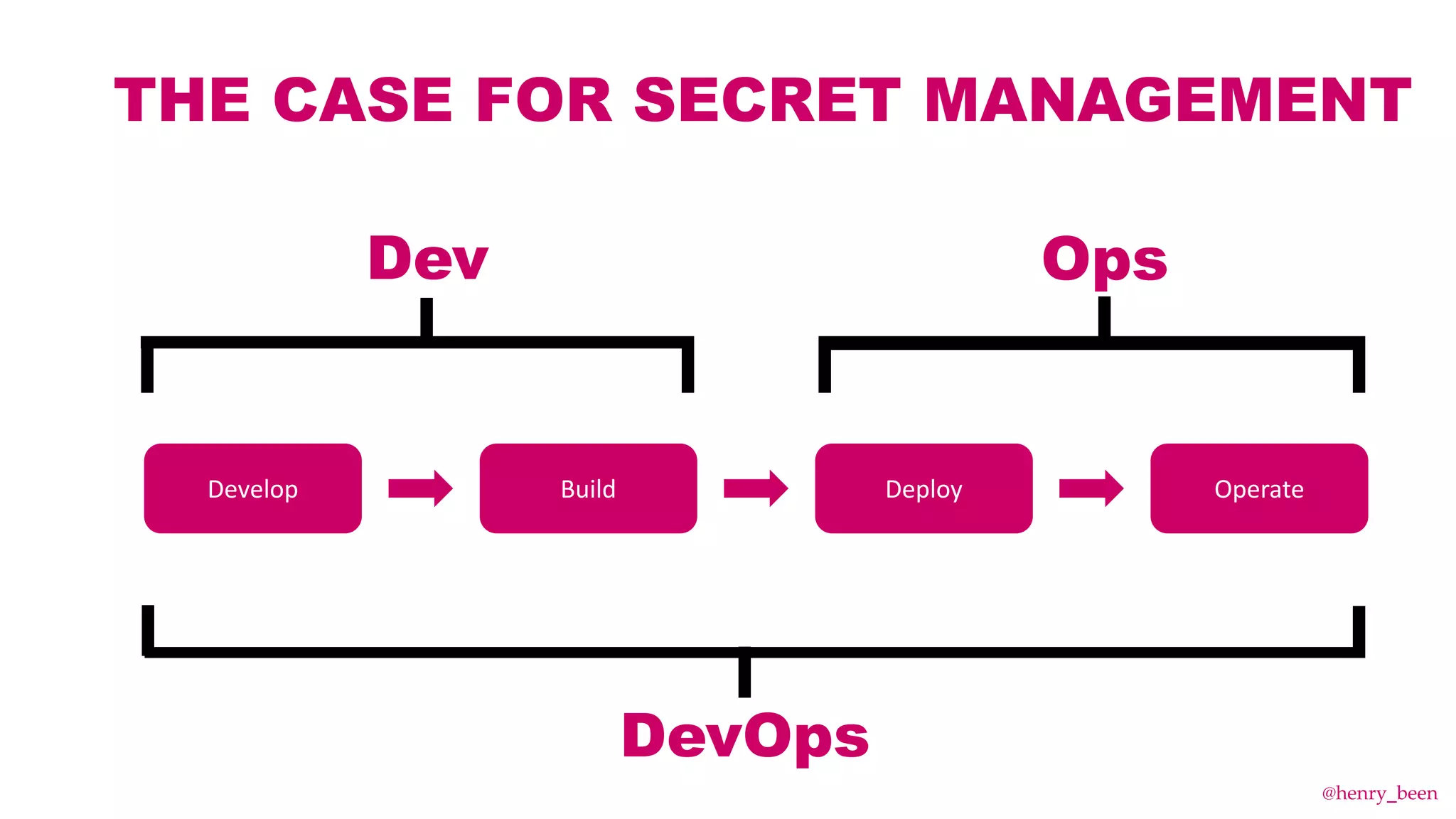
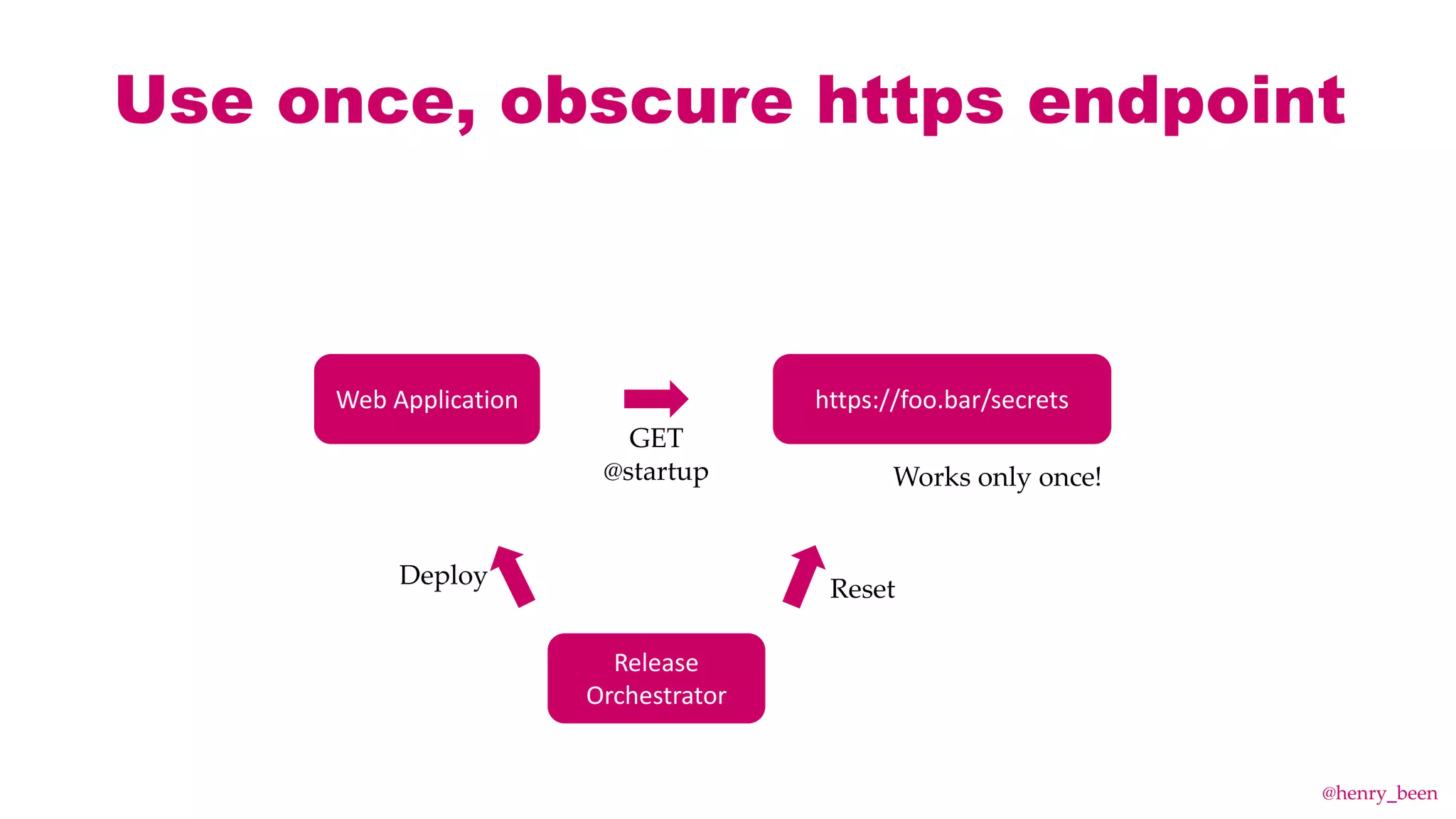
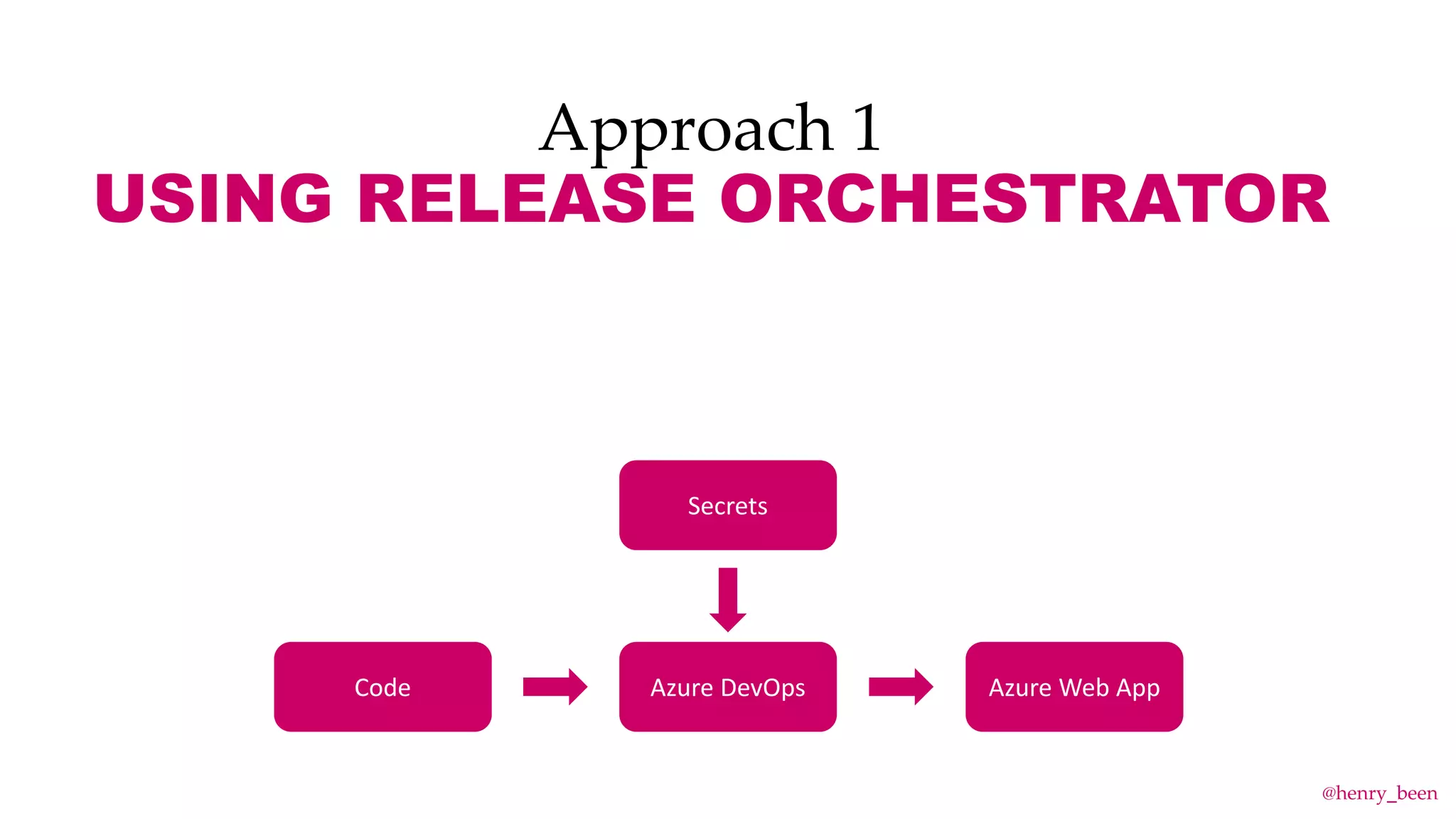
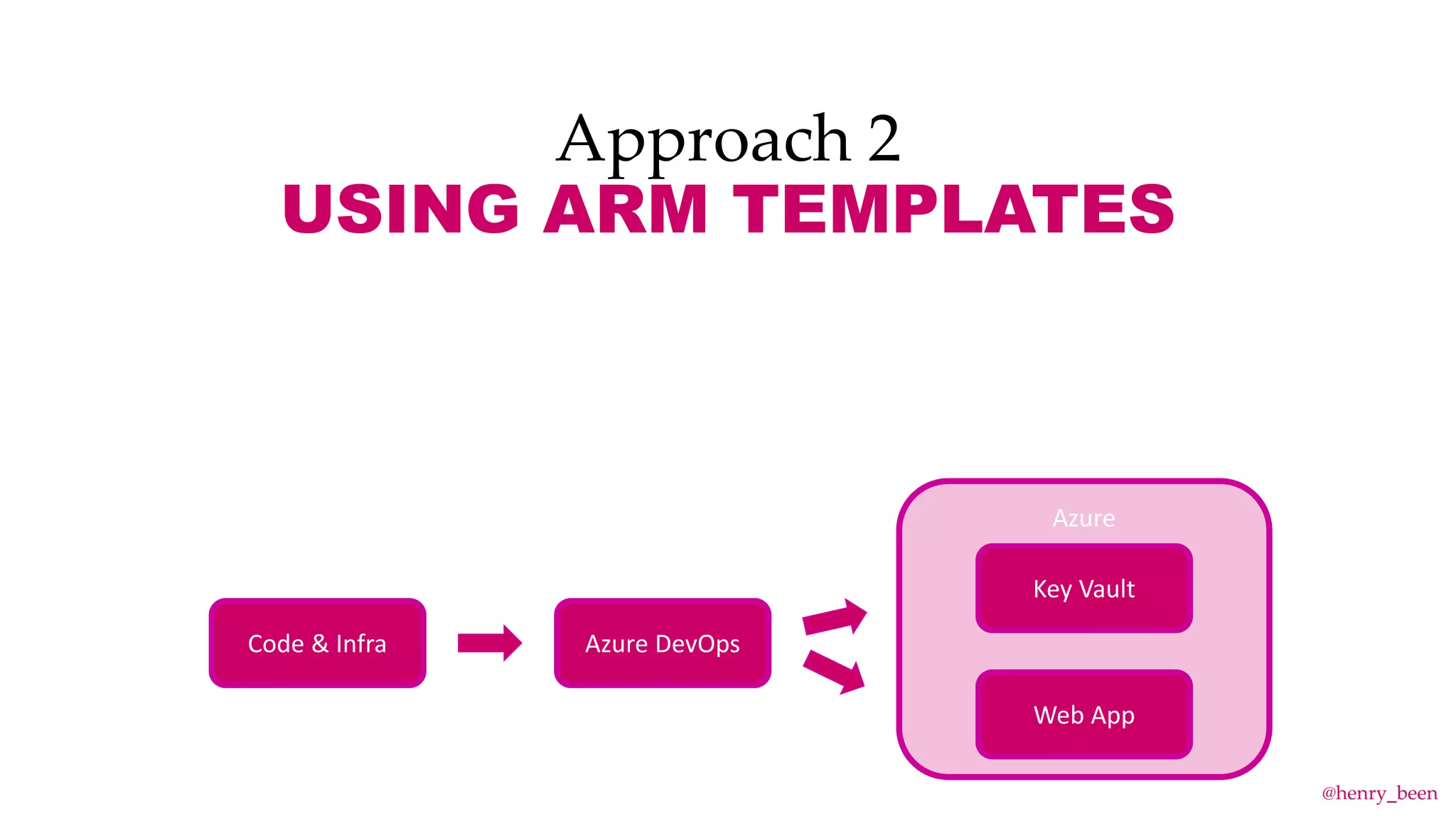
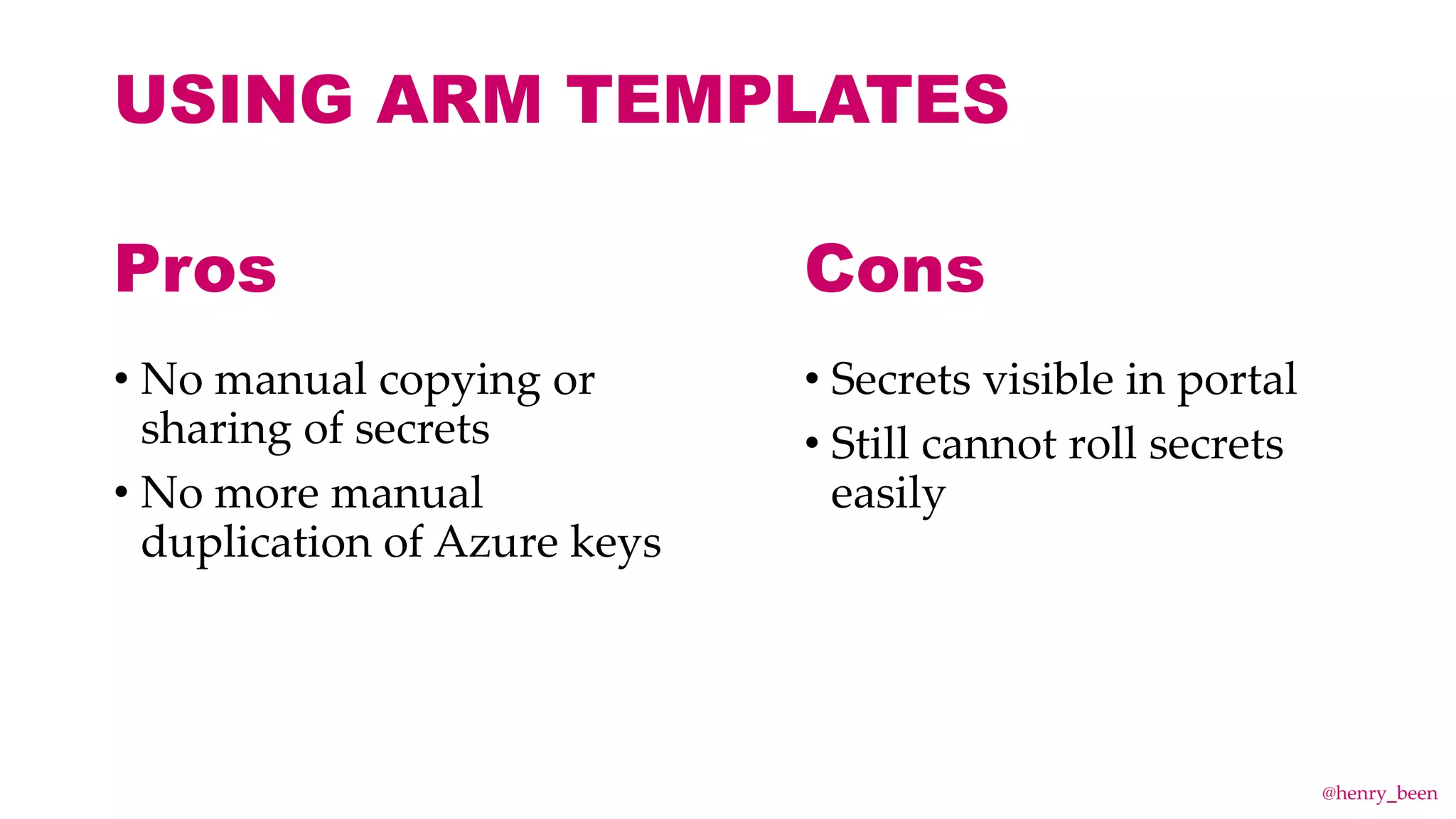
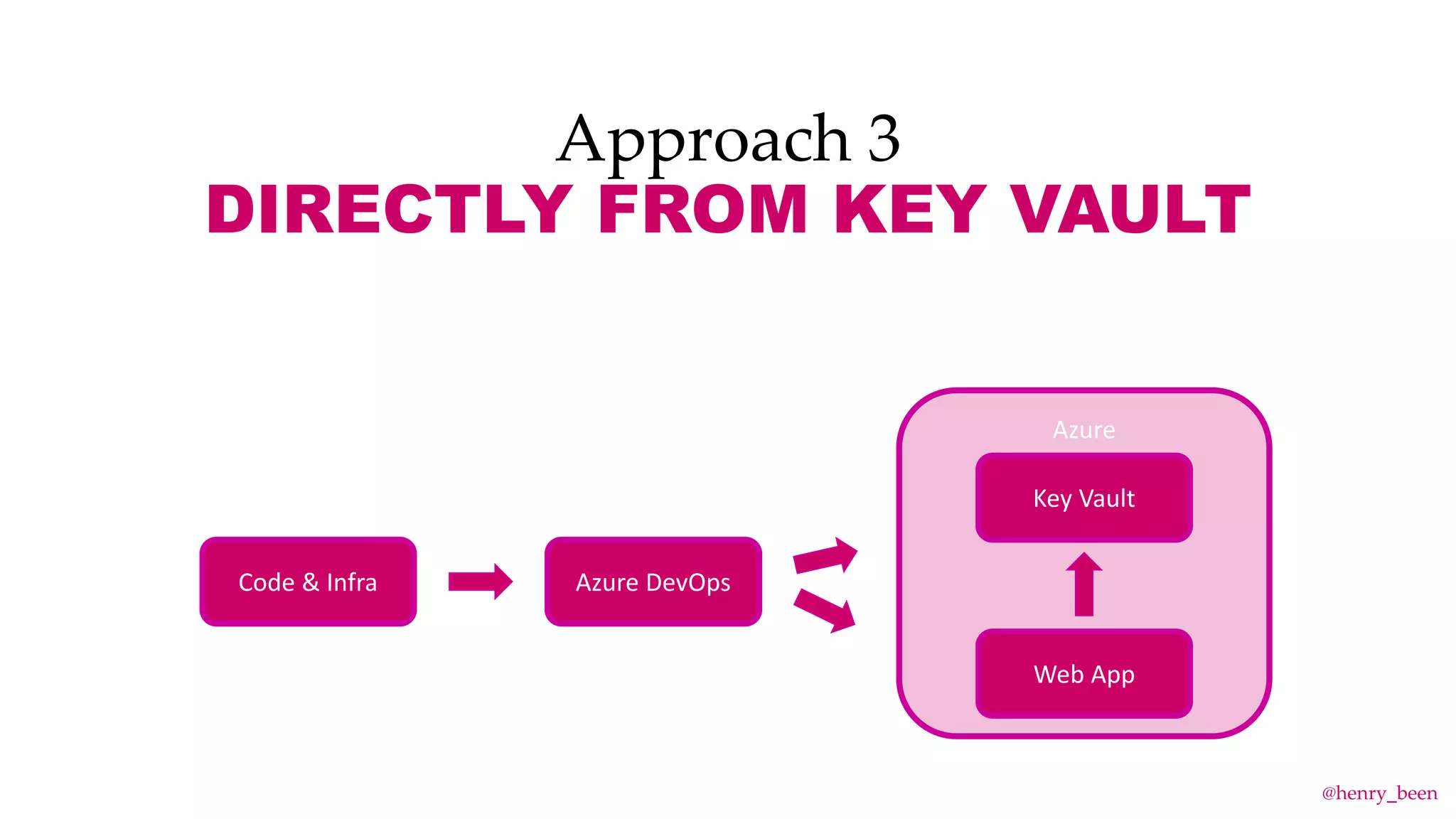
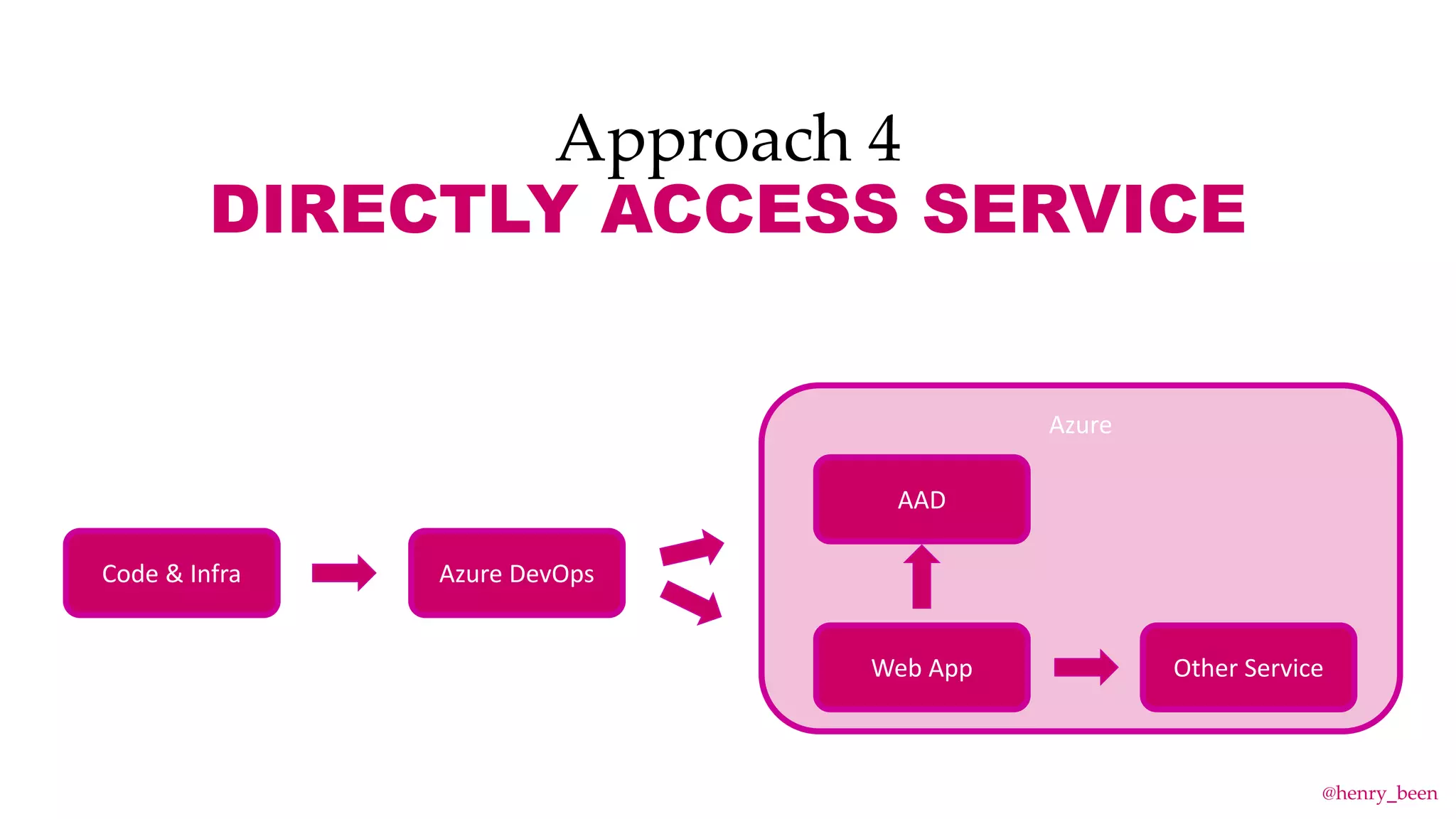
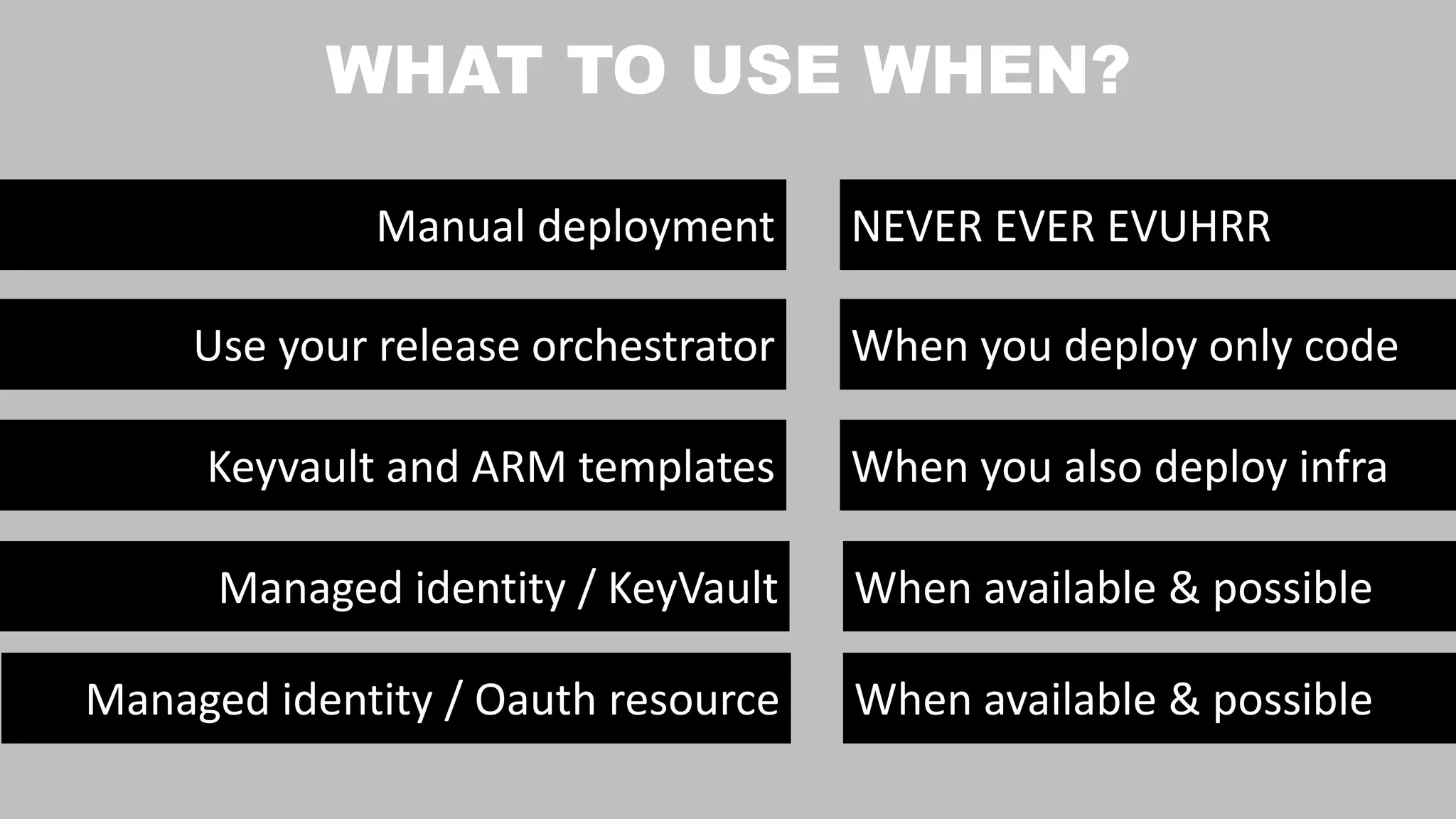
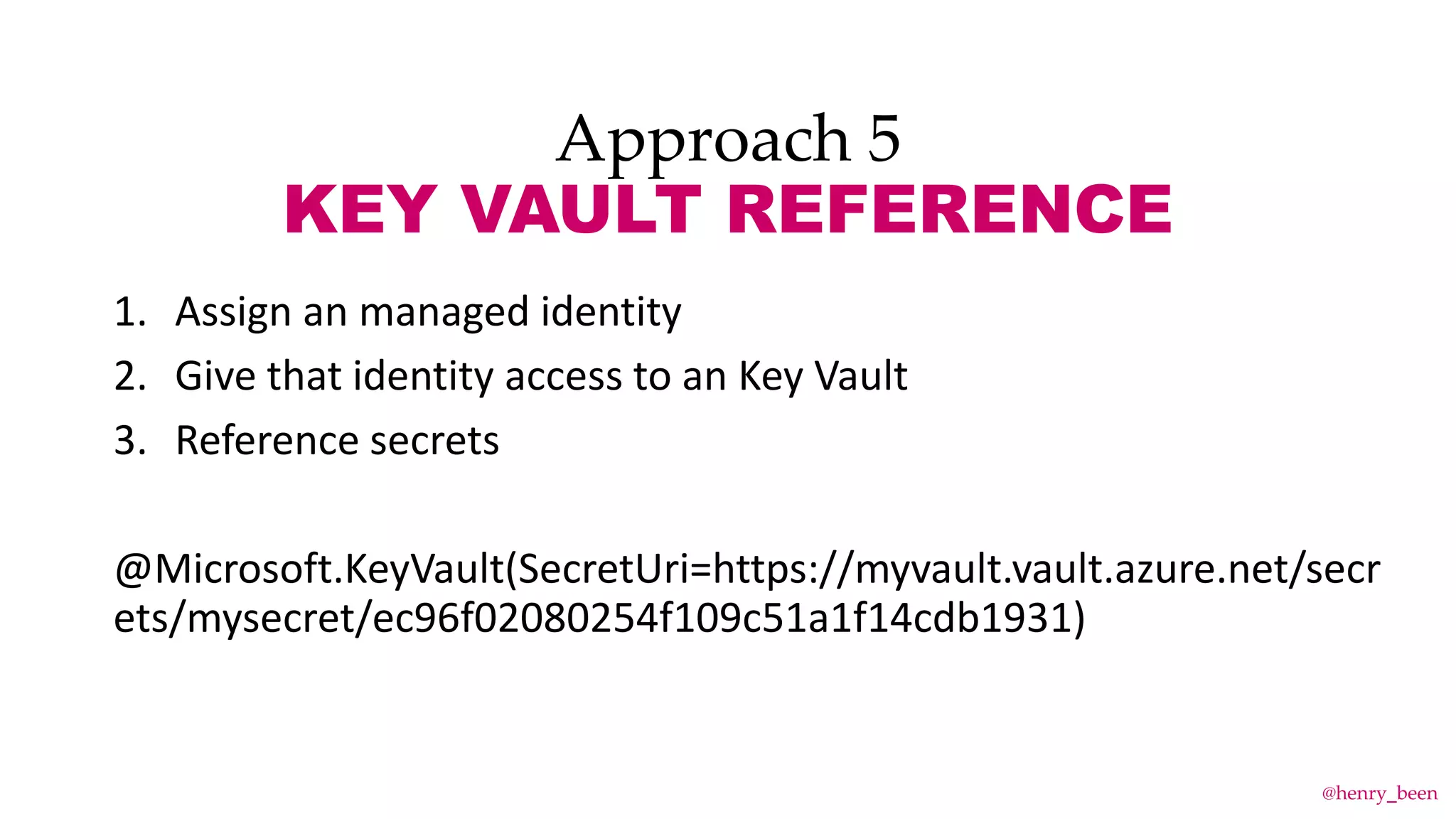
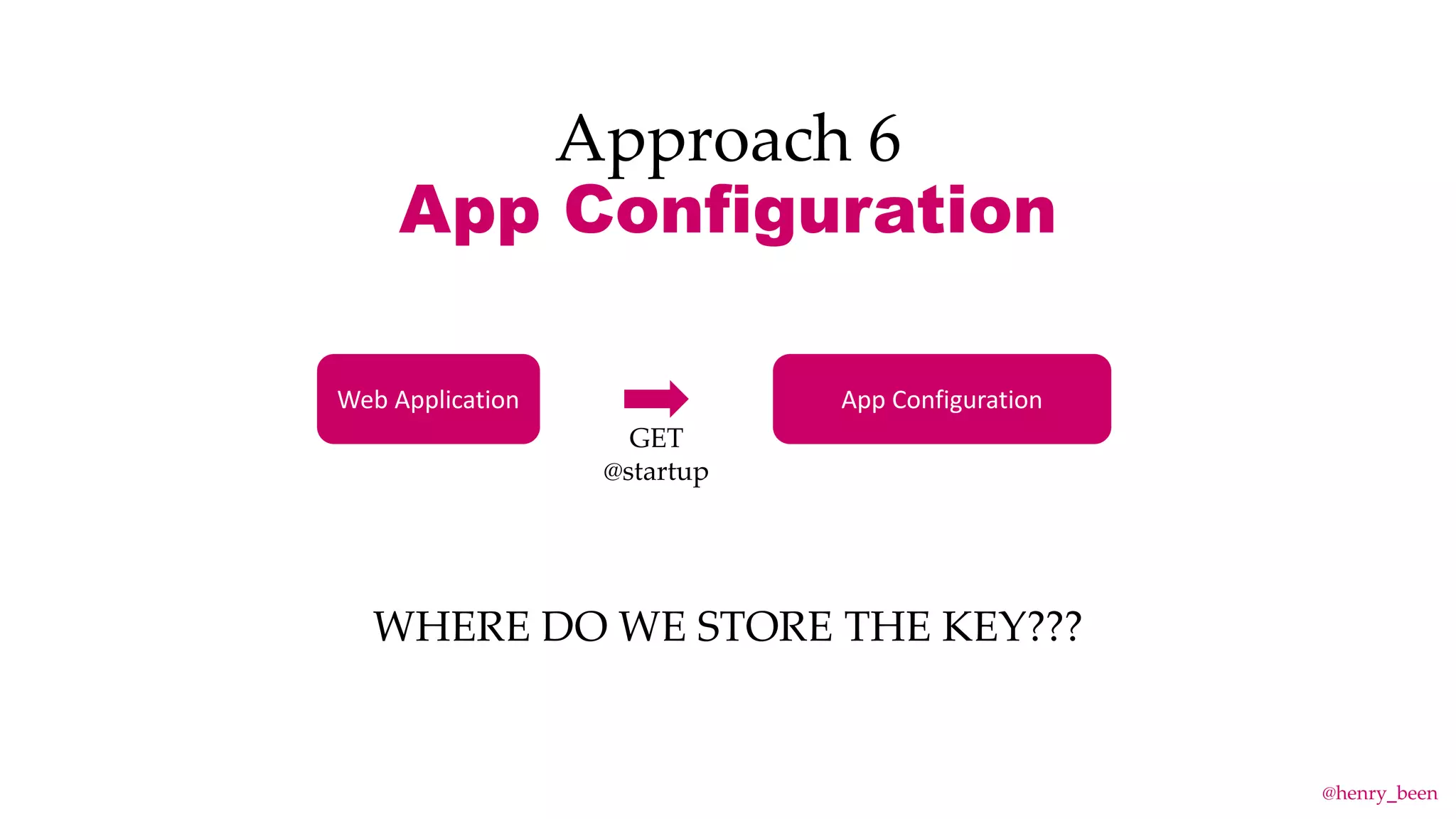
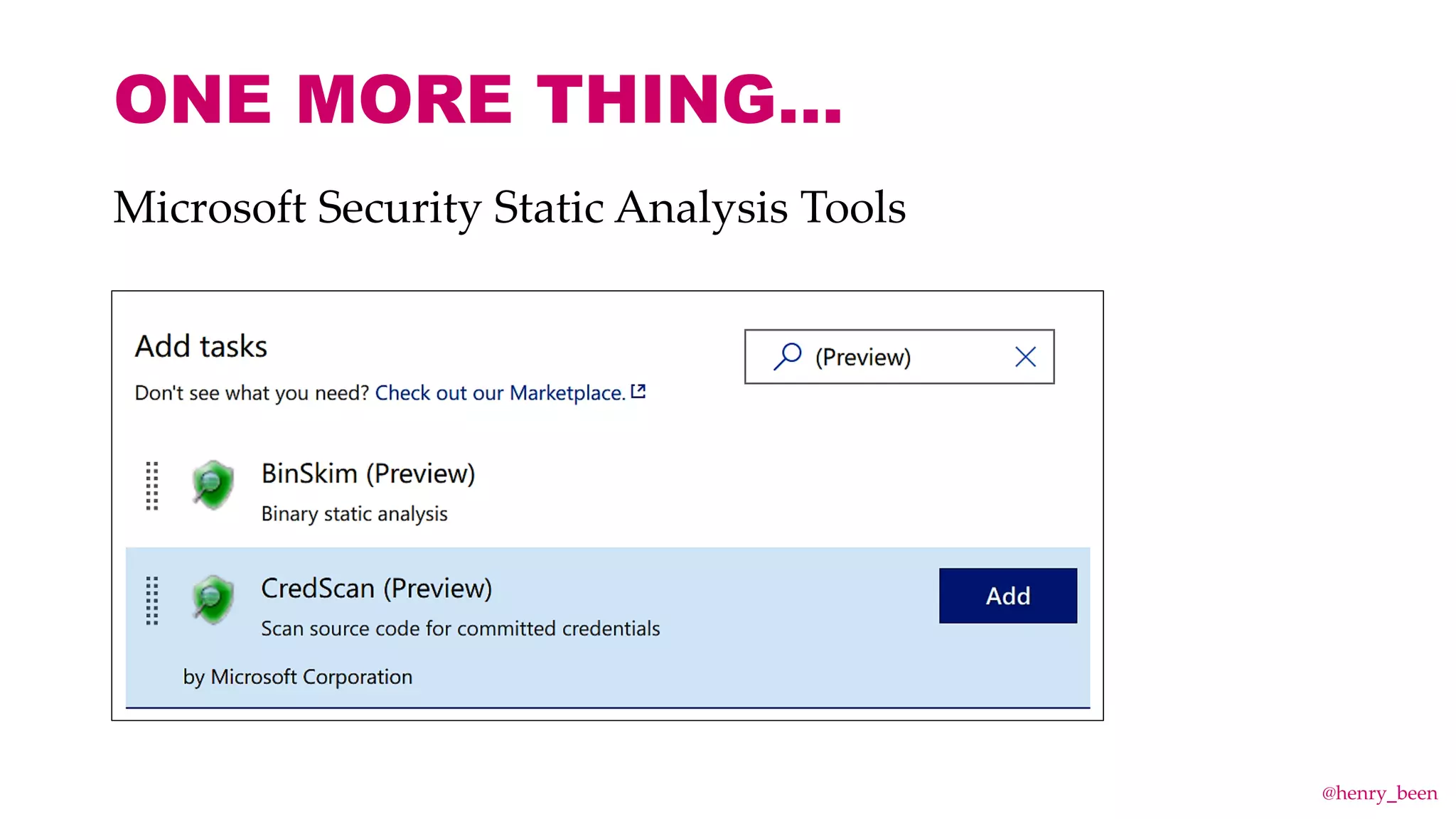
The document discusses secure secret management strategies for Azure DevOps and applications, highlighting several approaches to avoid sharing secrets and maintaining their integrity. It emphasizes the importance of using tools like Azure Key Vault, ARM templates, and managed identities to protect secrets effectively. The author also mentions the necessity of regularly updating and rolling secrets without manual duplication or risk of exposure.