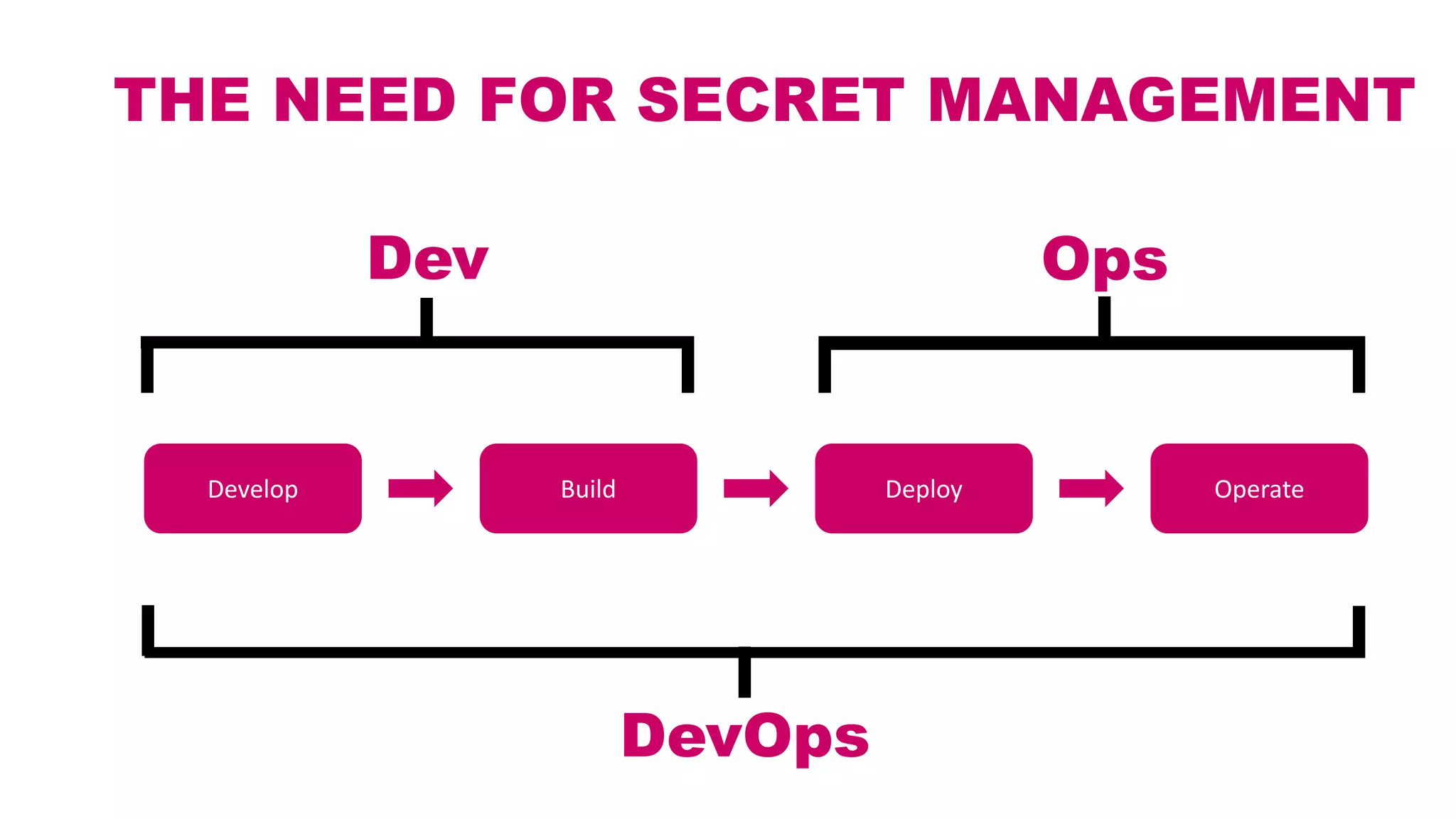
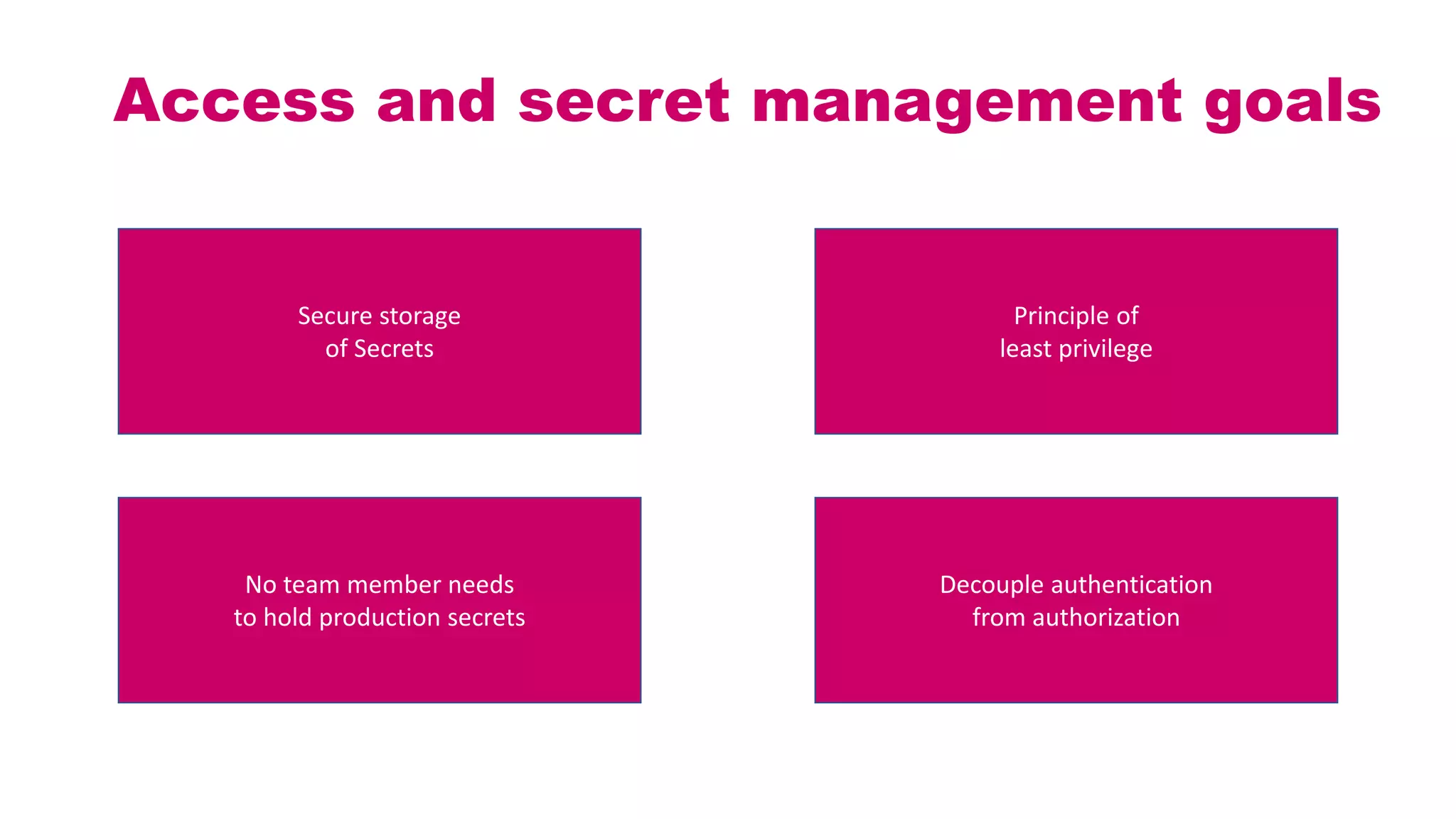
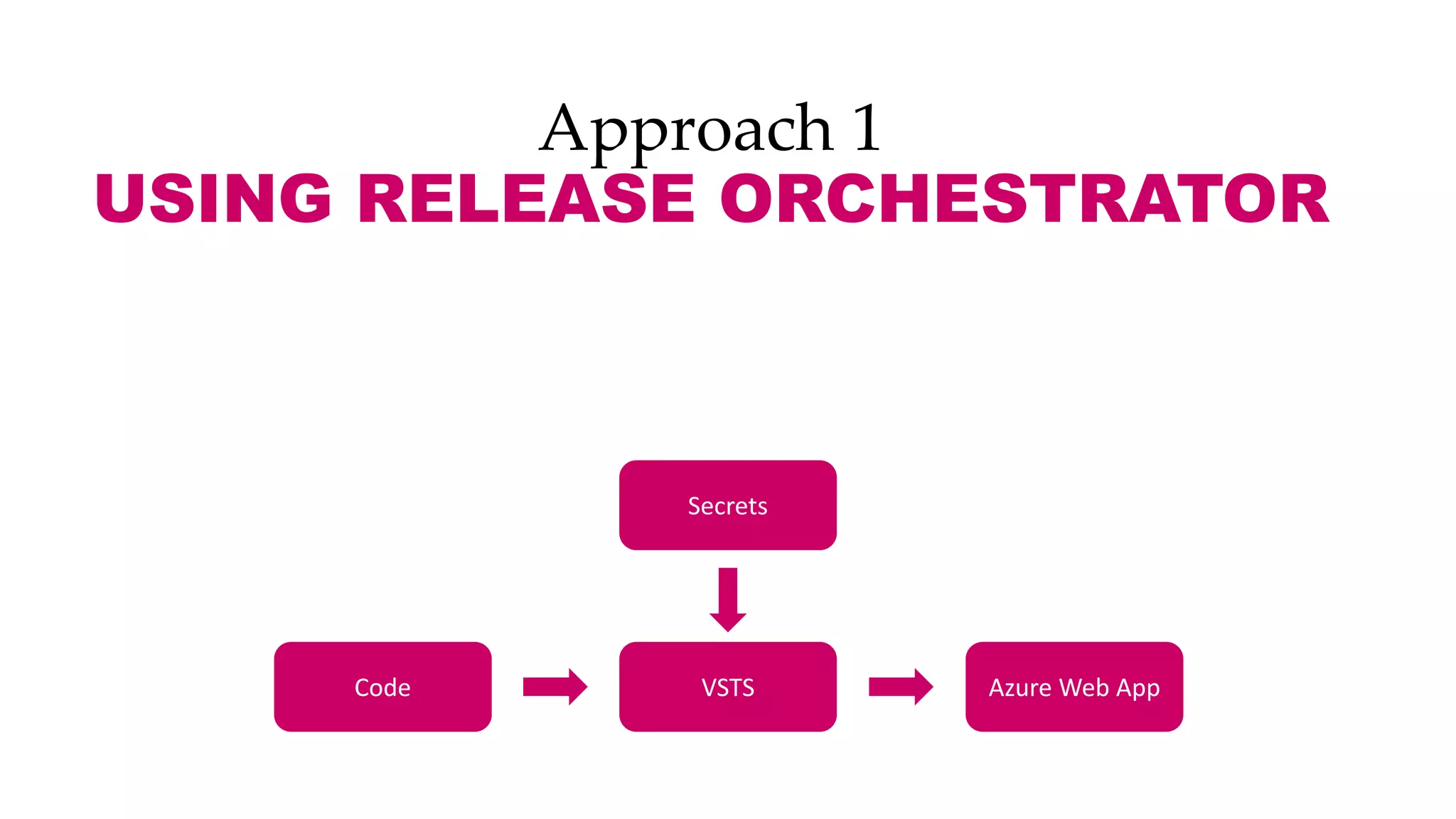
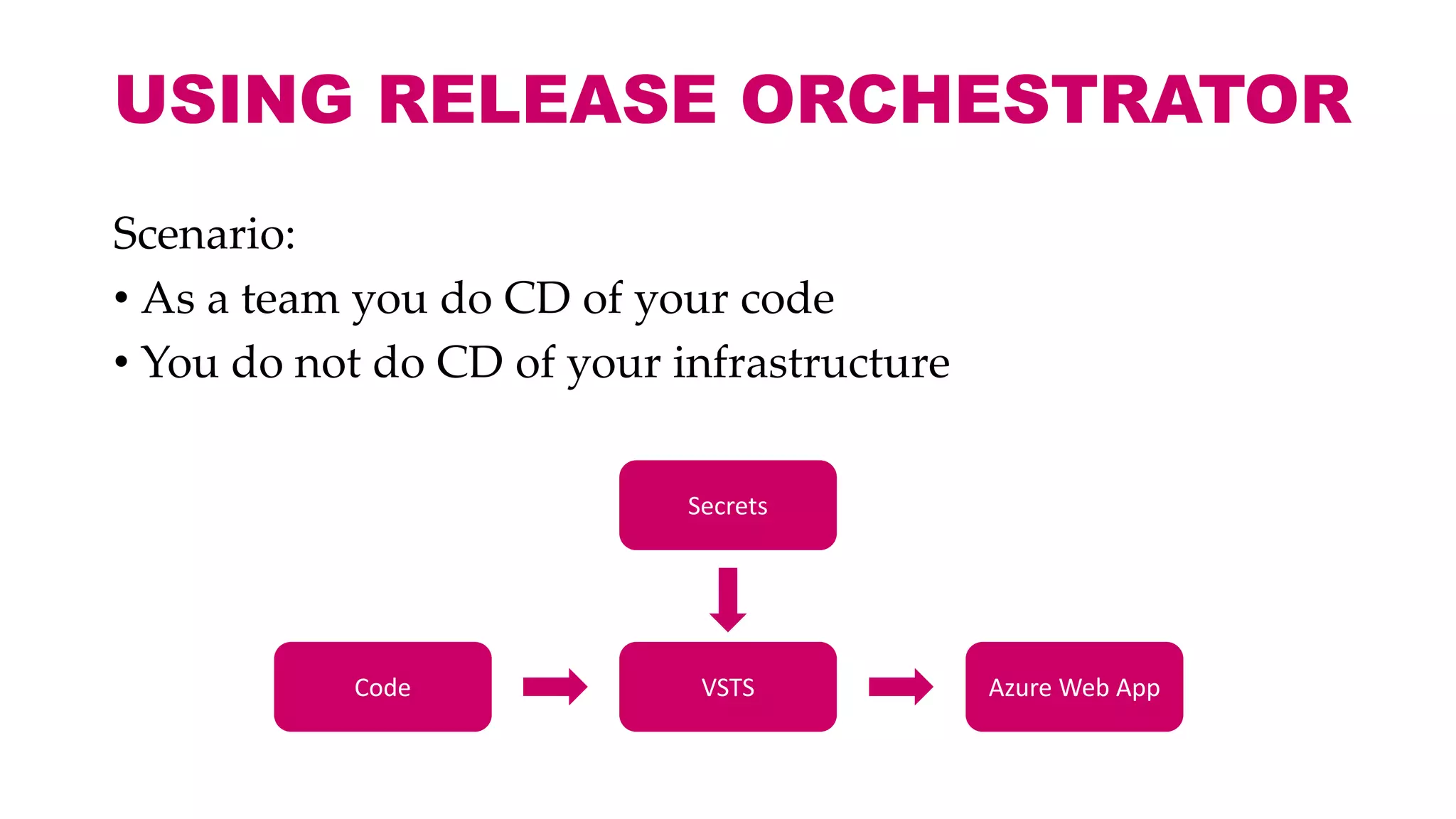
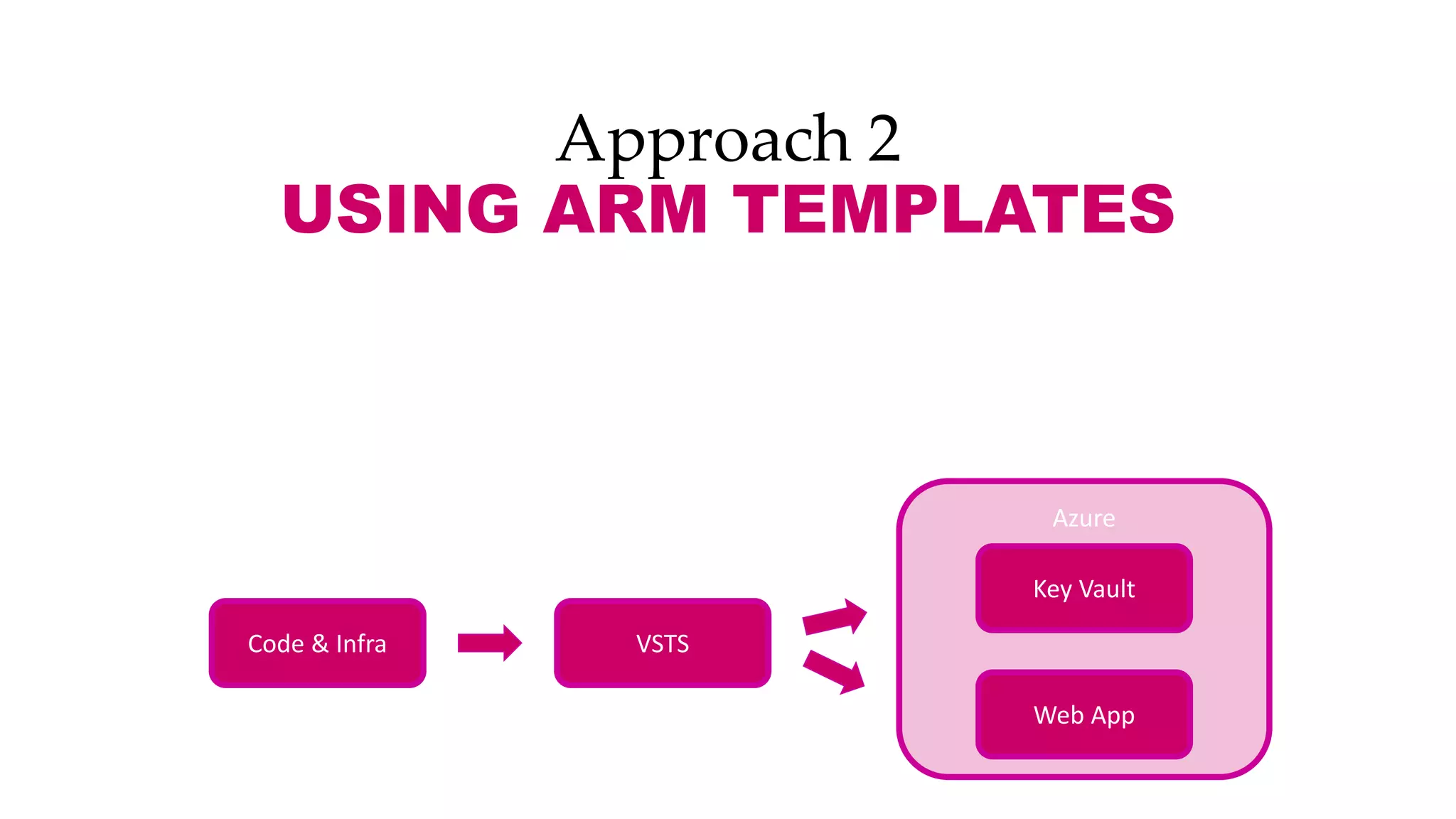
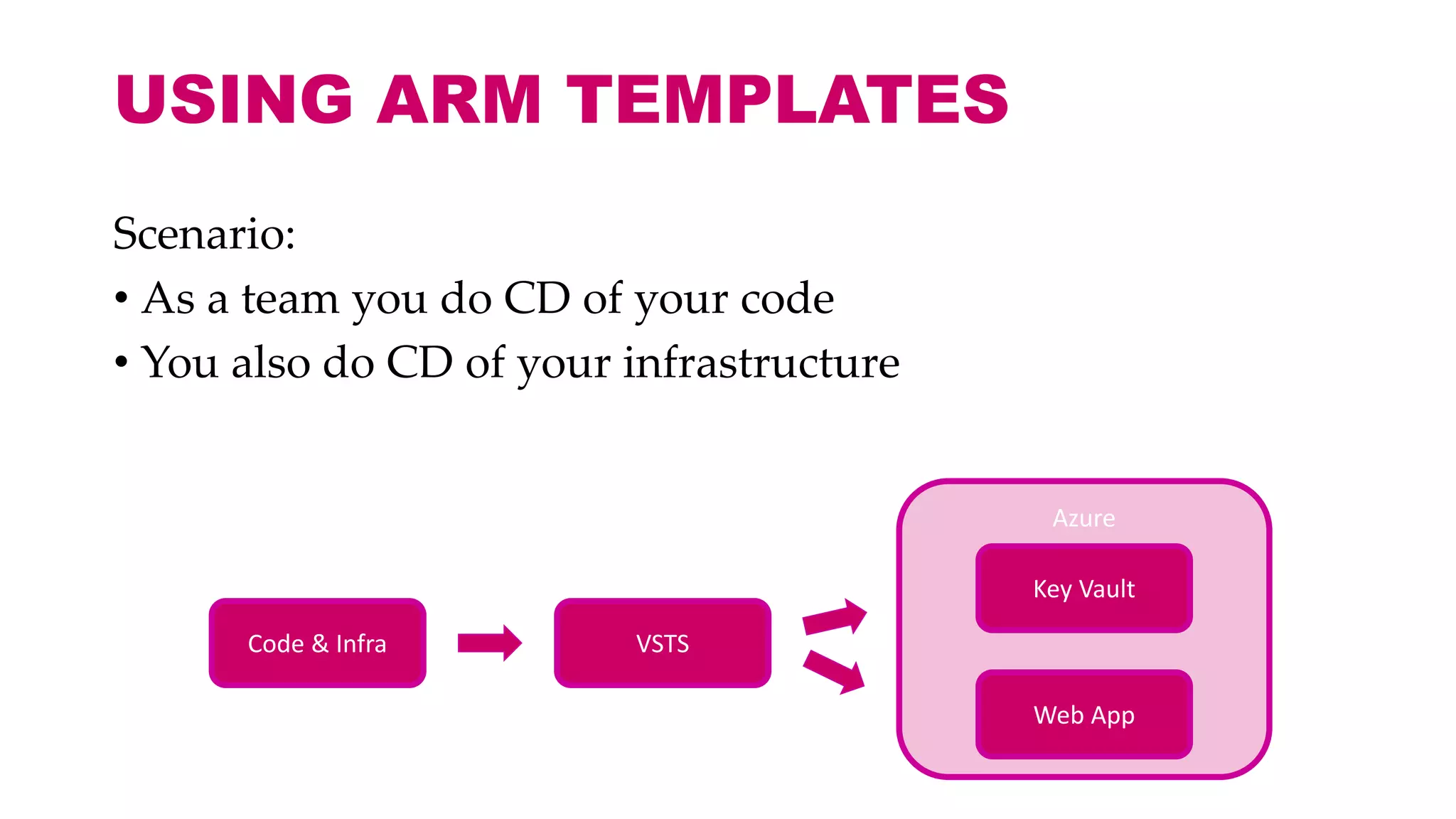
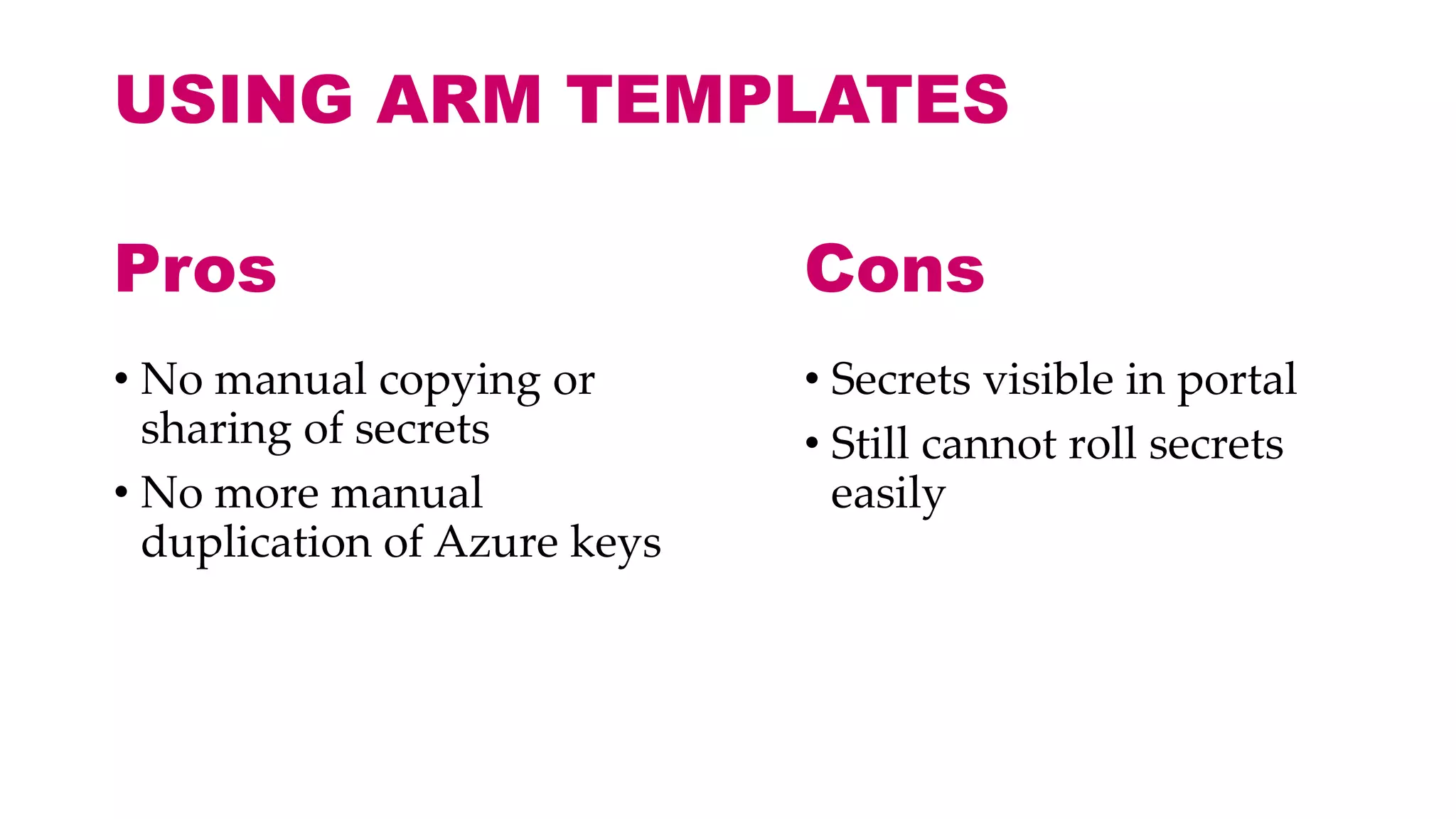
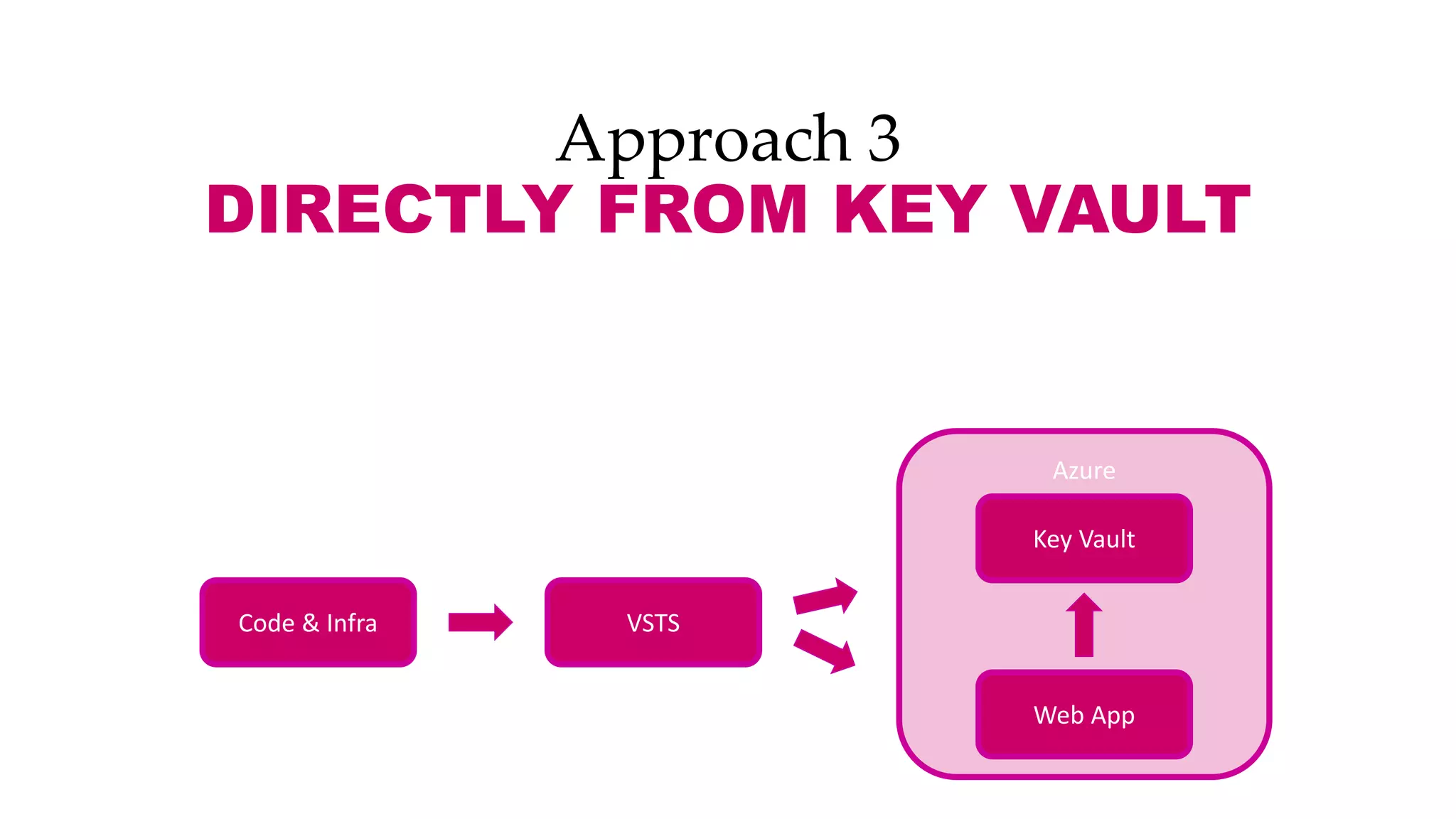
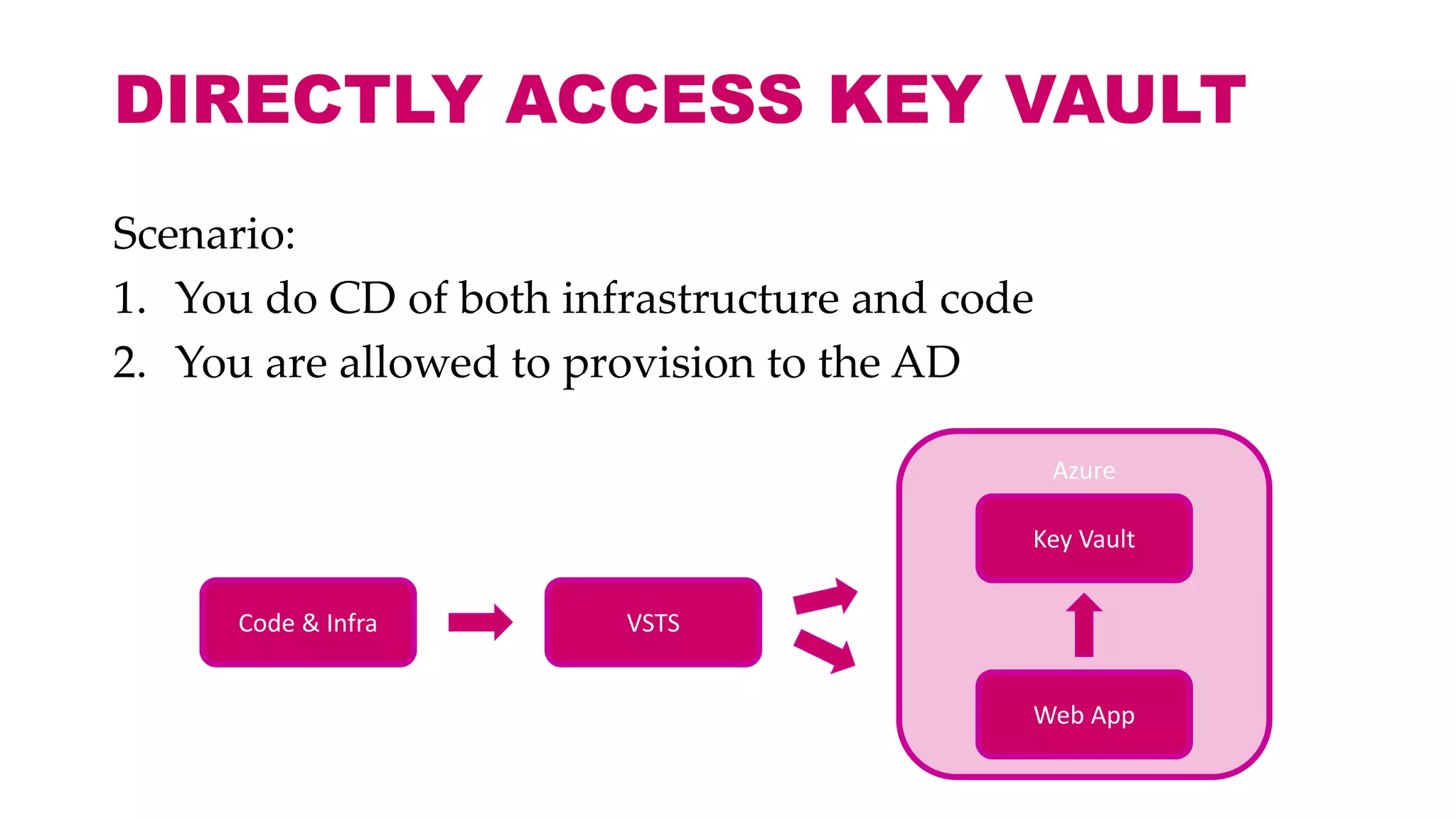
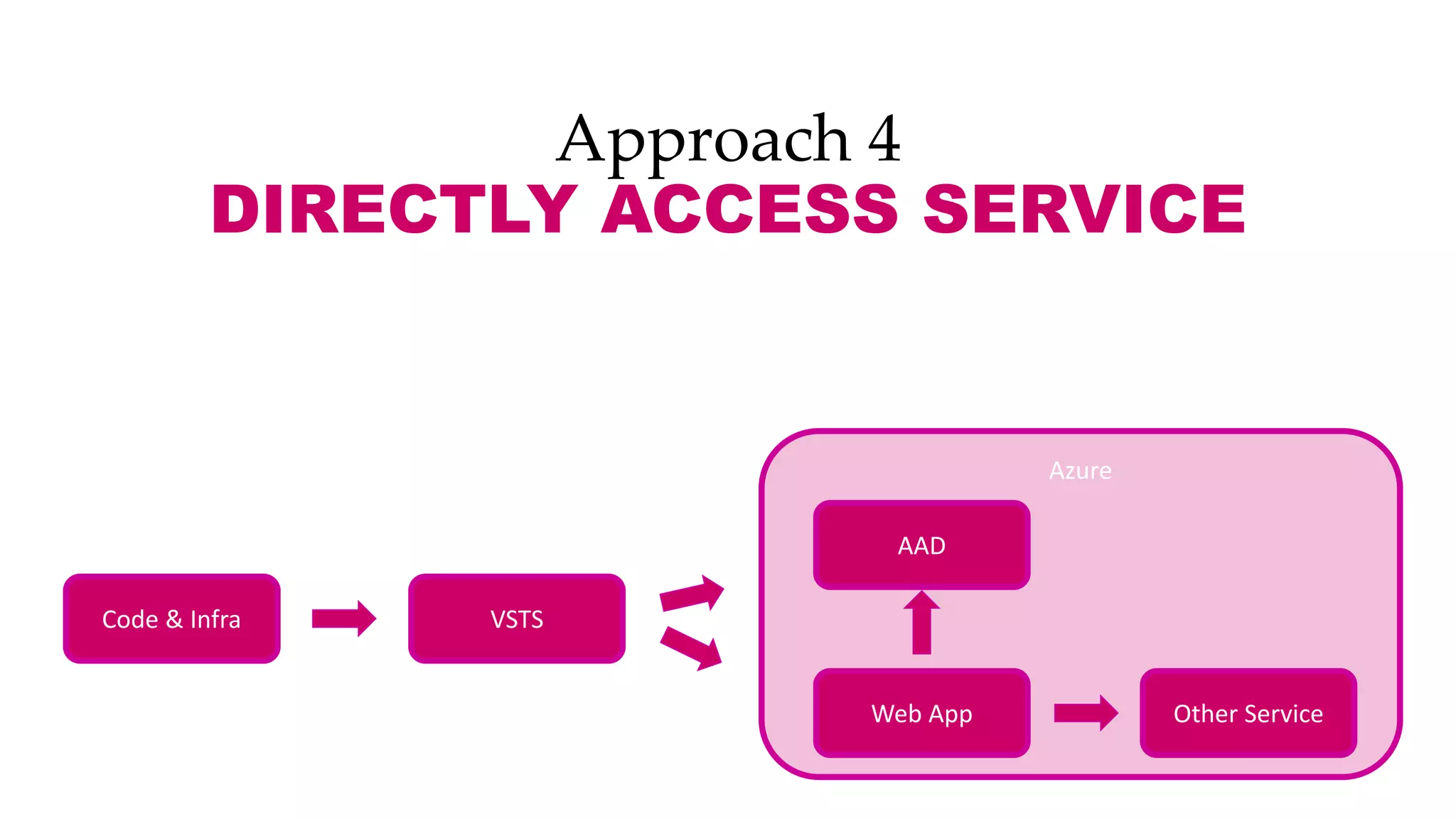
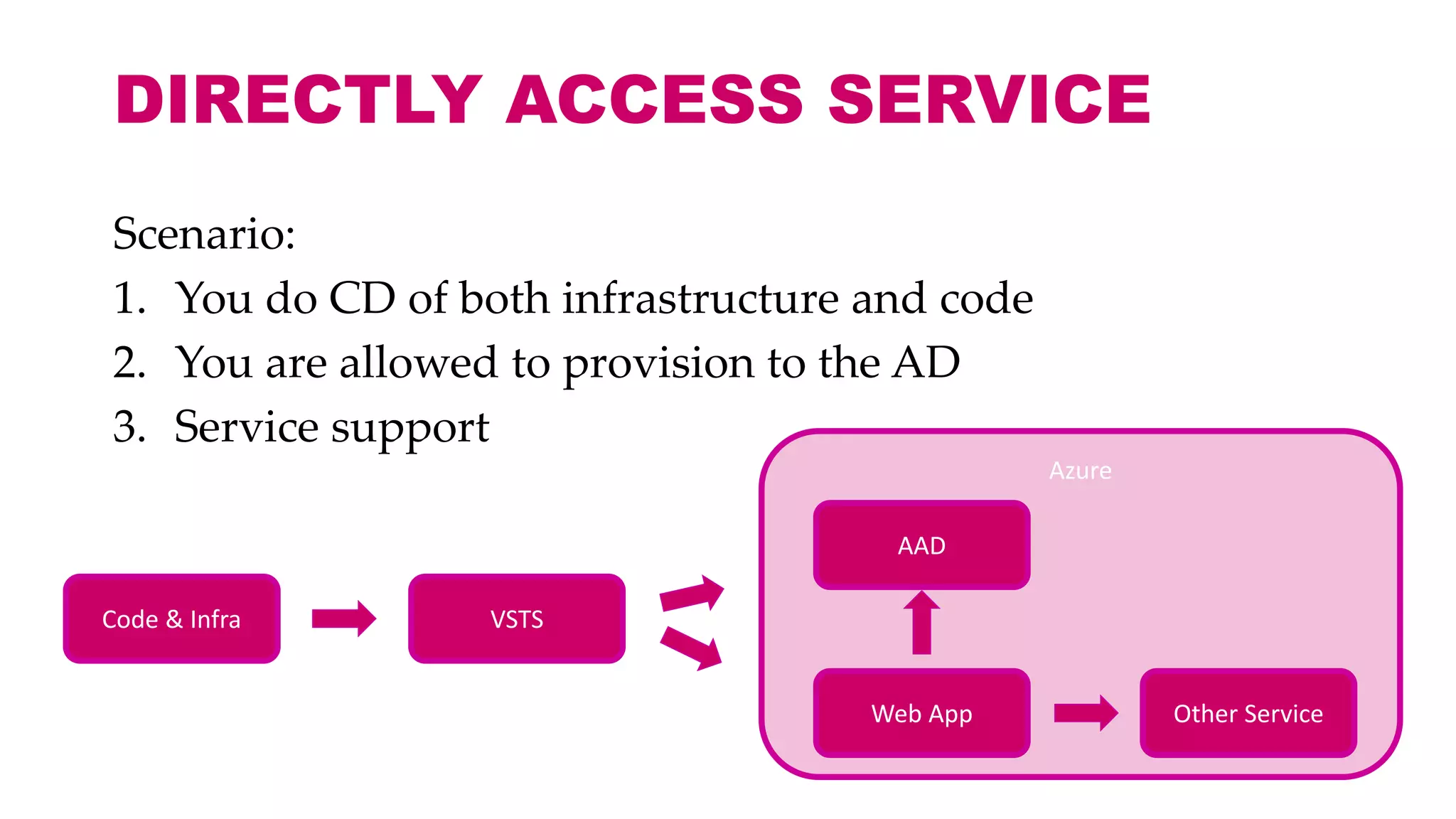
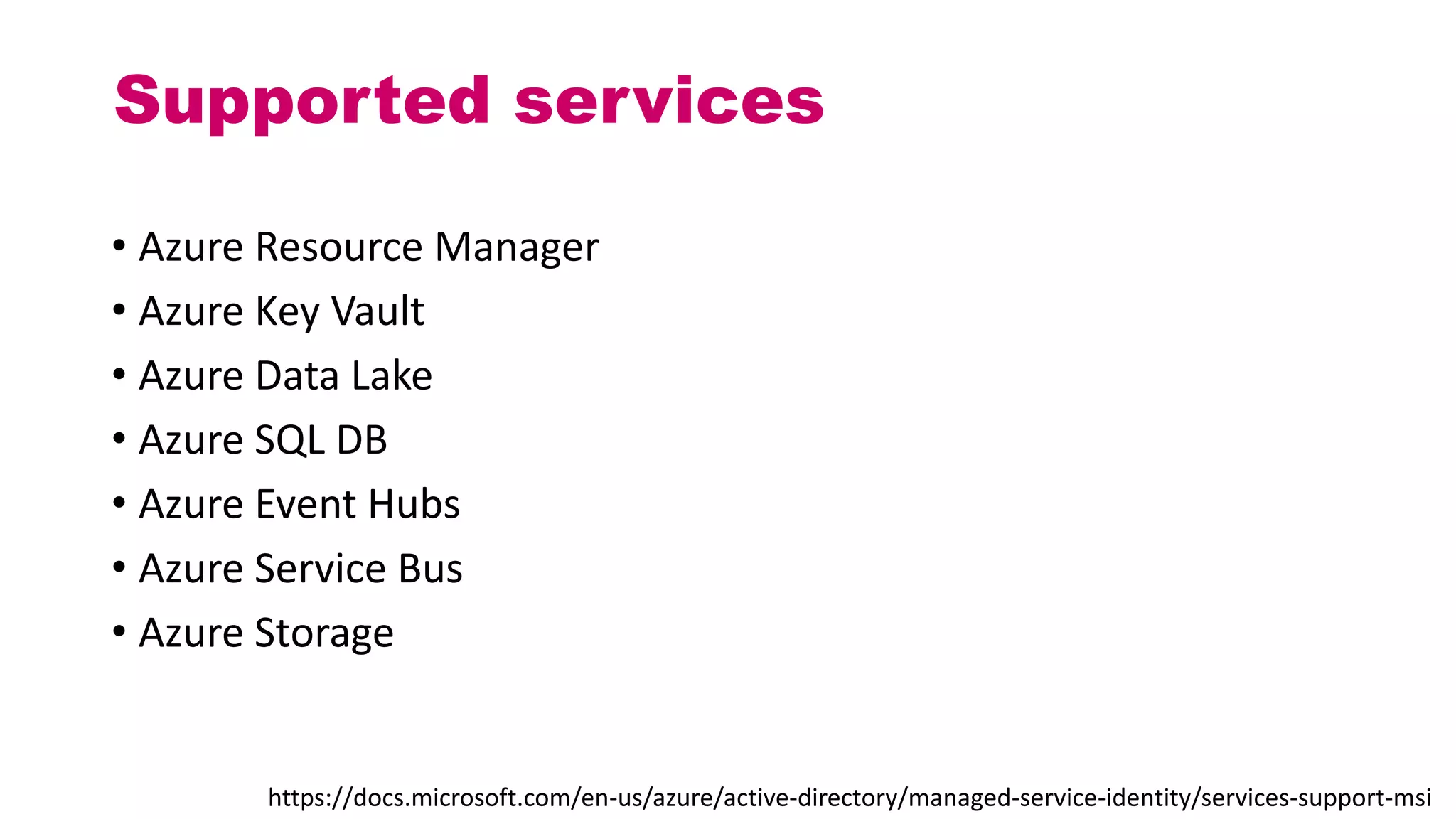
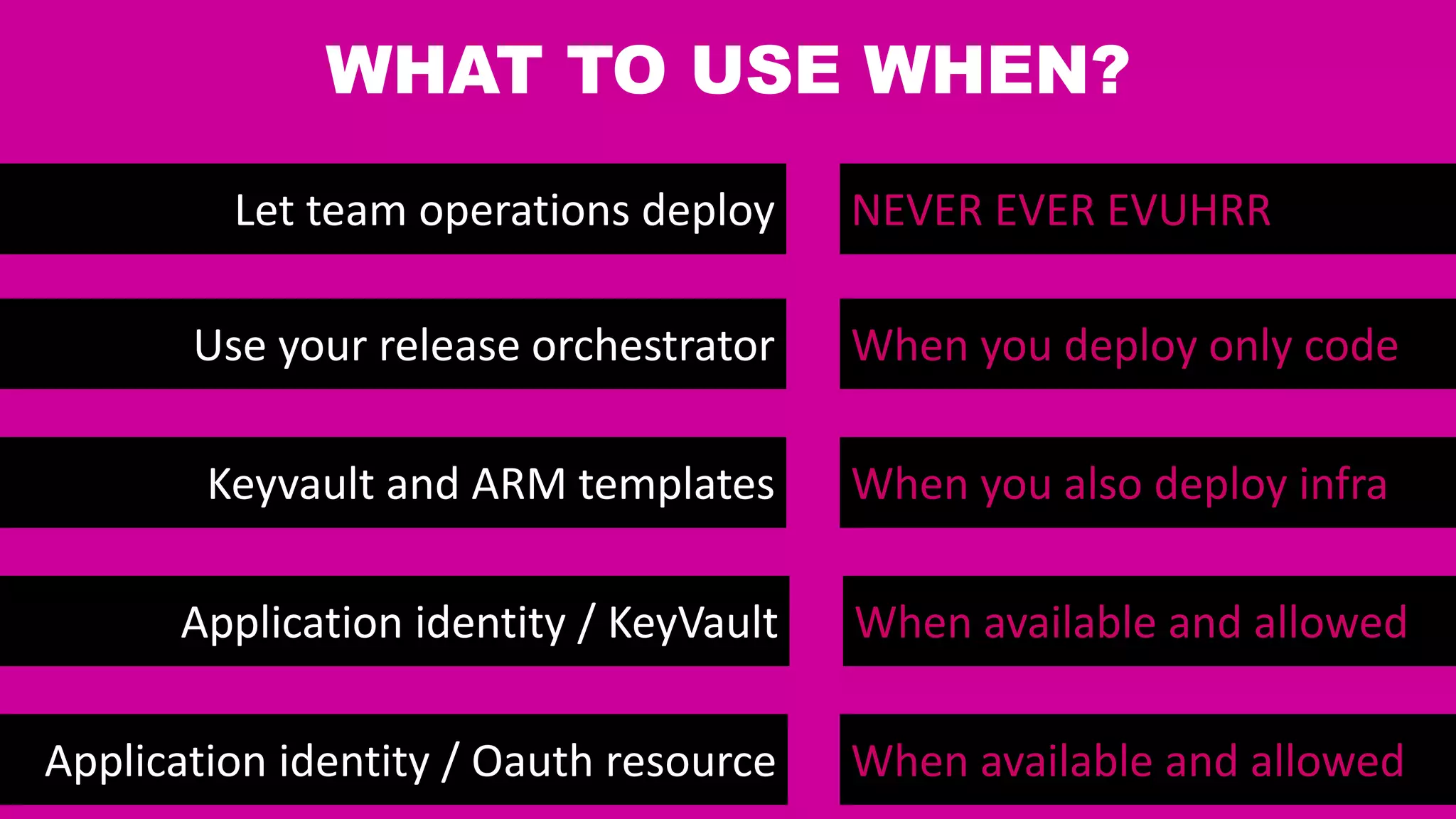
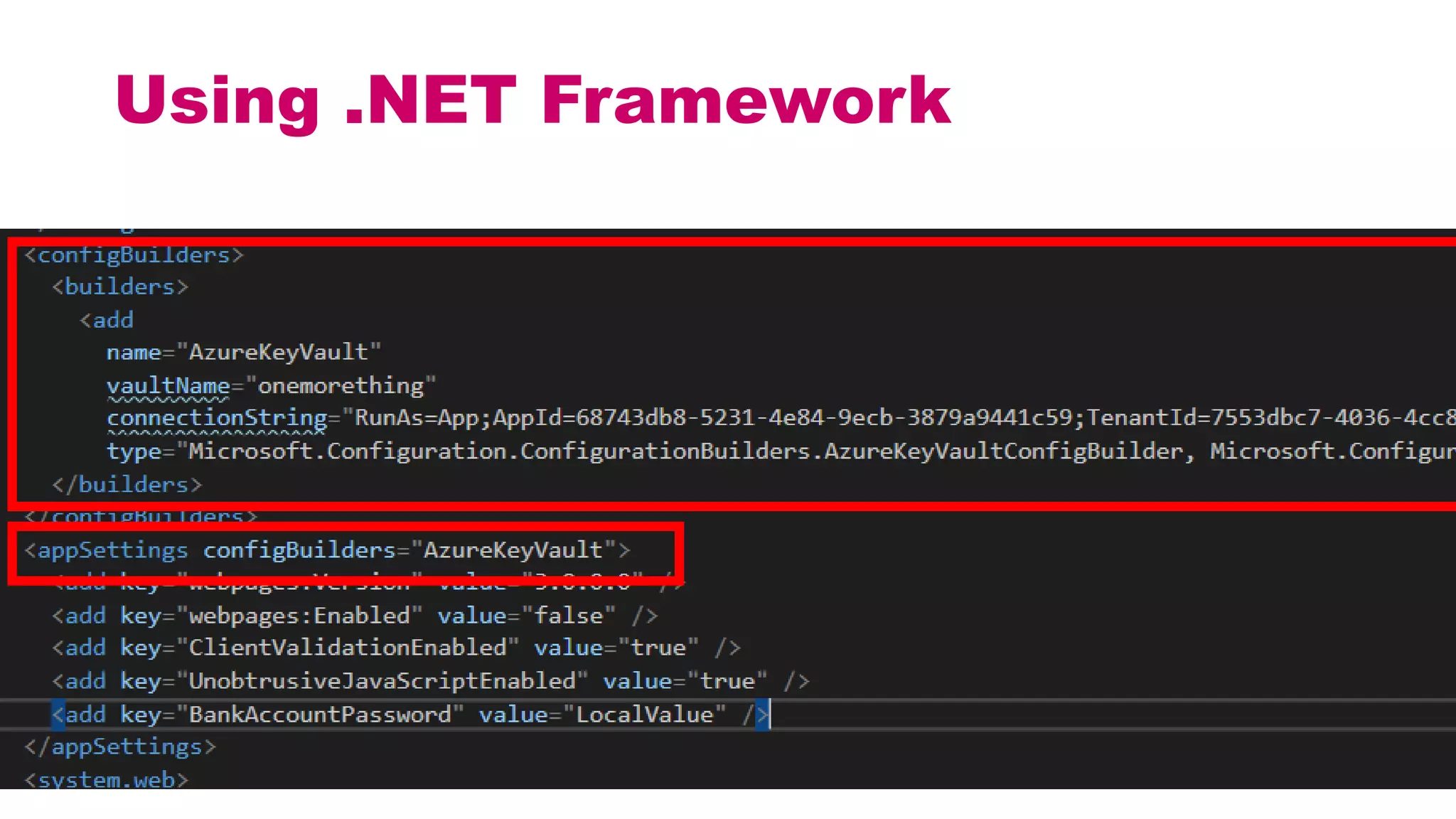
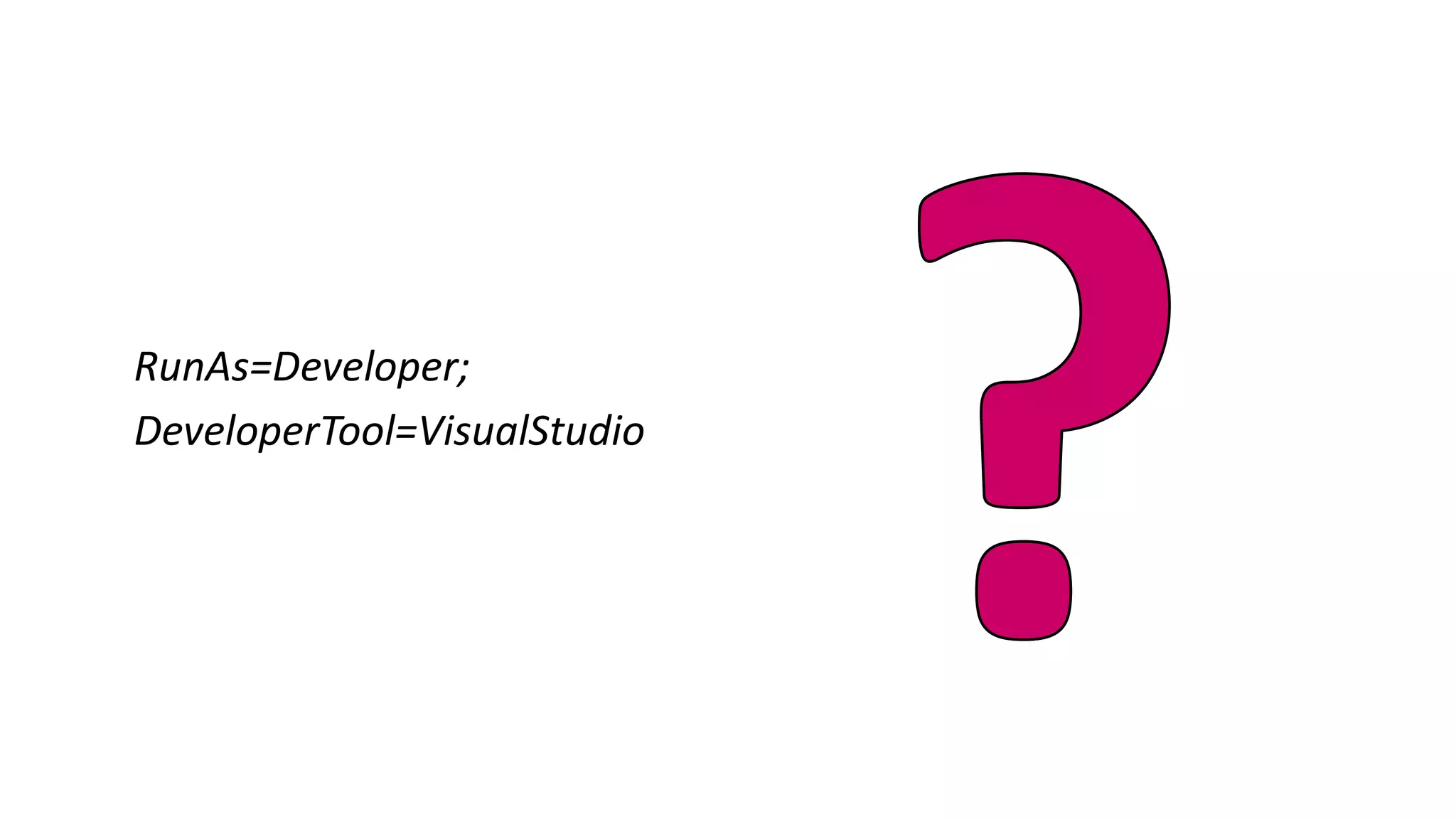
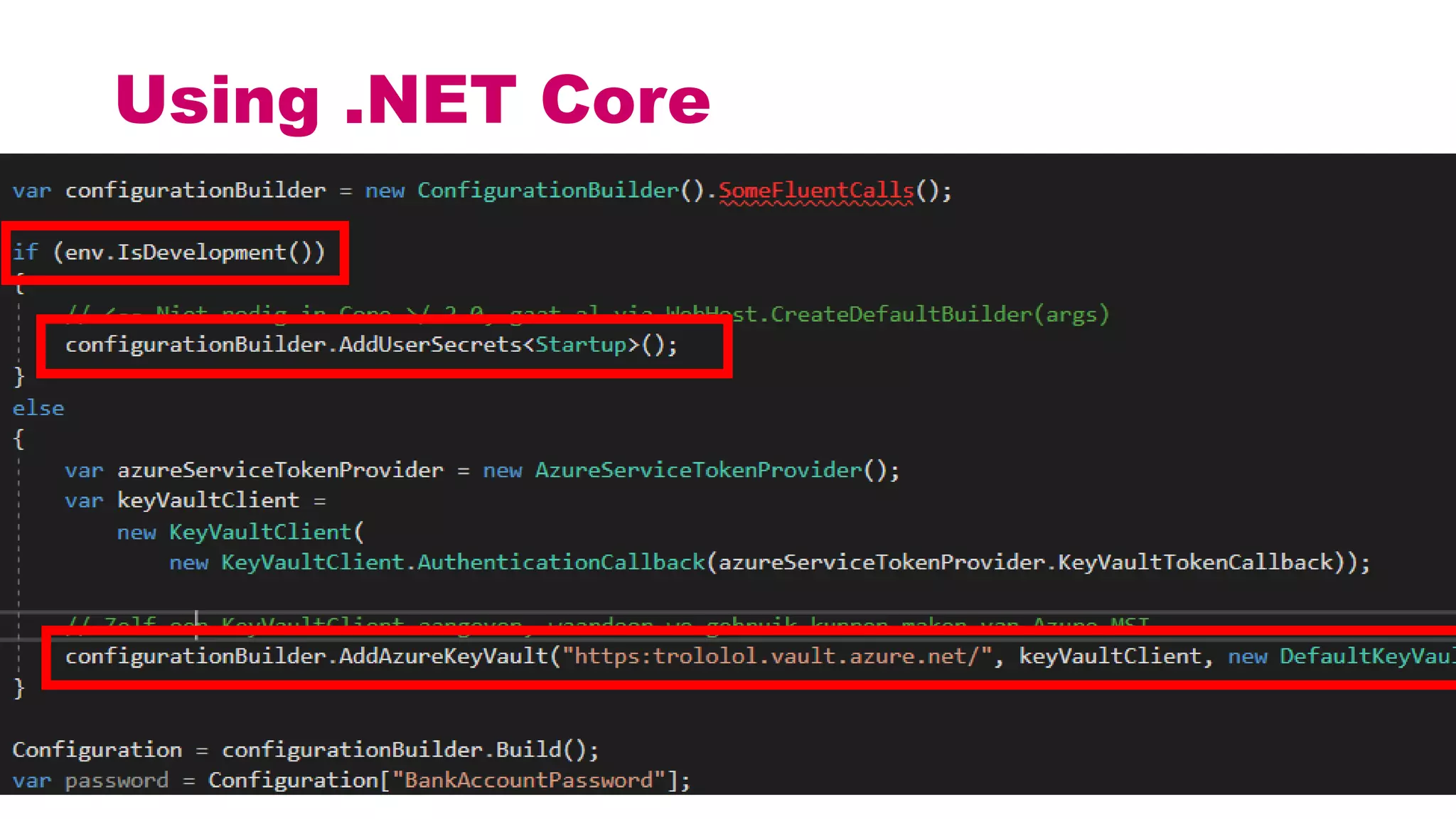
This document discusses different approaches for managing secrets securely in DevOps deployments. It presents four approaches: 1) using a release orchestrator which allows viewing secrets, 2) using ARM templates which prevents viewing secrets but they must be duplicated, 3) directly accessing key vault which prevents viewing and duplication of secrets but is only available on some Azure services, and 4) directly accessing other services which has the same benefits as 3 but is limited to supported services. The document recommends choosing an approach based on how code and infrastructure are deployed and what capabilities the services support. It also demonstrates config builders for managing secrets locally and in the cloud.