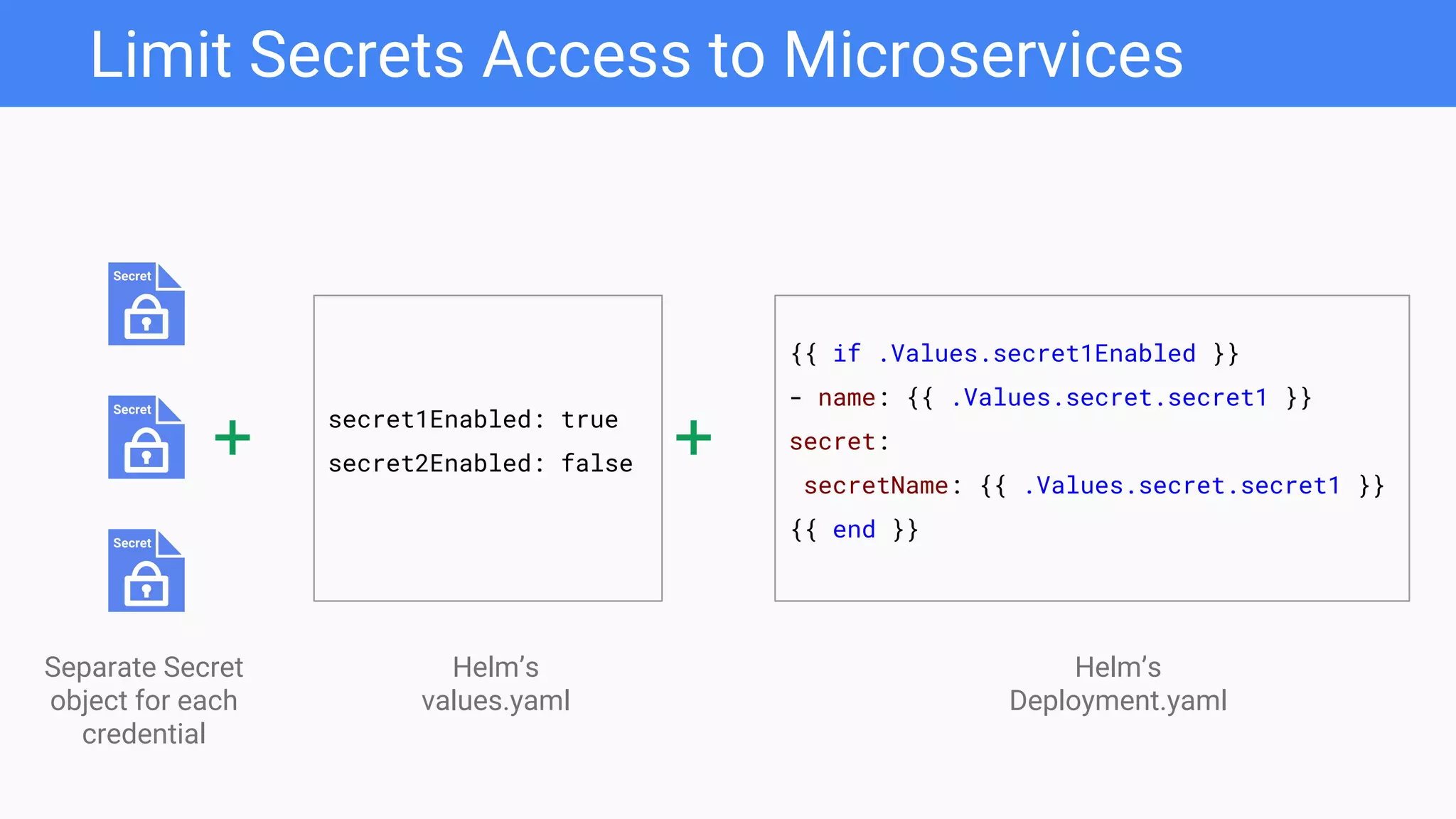
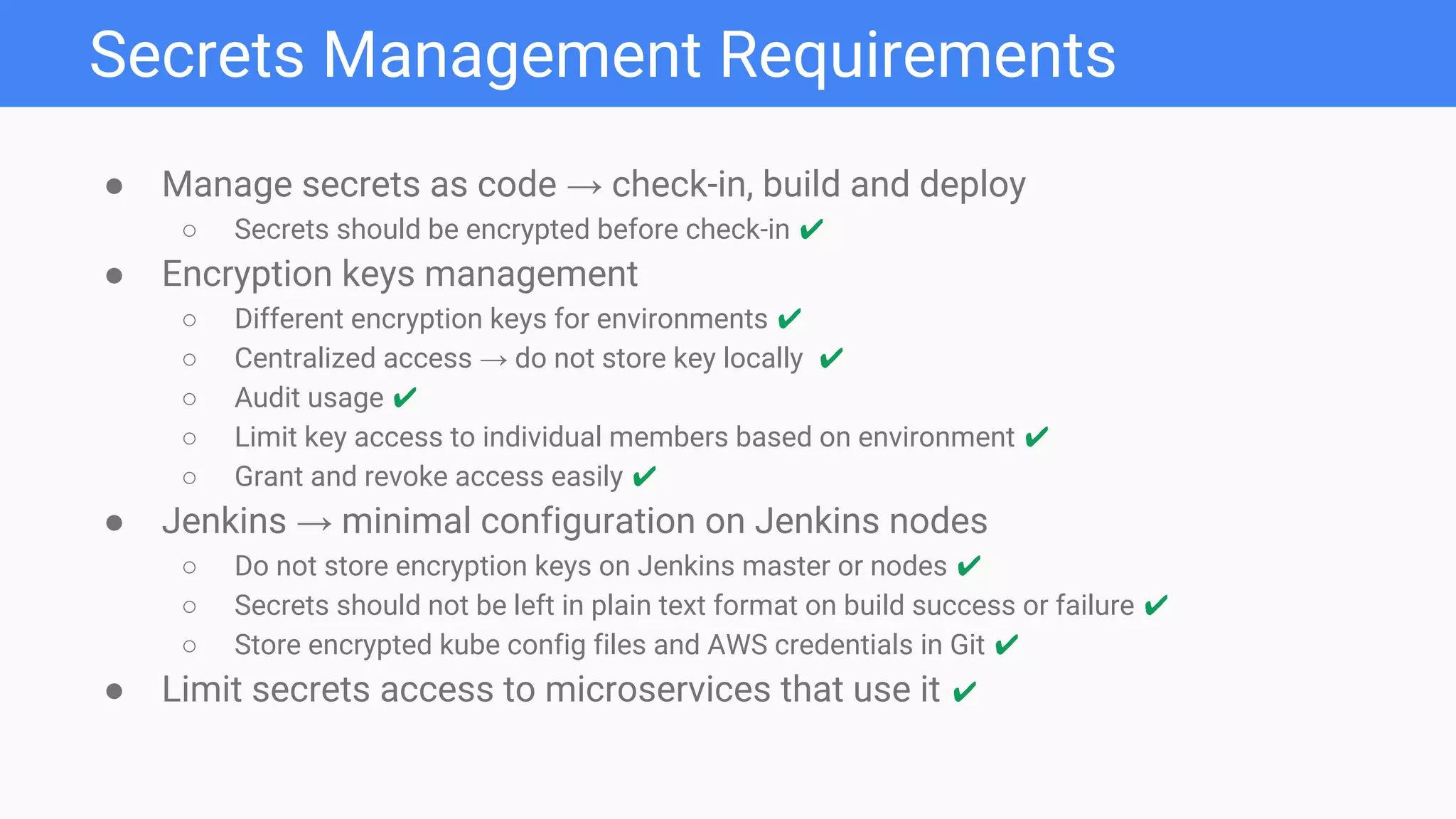
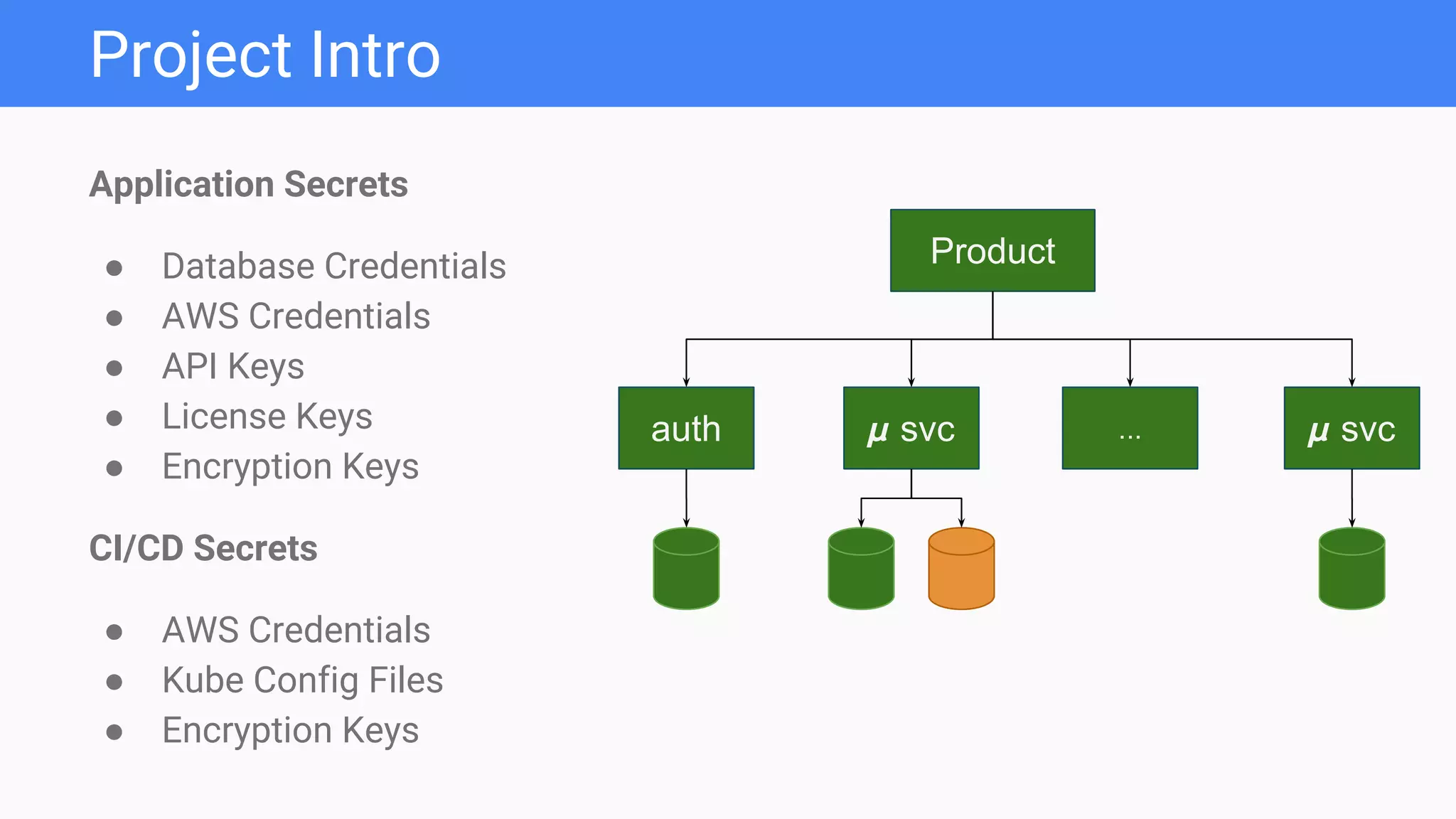
The document discusses a secrets management and delivery pipeline for Kubernetes pods, focusing on managing application secrets like API keys and credentials securely. It outlines the use of Mozilla SOPS for encryption, key management strategies, and minimizing exposure of secrets in CI/CD workflows. Additionally, it emphasizes the importance of managing secrets as code, implementing centralized access, and limiting key access based on environment needs.














![Mozilla SOPS - Diffs in Cleartext in Git
~ > cat ~/.gitattributes
*.enc diff=sopsdiffer
*.enc.yaml diff=sopsdiffer
*.enc.json diff=sopsdiffer
.gitattributes
~ > grep -A1 sops ~/.gitconfig
[diff "sopsdiffer"]
textconv = "sops -d"
.gitconfig
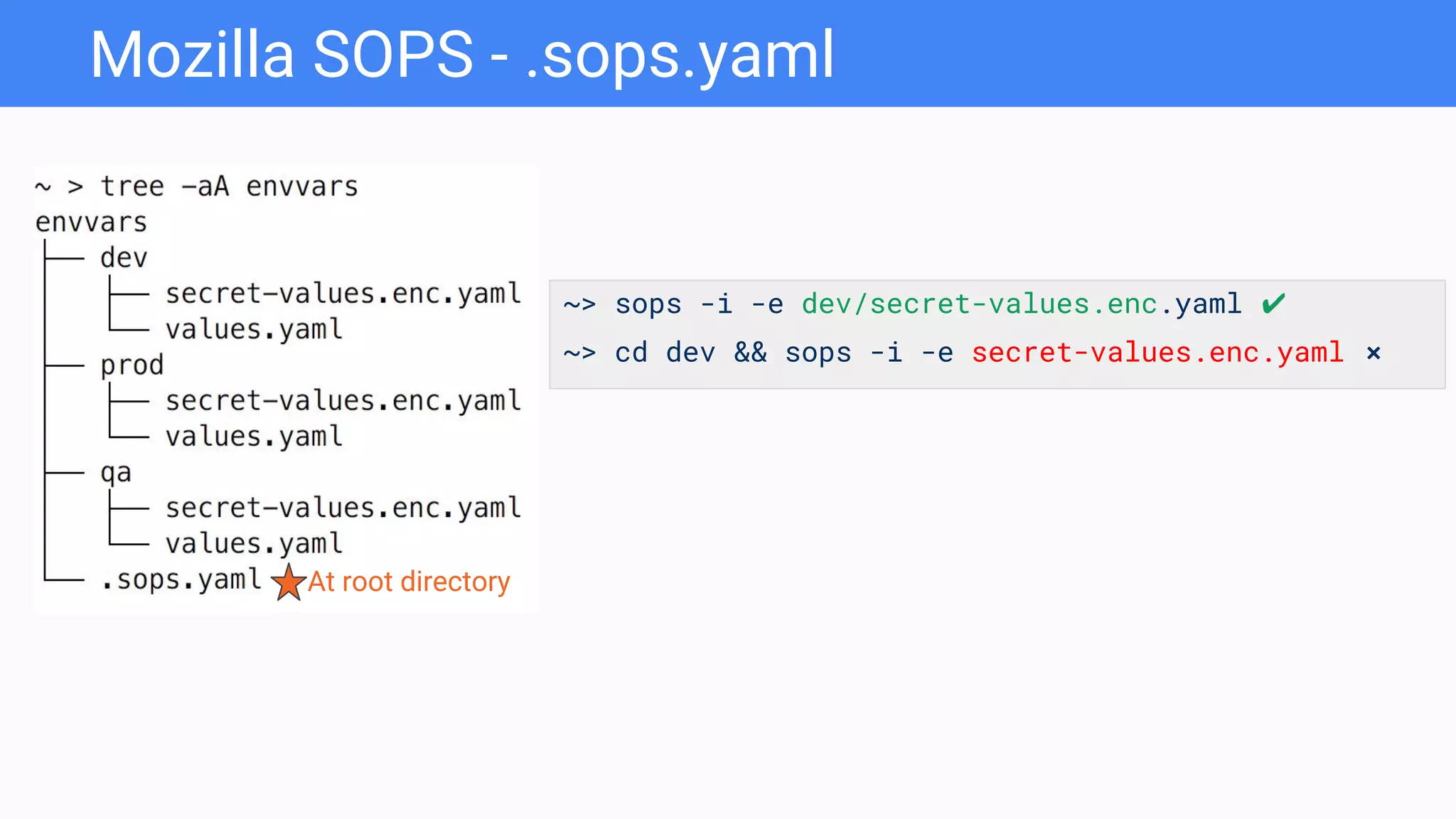
In my testing, this worked if
.sops.yaml is at the root directory
of the git project and regex expression
is based on the filename but not
directory name
dev/secret-values.enc.yaml →
dev-secret-values.enc.yaml](https://image.slidesharecdn.com/k8s-secretsmanagement-181121182055/75/Secrets-Management-and-Delivery-to-Kubernetes-Pods-20-2048.jpg)