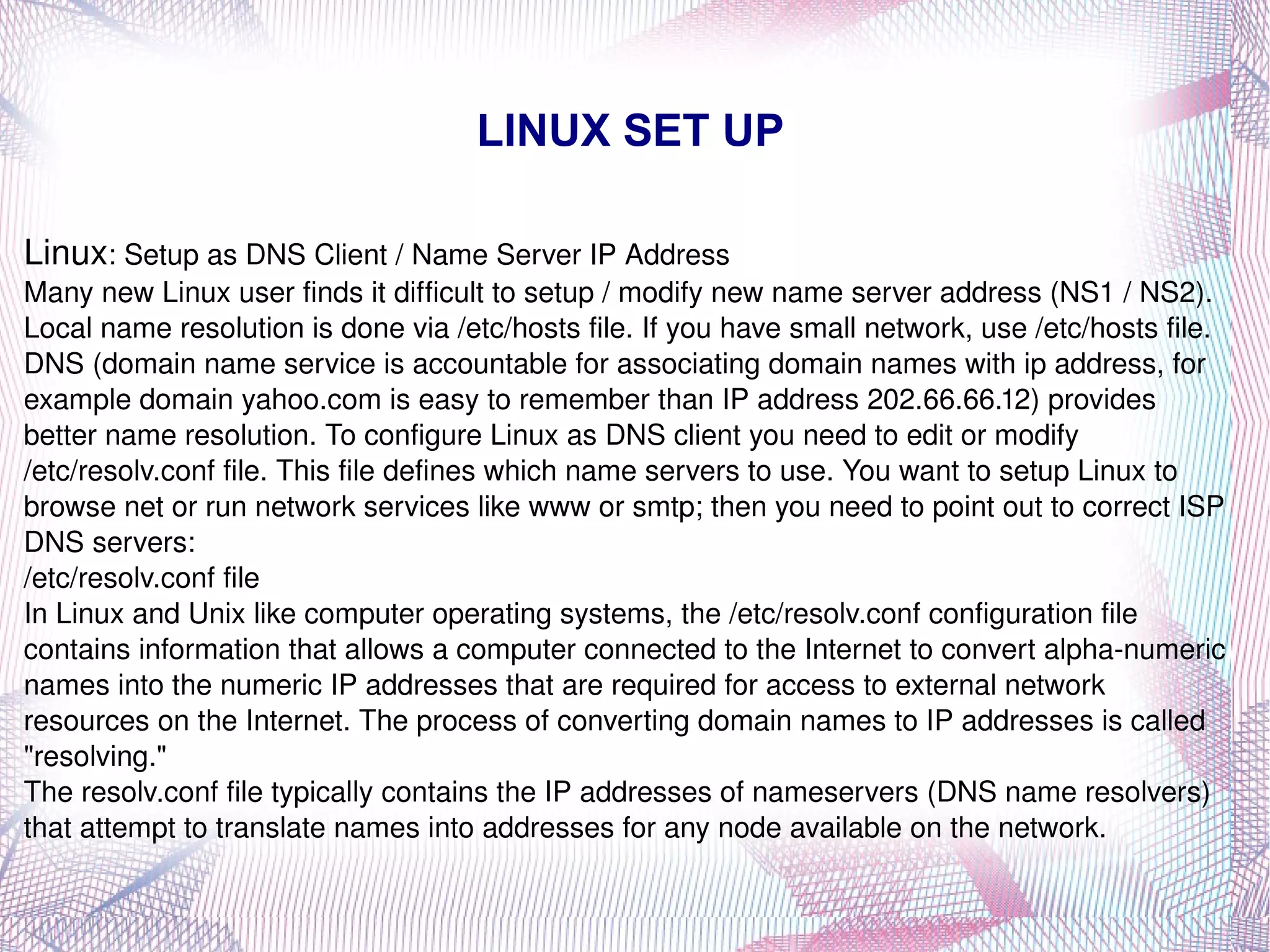
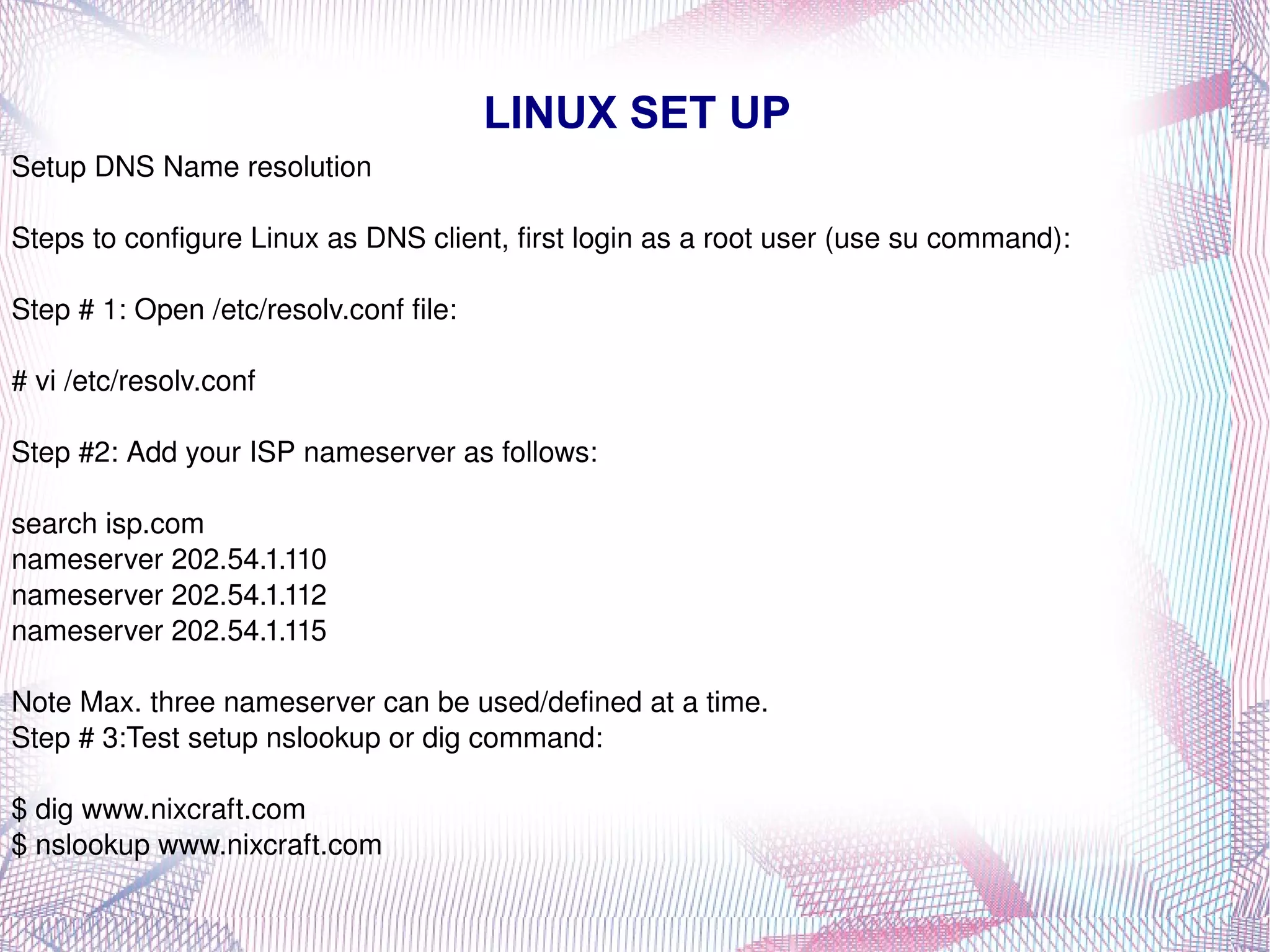
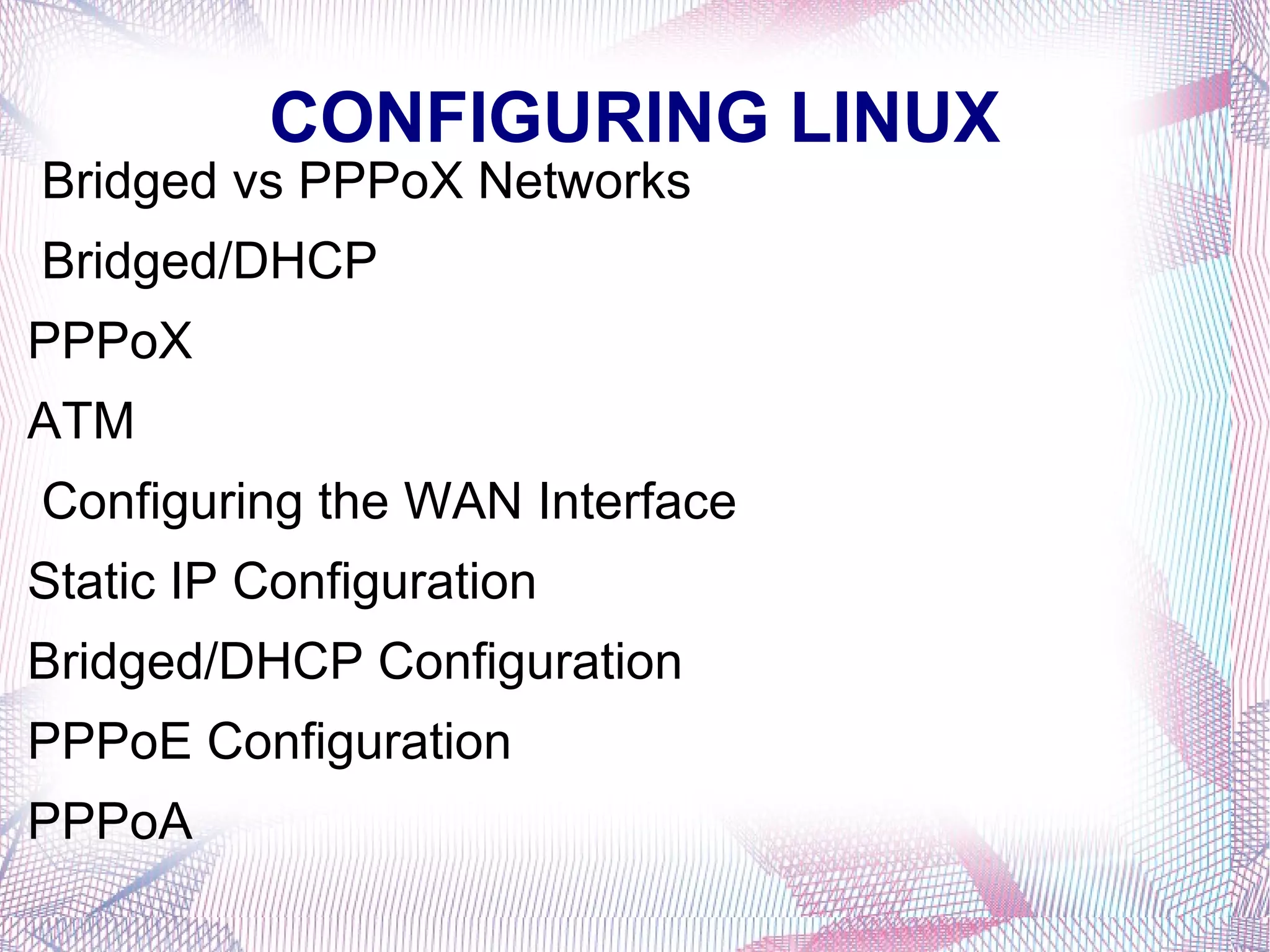
This document provides instructions on installing Linux, including collecting hardware information beforehand, preparing disk partitions, booting from CD-ROM, continuing the installation process by preparing filesystems and installing packages, and basic parts of an installation kit like README files, boot disk images, and the installation CD-ROM. It also covers uninstalling or removing software packages using either the graphical Synaptic tool or command line apt-get commands. Basic Linux commands like mkdir, cd, pwd, rmdir, chown, chmod, ls, and cp are described.