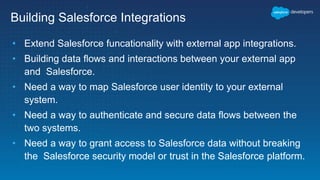
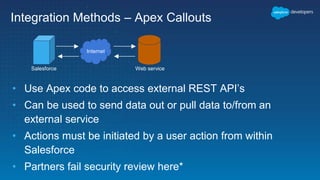
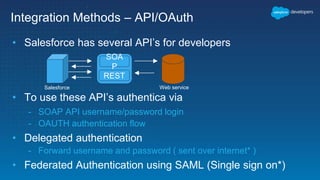
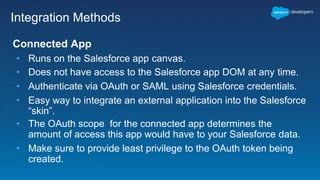
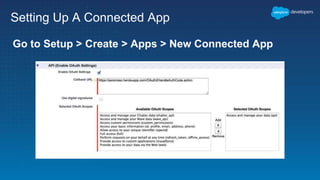
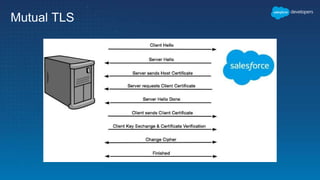
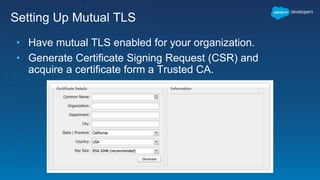
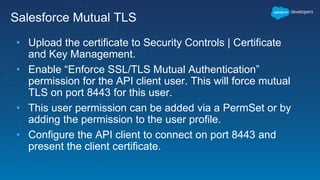
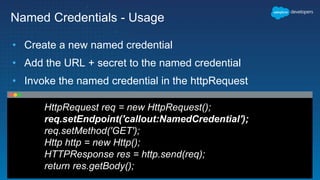
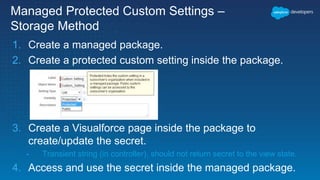
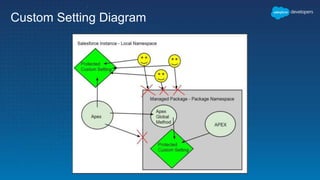
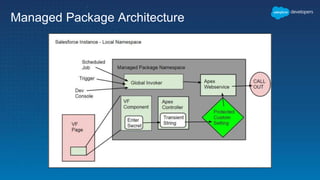
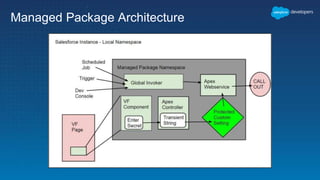
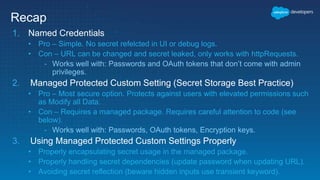
This document outlines the integration of external applications with Salesforce, addressing security measures such as API authentication, OAuth, and mutual TLS. It emphasizes the importance of secret protection through named credentials and managed protected custom settings for safeguarding sensitive data. Various integration methods and best practices for secure communication and data flow between Salesforce and external systems are also discussed.