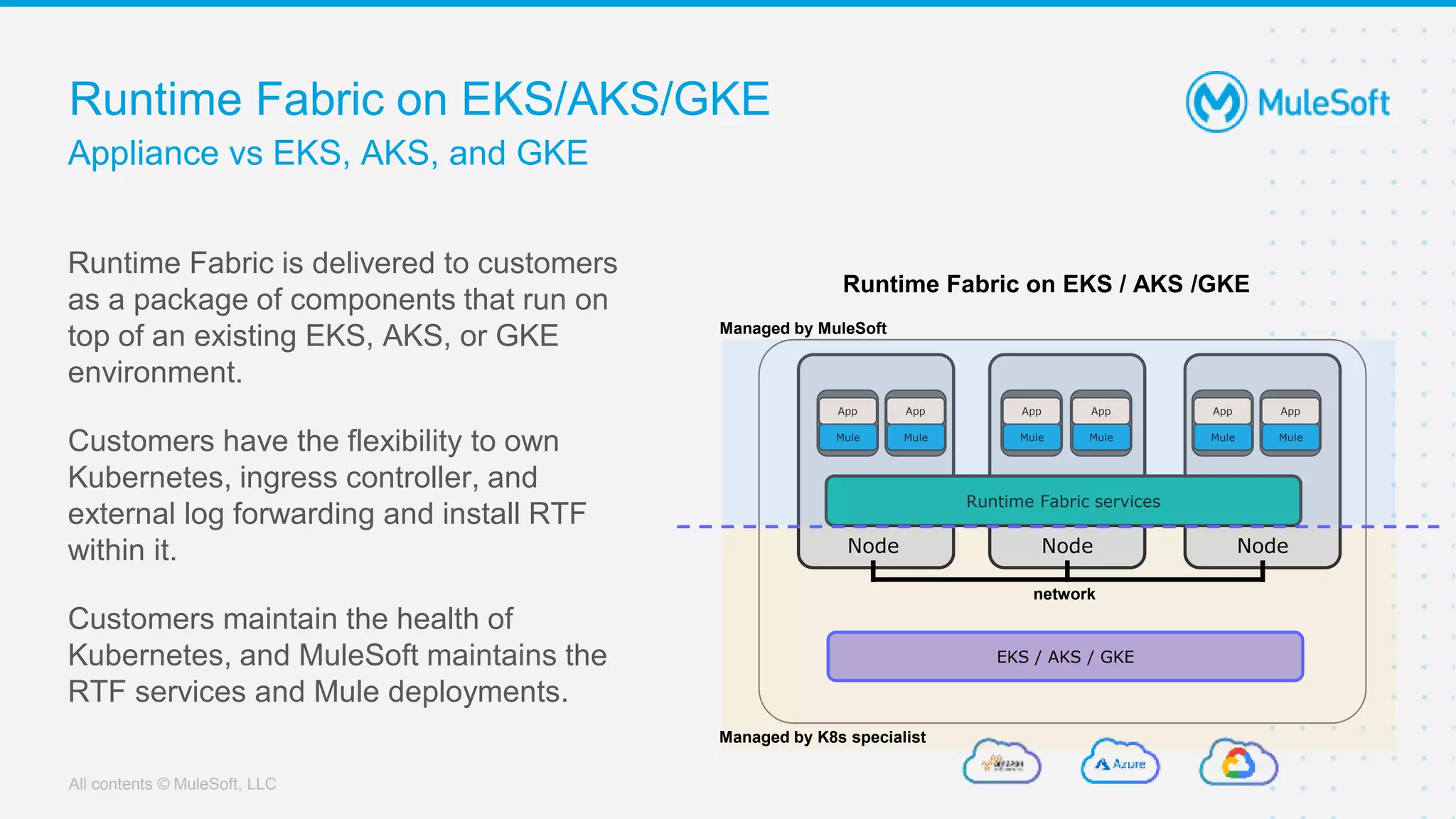
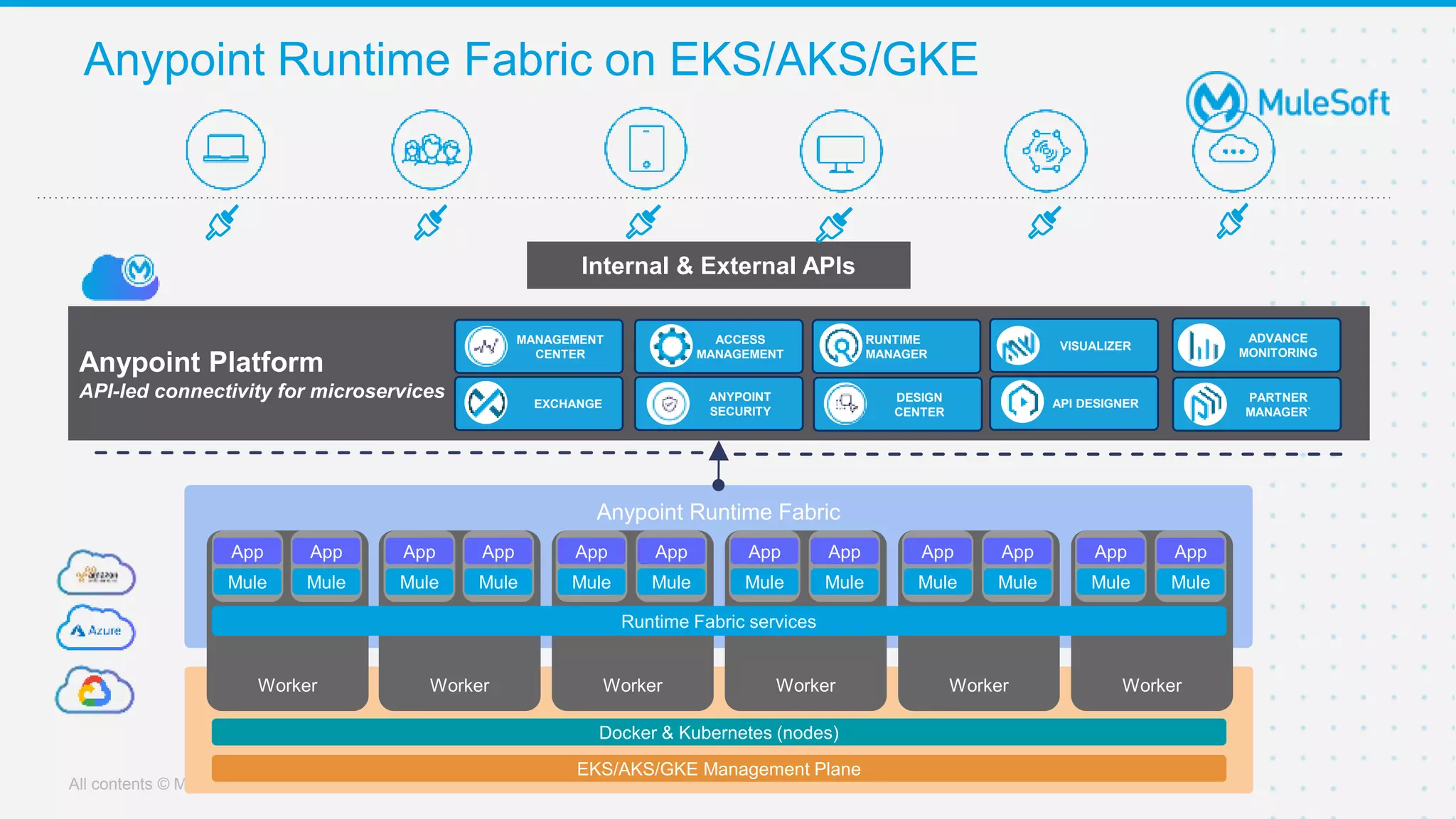
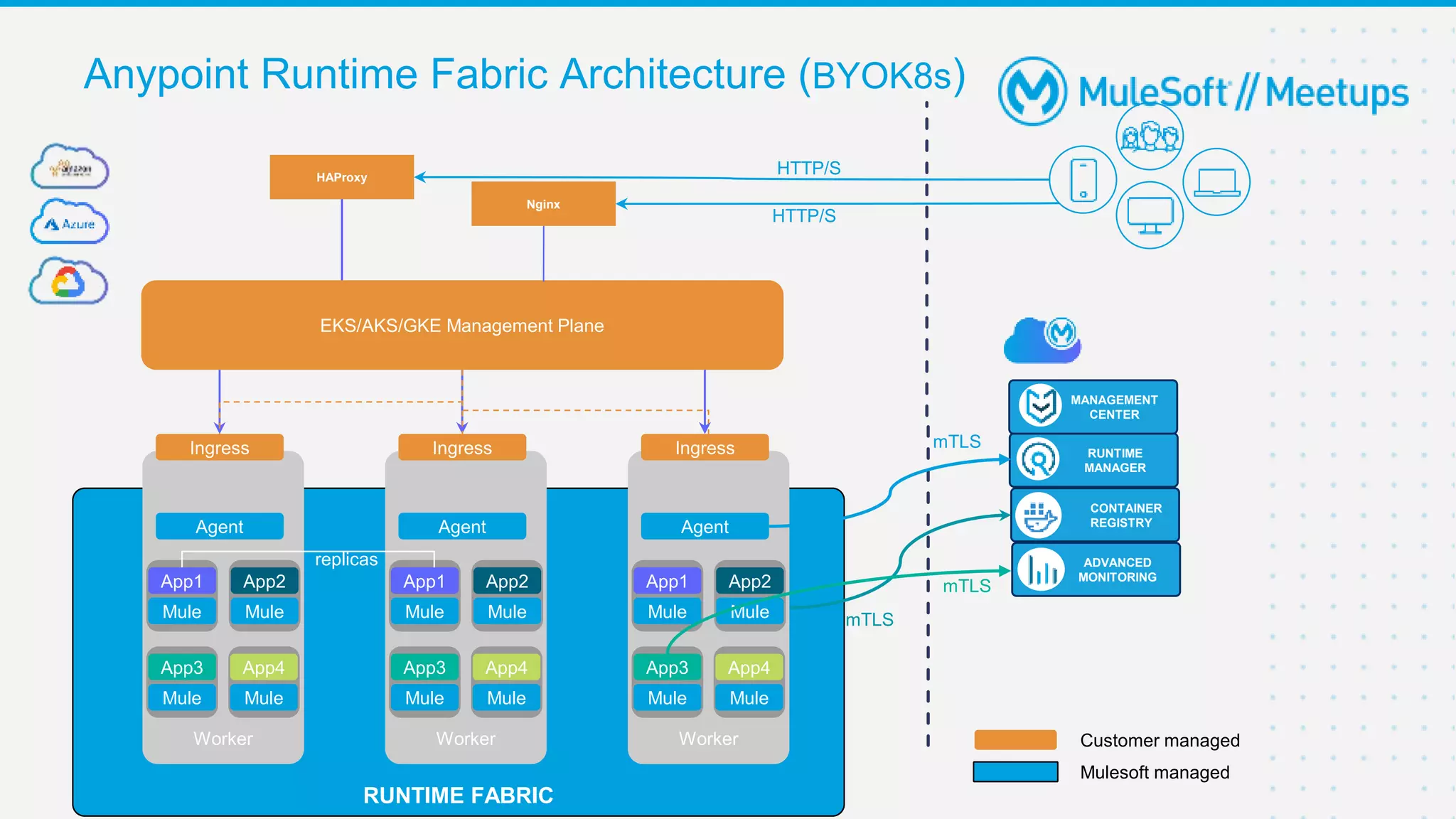
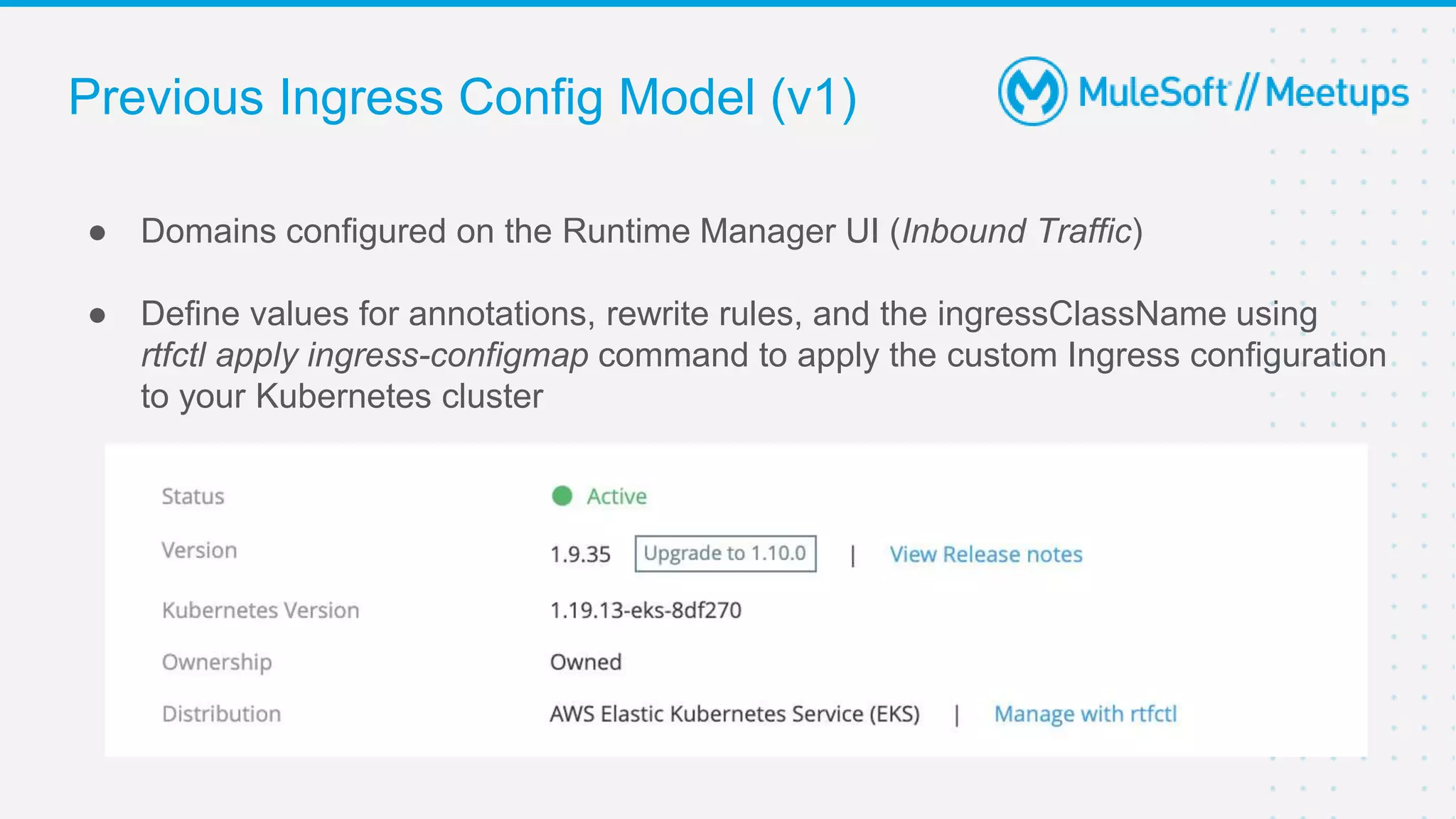
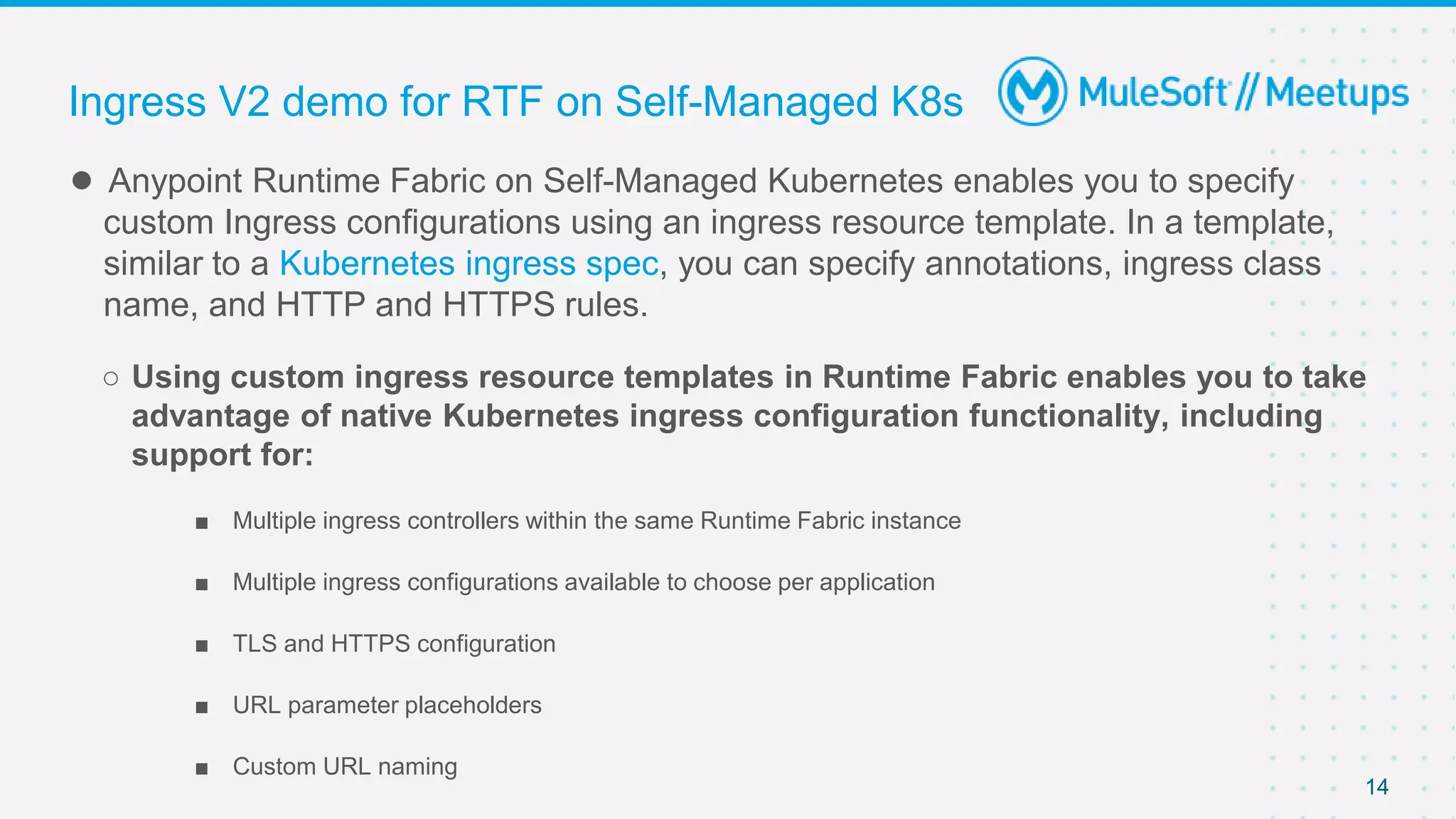
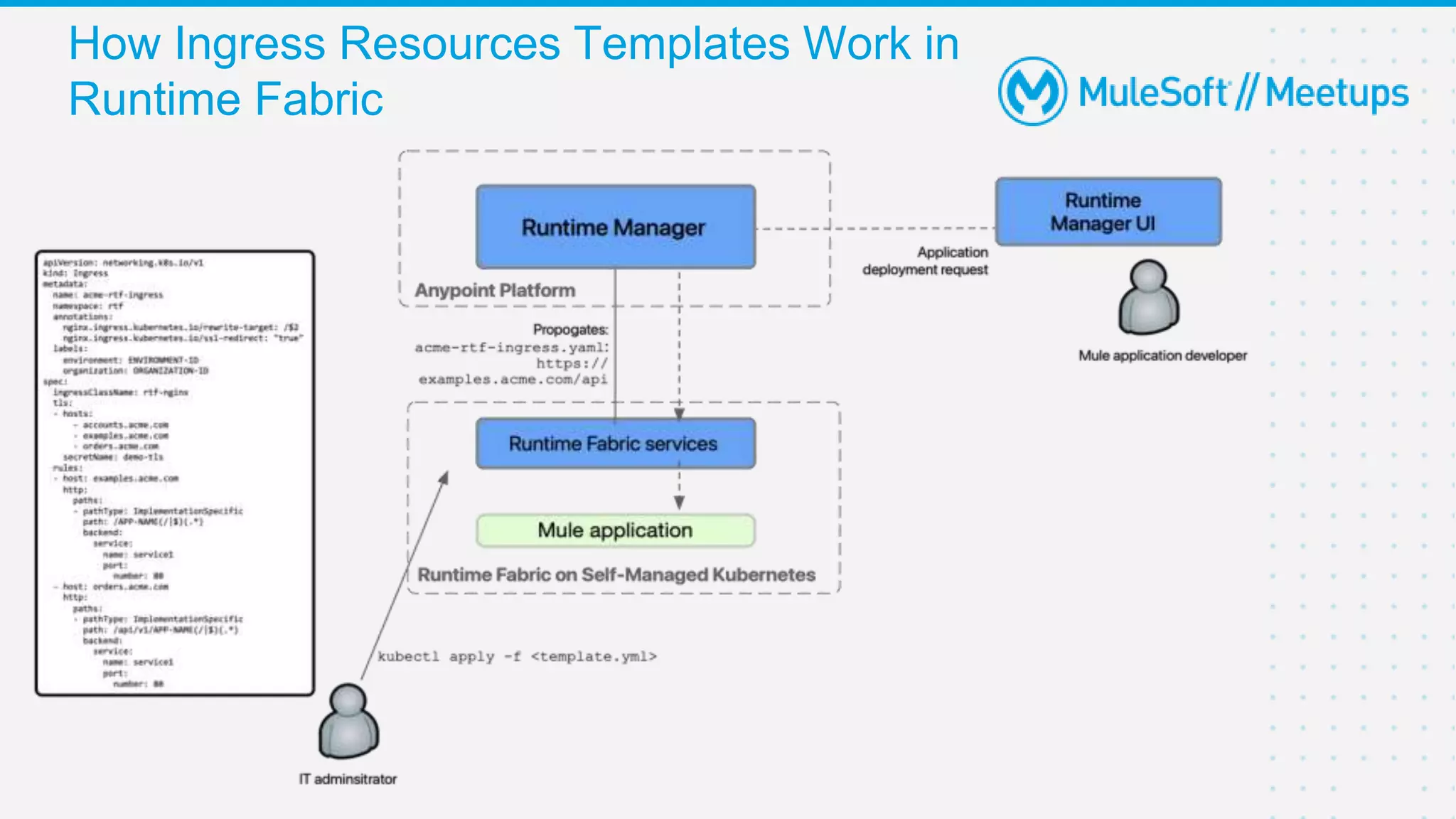
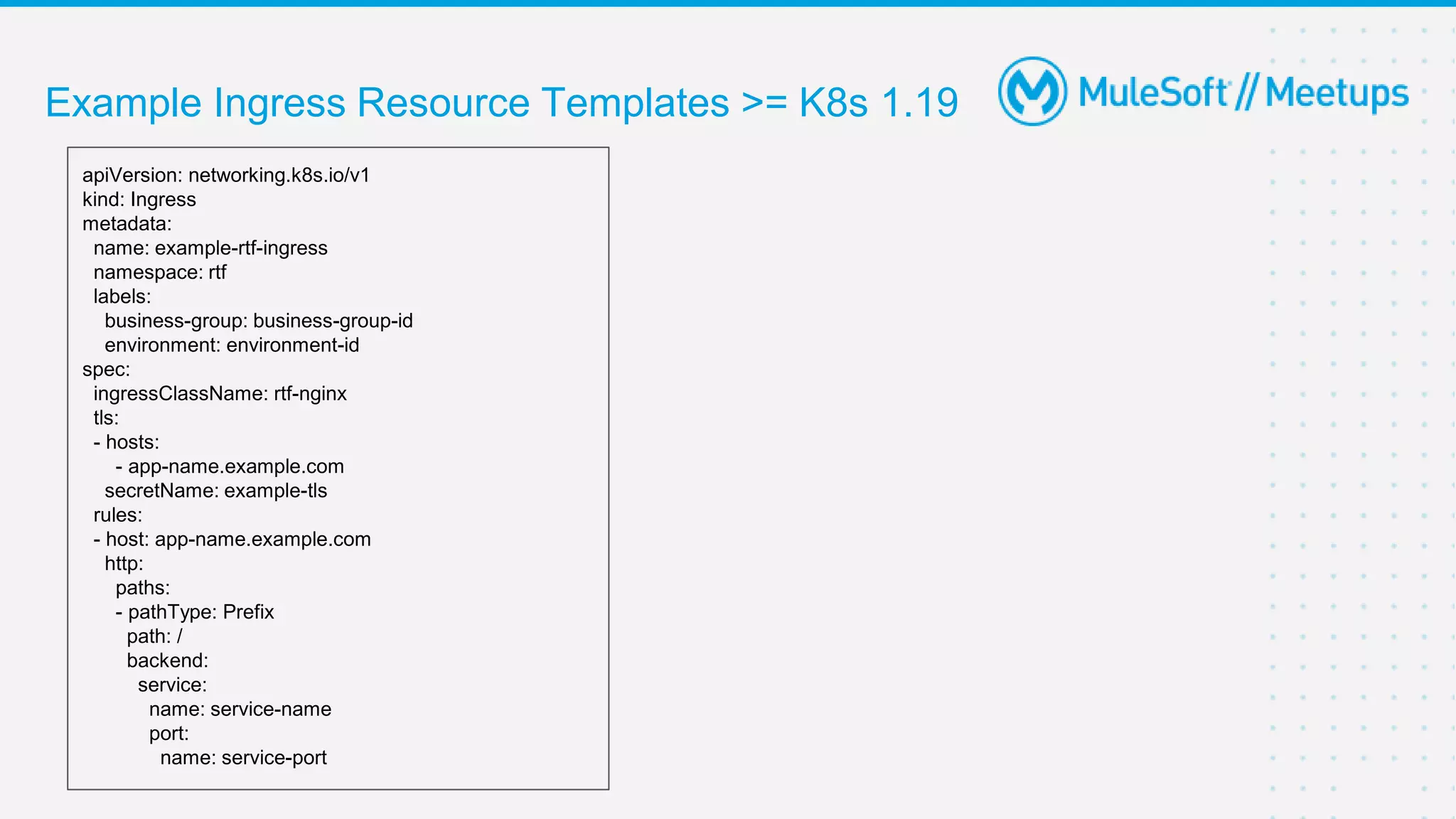
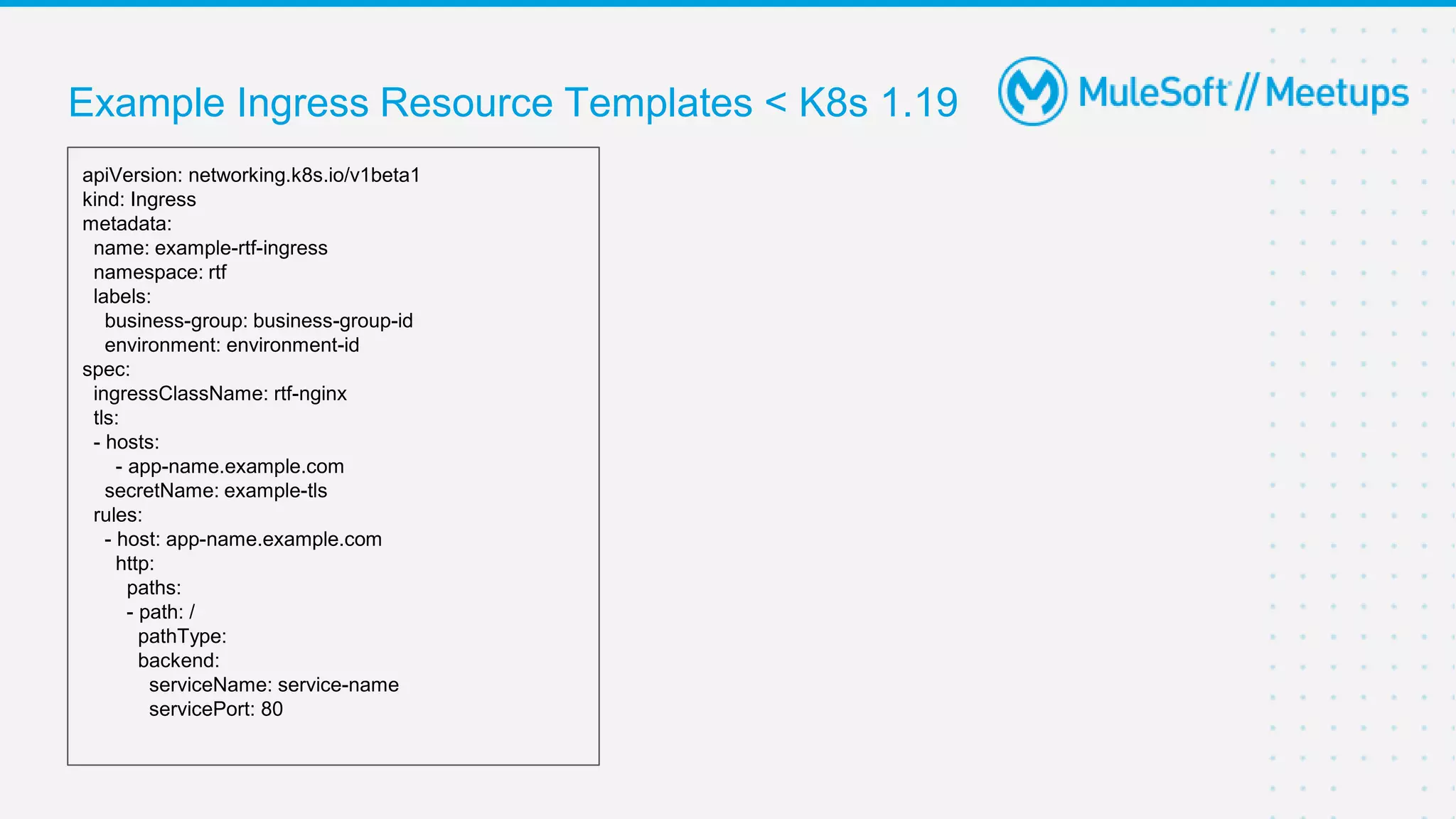
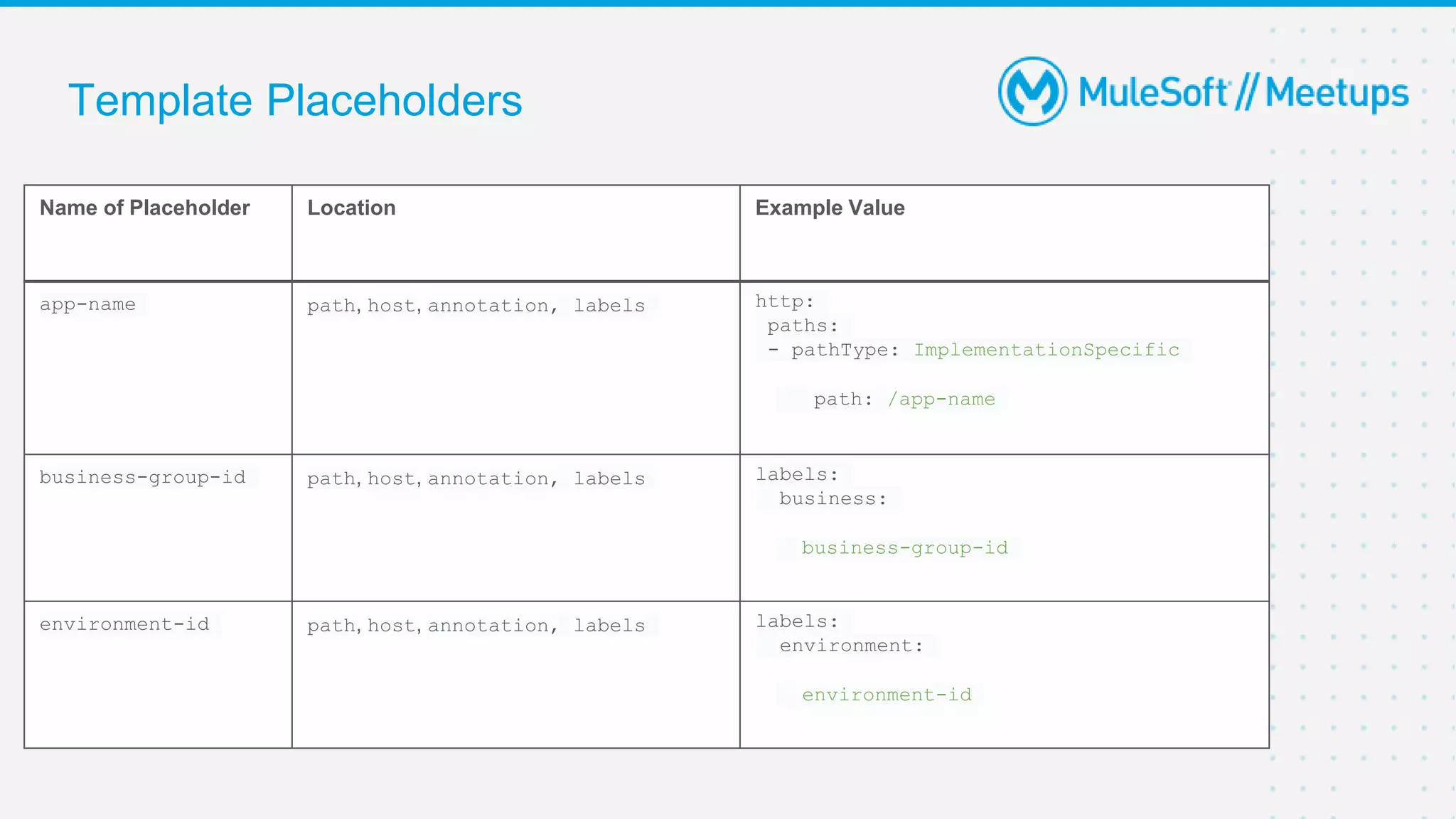
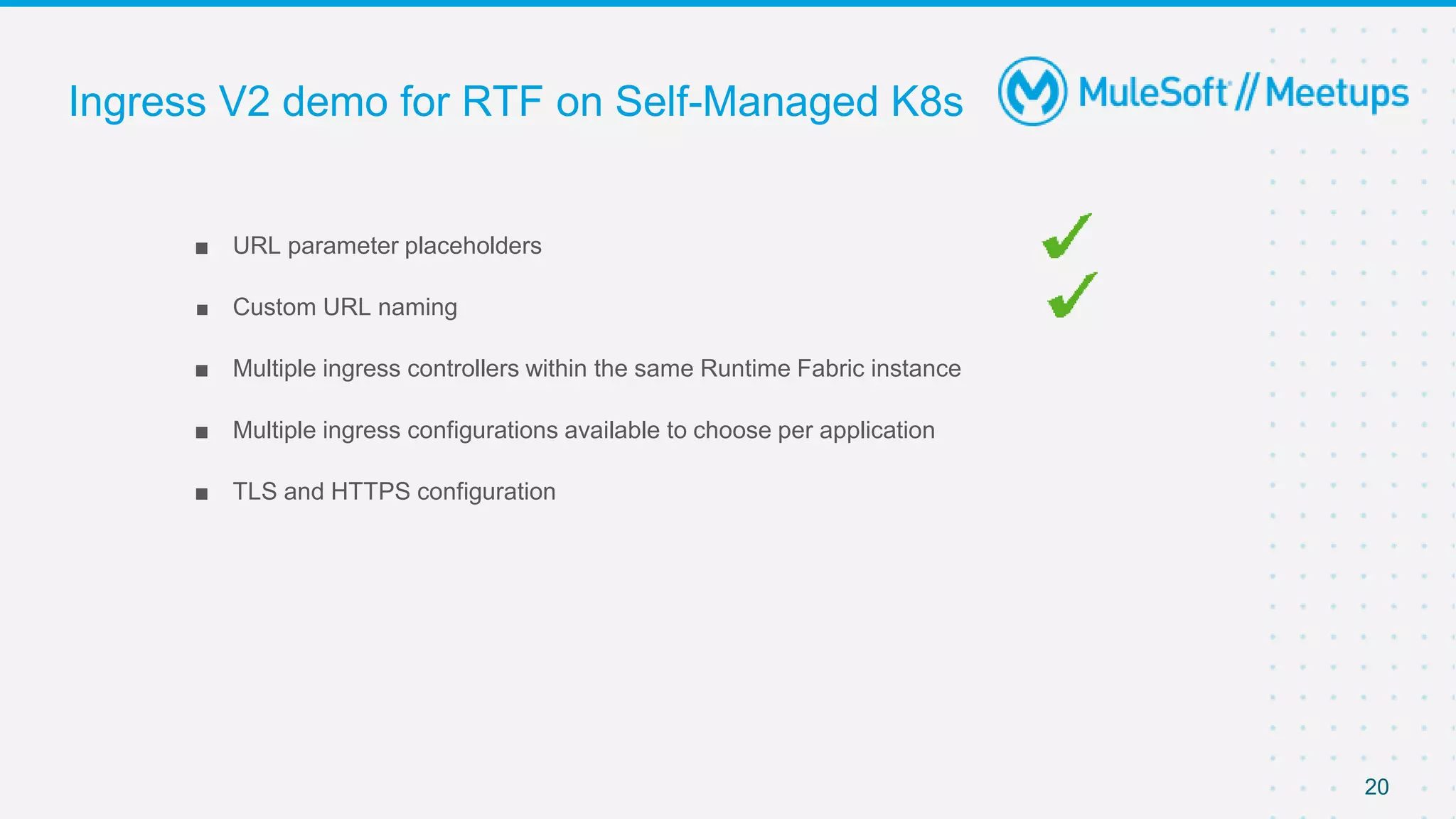
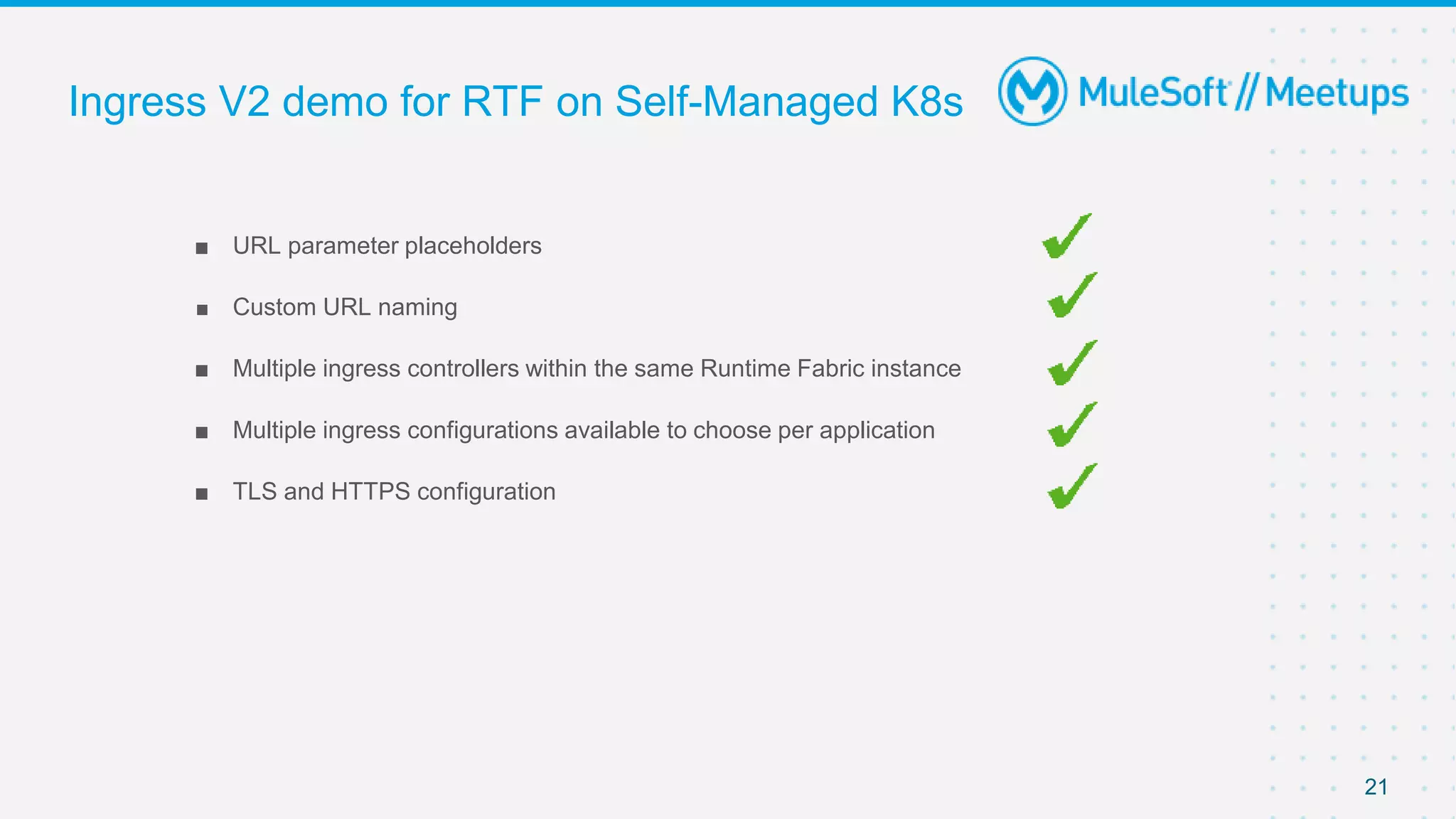
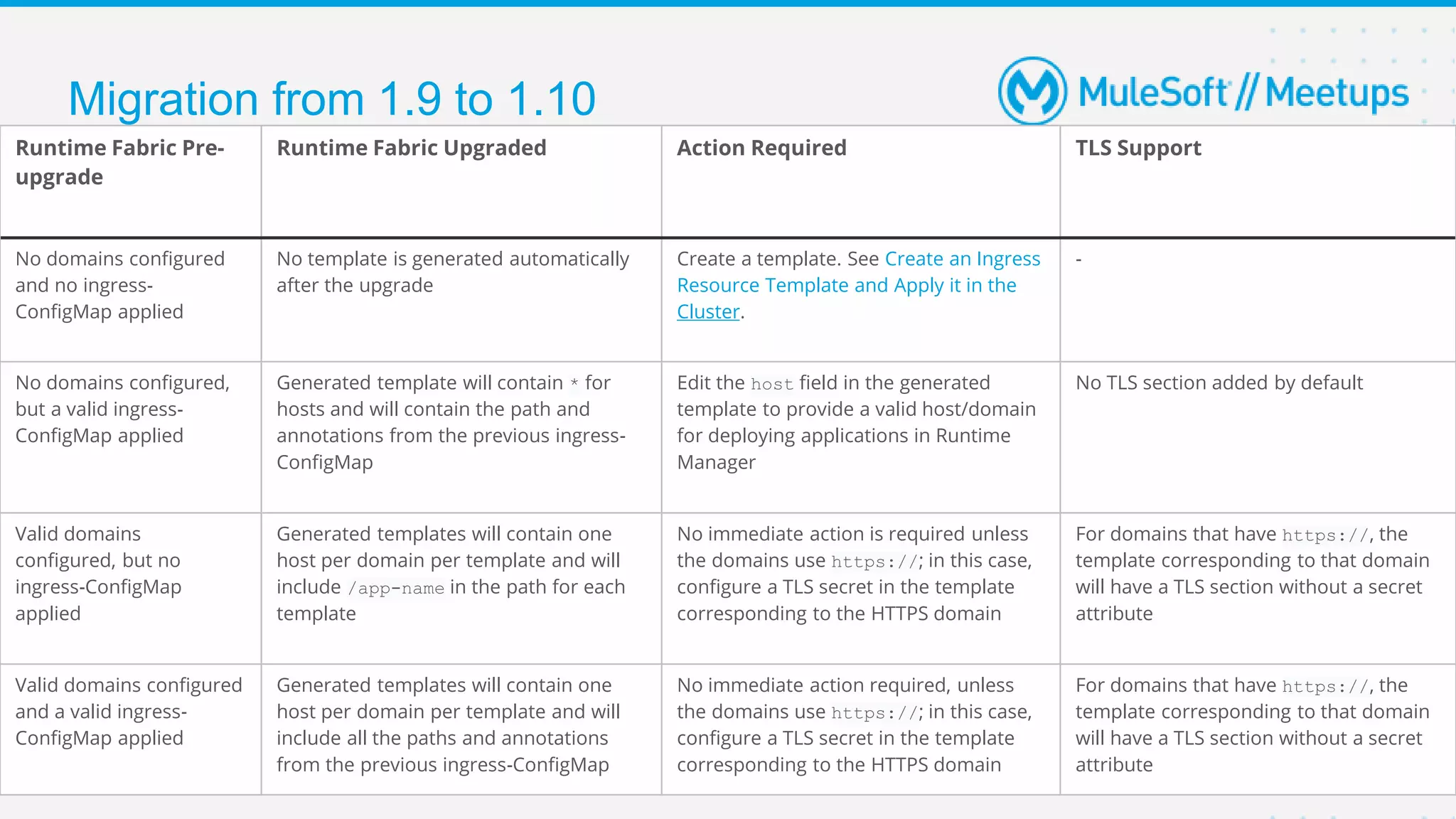
This document provides an overview and agenda for an online meetup discussing Ingress V2 for Runtime Fabric on self-managed Kubernetes. The agenda includes guidelines for the meetup, a walkthrough of Ingress V2, a demo, and a question and answer session. Ingress V2 allows for custom ingress configurations using ingress resource templates that define rules like hostnames, paths, backends and TLS settings. It provides benefits over the previous ingress configuration model like supporting multiple ingress controllers and configurations per application.