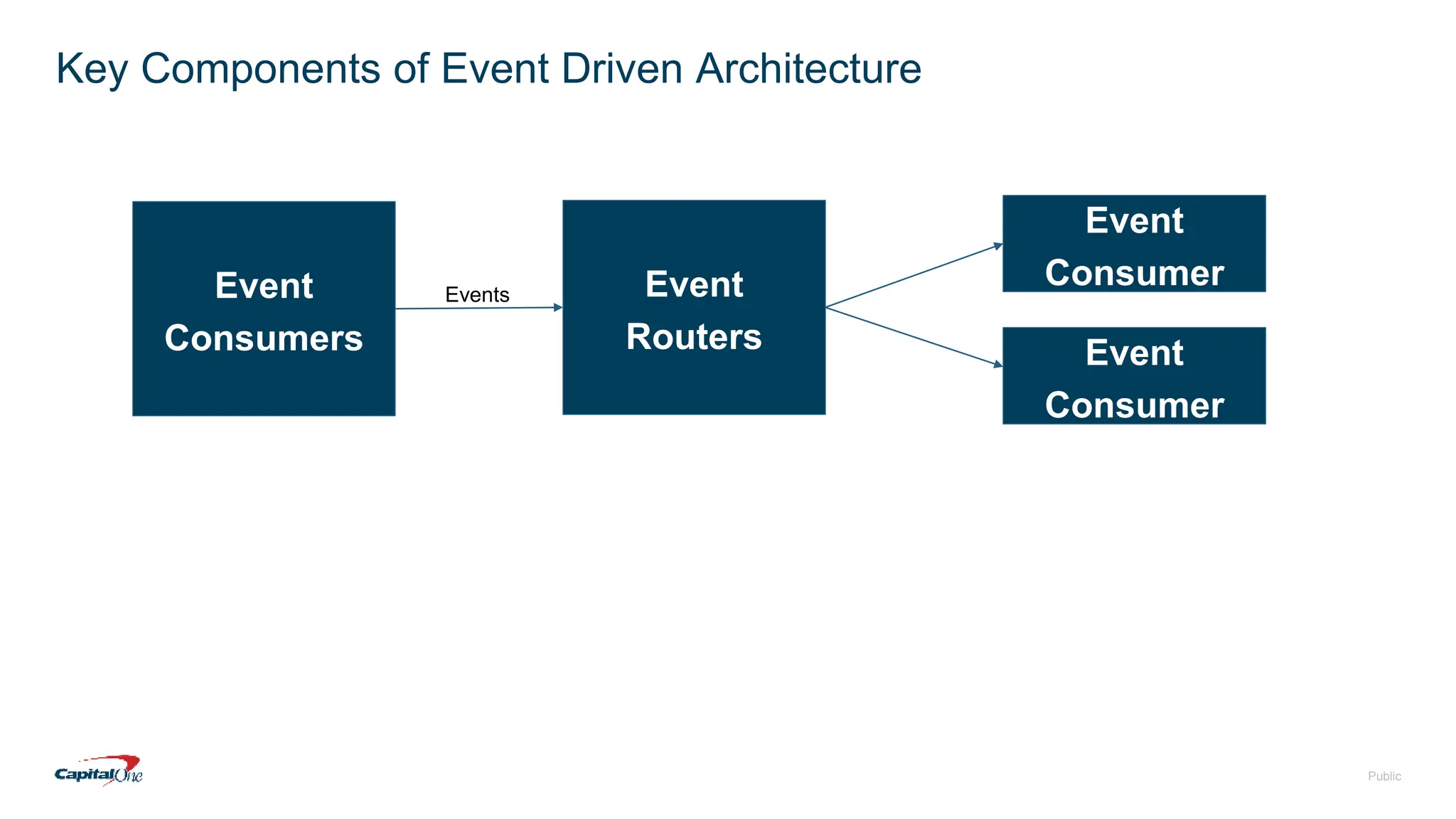
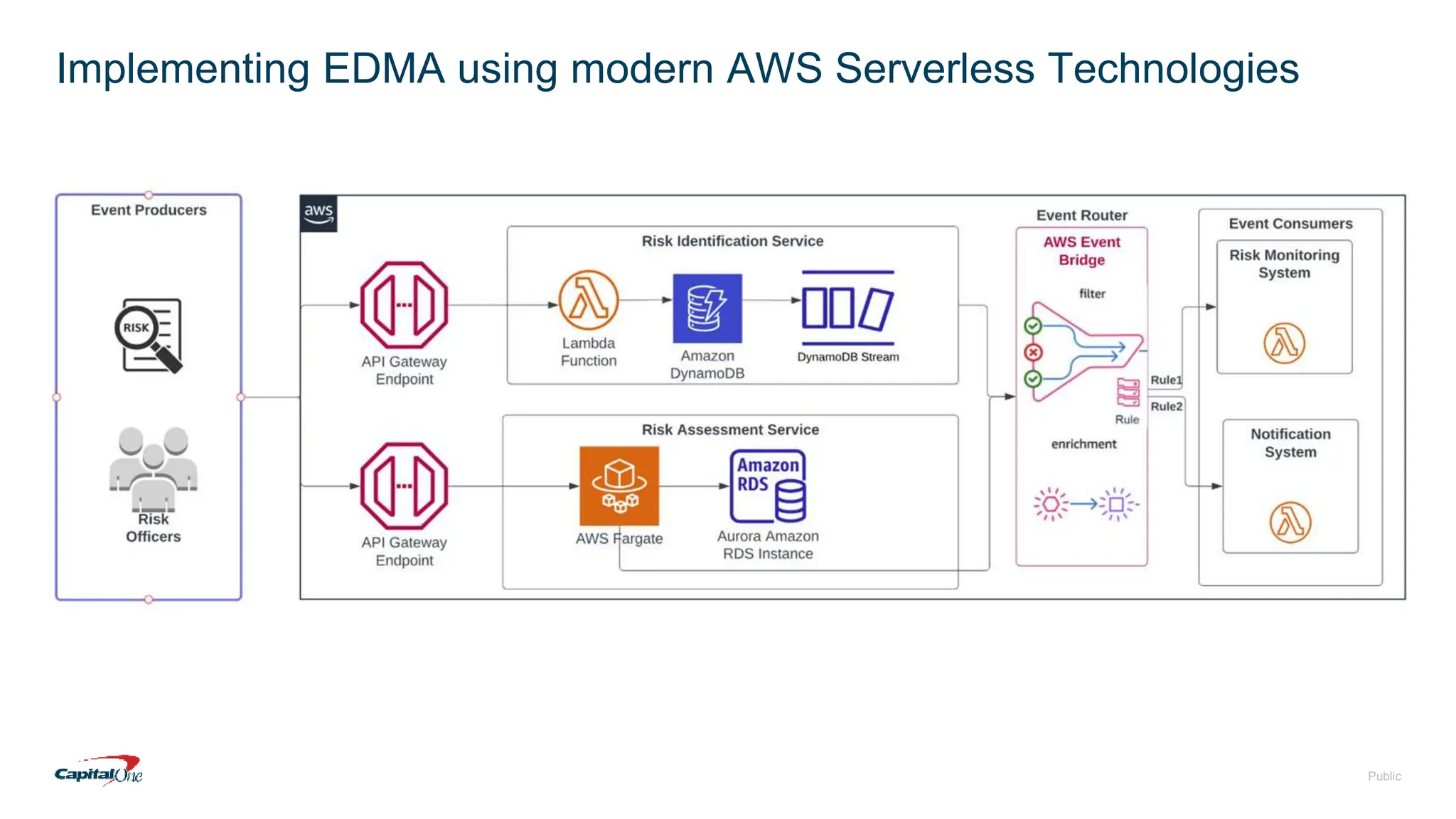
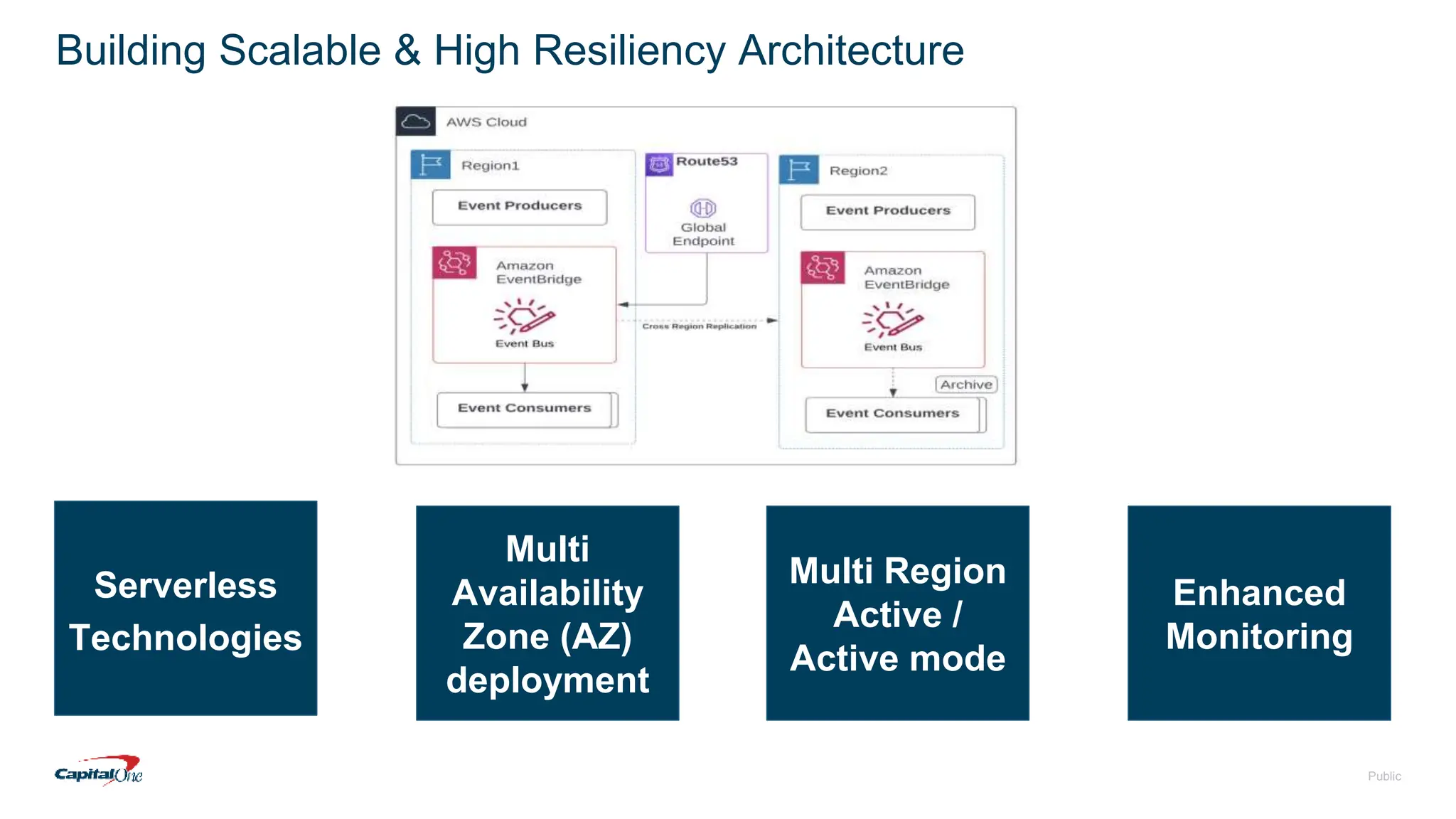
Capital One has transitioned to a cloud-first strategy and focuses on risk management through event-driven mesh architecture, which enhances real-time monitoring and response to risks. Their investment in technology includes a robust infrastructure, a culture of open-source contributions, and a commitment to creating exceptional banking experiences for customers. The document also outlines fundamental concepts of risk management and the architecture underlying event-driven systems.