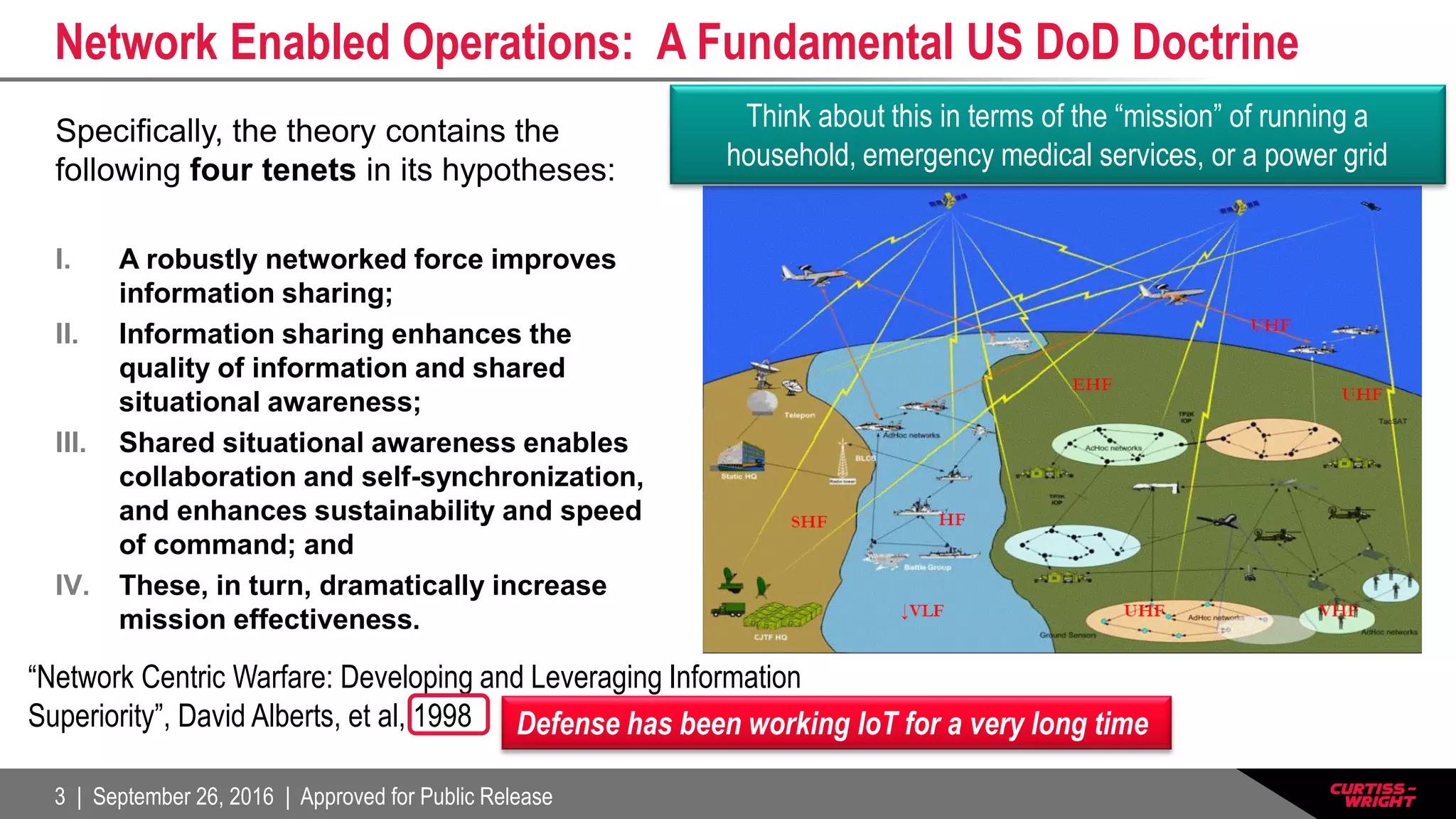
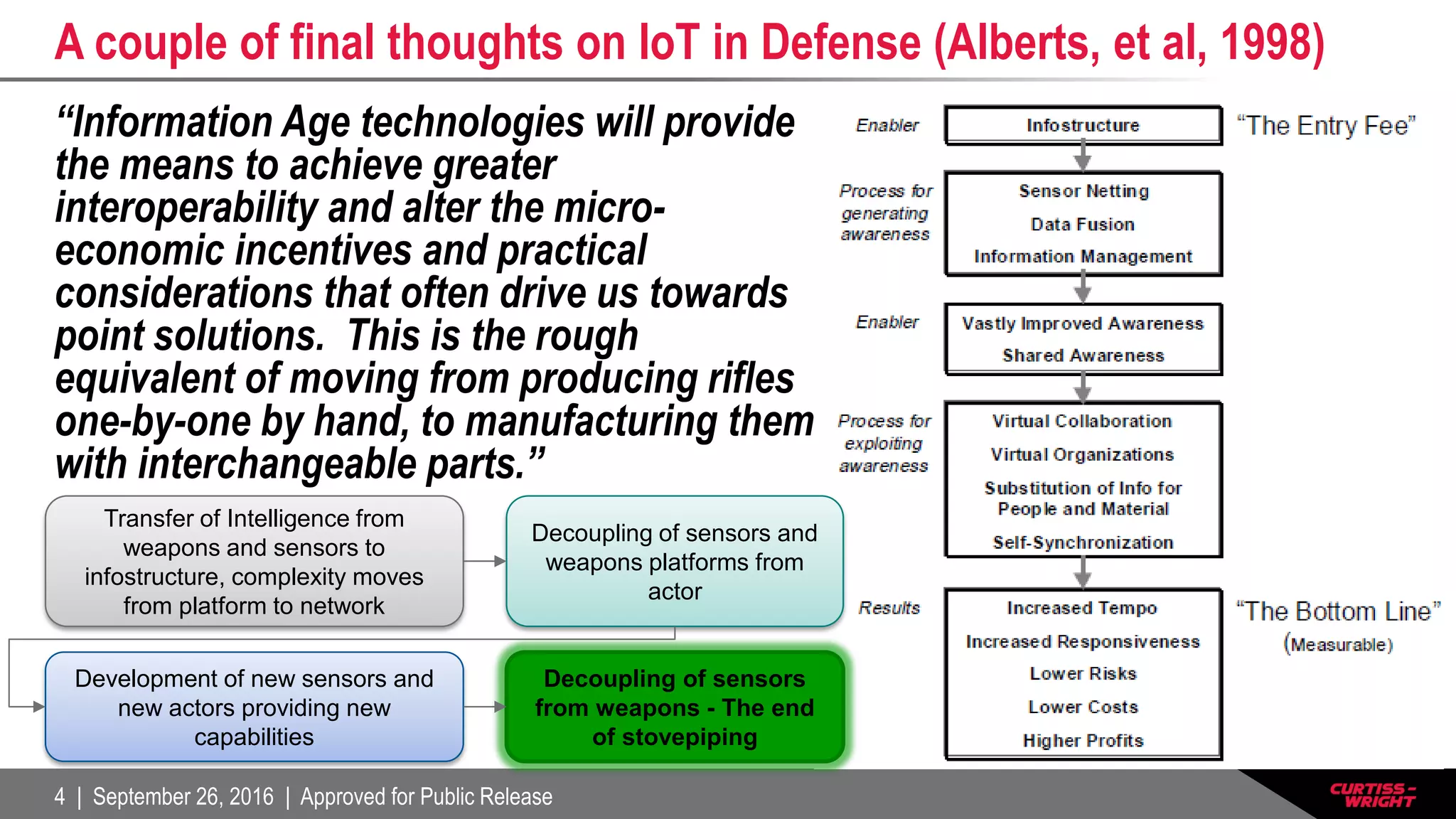
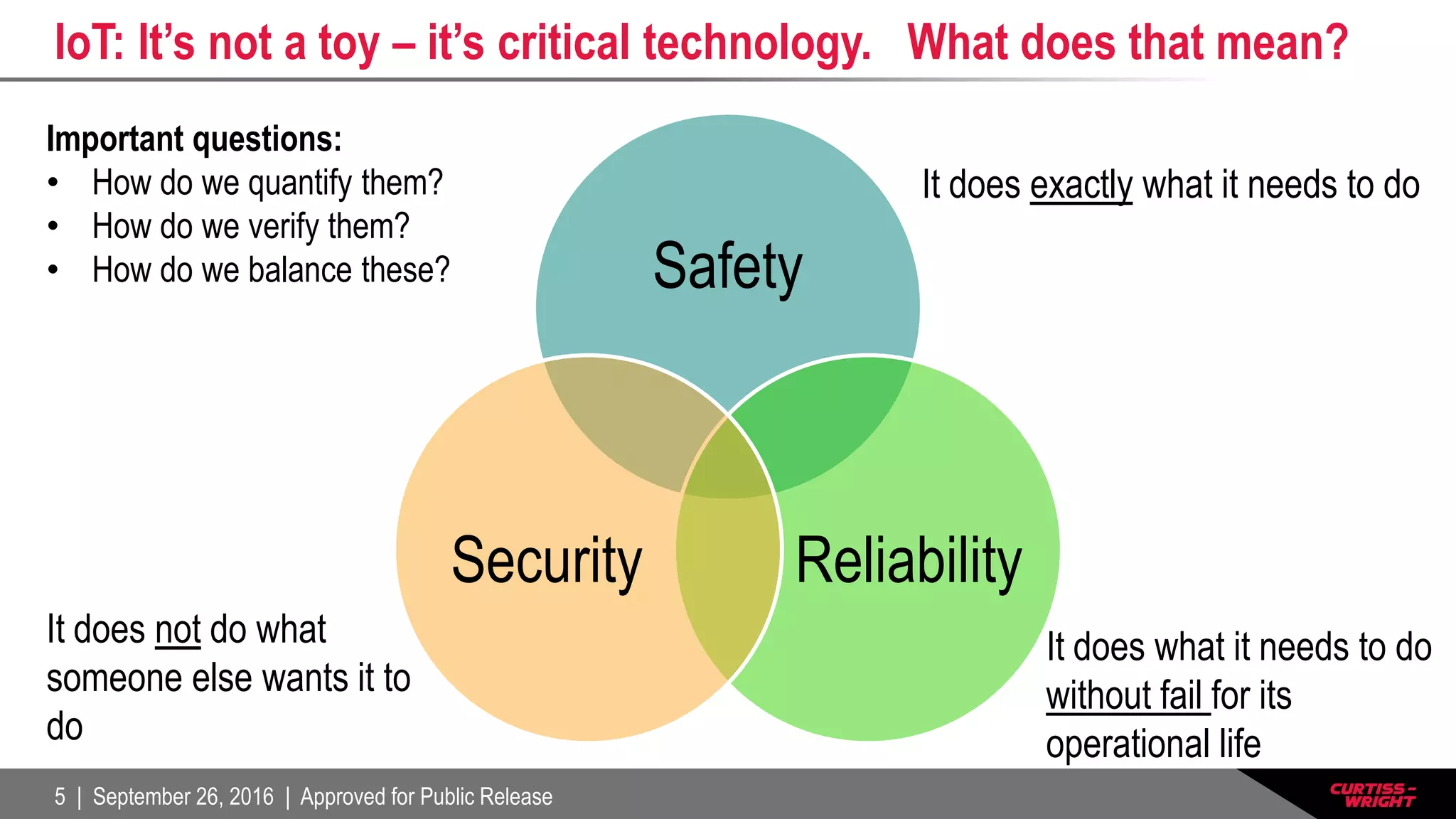
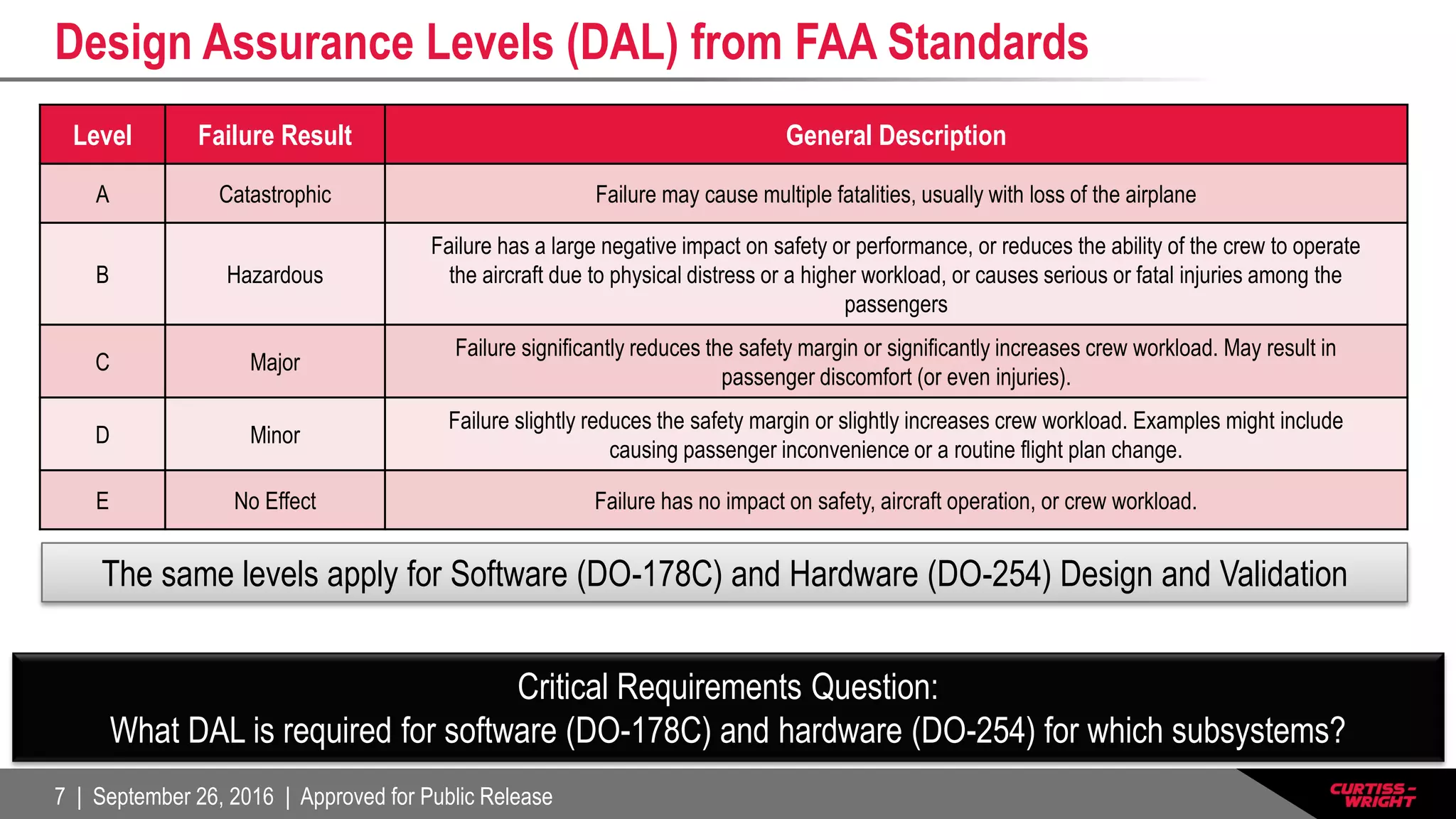
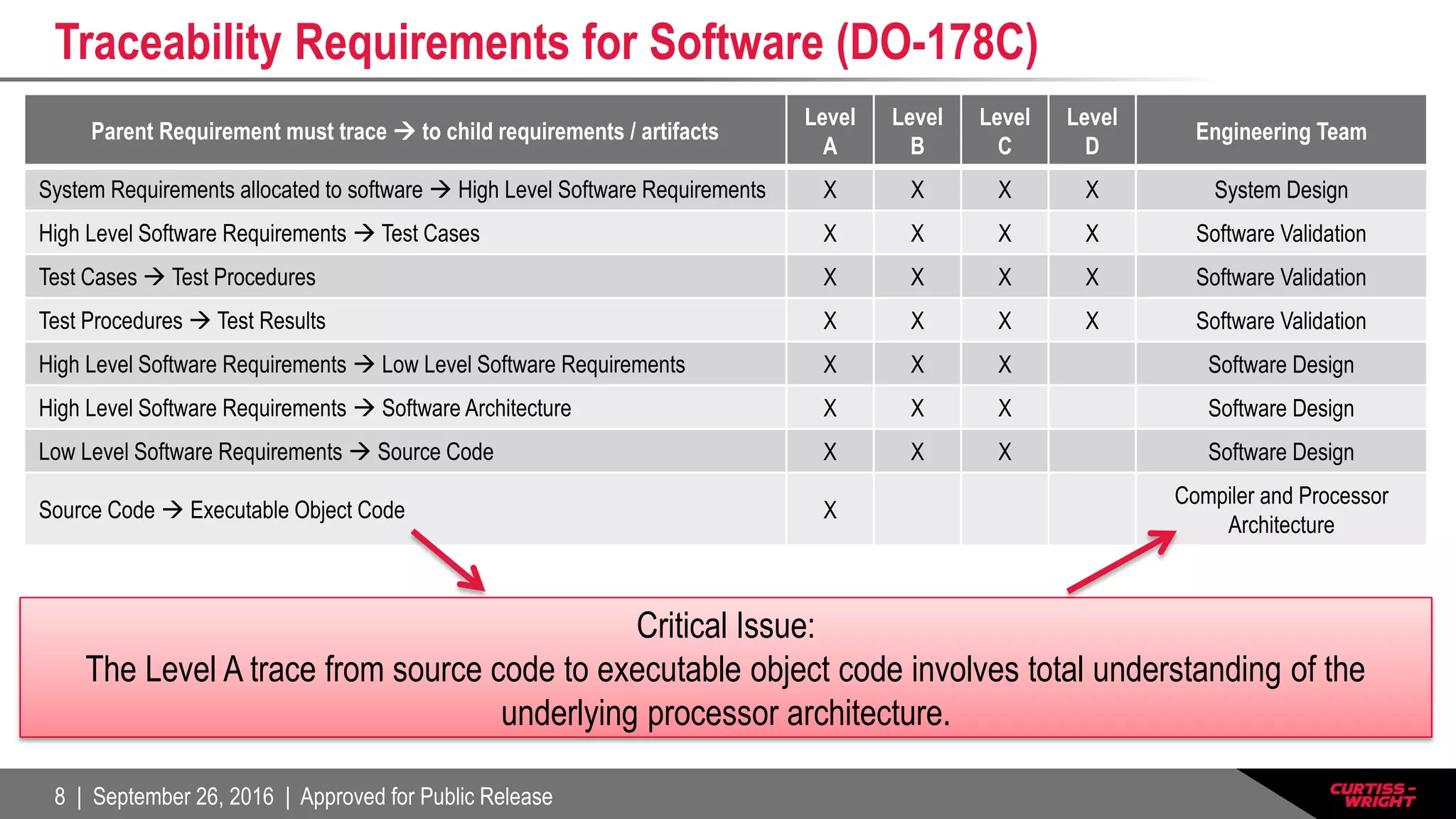
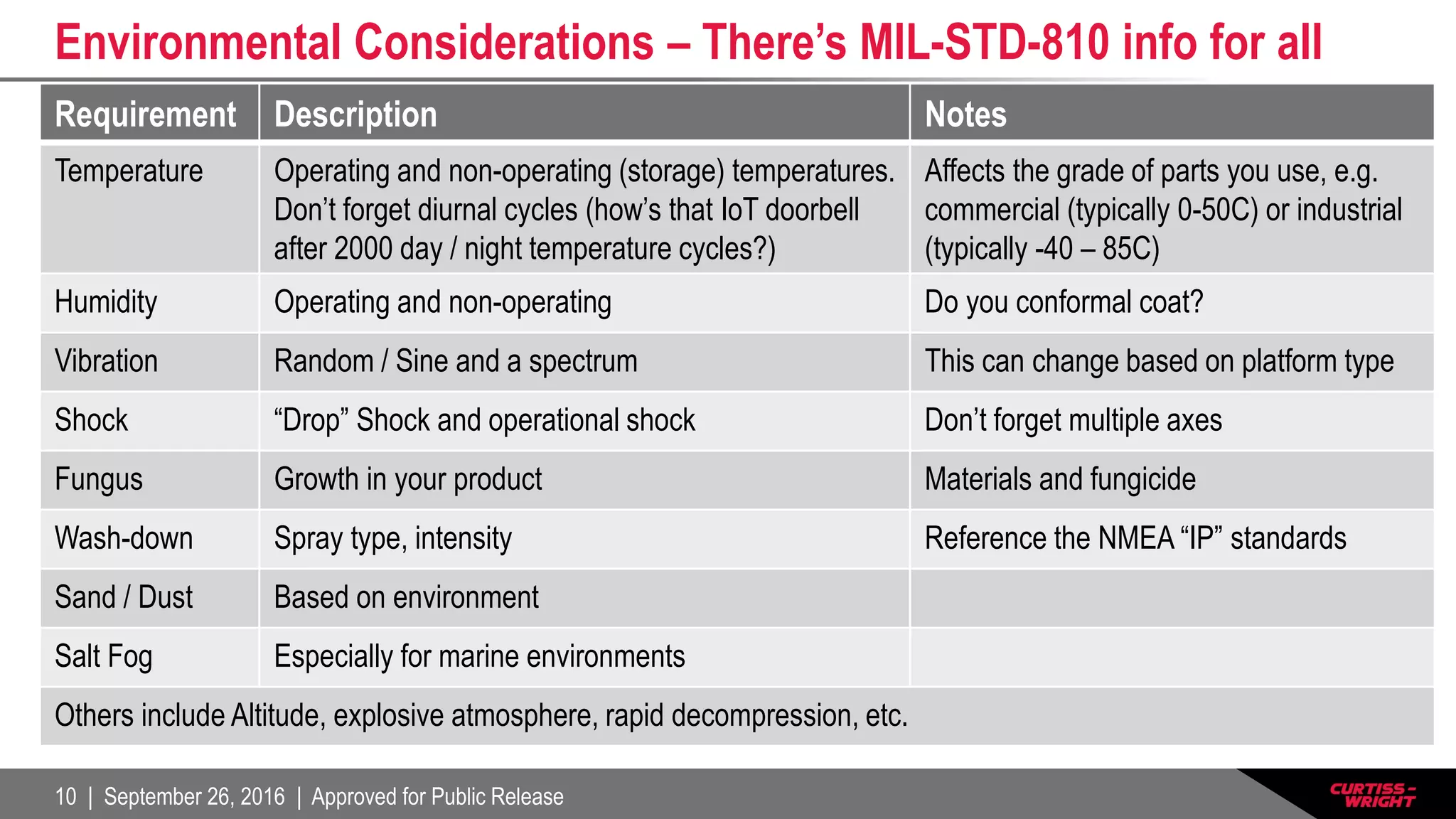
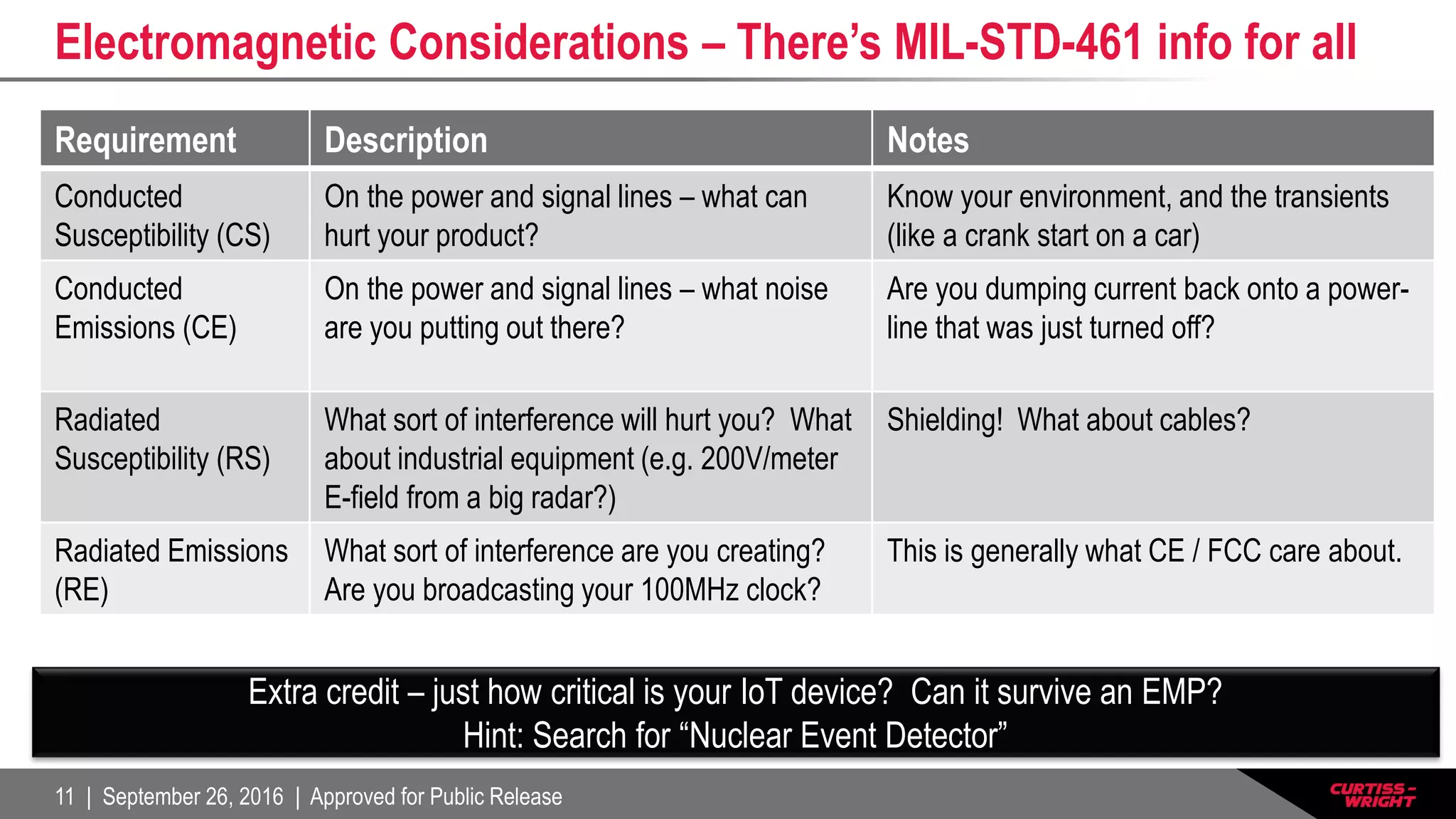
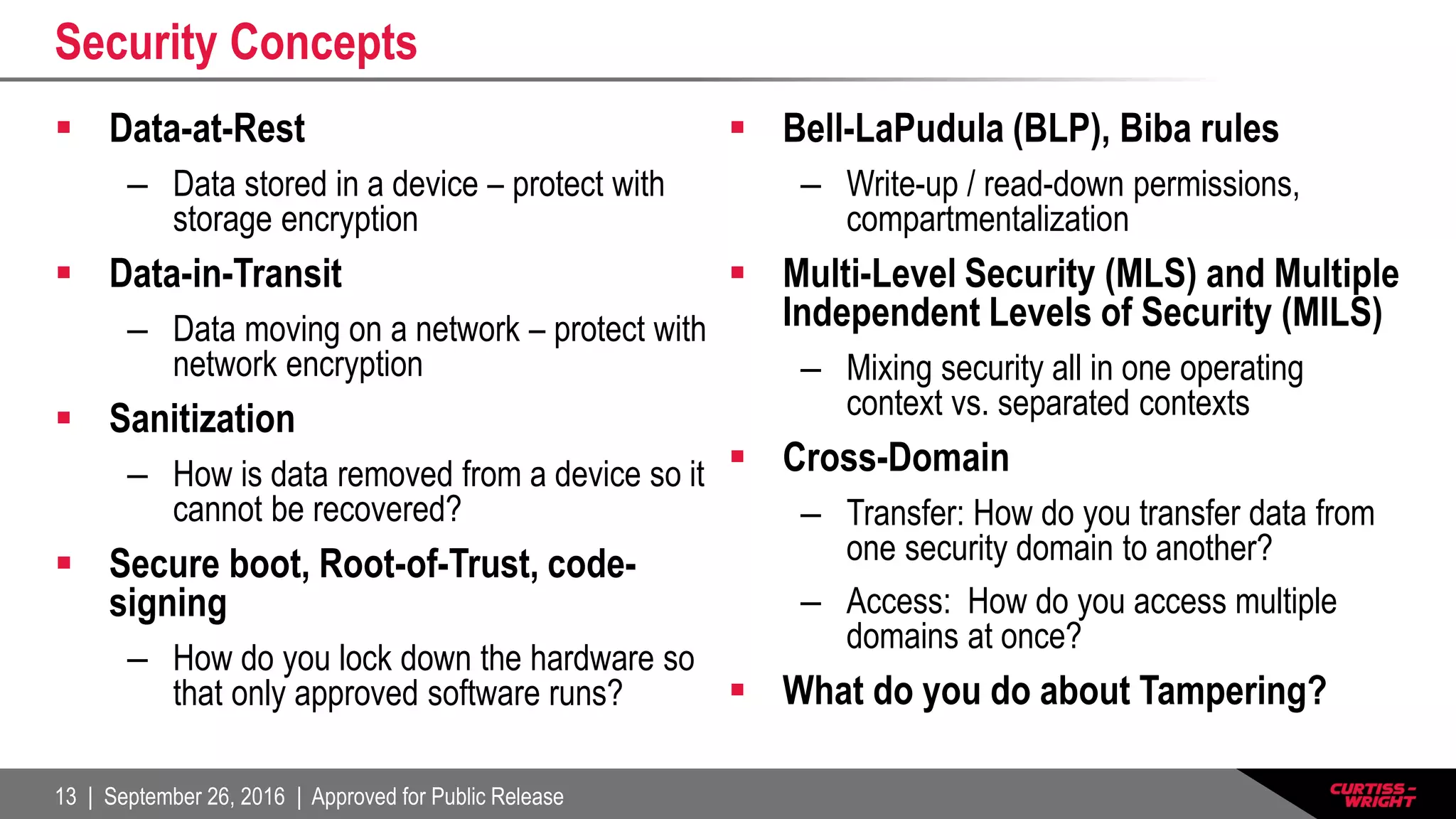
The document discusses the integration of the Internet of Things (IoT) within defense systems, emphasizing the importance of network-enabled operations to enhance mission effectiveness. It covers critical aspects of safety, reliability, and security for these technologies, referring to standards and requirements such as FAA guidelines and various testing protocols. Key themes include the necessity for robust security measures and addressing environmental challenges to ensure the dependable performance of IoT devices in defense scenarios.