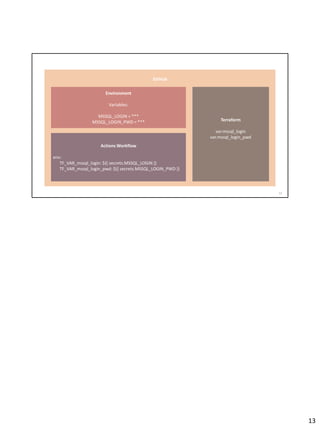
This document discusses best practices for securely provisioning Azure resources using GitHub and Terraform. It covers setting up GitHub Actions workflows to deploy resources with Terraform, integrating advanced security measures with SonarCloud, and key takeaways around protecting secrets, using standards like OpenID Connect, and maintaining code quality through dependency reviews and secret scanning. An agenda is provided that includes introductions, demonstrations of GitHub Actions, Azure, and Terraform, a discussion of GitHub advanced security and SonarCloud, and concluding key takeaways.