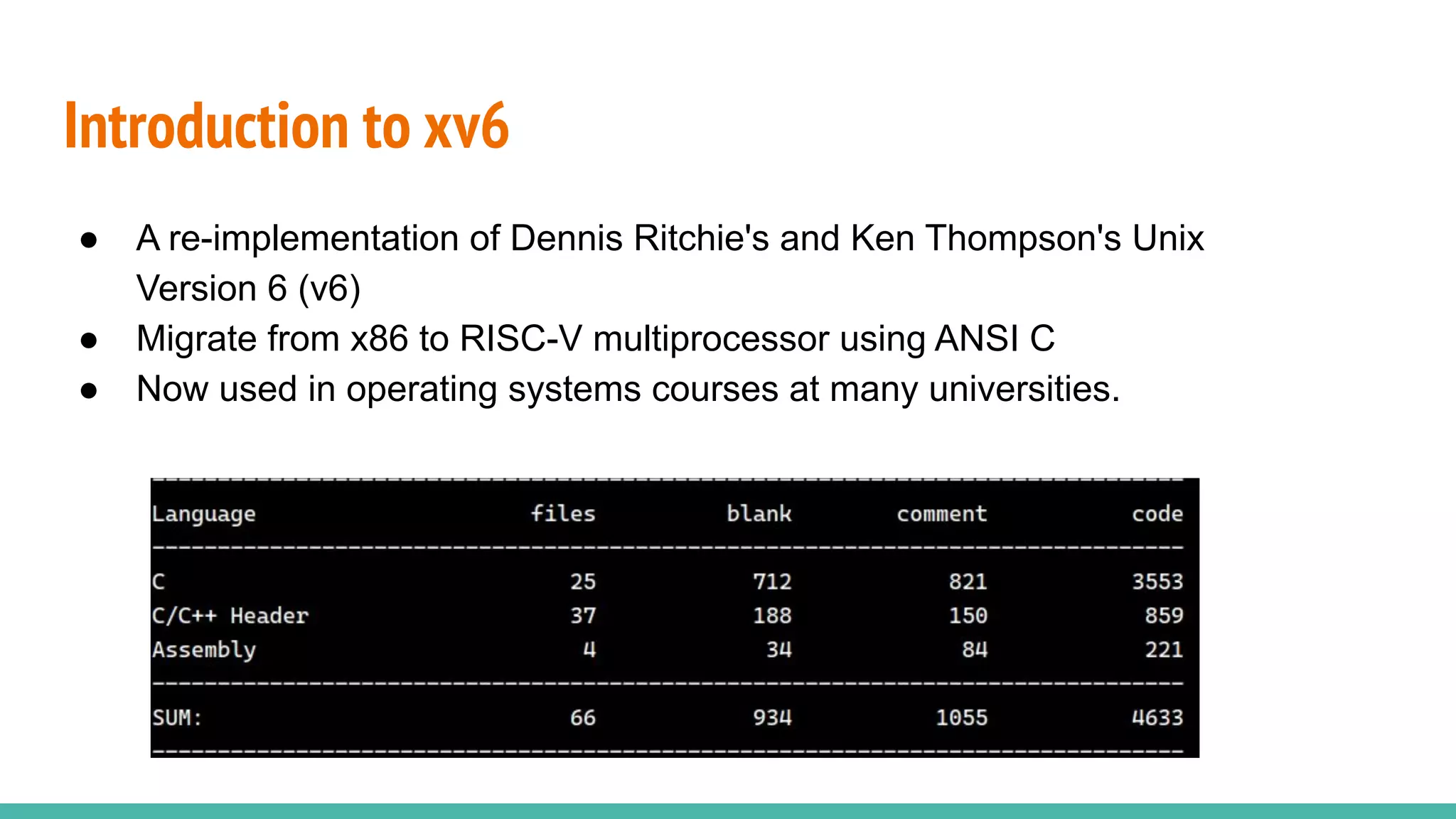
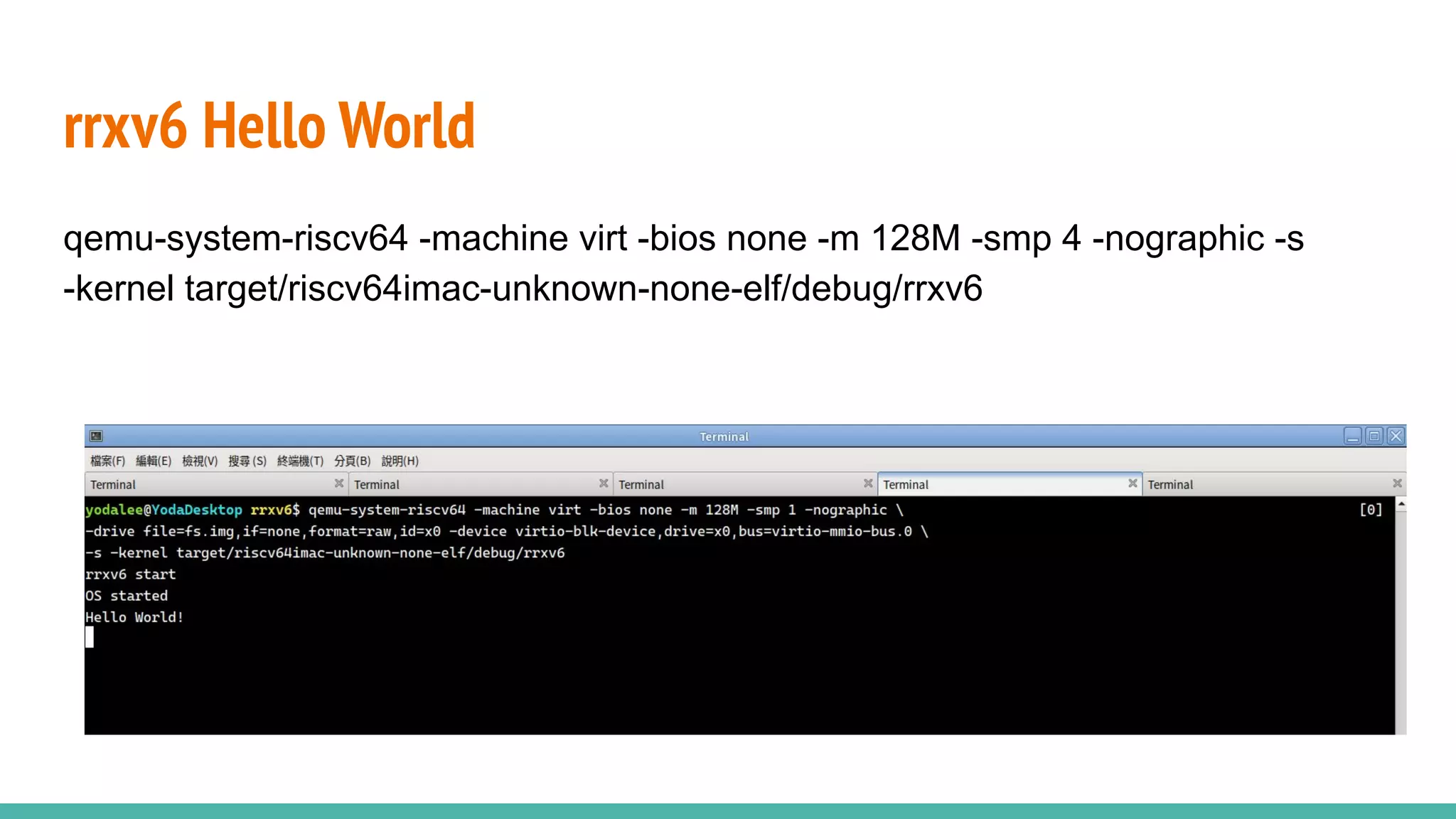
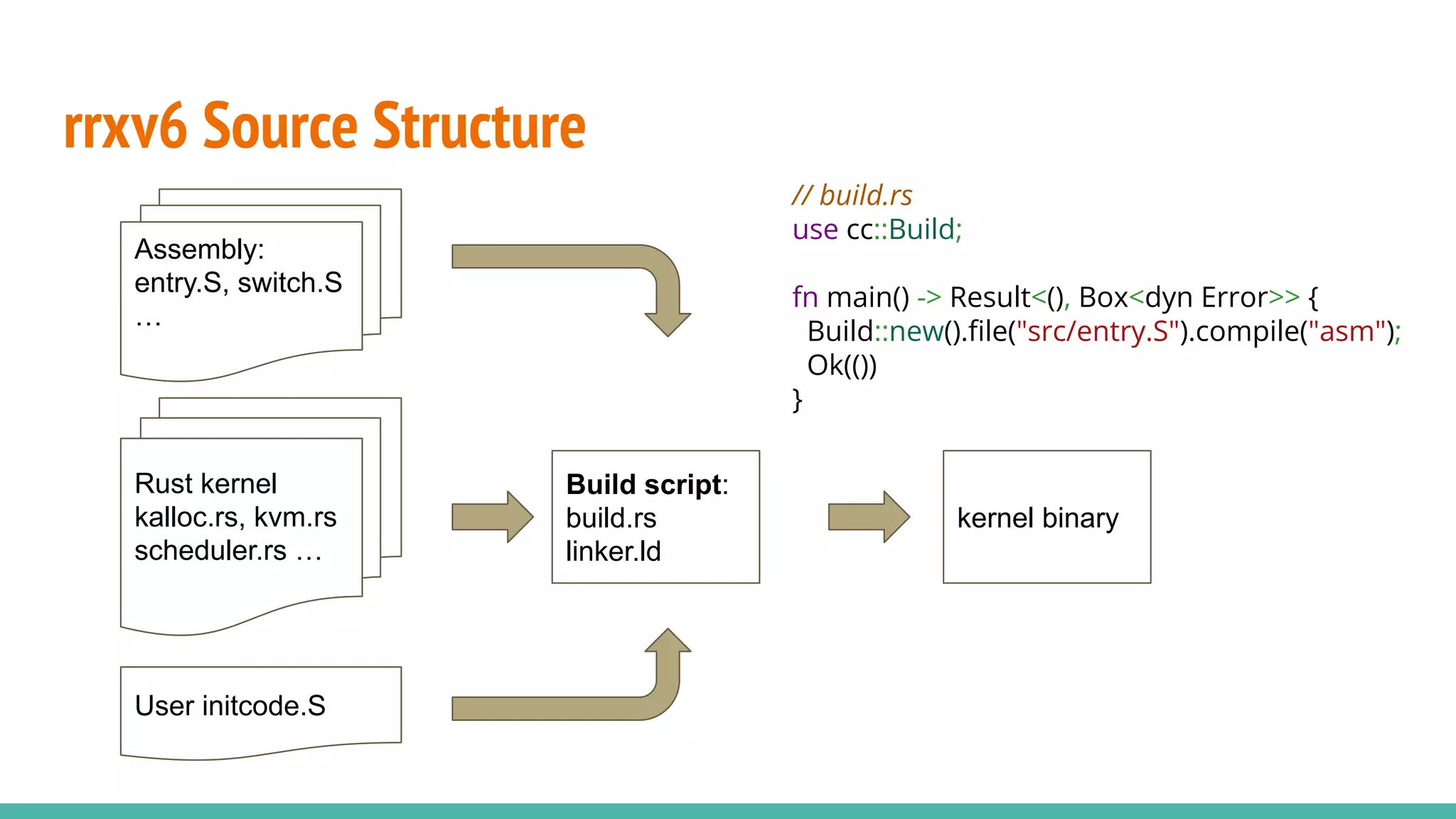
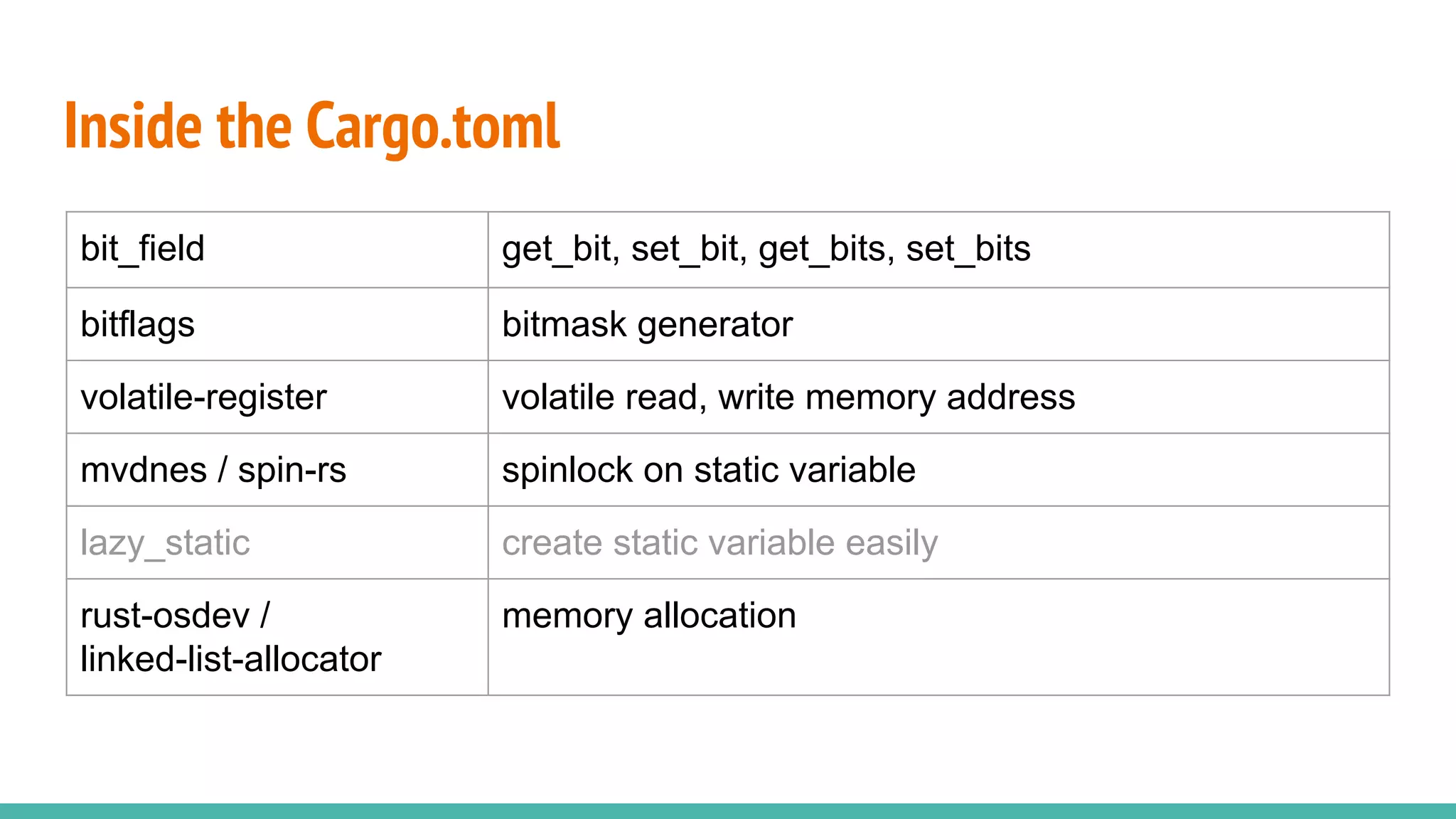
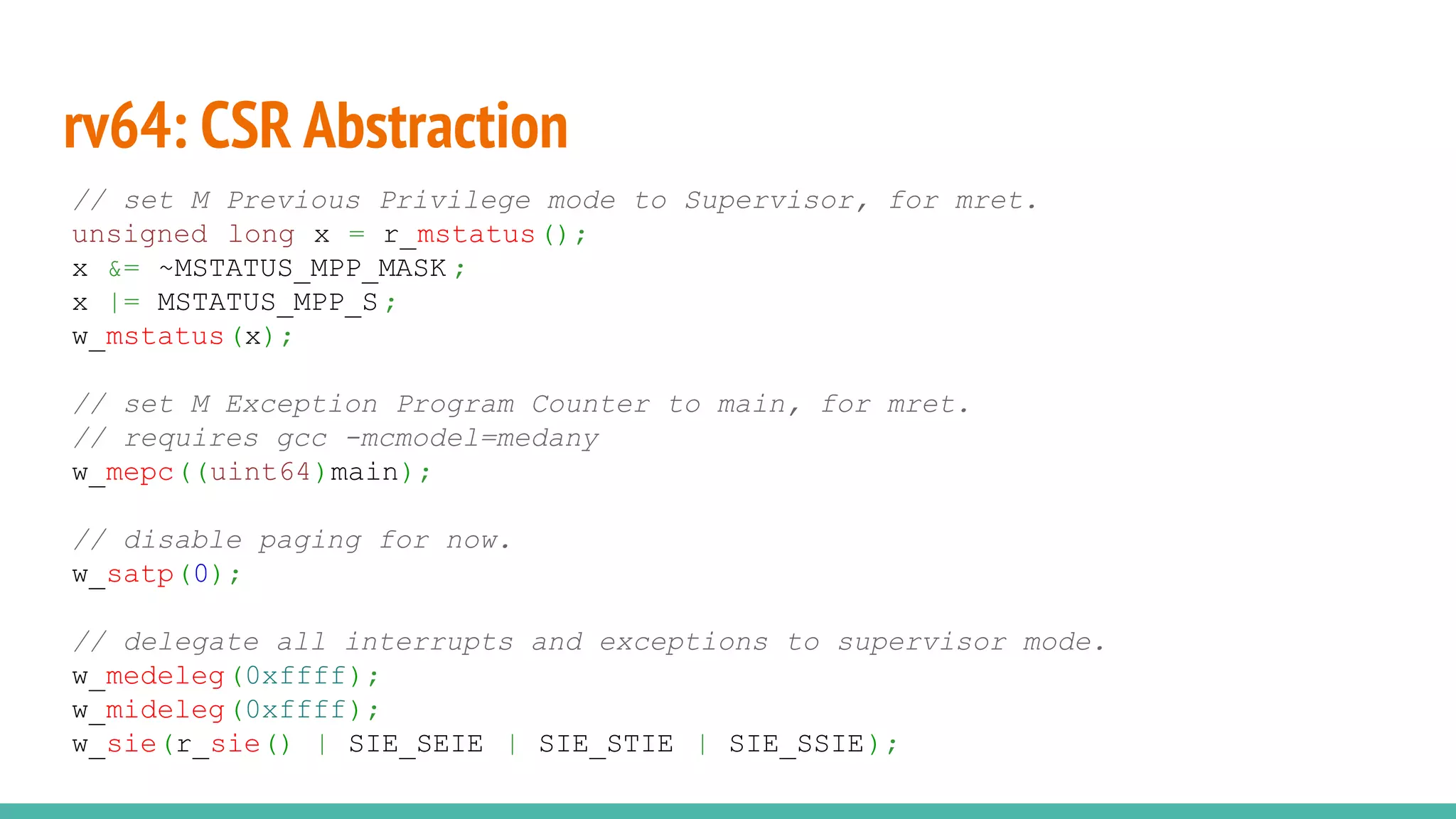
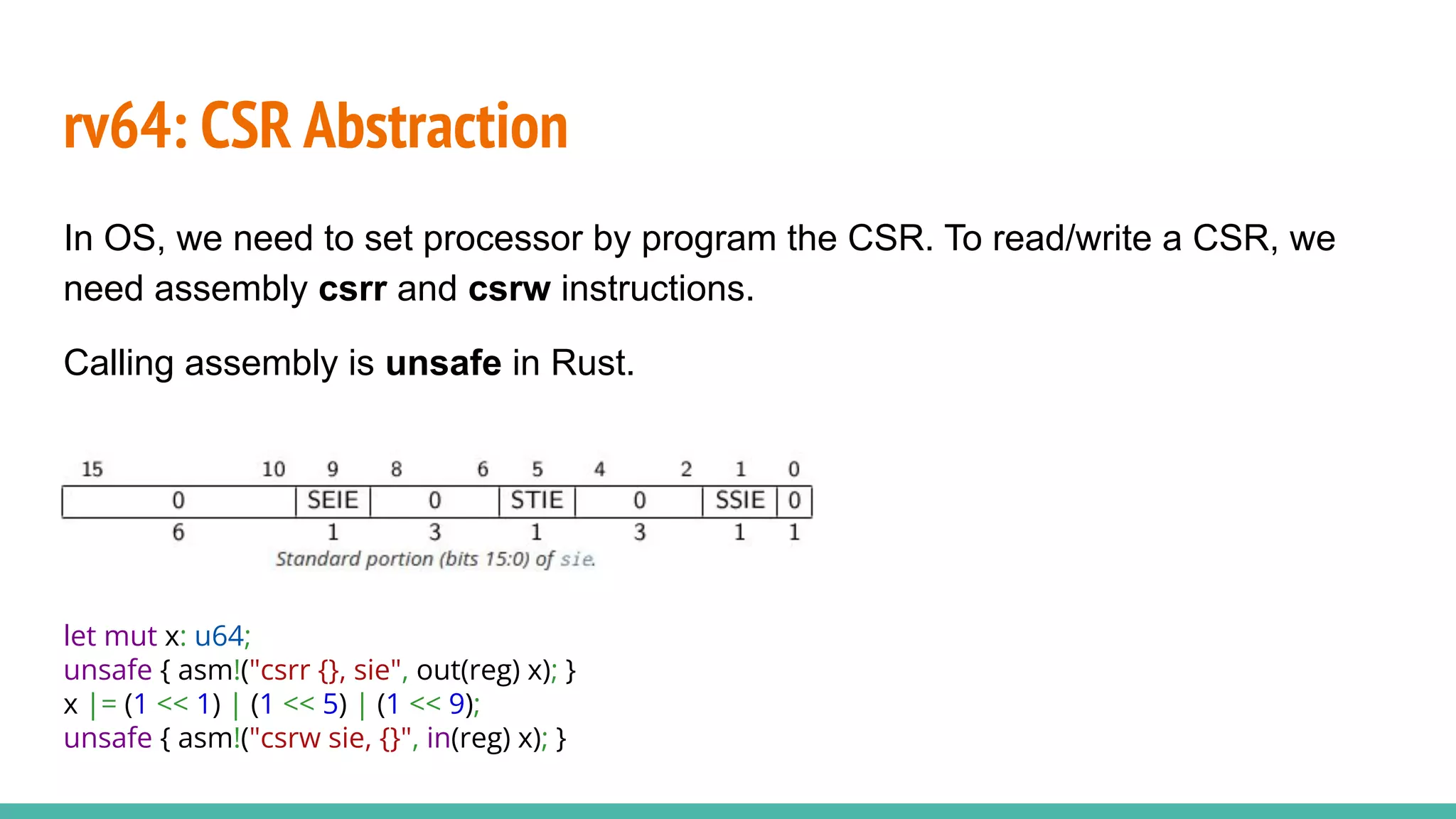
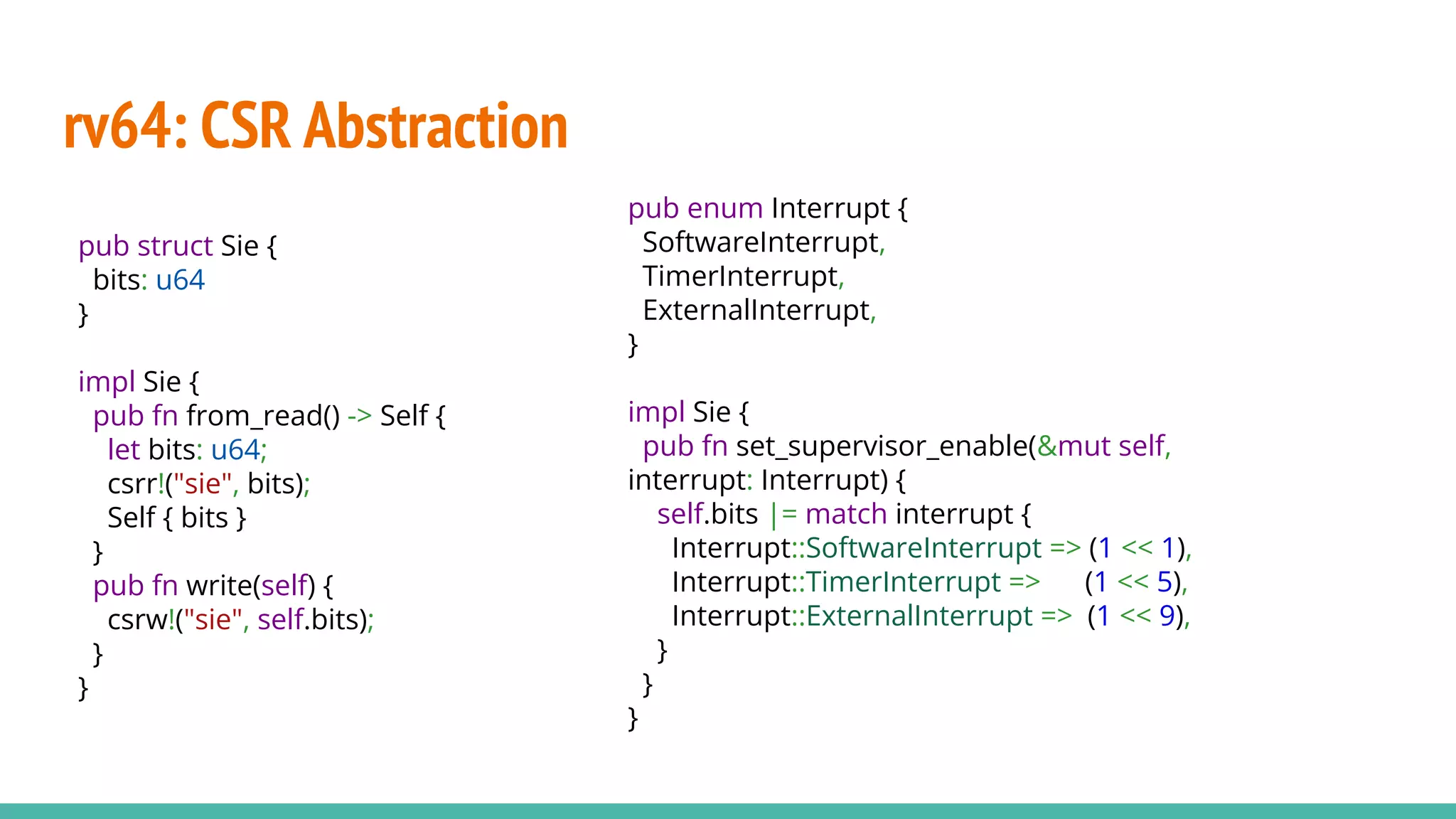
The document discusses the rrxv6 project, which is a Rust-based re-implementation of the xv6 operating system on a RISC-V architecture, emphasizing its features and implementation steps. It details the necessary toolchain for building and running the kernel, along with the source code structure and the challenges associated with memory allocation and mutable static data in Rust. The conclusion reflects on the feasibility of building a kernel in Rust without standard libraries and highlights the project's future work, including features like virtio and IPC.







![Required Toolchain
1. Use rustup to install rust toolchain riscv64imac-unknown-none-elf (lp64)
Set target in .cargo/config
2. Install riscv gcc for linking riscv64-unknown-elf-gcc
3. Install qemu-system-riscv to emulate the hardware
// .cargo/config
[build]
target = "riscv64imac-unknown-none-elf"
[target.riscv64imac-unknown-none-elf]
rustflags = ["-C", "link-arg=-Tlinker.ld"]](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-10-2048.jpg)

![Going std-less
Rust does not have std in RISC-V target.
// main.rs
#![no_std]
#![no_main]
use core::panic::PanicInfo;
static STACK0: [u8;STACK_SIZE * NCPU] = [0;STACK_SIZE * NCPU];
#[no_mangle]
fn start() -> ! { loop{} }
#[panic_handler]
fn panic(_panic: &PanicInfo<'_>) -> ! {
loop {}
}
.global _entry
_entry:
# sp = STACK0 + (hartid * 4096)
la sp, STACK0
li a0, STACK_SIZE
csrr a1, mhartid
addi a1, a1, 1
mul a0, a0, a1
add sp, sp, a0
call start](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-14-2048.jpg)


![MemoryAllocator
We cannot allocate memory if we are #![no_std].
All the memory allocation defined in alloc will cause panic!
Box::new(16)
Rc::new(32)
string::from_utf8()
format!("{}", 64)
vec![1,2,3,4,5]
Arc::new(48)](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-20-2048.jpg)
![MemoryAllocator
We have to provide the #[global_allocator], which should implement the
GlobalAlloc Trait.
pub unsafe trait GlobalAlloc {
unsafe fn alloc(&self, layout: Layout) -> *mut u8;
unsafe fn dealloc(&self, ptr: *mut u8, layout: Layout);
// optional
unsafe fn alloc_zeroed(&self, layout: Layout) -> *mut u8;
unsafe fn realloc(&self, ptr: *mut u8, layout: Layout, new_size: usize) -> *mut u8;
}](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-21-2048.jpg)
![MemoryAllocator -Dummy Implementation
struct DummyAllocator;
unsafe impl GlobalAlloc for DummyAllocator {
unsafe fn alloc(&self, _layout: Layout) -> *mut u8 { null_mut() }
unsafe fn dealloc(&self, _ptr: *mut u8, _layout: Layout) {}
}
#[global_allocator]
static ALLOCATOR: DummyAllocator = DummyAllocator {};](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-22-2048.jpg)
![MemoryAllocator
#[global_allocator]
static ALLOCATOR: LockedHeap = LockedHeap::empty();
pub const KERNELBASE : u64 = 0x8000_0000;
pub const PHYSTOP : u64 = KERNELBASE + 128 * 1024 * 1024;
pub fn init_kvm() {
ALLOCATOR
.lock()
.init(KERNELBASE, PHYSTOP)
}
I use rust-osdev / linked-list-allocator (and submit a patch to it)](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-23-2048.jpg)
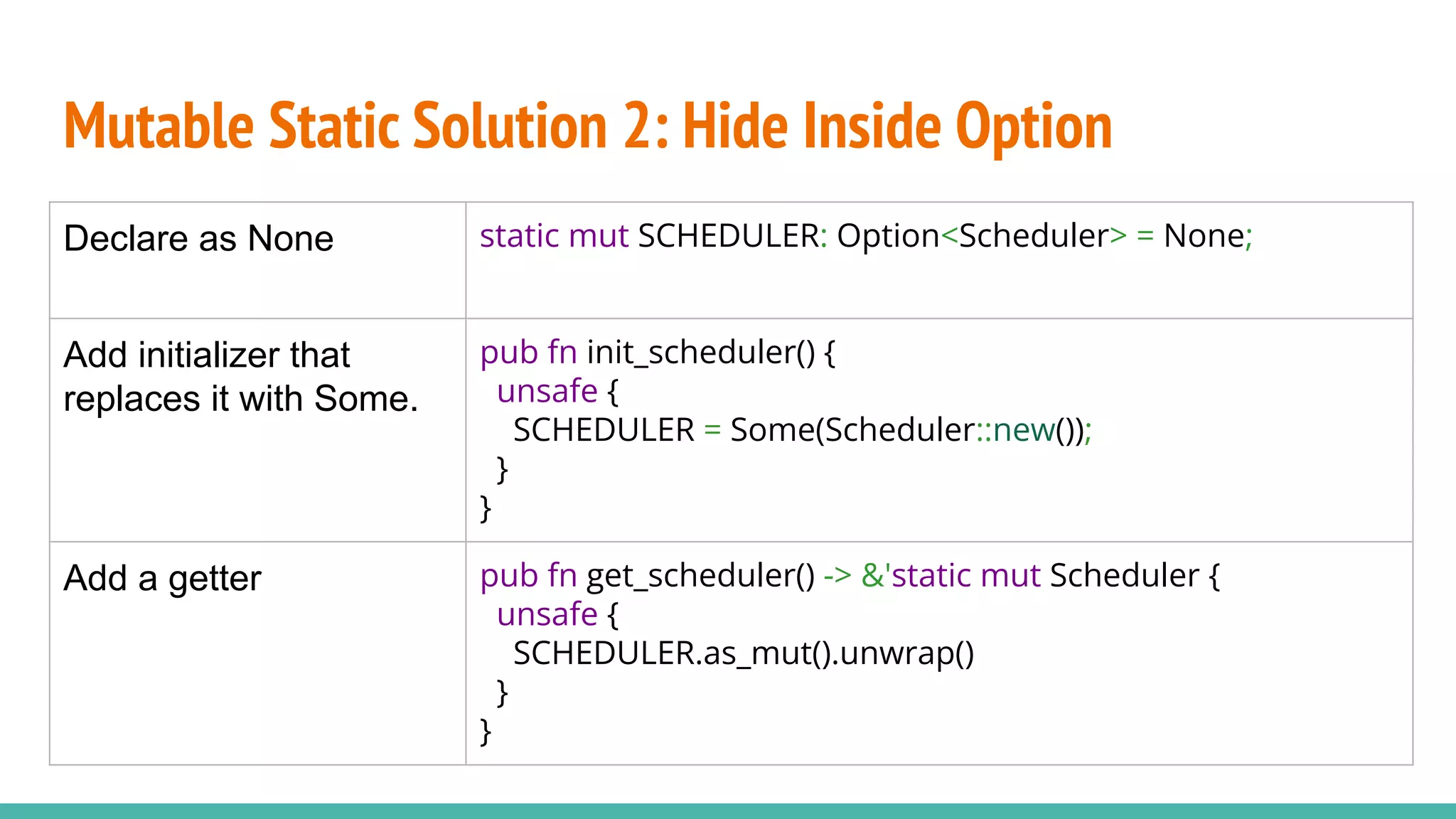
![Mutable Static
Accessing mutable static is unsafe in Rust. (what a surprise)
static mut DATA: u32 = 0;
println("{}", DATA);
error[E0133]: use of mutable static is unsafe and requires unsafe
function or block
--> a.rs:4:20
|
4 | println!("{}", DATA);
| ^^^^ use of mutable static](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-25-2048.jpg)

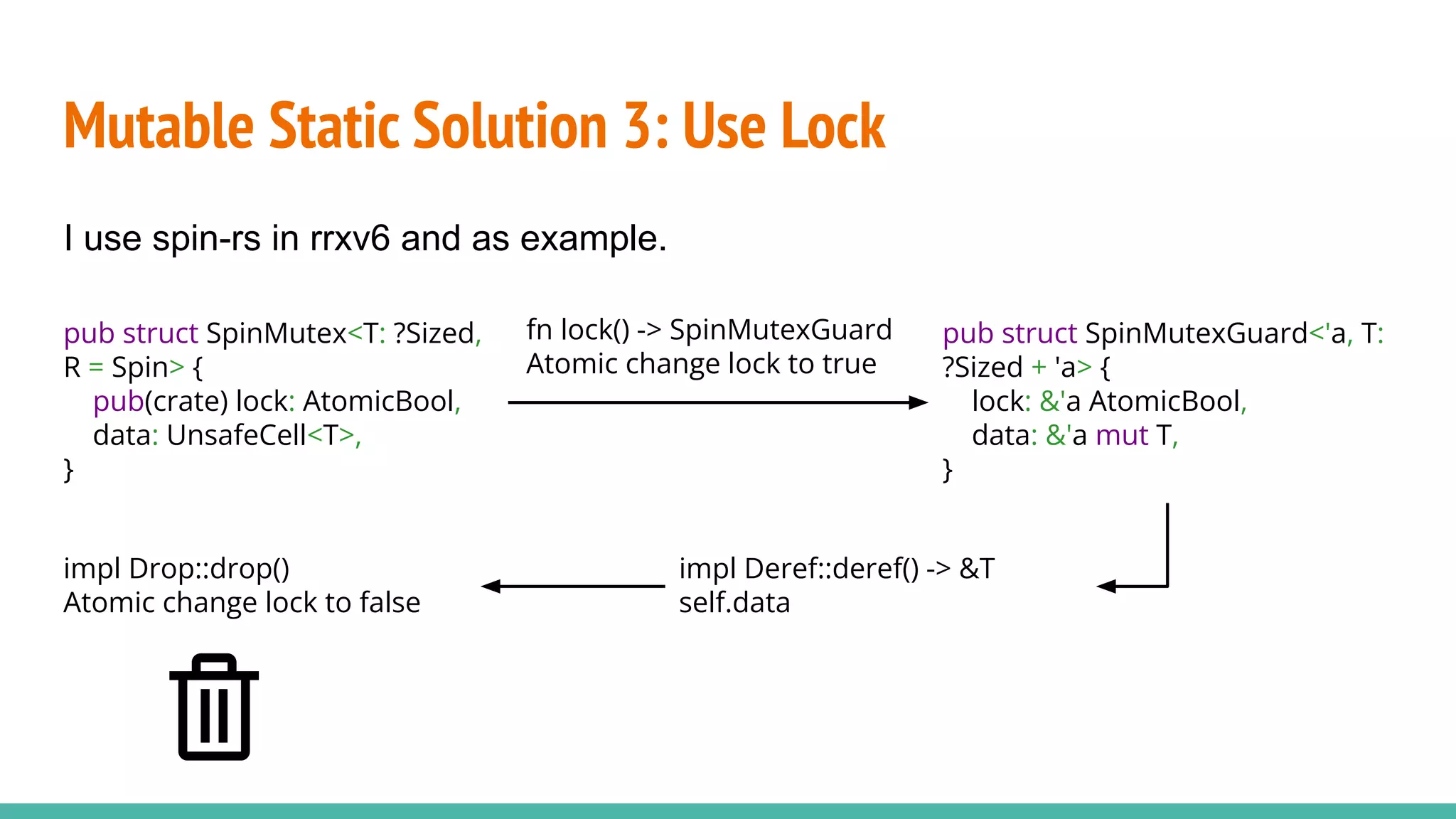
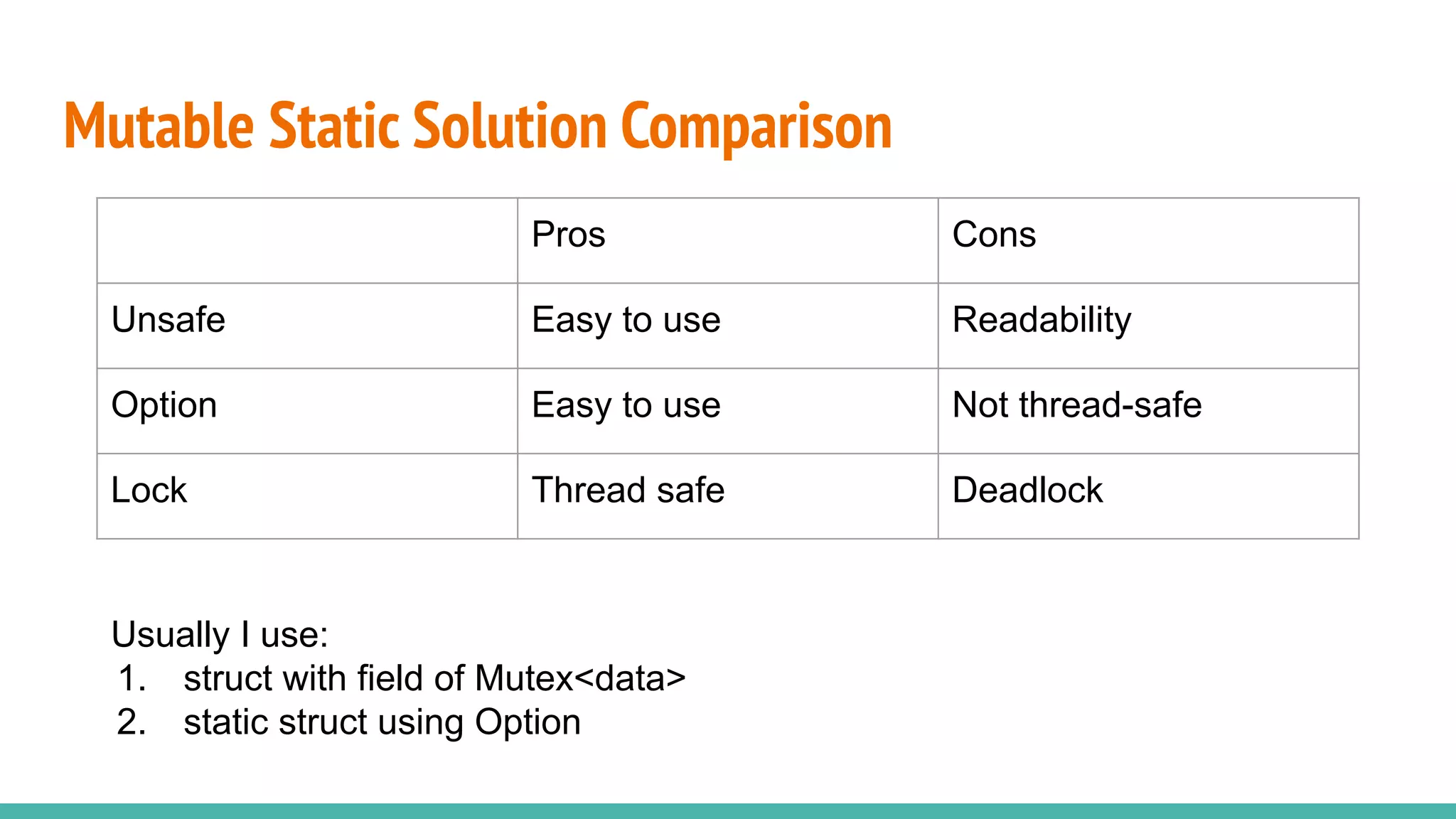
![Limitation: be careful not to create deadlock.
Once I put process infomations in a lock: Mutex<PROCESS[16]>
Mutable Static Solution 3: Use Lock
scheduler process[0]
Context switch
lock() and get
process[0]
Timer interrupt
Deadlock](https://image.slidesharecdn.com/rrxv6buildariscvxv6kernelinrust-220803140812-d42faa73/75/rrxv6-Build-a-Riscv-xv6-Kernel-in-Rust-pdf-29-2048.jpg)