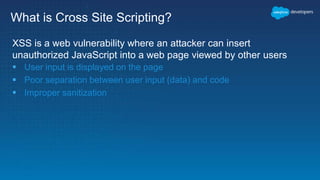
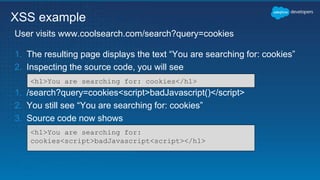
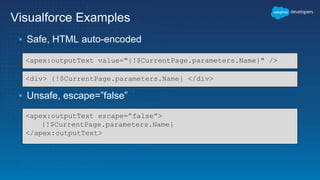
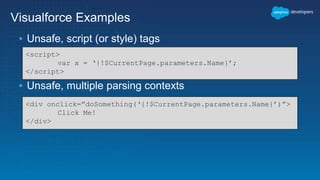
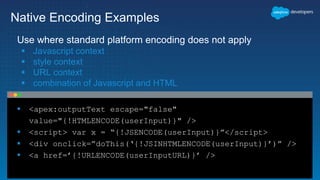
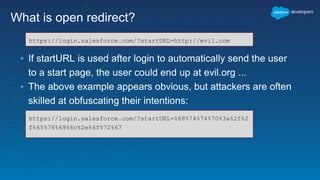
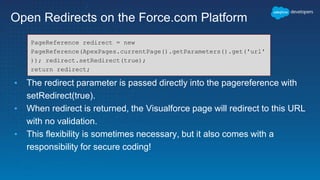
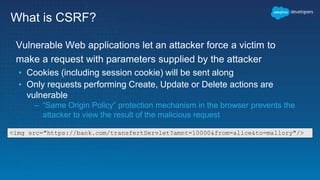
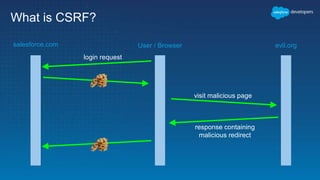
The document discusses secure development practices on the Salesforce platform. It covers topics like cross-site scripting (XSS), open redirects, and cross-site request forgery (CSRF). For XSS, it describes different types (reflected, stored, DOM) and provides examples of how to properly encode output. For open redirects, it explains the risk and best practices like whitelisting URLs. For CSRF, it discusses how to prevent malicious requests by using tokens validated on the server. The document aims to help developers understand and address common vulnerabilities.