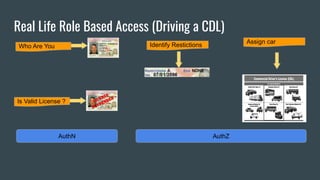
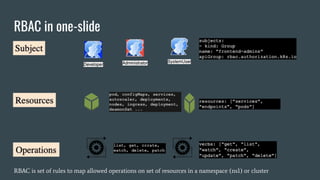
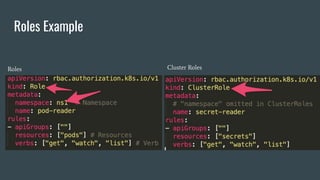
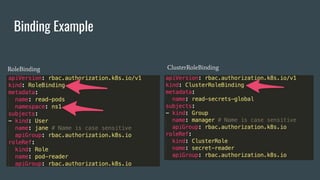
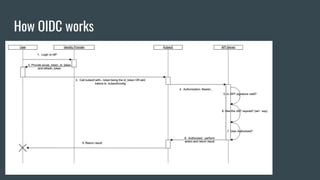
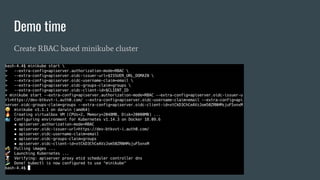
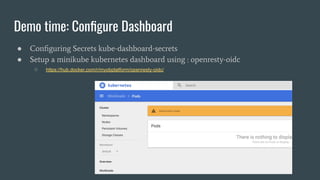
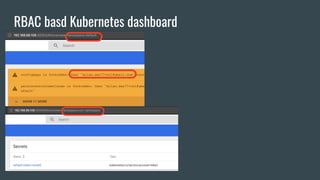
This document discusses Role Based Access Control (RBAC) in Kubernetes. It begins with an introduction of the speaker and then provides an overview of RBAC including roles, bindings, and how authentication works. It demonstrates how to configure RBAC and manage users through extensions like Auth0 to restrict access at the namespace and cluster level. The speaker then shows a demo of setting up RBAC roles and bindings in a Minikube cluster to configure secure access to the Kubernetes dashboard.