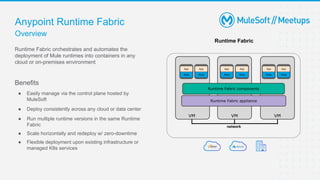
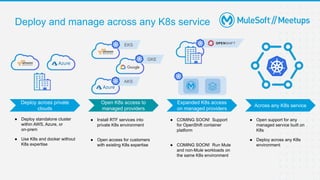
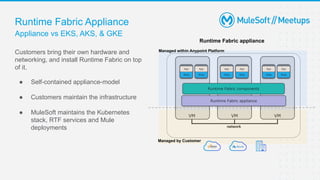
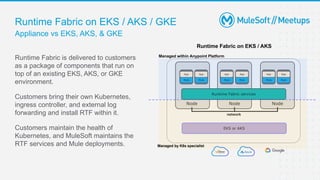
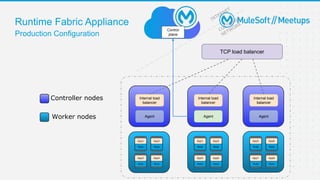
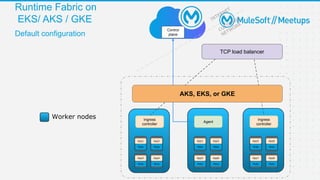
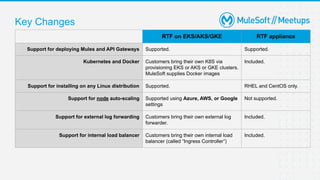
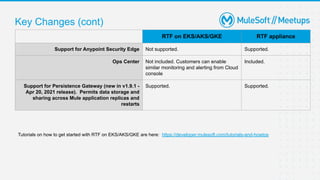
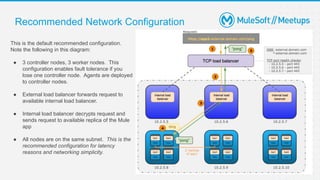
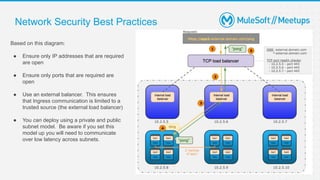
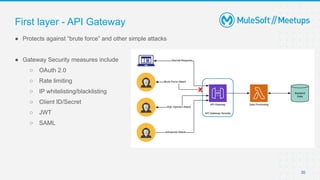
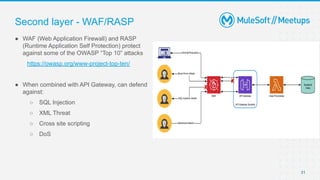
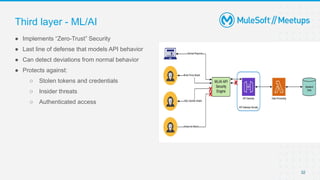
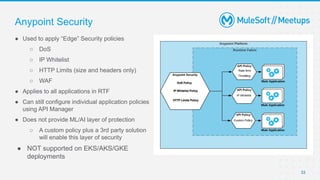
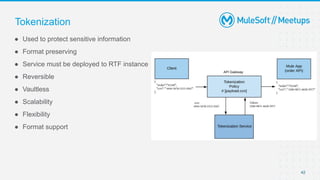
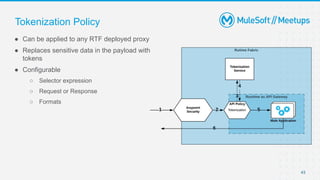
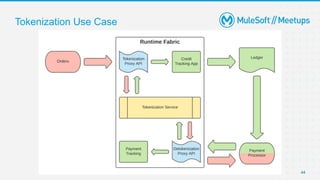
The document outlines the agenda and activities of a virtual Mulesoft meetup focused on Anypoint Runtime Fabric (RTF) security, featuring discussions on security best practices, event rules, and trivia guidelines. It also includes detailed insights into RTF components, deployment strategies, and security measures, emphasizing encryption and tokenization of sensitive information. Furthermore, it covers the implications of security in API management and the technical aspects of configuring secure properties and network setups in RTF environments.