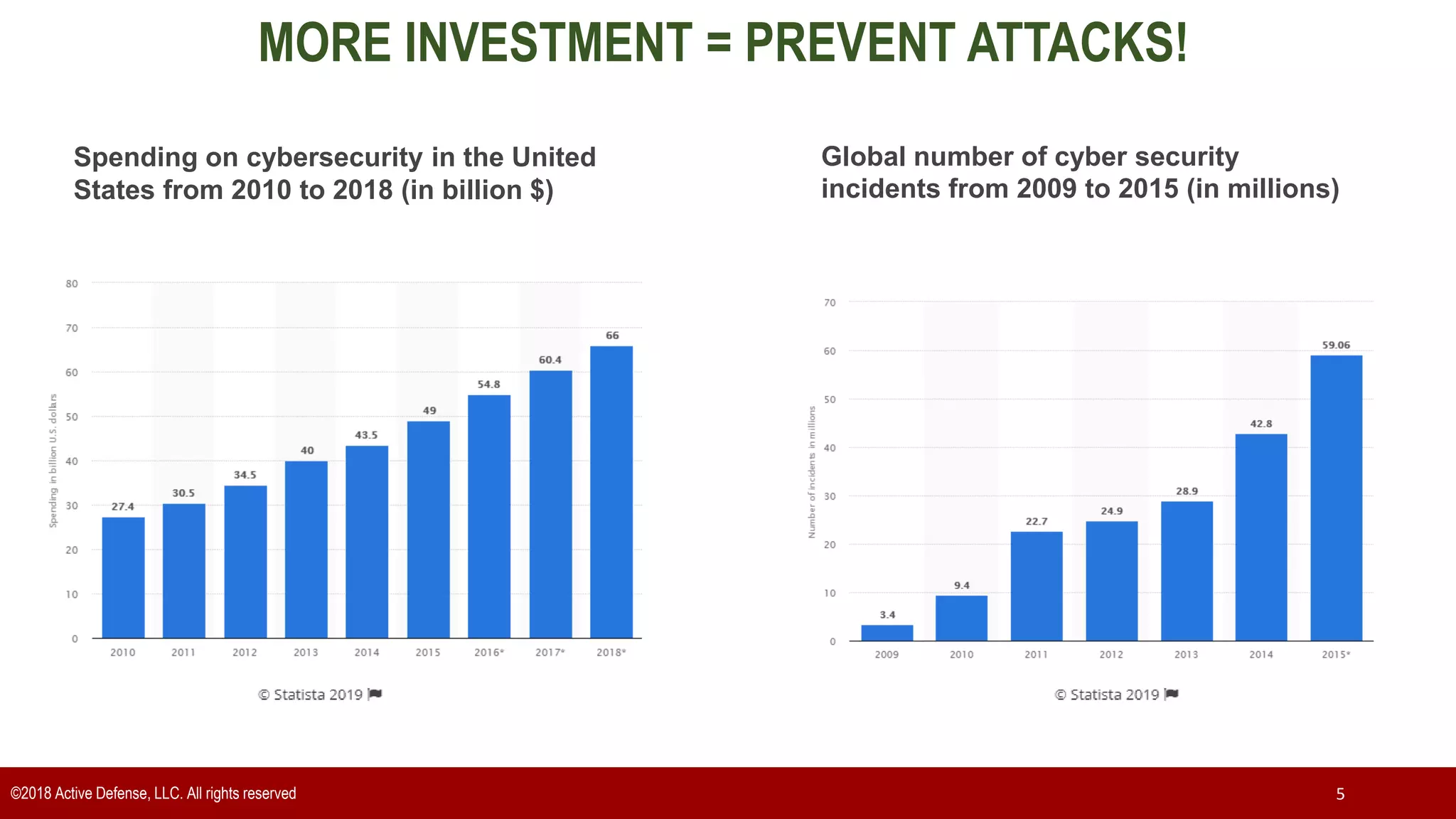
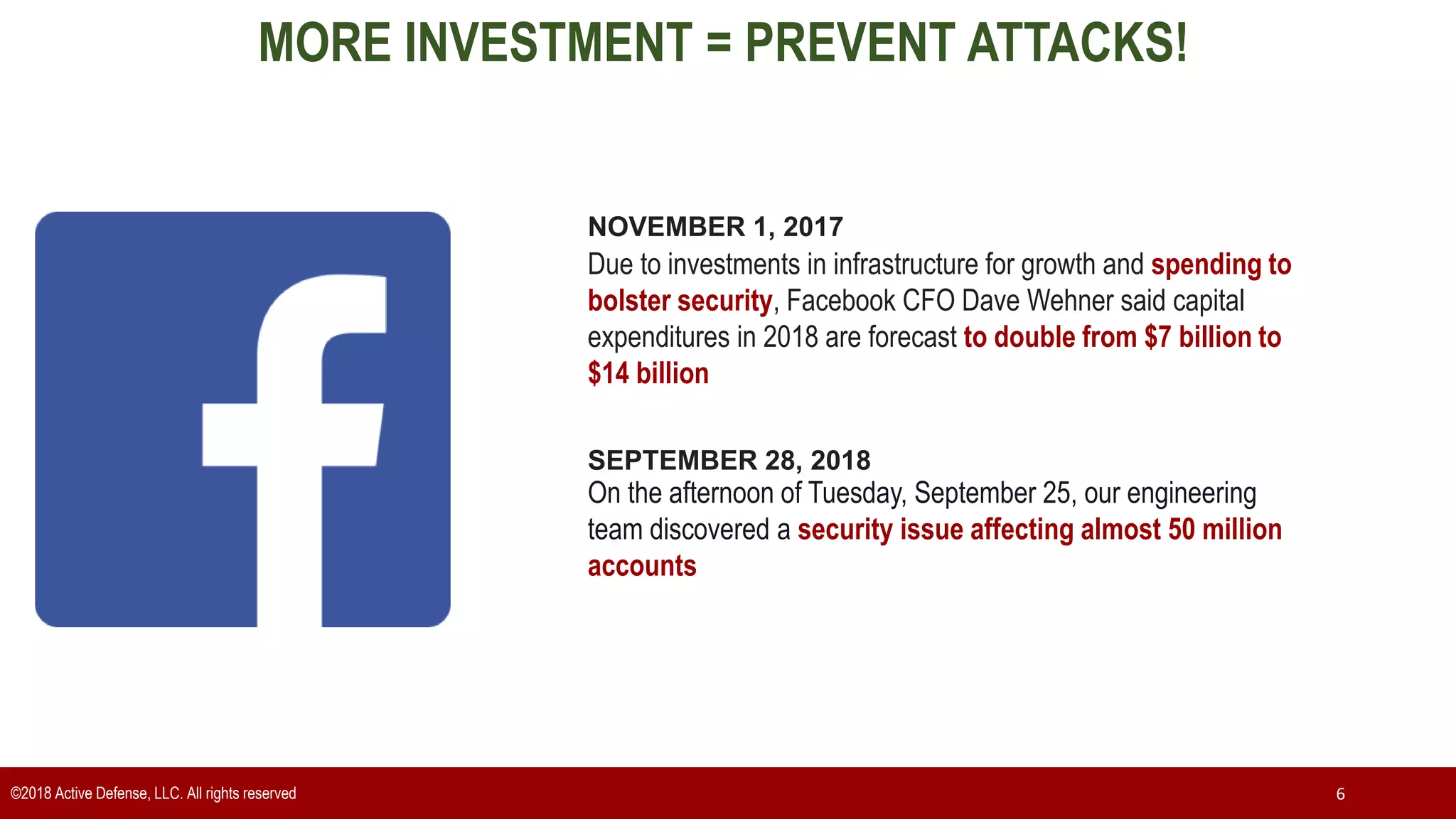
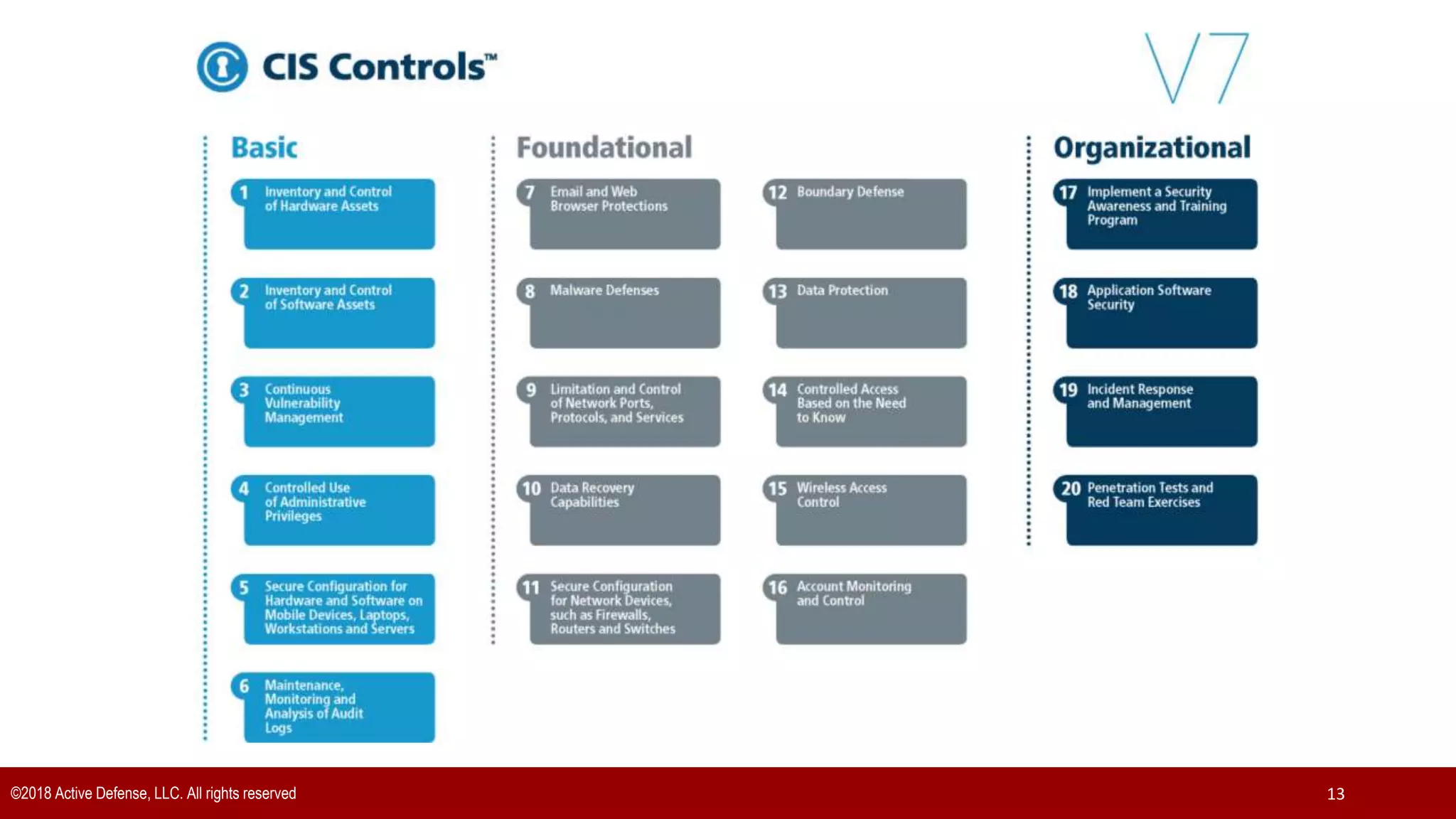
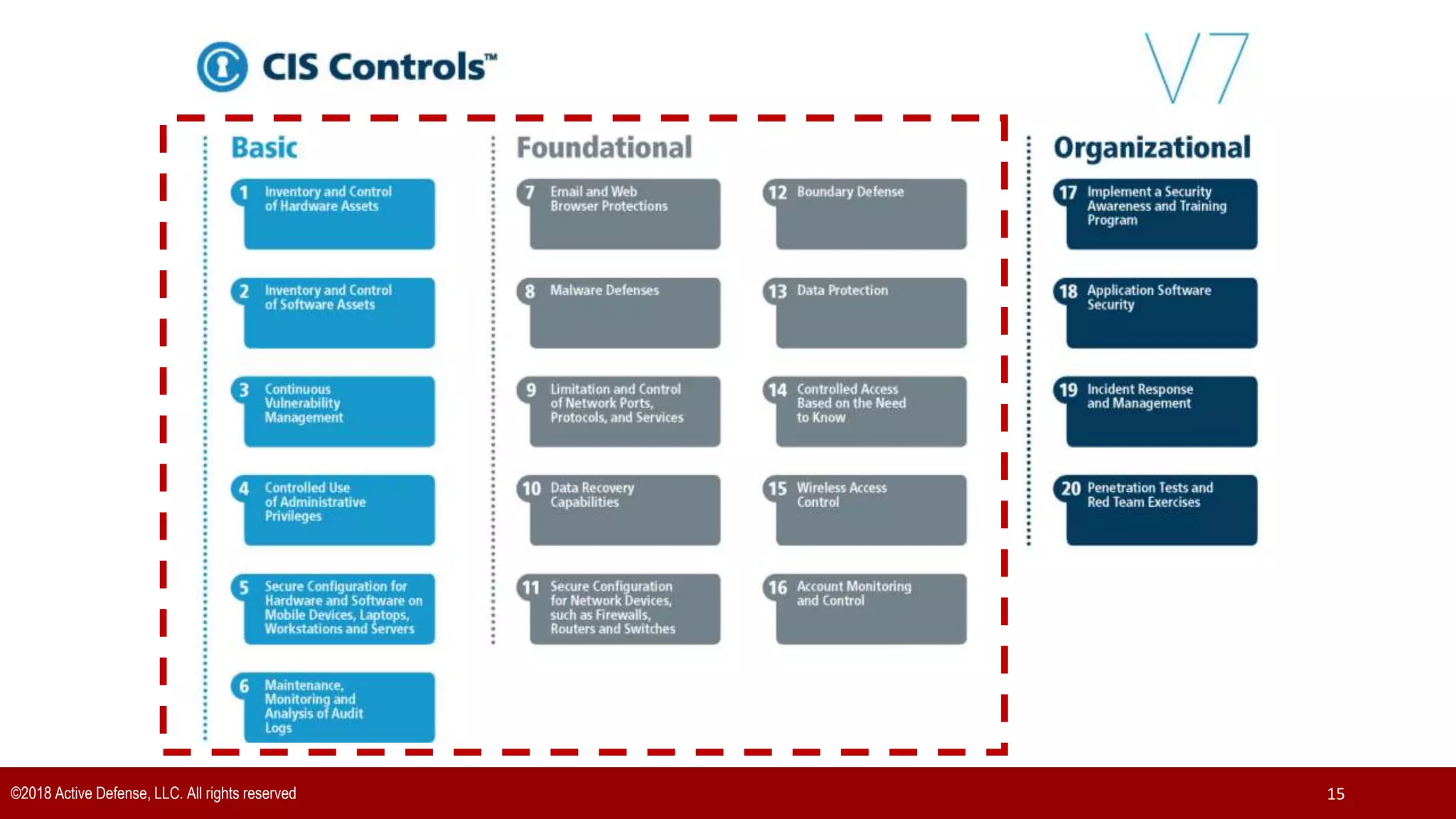
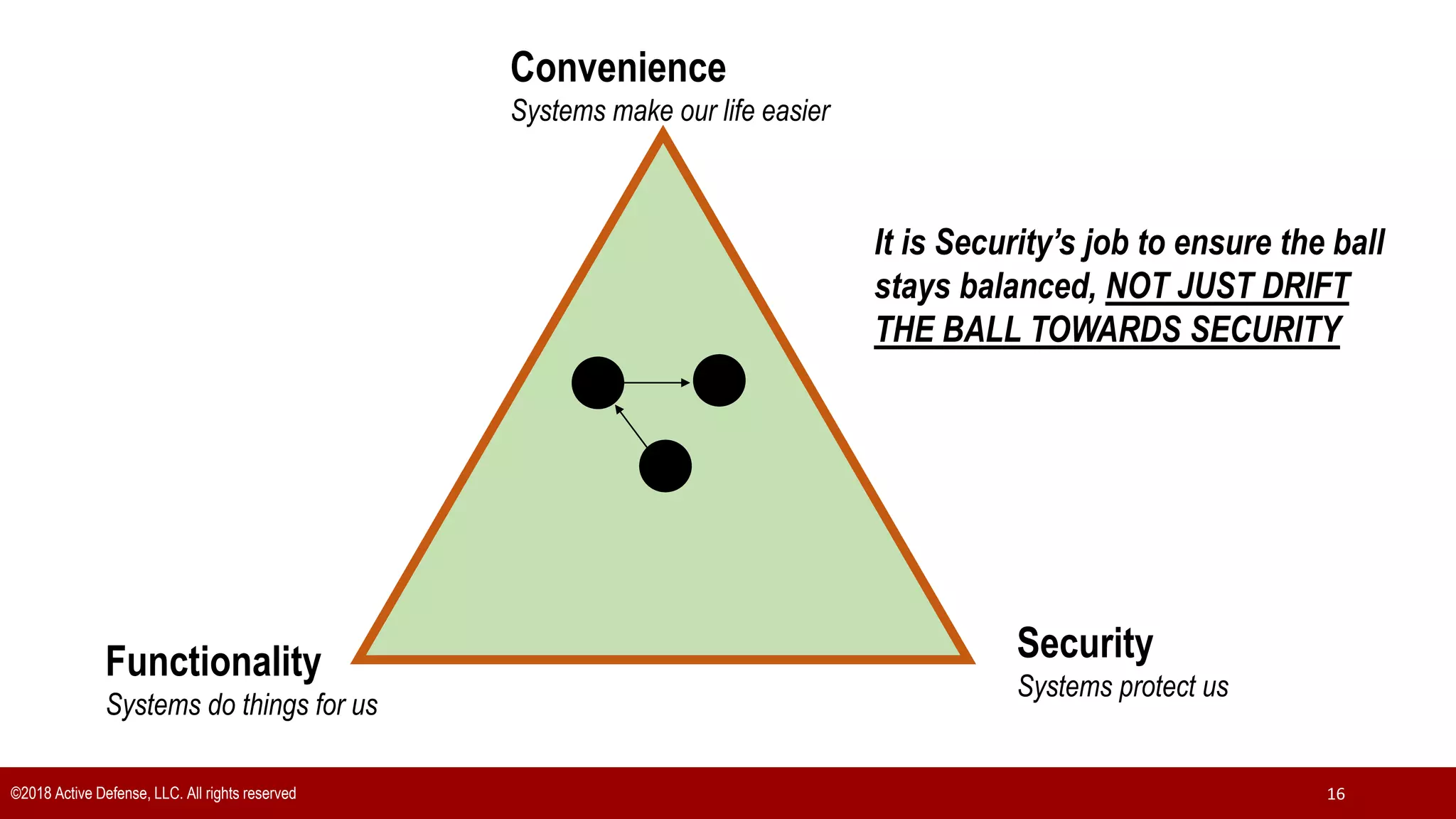
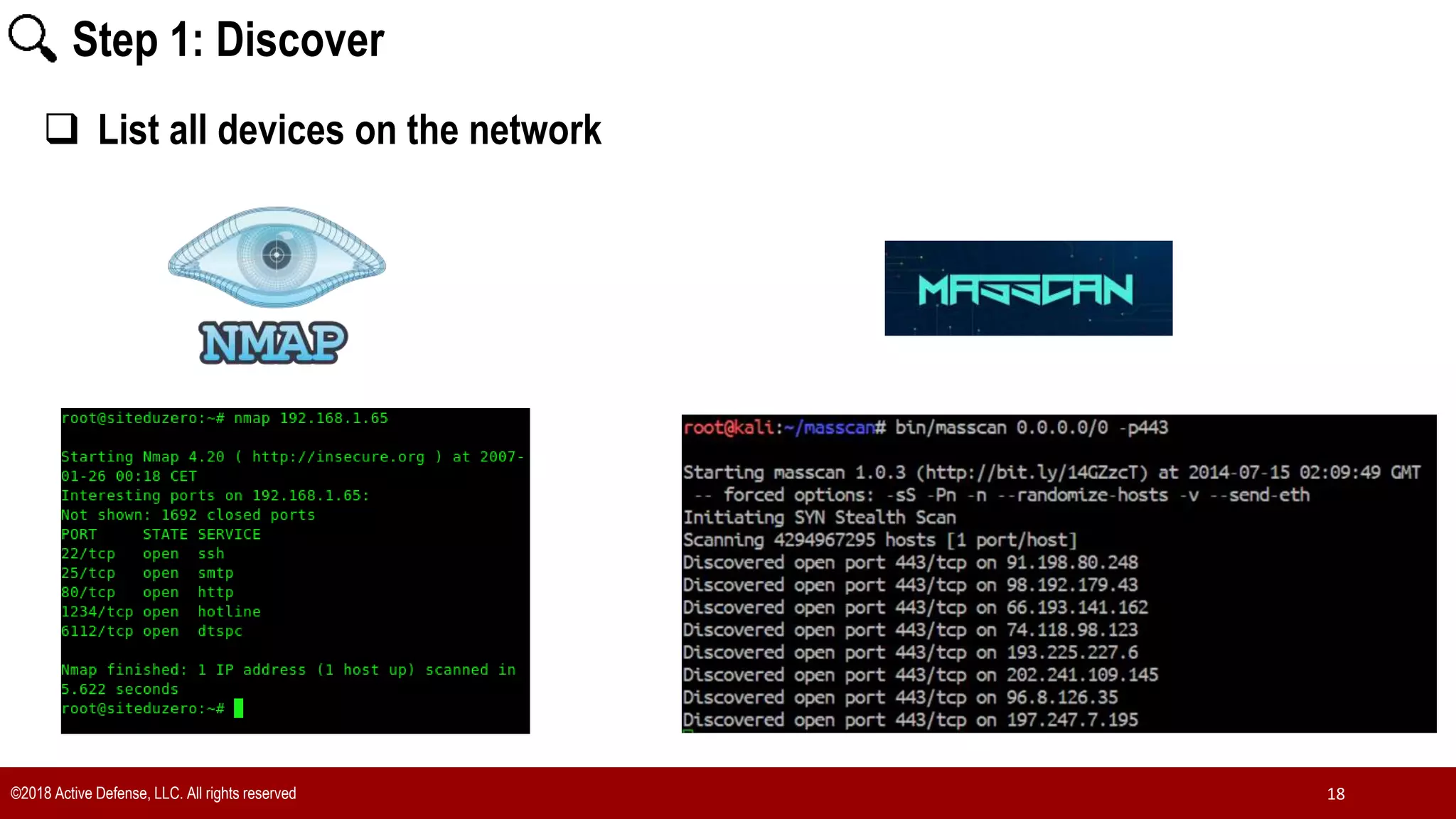
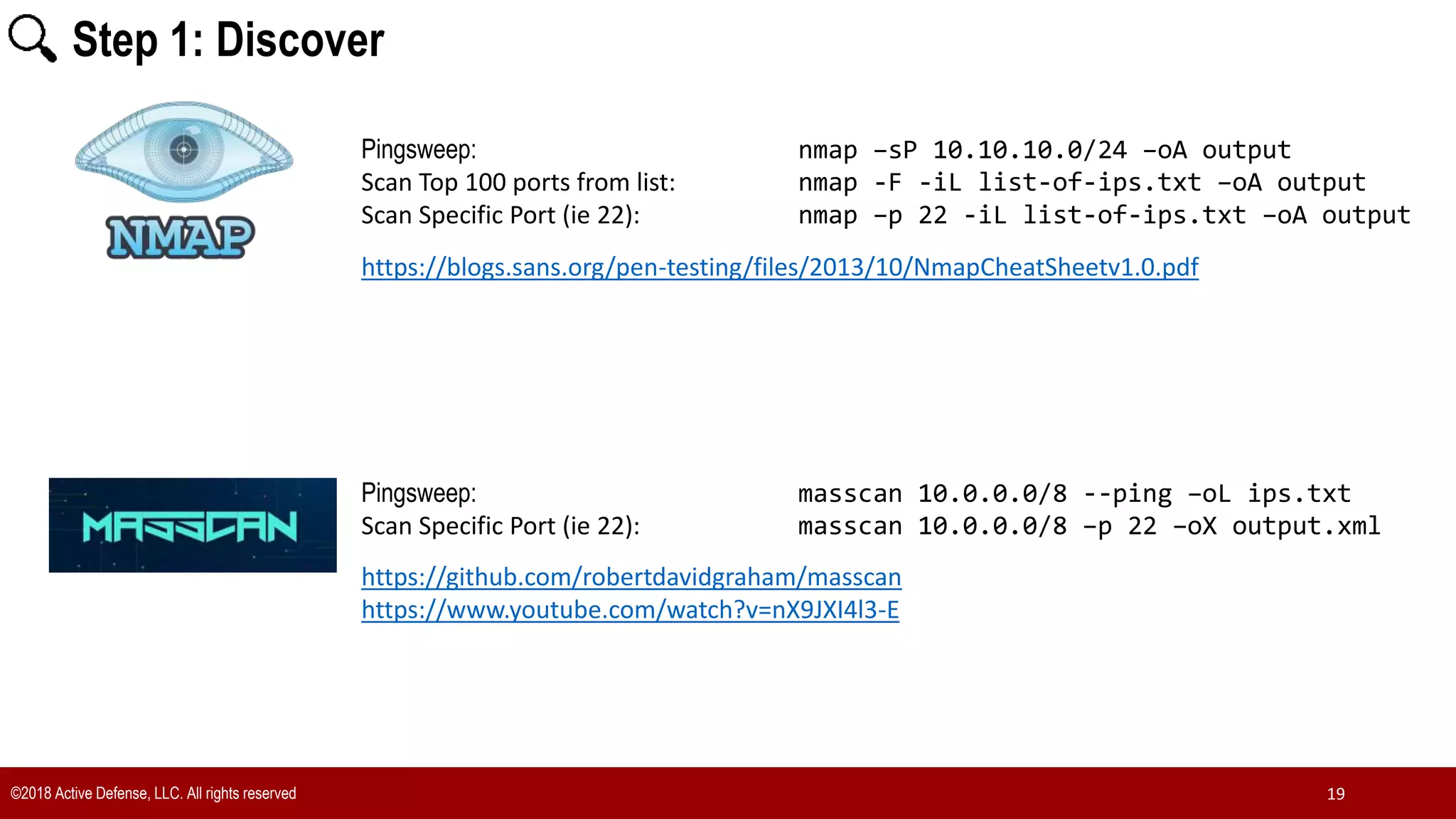
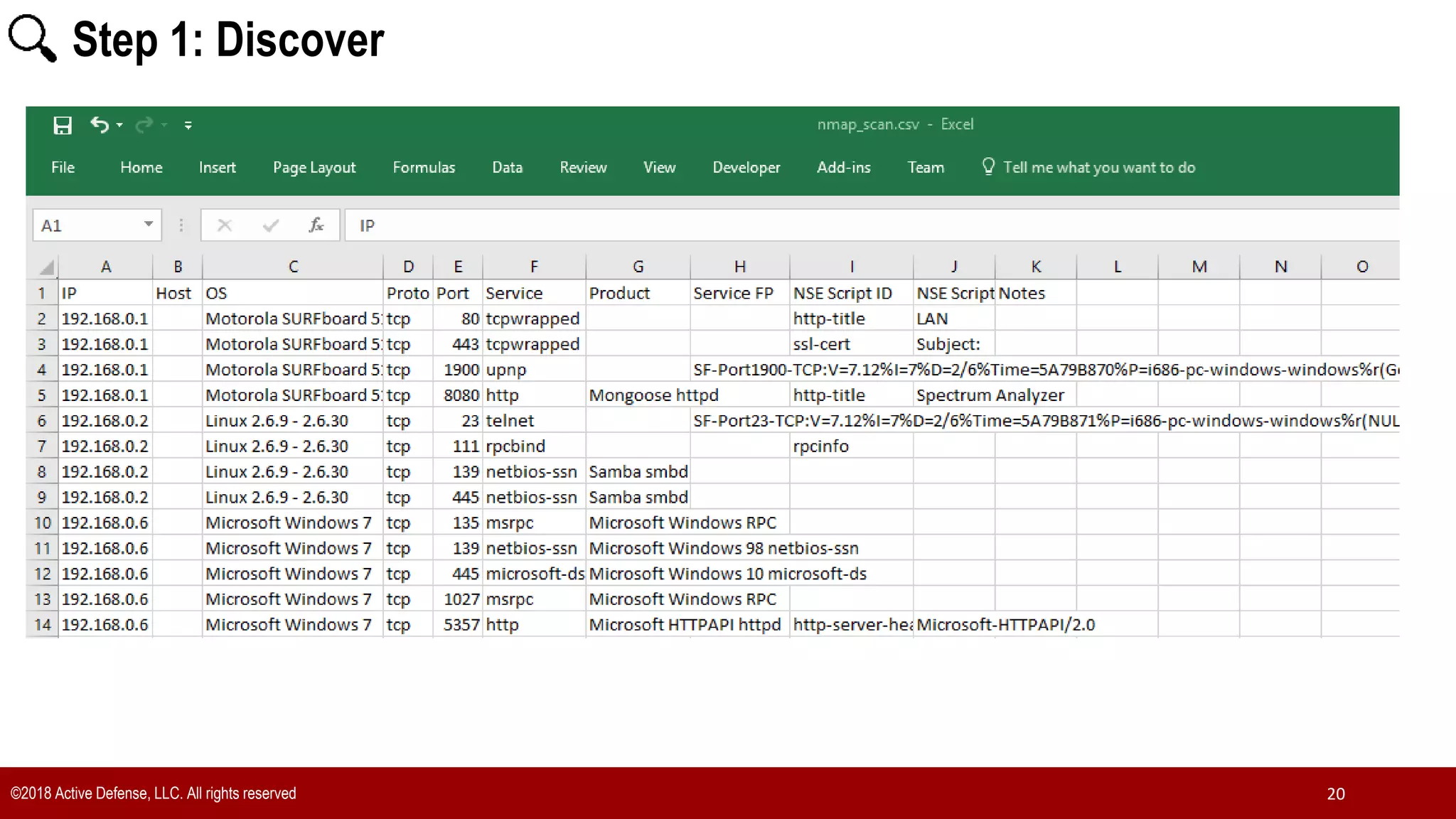
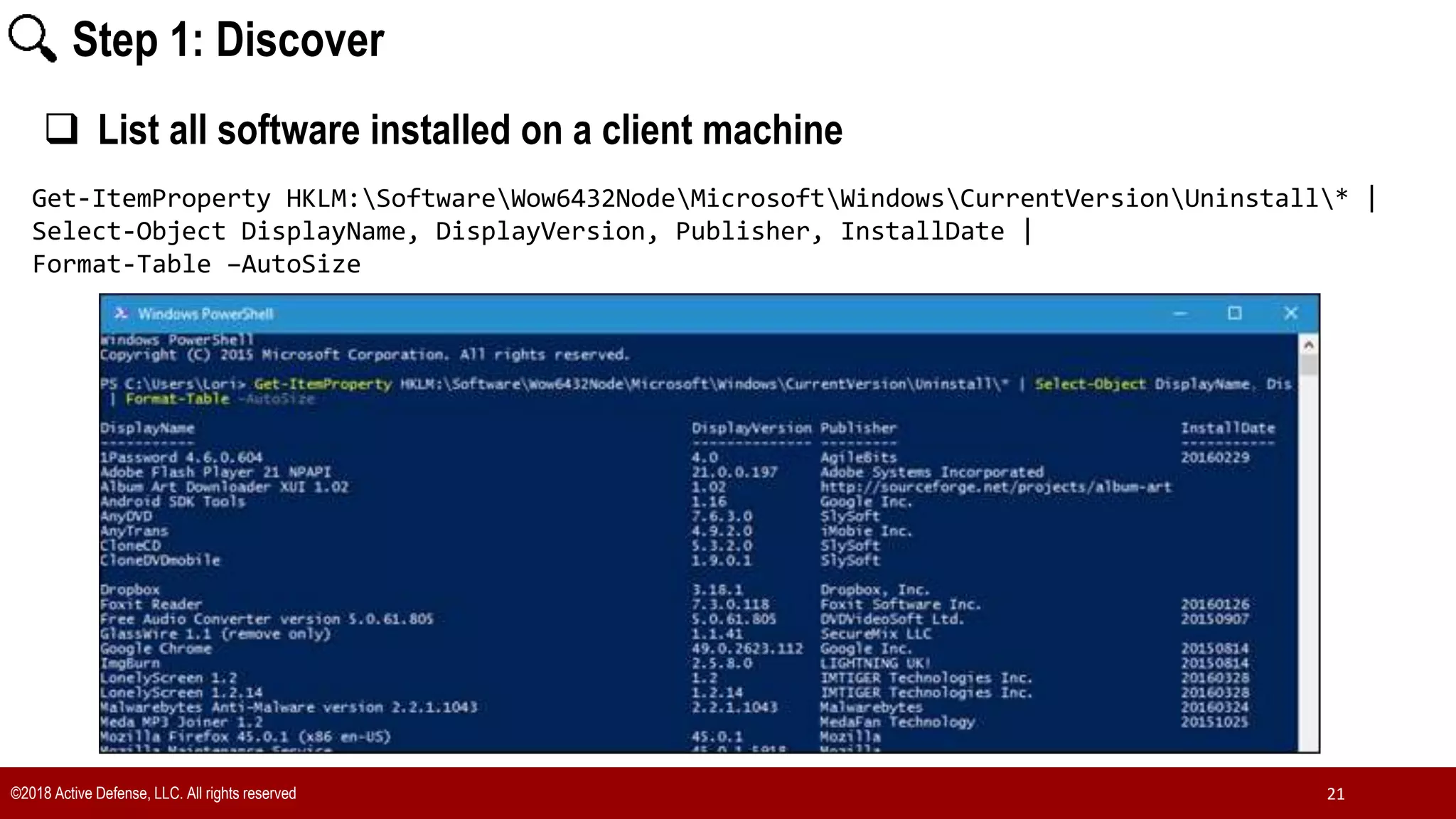
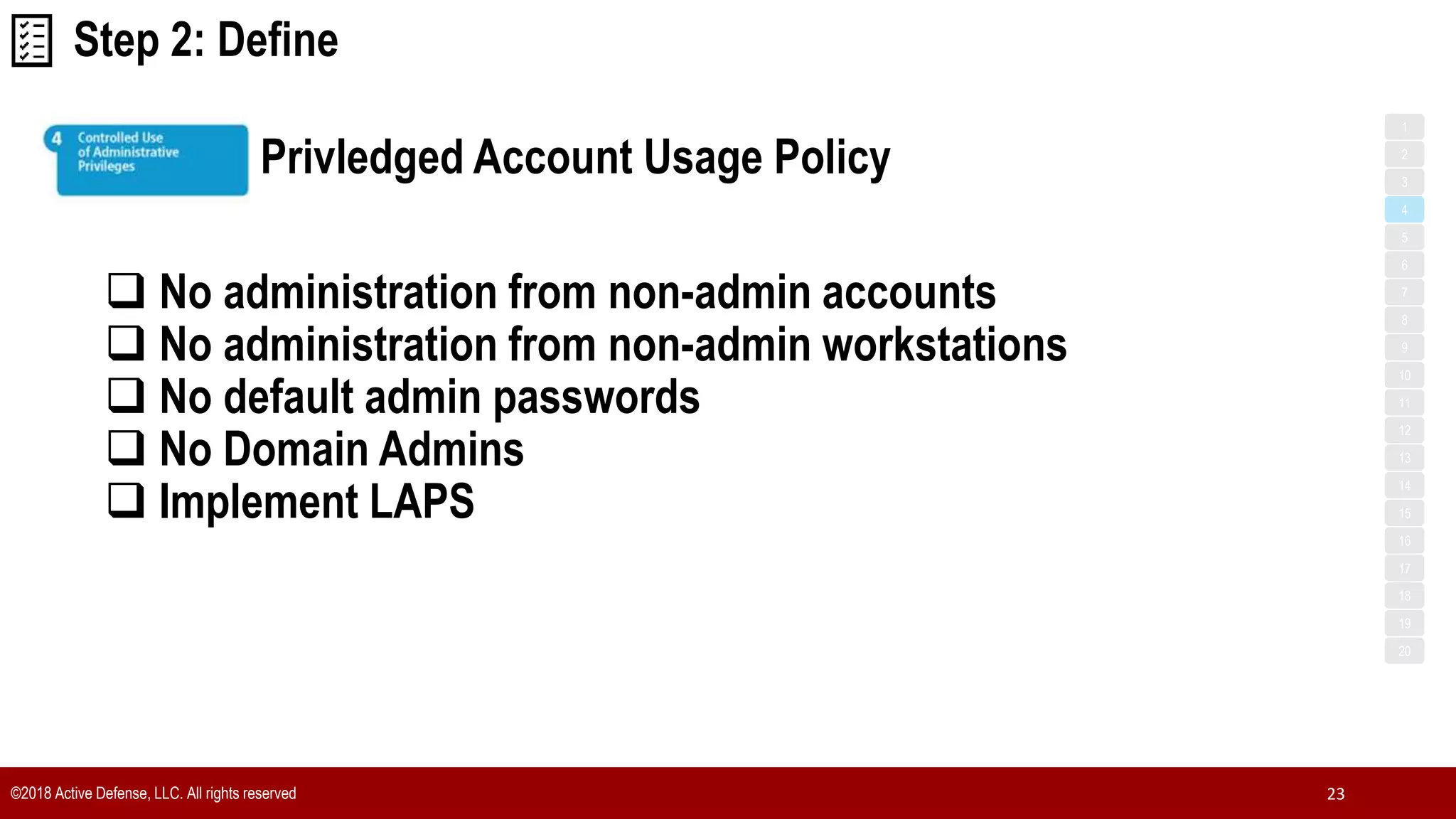
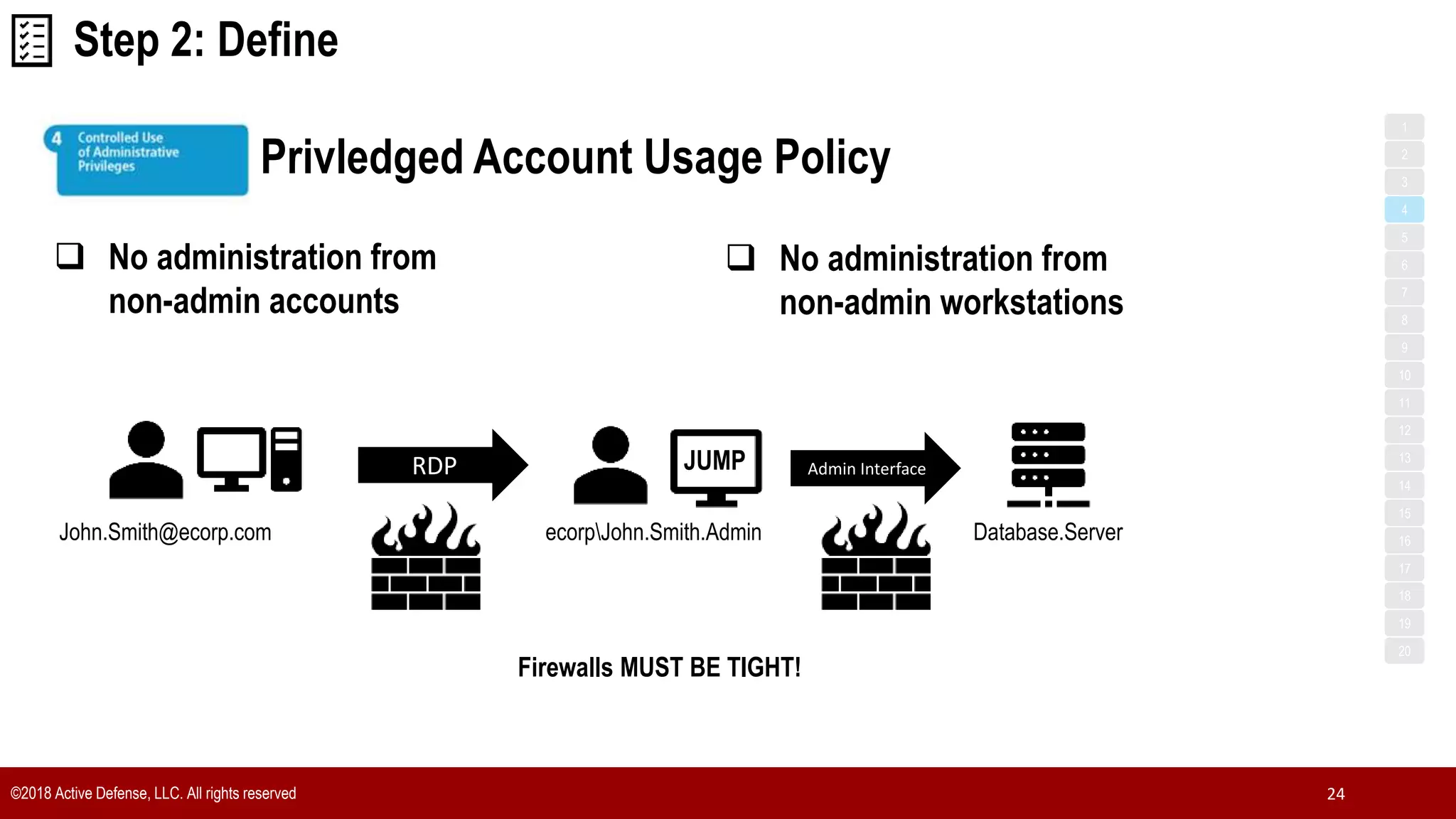
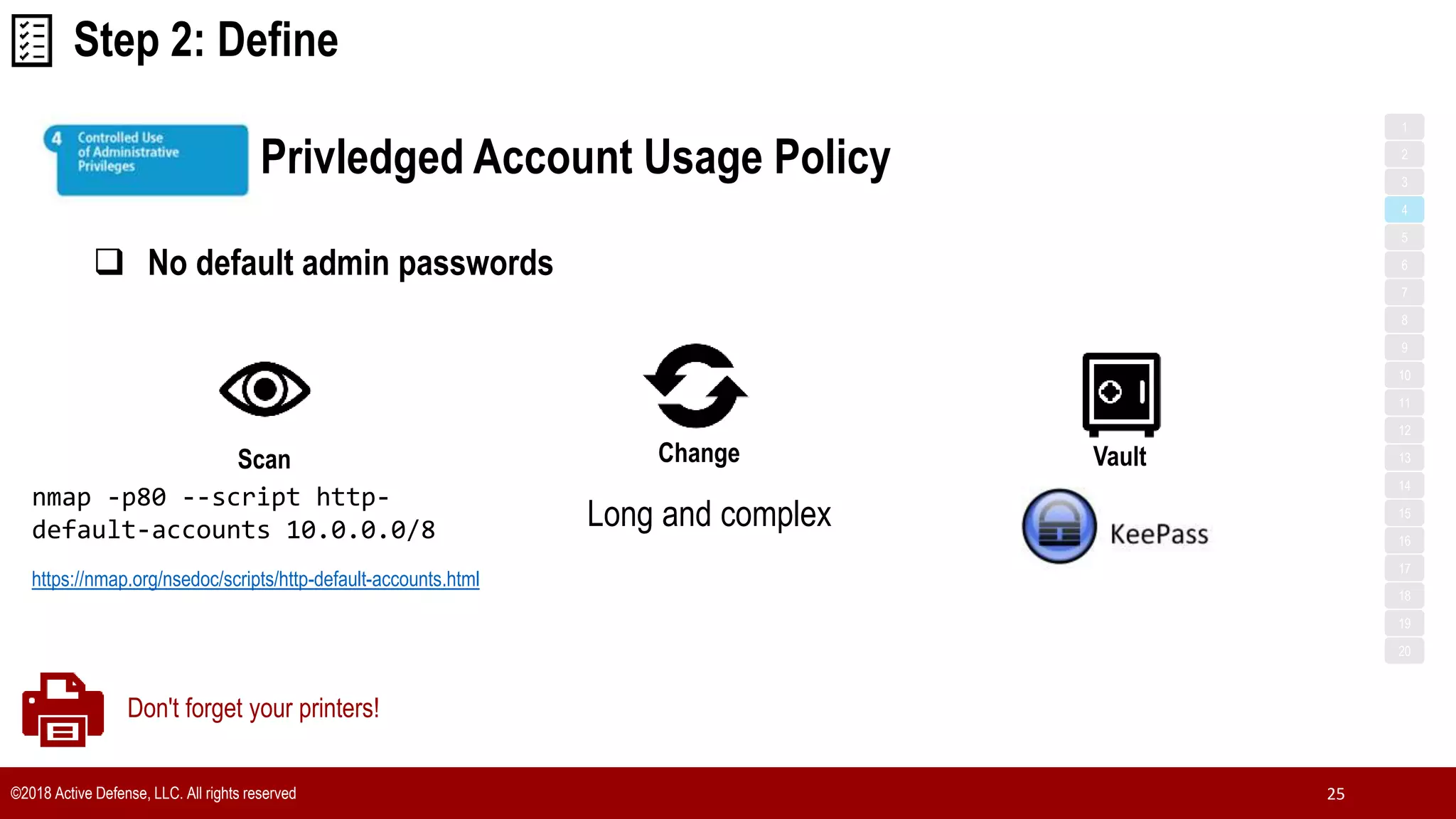
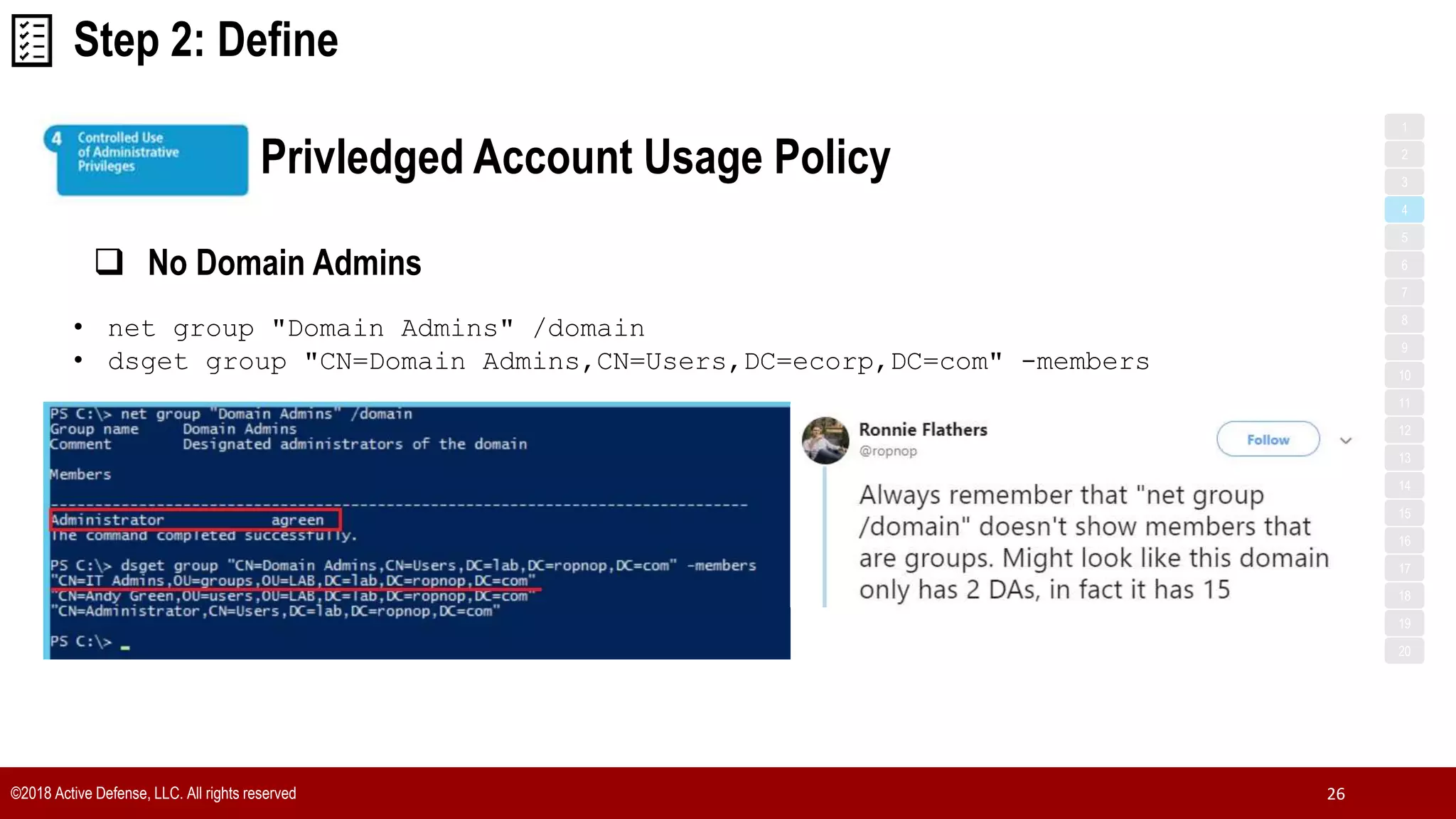
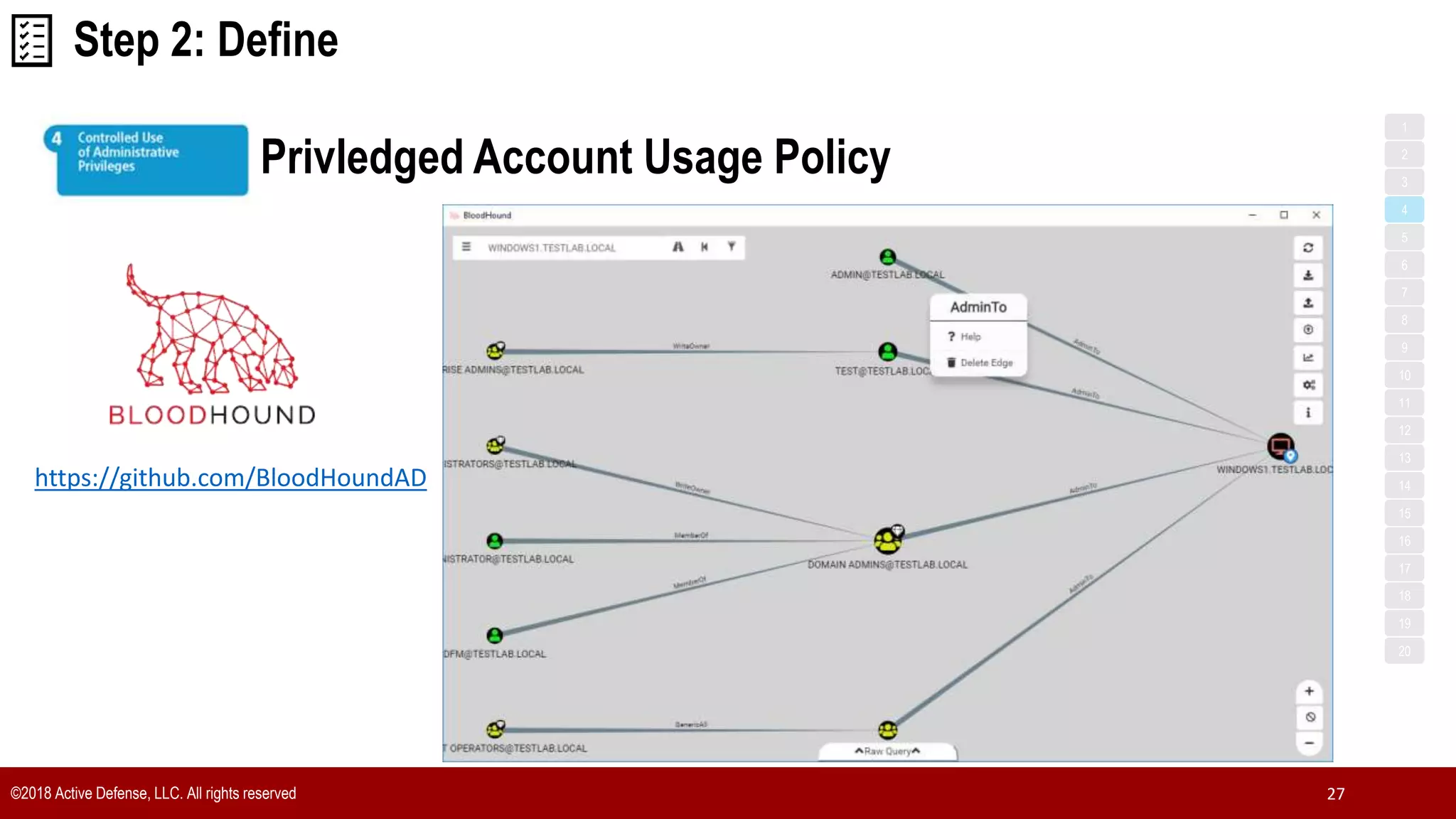
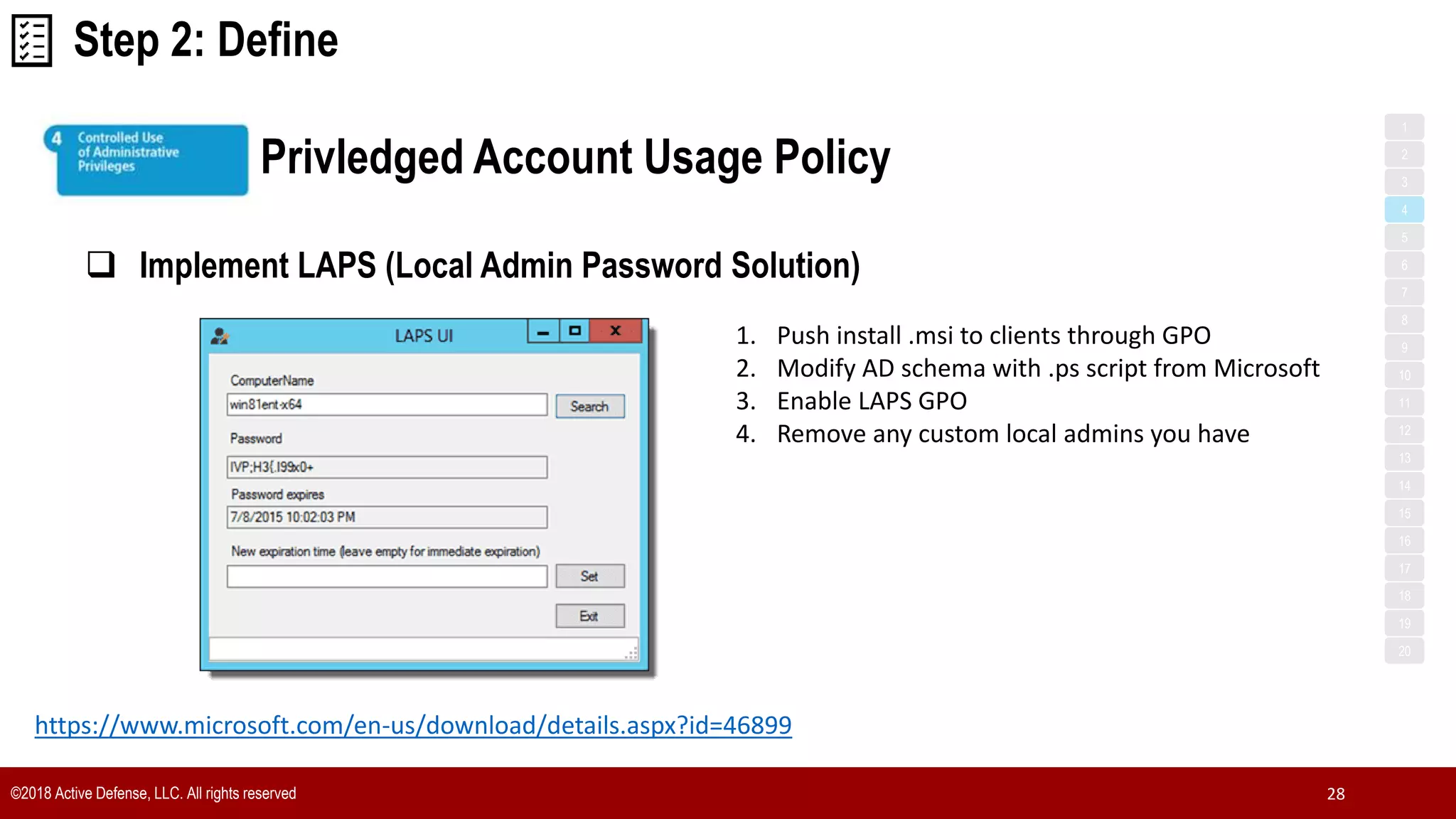
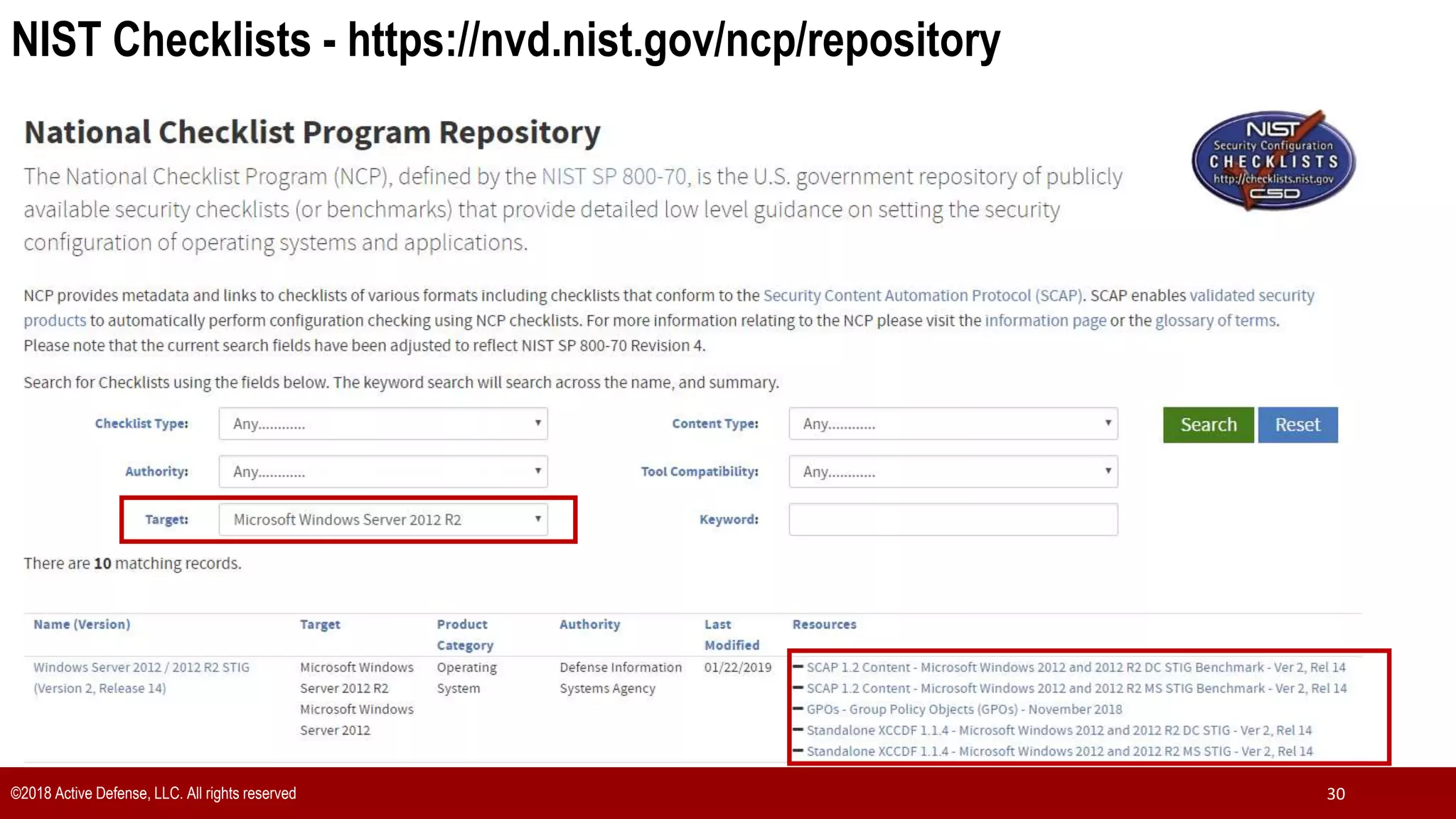
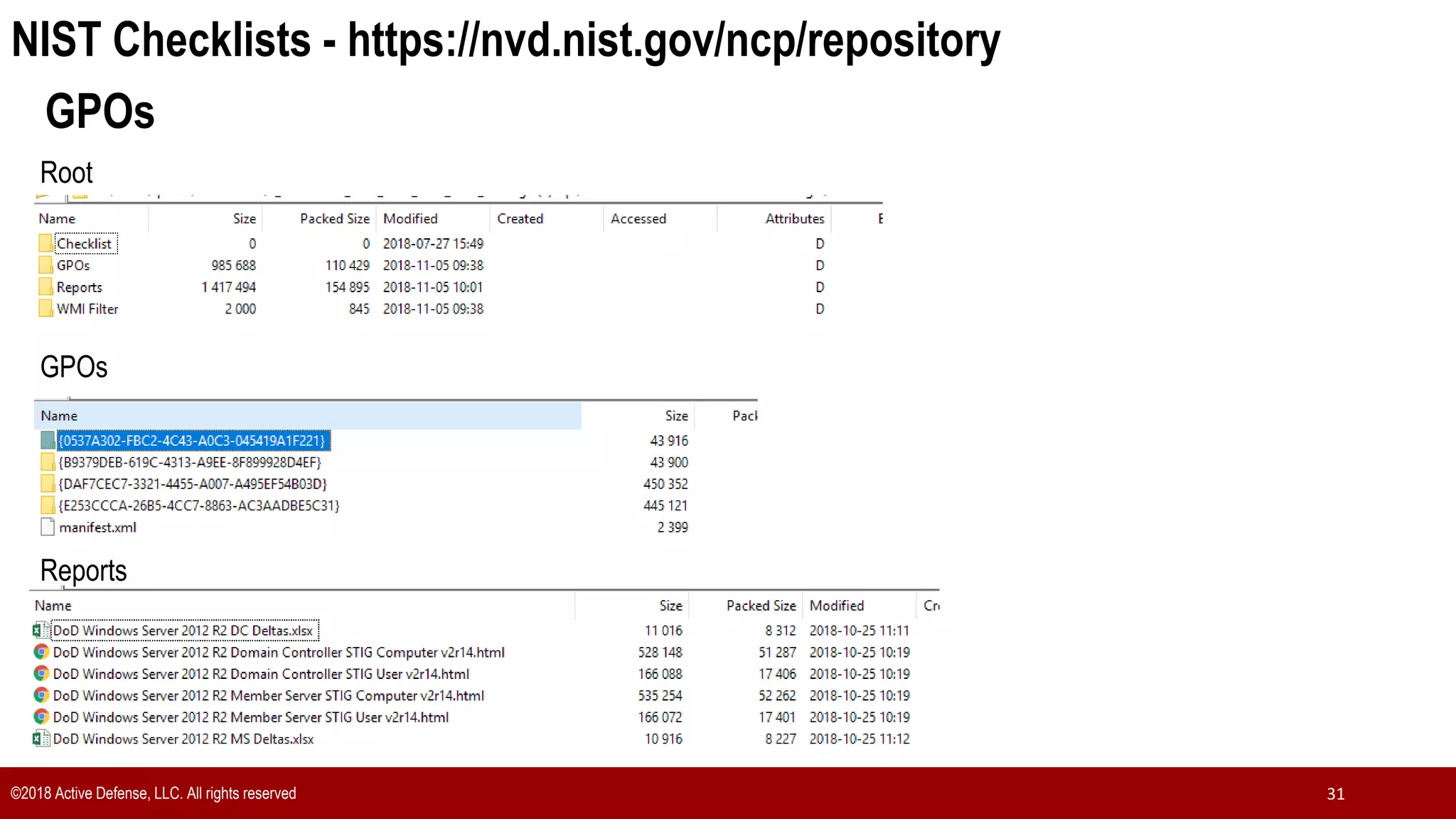
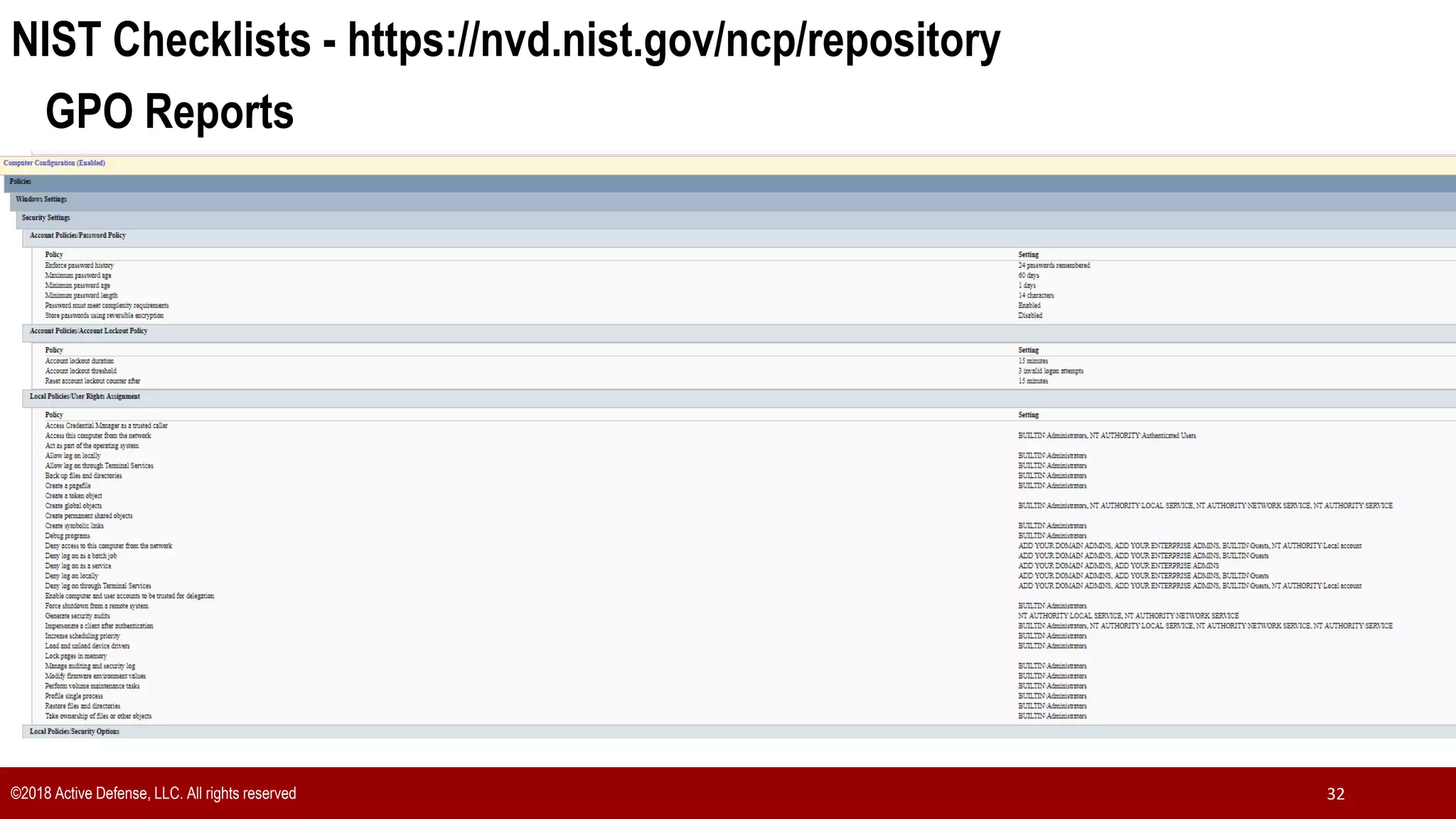
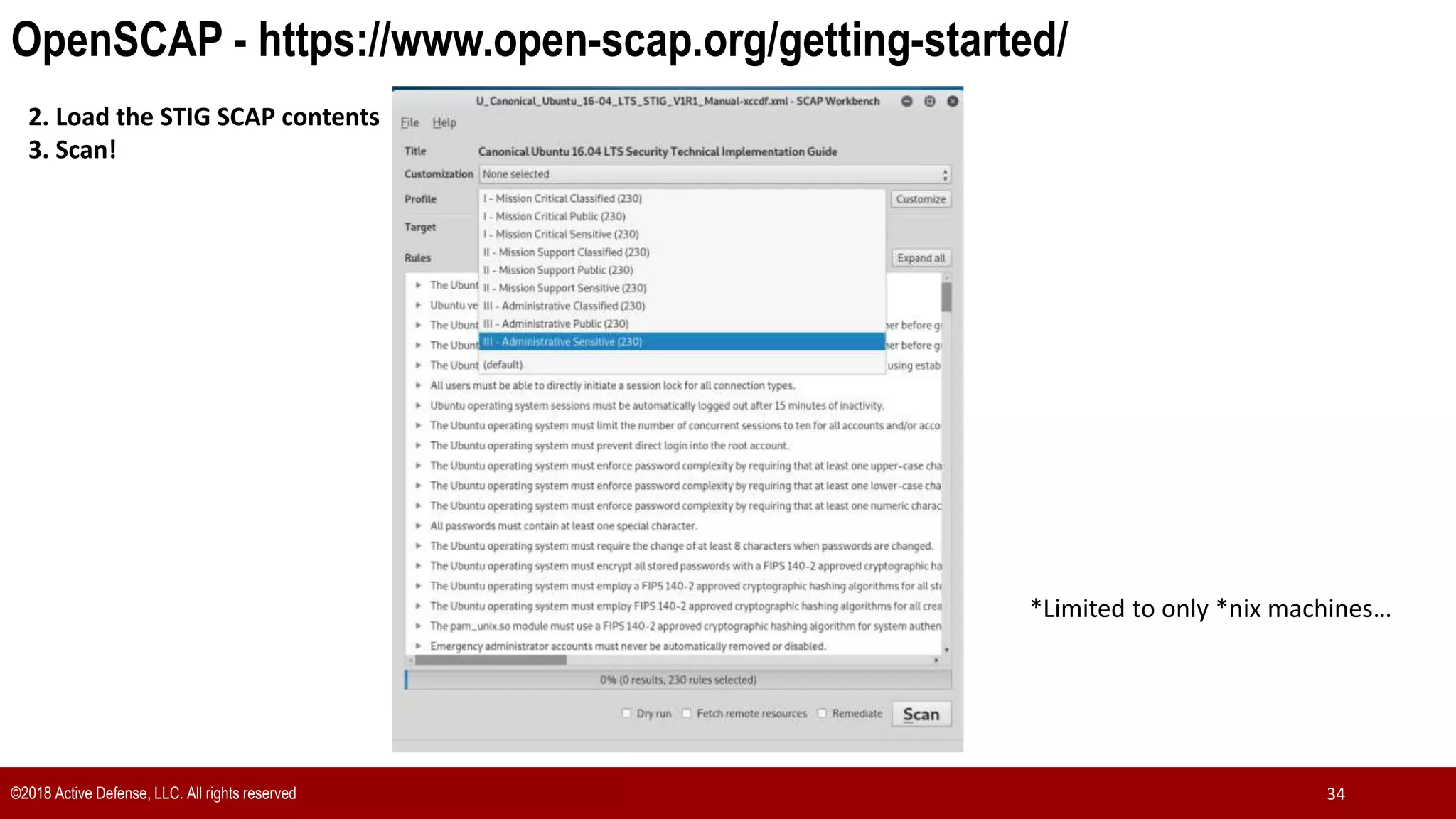
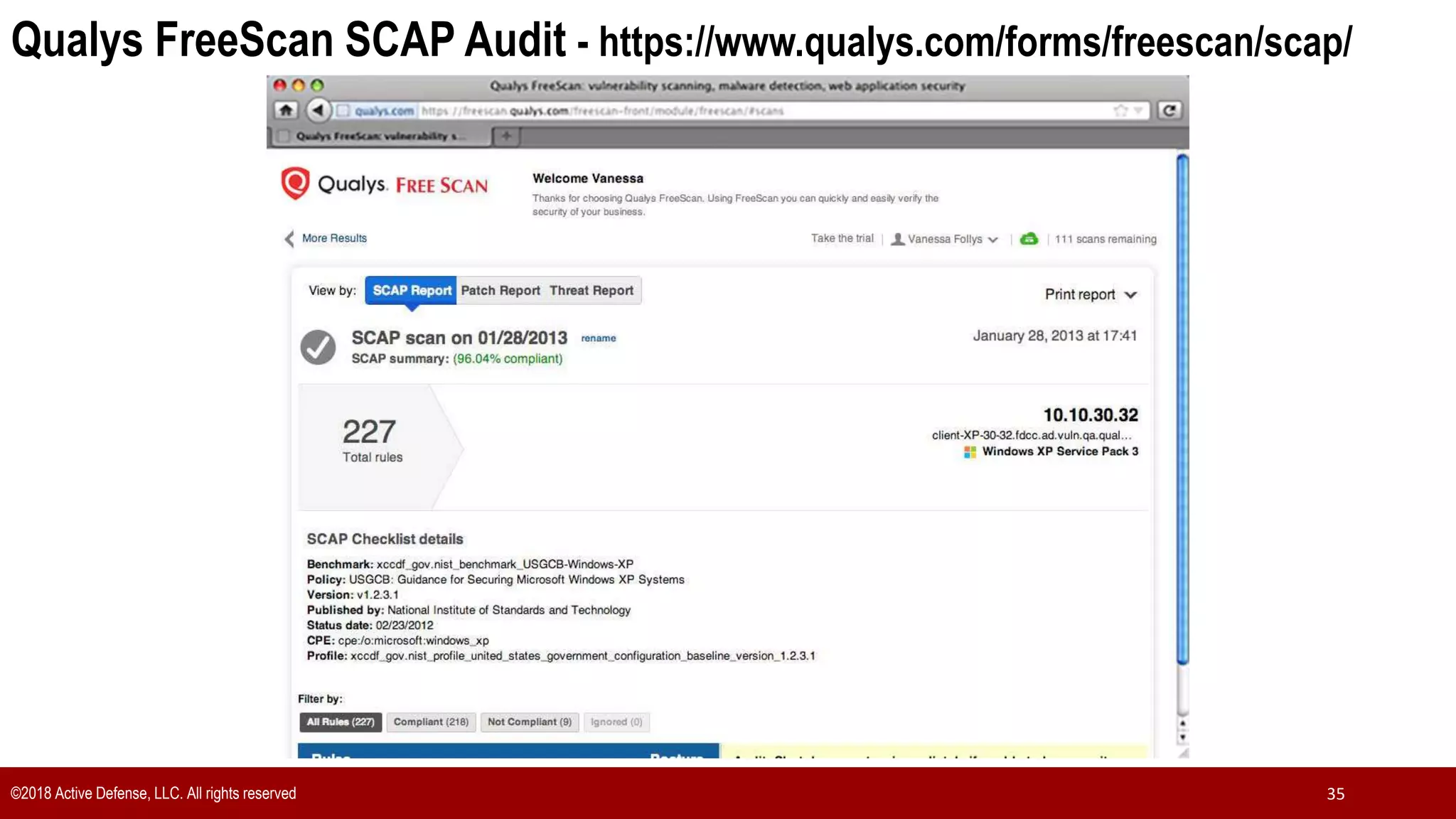
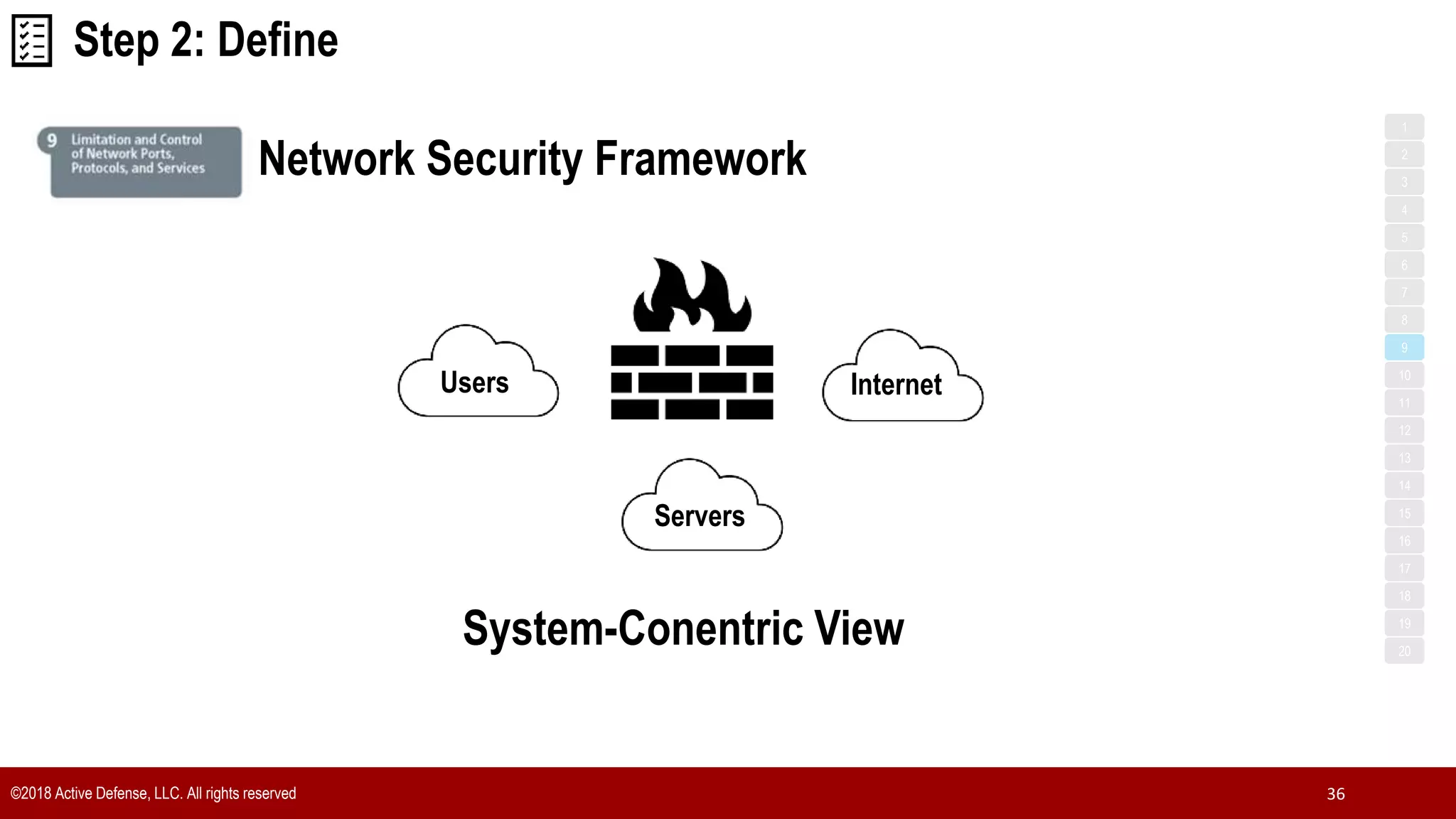
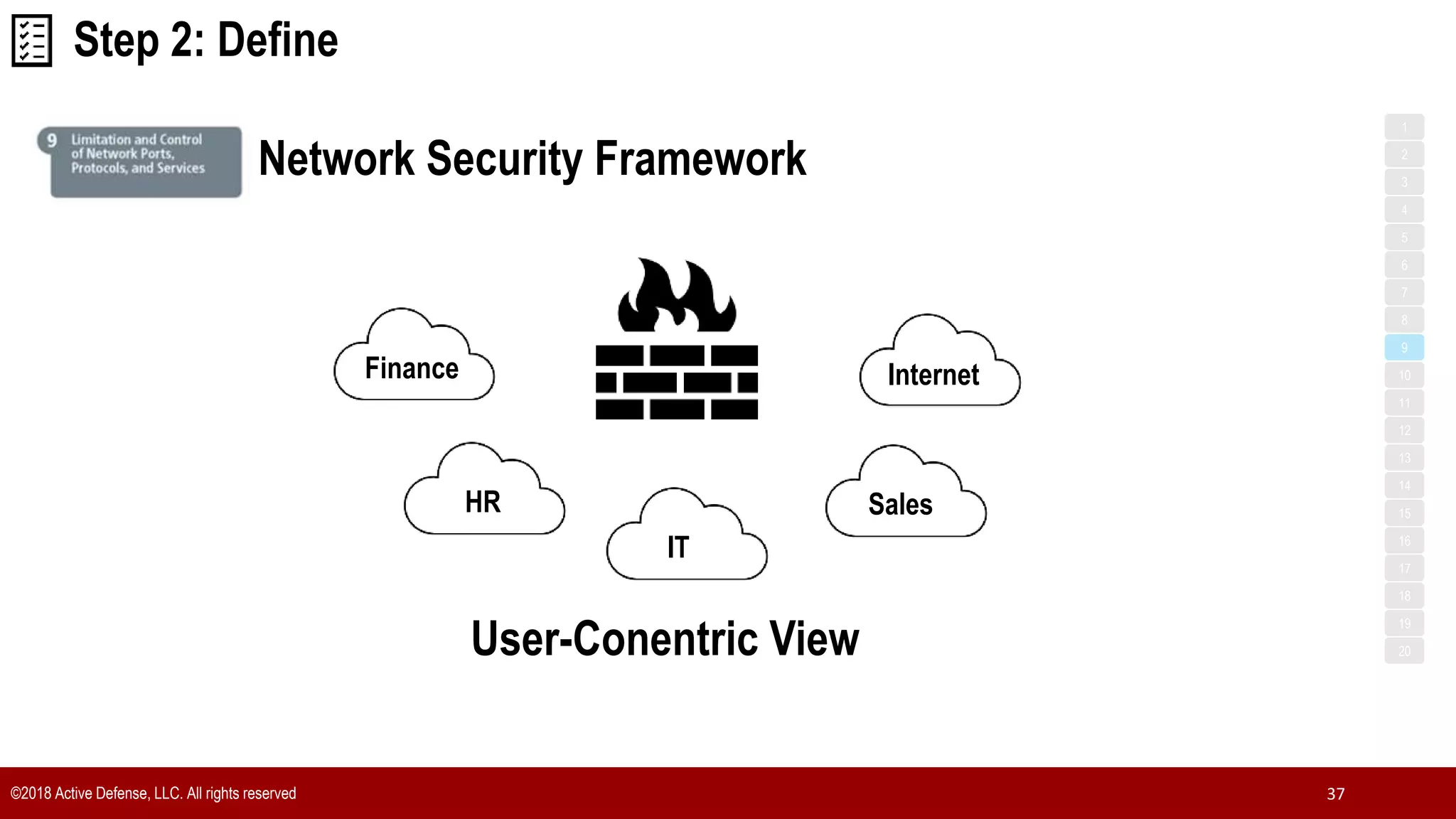
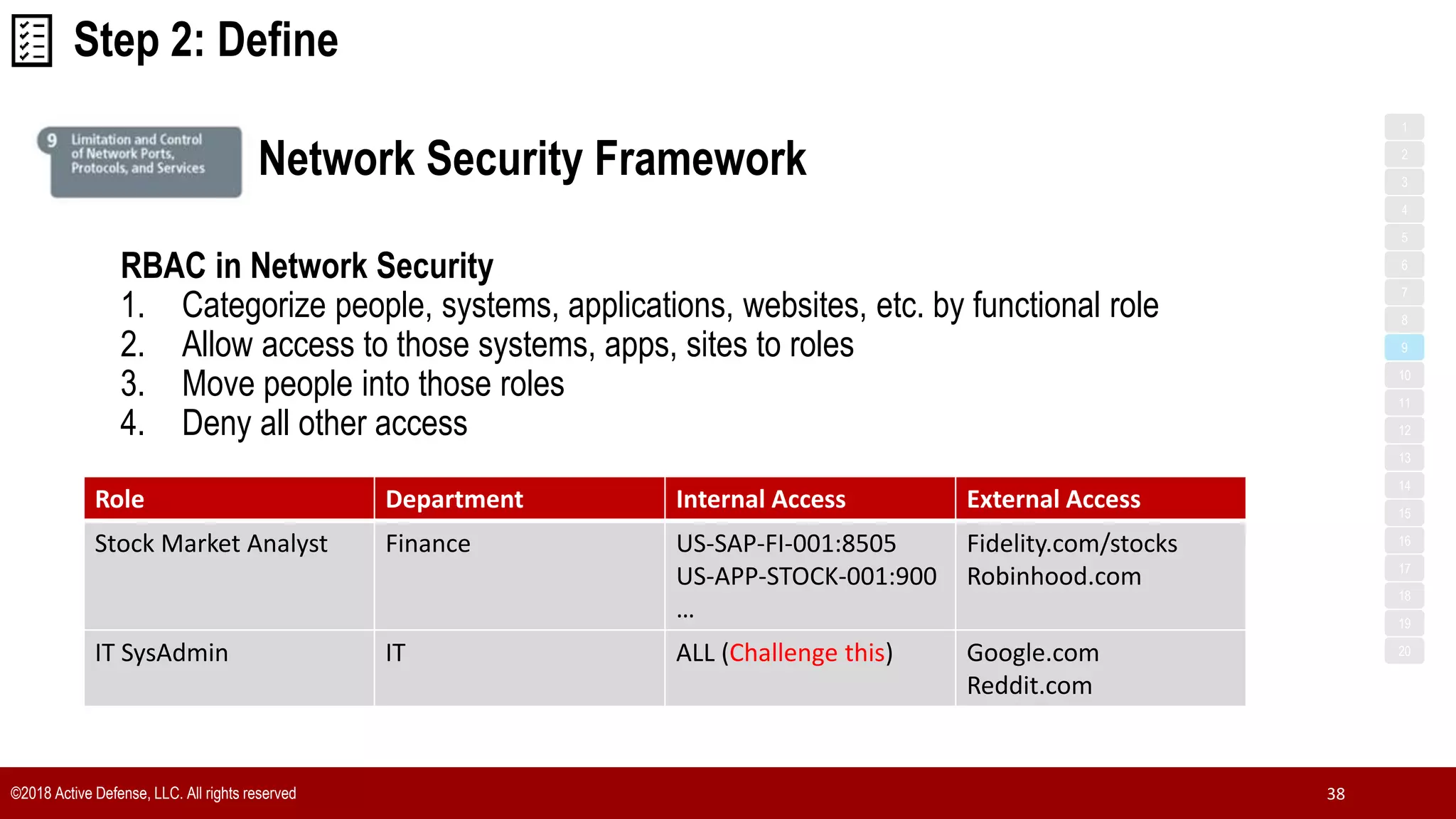
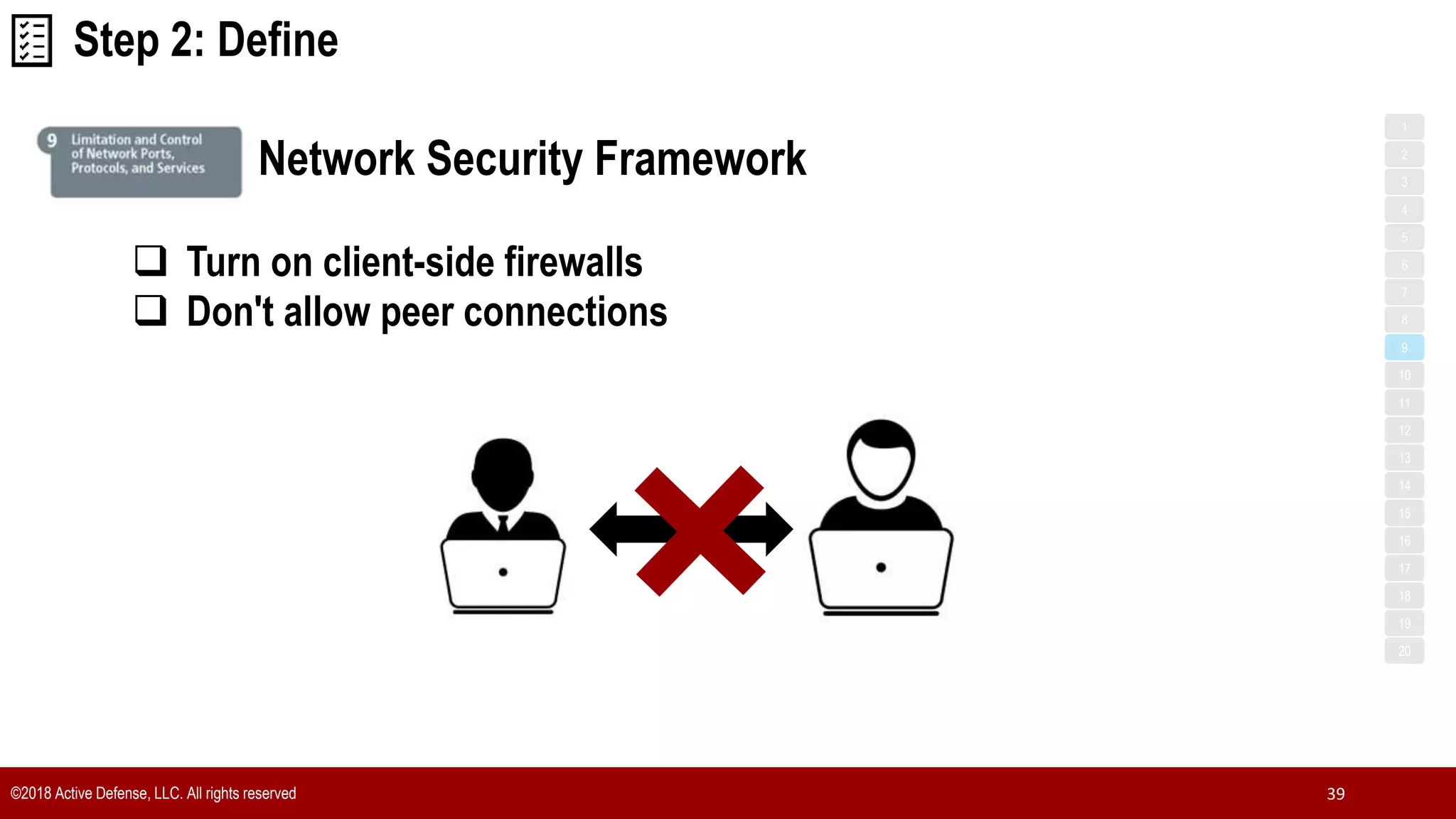
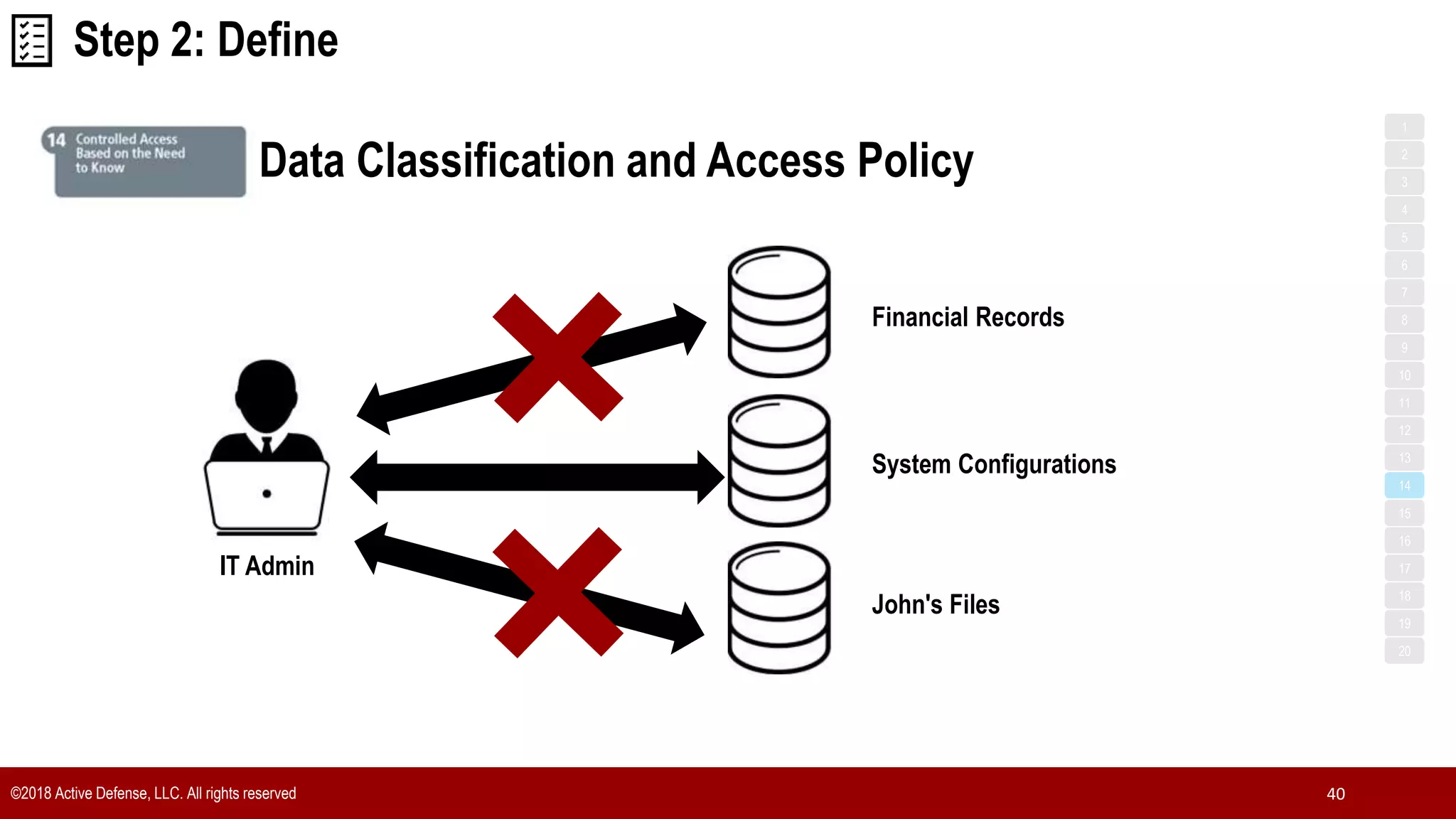
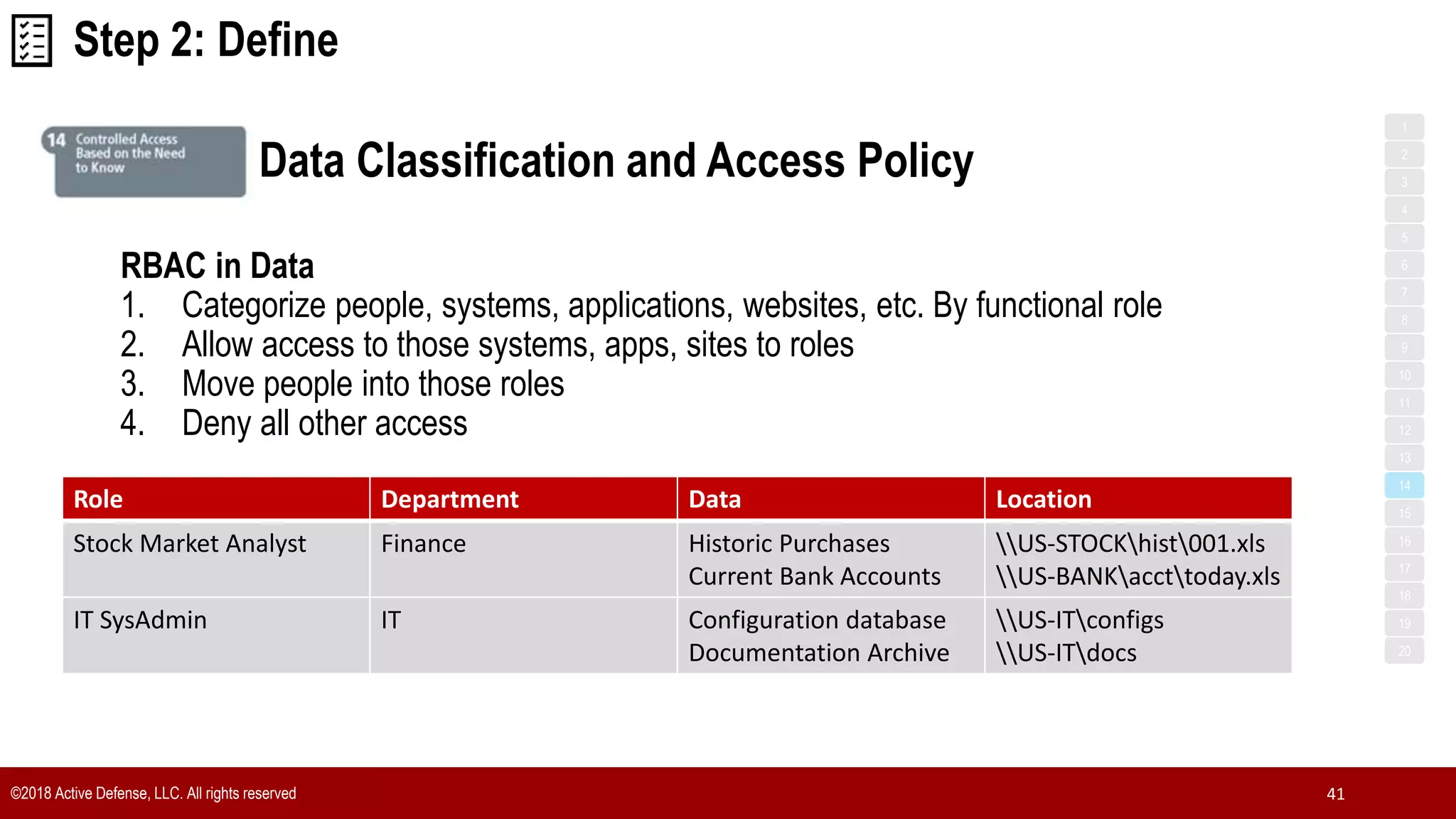
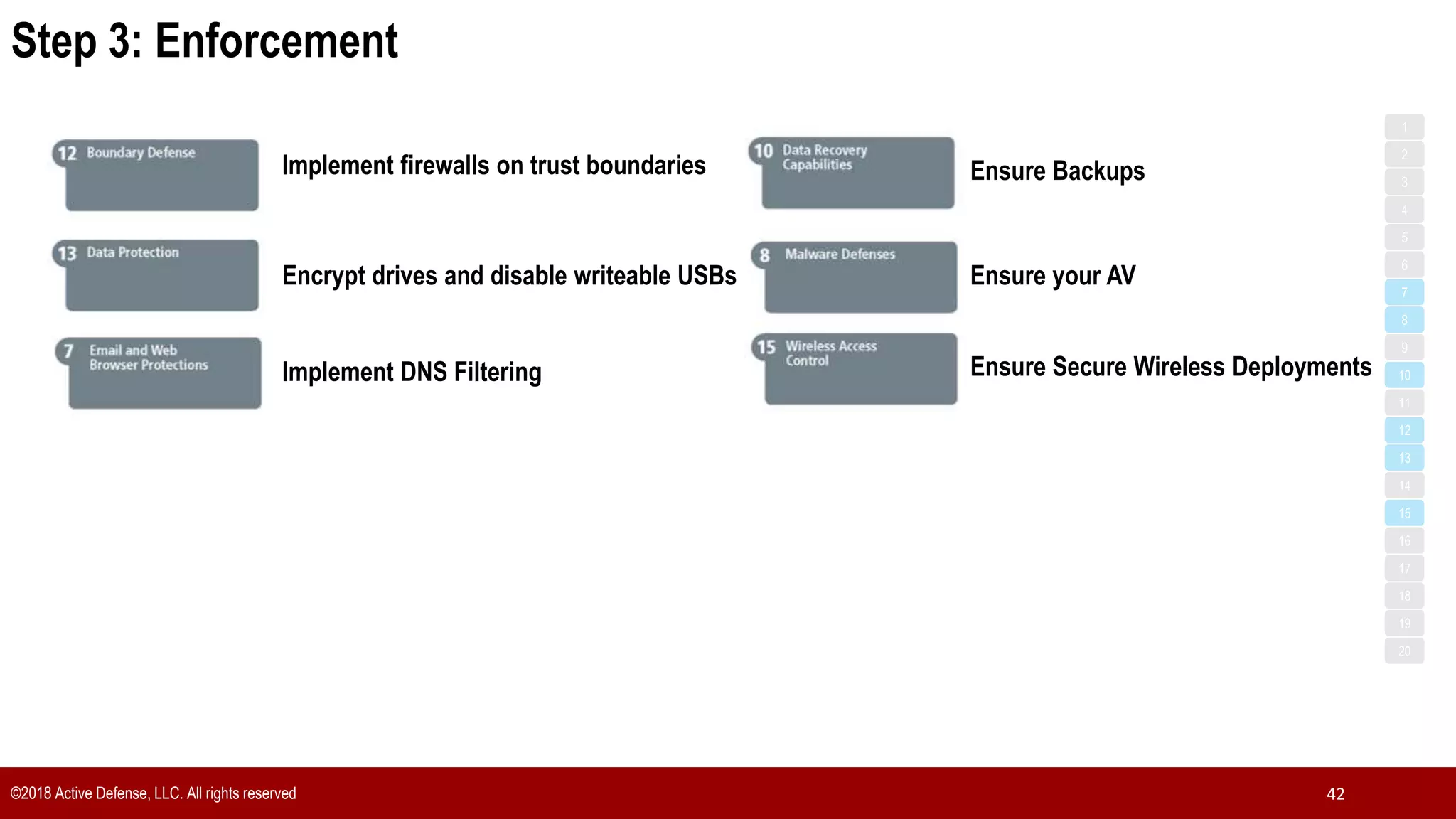
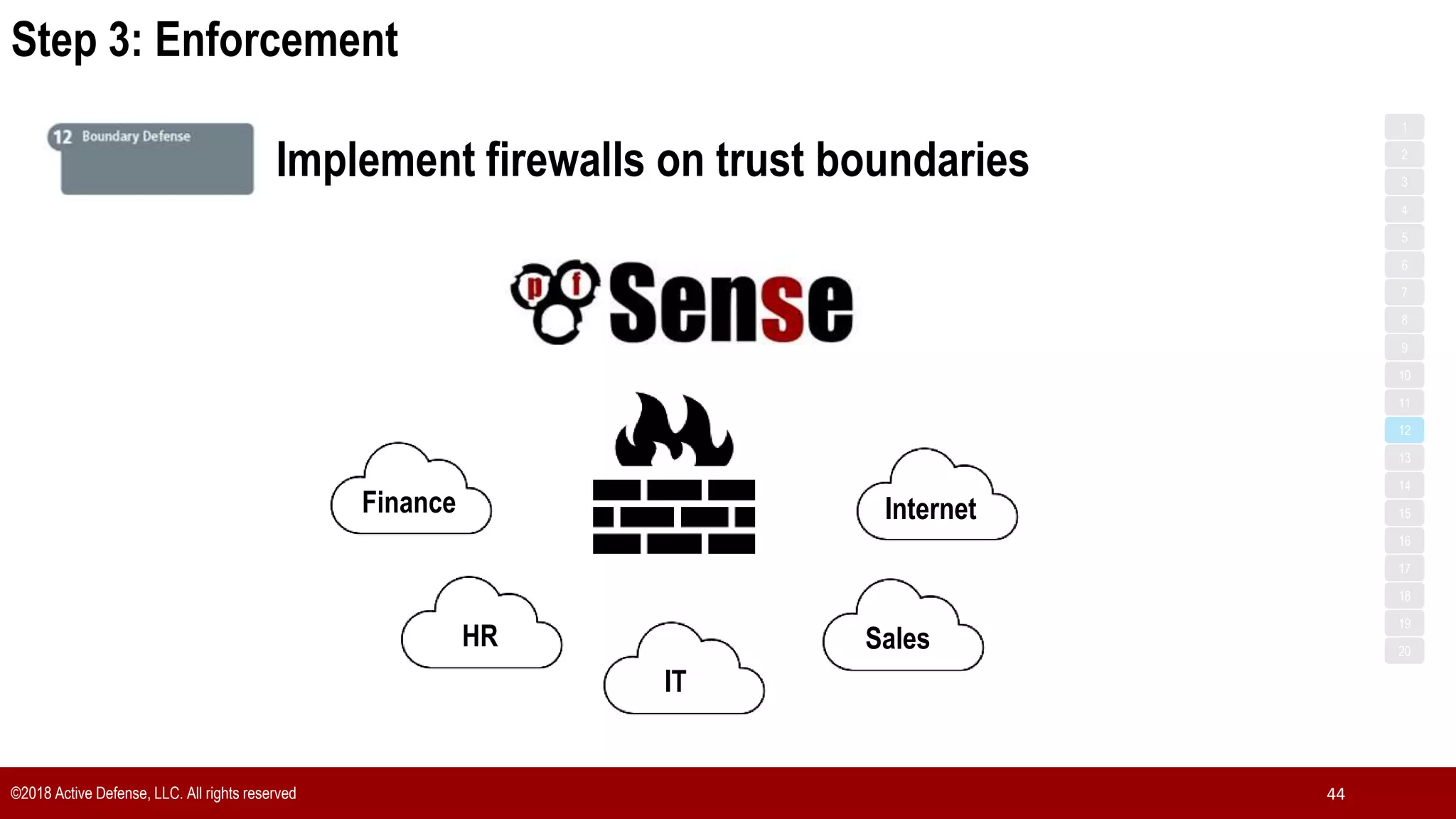
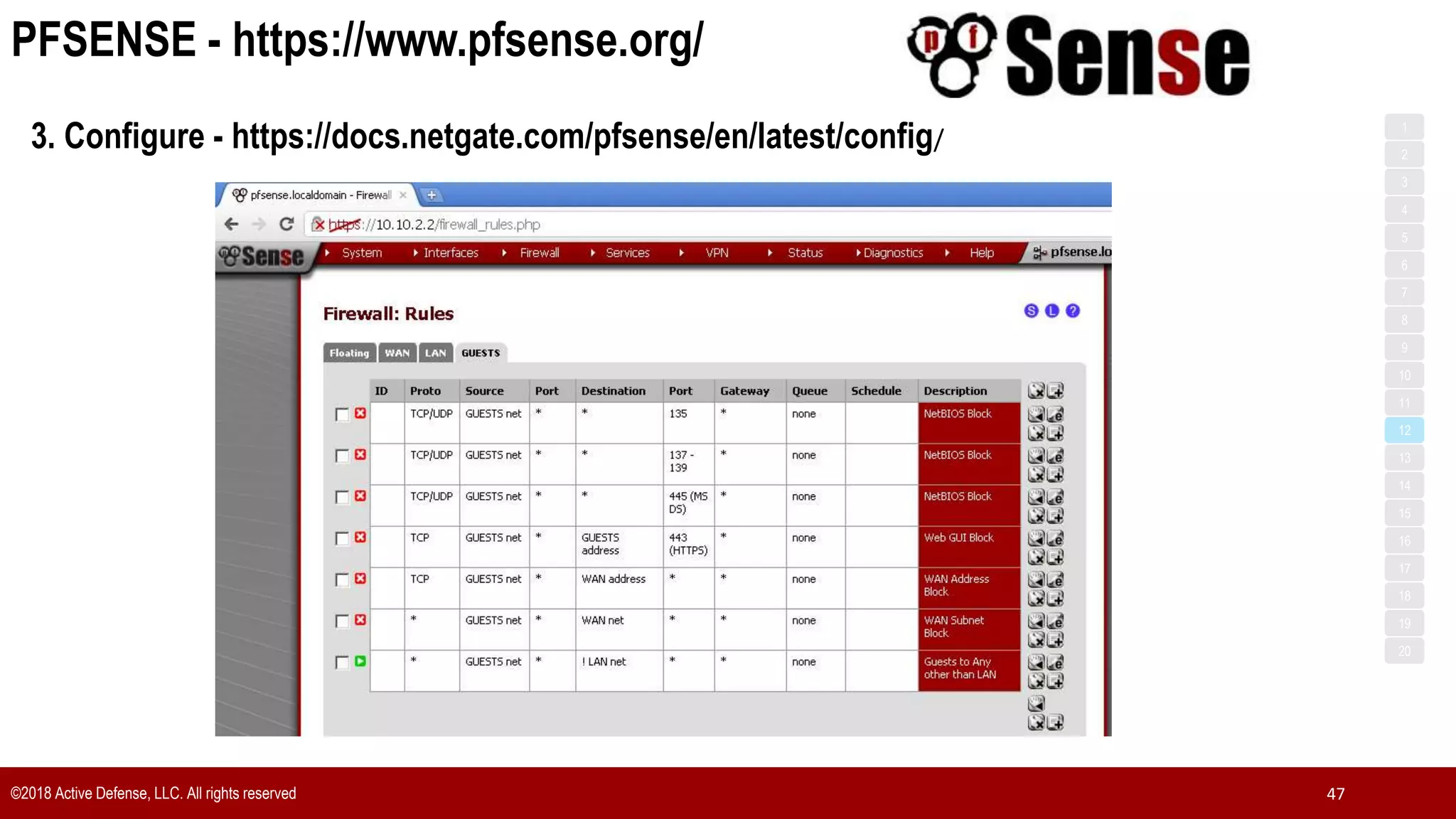
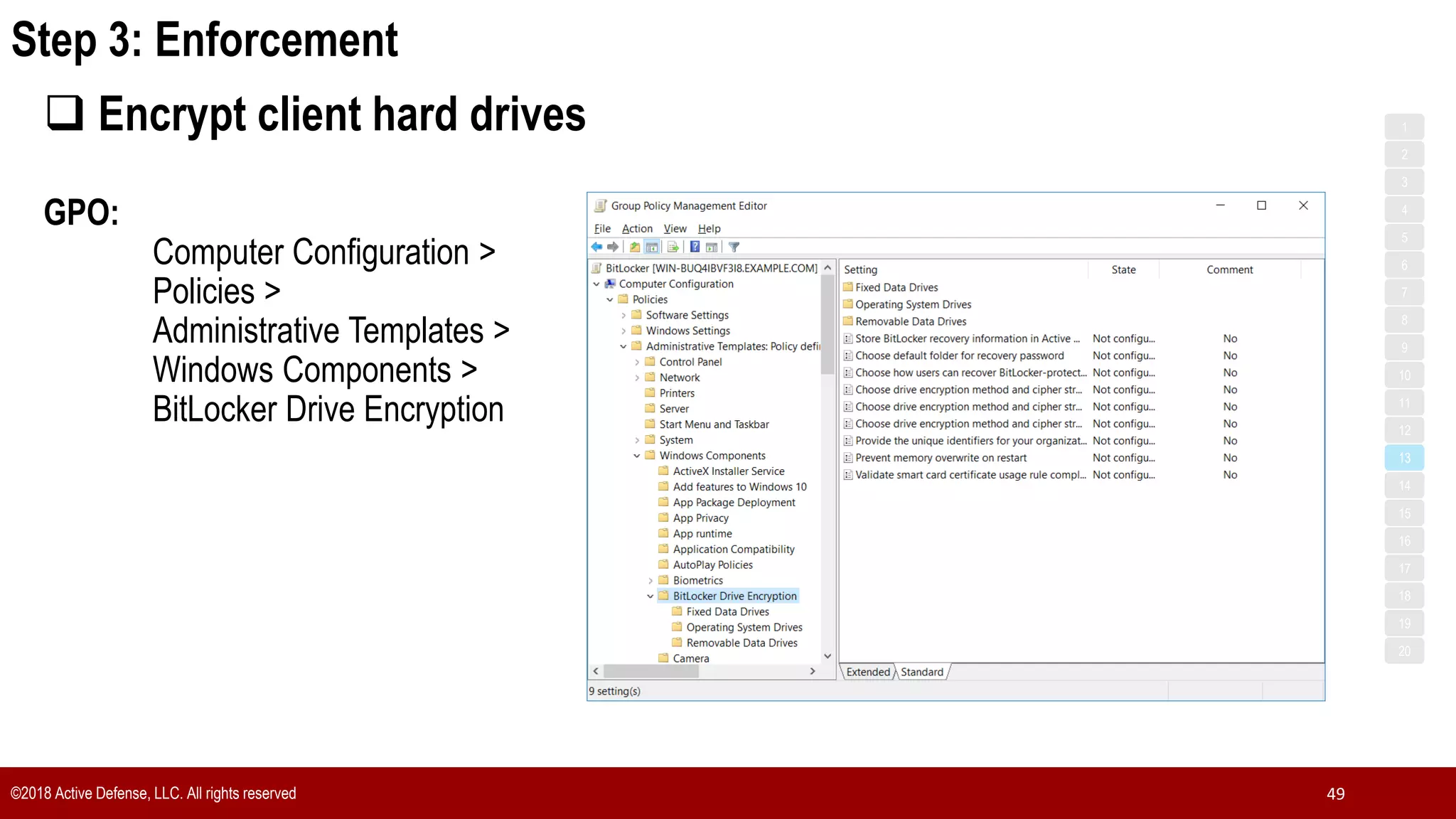
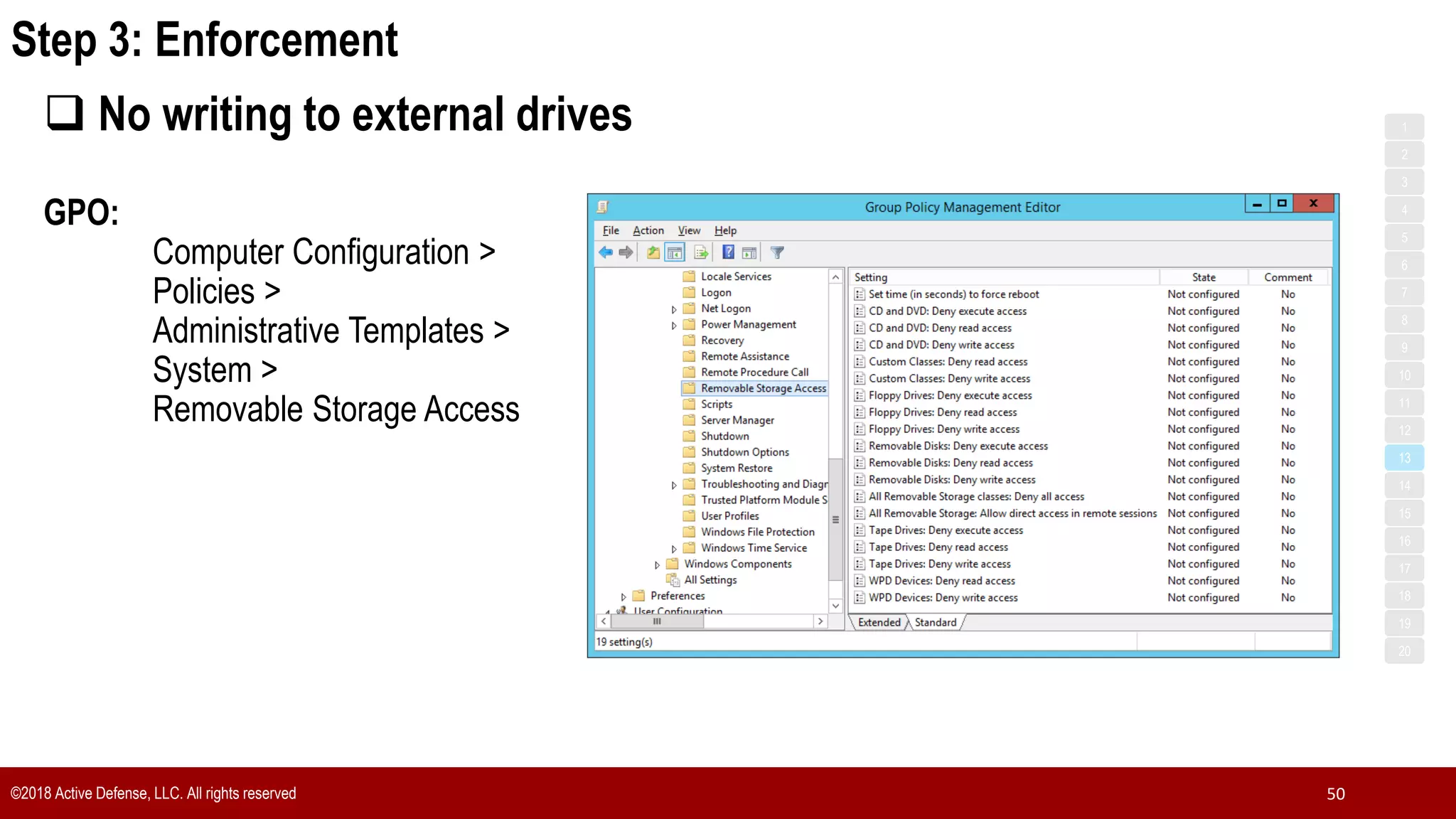
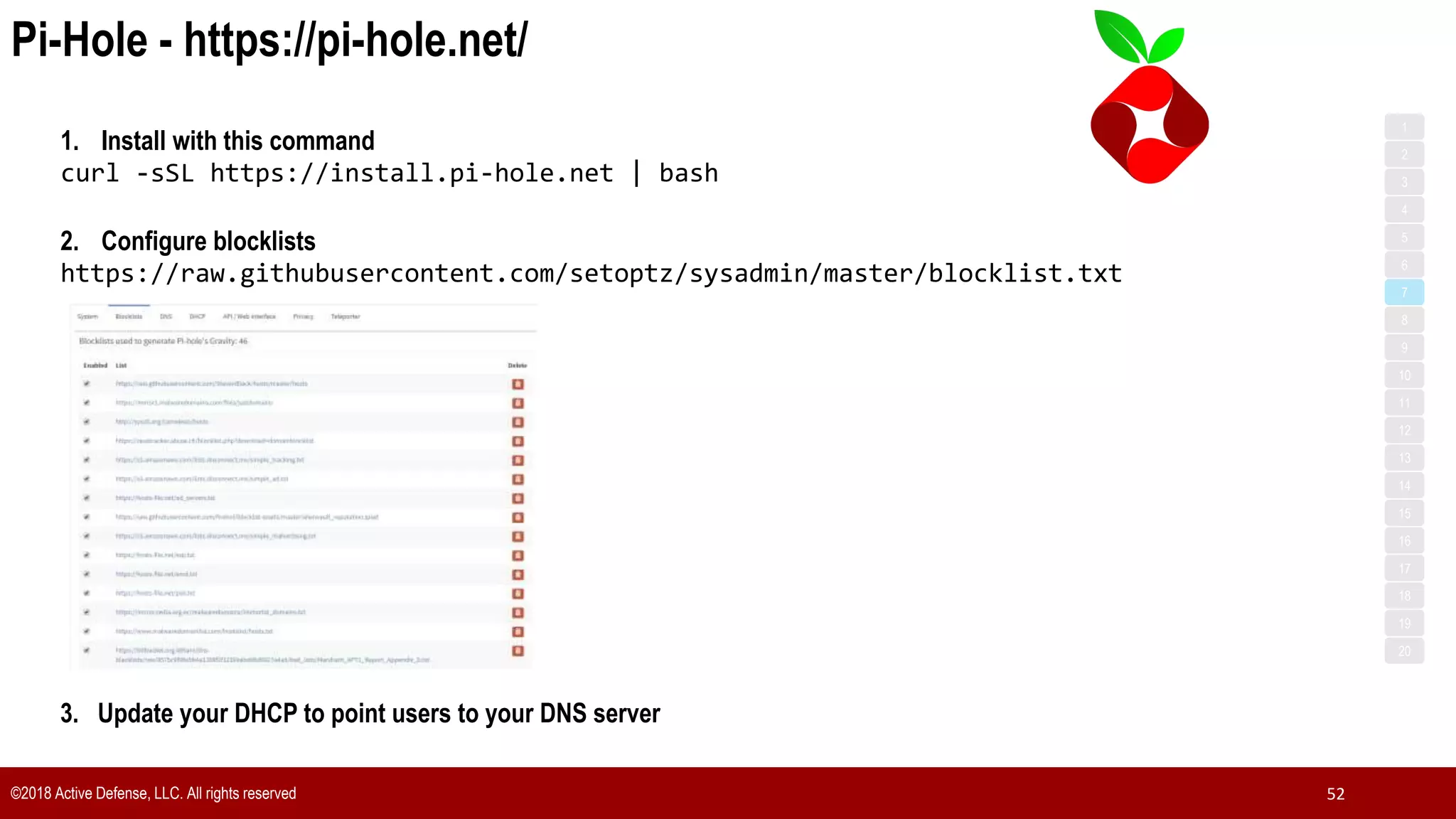
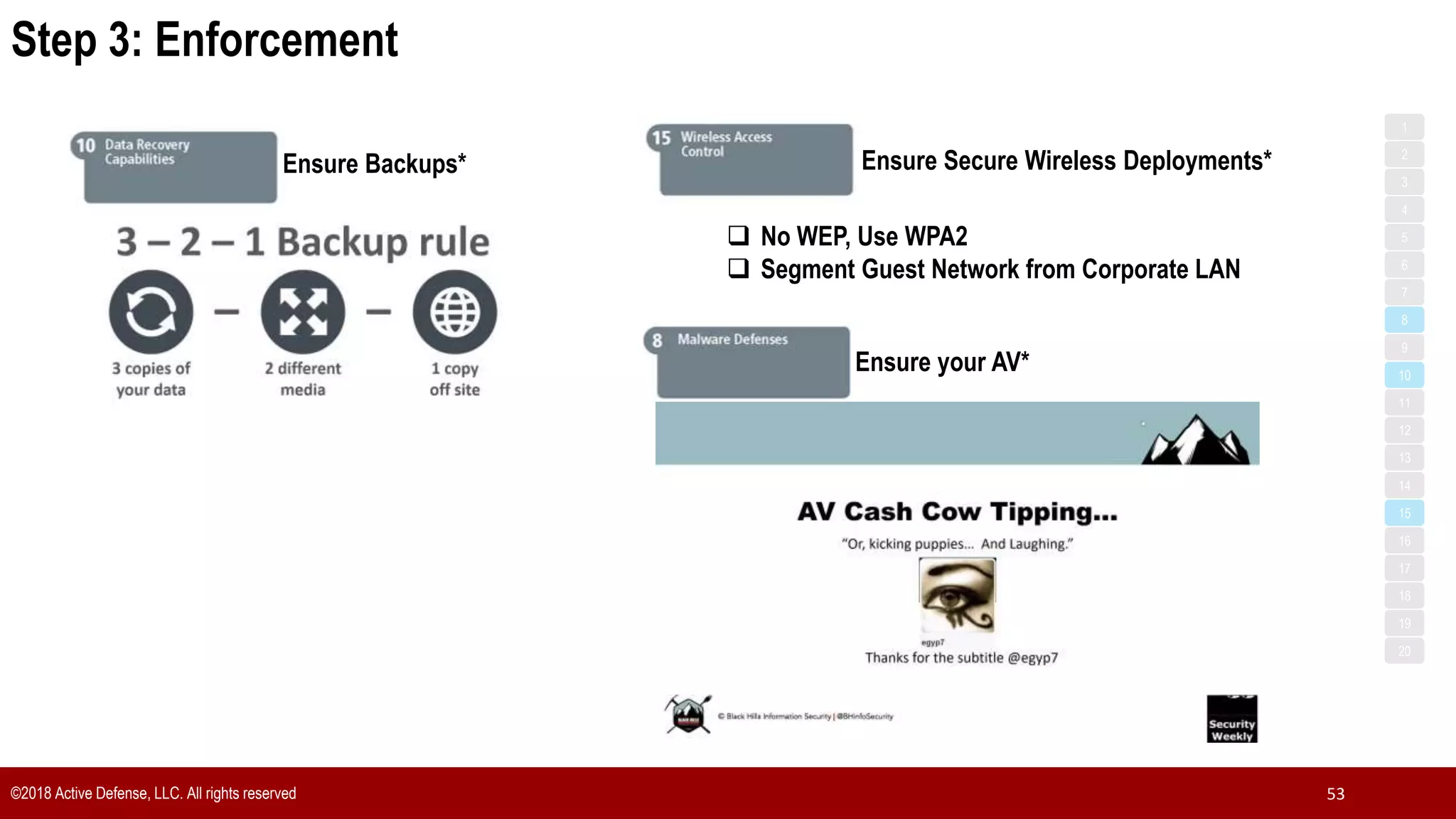
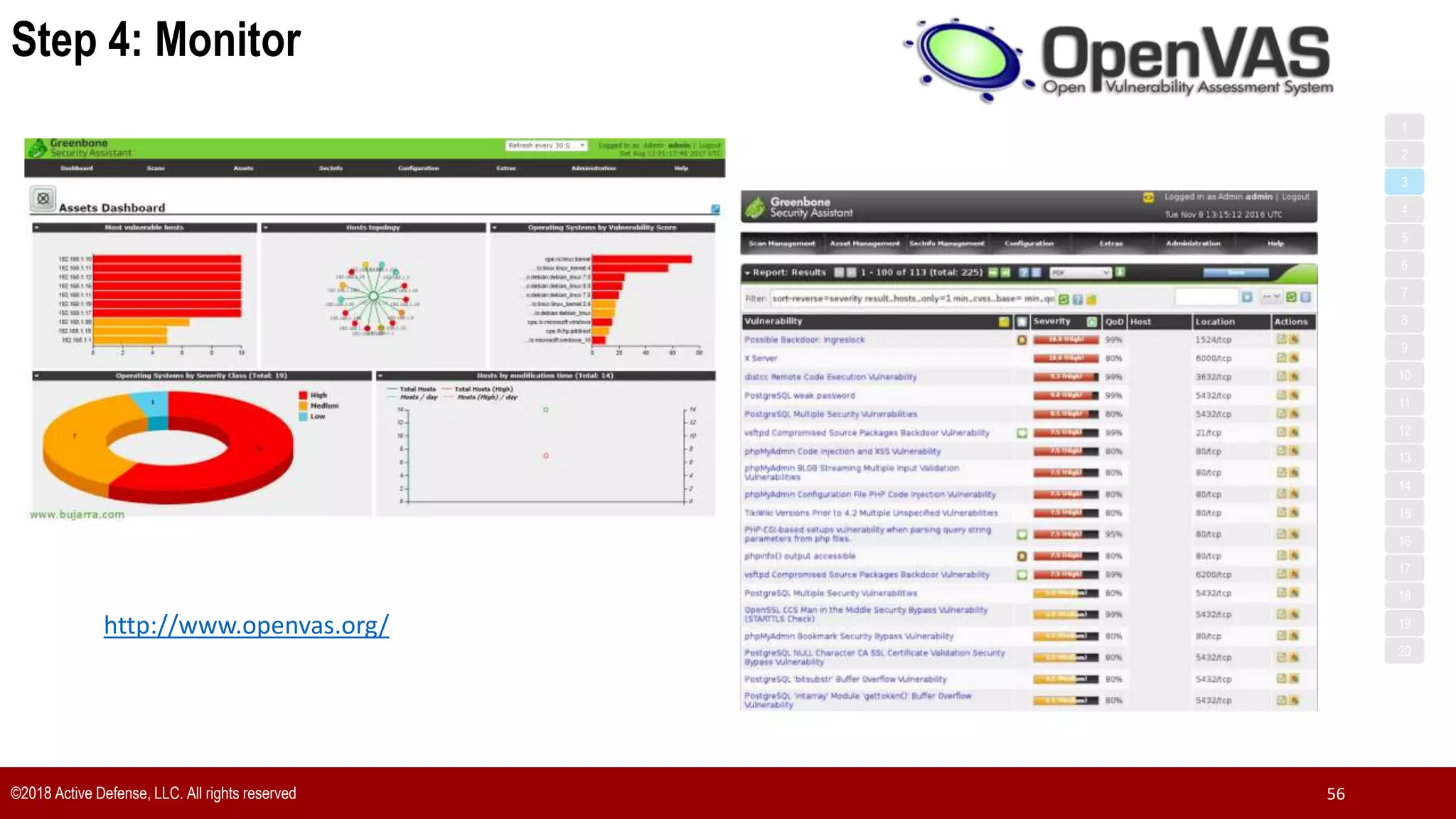
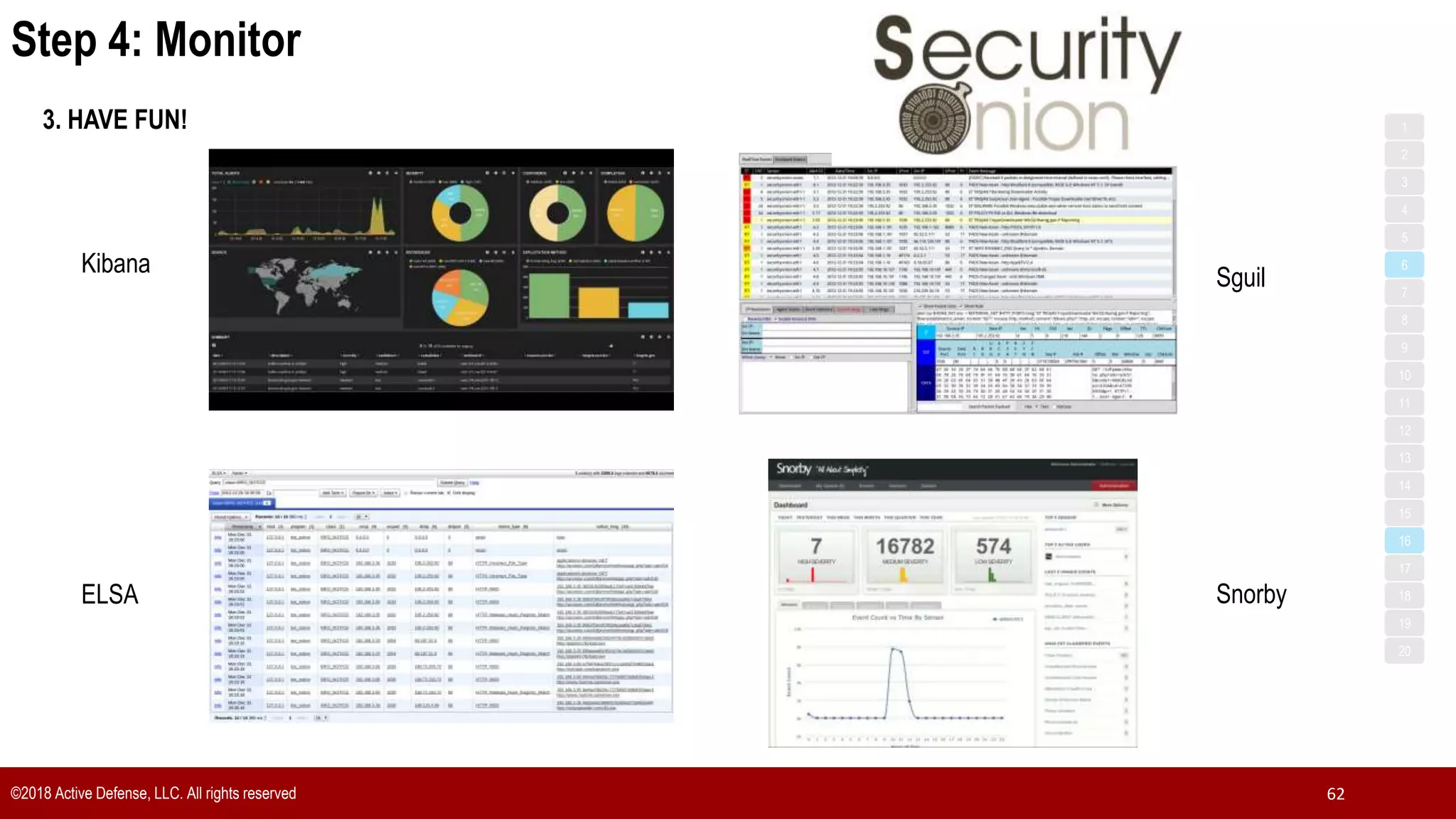
The document discusses the implementation of the CIS Top 20 cybersecurity controls with limited resources, outlining a step-by-step approach starting from device discovery to enforcement. It emphasizes the importance of risk management and investment in cybersecurity tools while providing practical examples and strategies for improving security posture. Key steps include discovering network devices, defining policies for privileged accounts, and enforcing security measures like firewalls and data encryption.