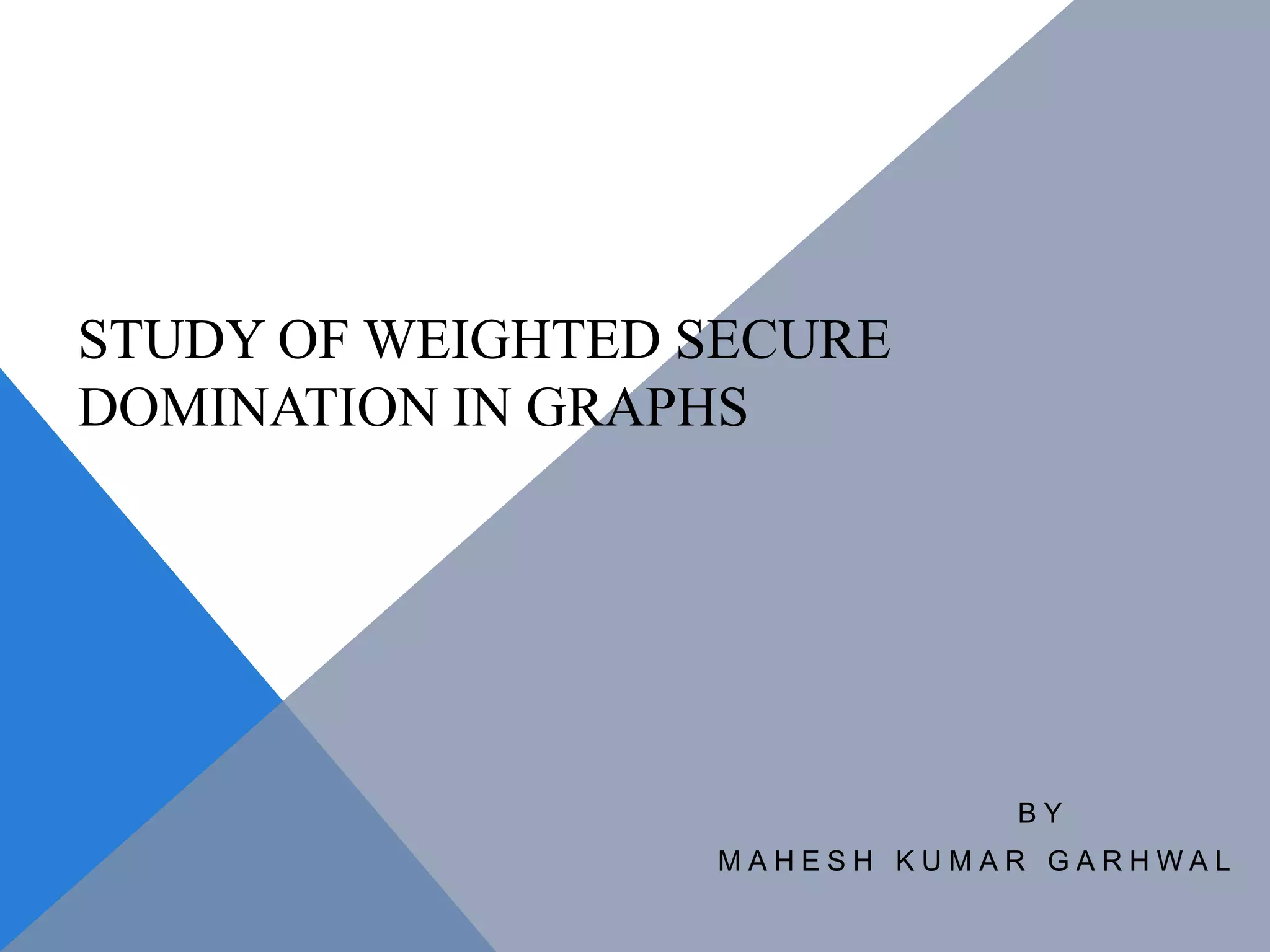
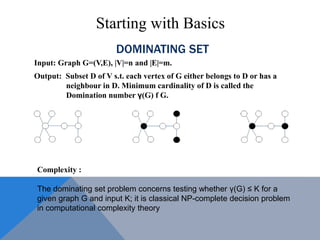
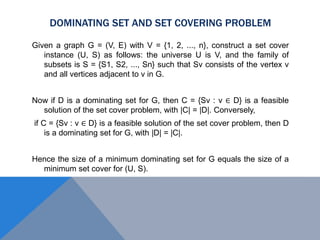
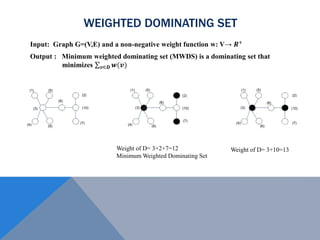
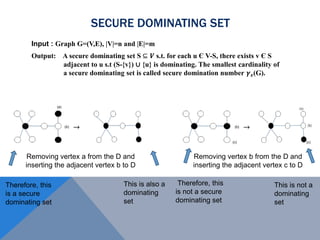
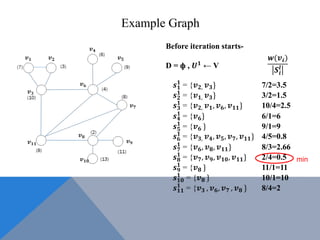
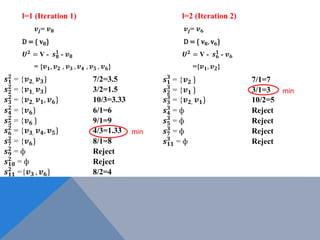
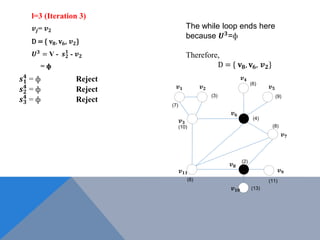
The document discusses weighted secure domination in graphs. It begins by defining domination number and weighted domination number. It proposes a greedy algorithm that provides a 1 + log(n) approximation for weighted domination number. The algorithm works by iteratively selecting the unselected vertex with the minimum ratio of weight to number of uncovered neighbors. This achieves an approximation ratio of H(n), which is at most 1 + log(n). The algorithm runs in polynomial time.