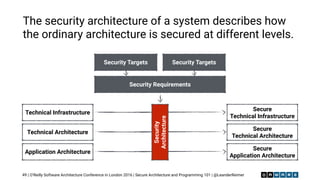
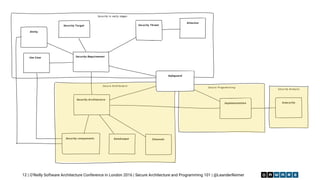
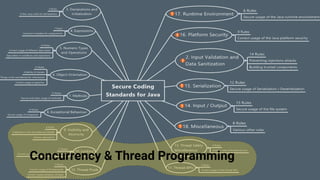
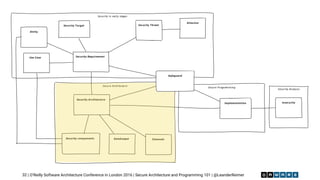
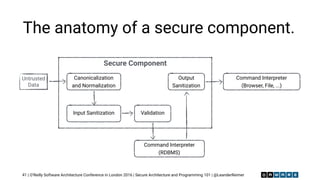
The document outlines essential principles of secure software architecture and programming, emphasizing the importance of security as a non-functional requirement often overlooked in development. It discusses vulnerabilities, secure coding practices, and the necessity of using reliable libraries, along with tools and strategies to mitigate risks. The presentation highlights the role of developers in ensuring security through good practices, peer reviews, and continuous monitoring of dependencies and security threats.



















![| O’Reilly Software Architecture Conference in London 2016 | Secure Architecture and Programming 101 | @LeanderReimer
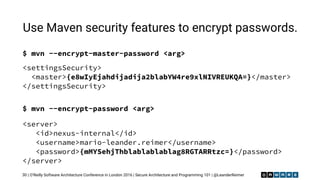
Secure passwords using Gradle Credentials plugin
31
plugins {
id 'de.qaware.seu.as.code.credentials' version '2.4.0'
}
repositories {
maven {
url 'https://your.company.com/nexus/repo'
credentials {
username project.credentials['Nexus'].username
password project.credentials['Nexus'].password
}
}
}](https://image.slidesharecdn.com/securearchitectureandprogramming101-161020095519/85/Secure-Architecture-and-Programming-101-31-320.jpg)



![| O’Reilly Software Architecture Conference in London 2016 | Secure Architecture and Programming 101 | @LeanderReimer
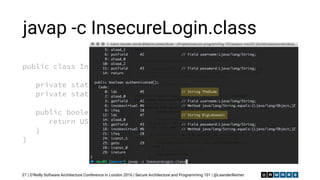
mvn versions:display-dependency-updates
36
[INFO] The following dependencies in Dependencies have newer versions:
[INFO] com.sun.faces:jsf-api ......................................... 2.1.10 -> 2.2.12
[INFO] com.sun.jersey:jersey-client ..................................... 1.9.1 -> 1.19
[INFO] commons-fileupload:commons-fileupload ........................... 1.2.1 -> 1.3.1
[INFO] org.apache.httpcomponents:httpclient ............................ 4.2.1 -> 4.5.1
[INFO] org.apache.solr:solr-core ....................................... 4.6.1 -> 5.3.1](https://image.slidesharecdn.com/securearchitectureandprogramming101-161020095519/85/Secure-Architecture-and-Programming-101-36-320.jpg)





![| O’Reilly Software Architecture Conference in London 2016 | Secure Architecture and Programming 101 | @LeanderReimer
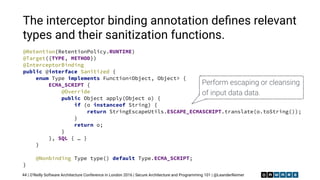
Security is a cross cutting concern. Interceptors are
a perfect match to implement security functionality.
43
@Interceptor
@Sanitized
public class SanitizedInterceptor implements Serializable {
@AroundInvoke
public Object invoke(InvocationContext ctx) throws Exception {
Sanitized sanitizer = getSanitizedAnnotation(ctx.getMethod());
// apply the sanitization function
Object[] raw = ctx.getParameters();
Object[] sanitized = Arrays.stream(raw).map(sanitizer.type()).toArray();
ctx.setParameters(sanitized);
return ctx.proceed();
}
private Sanitized getSanitizedAnnotation(Method m) { … }
}](https://image.slidesharecdn.com/securearchitectureandprogramming101-161020095519/85/Secure-Architecture-and-Programming-101-43-320.jpg)