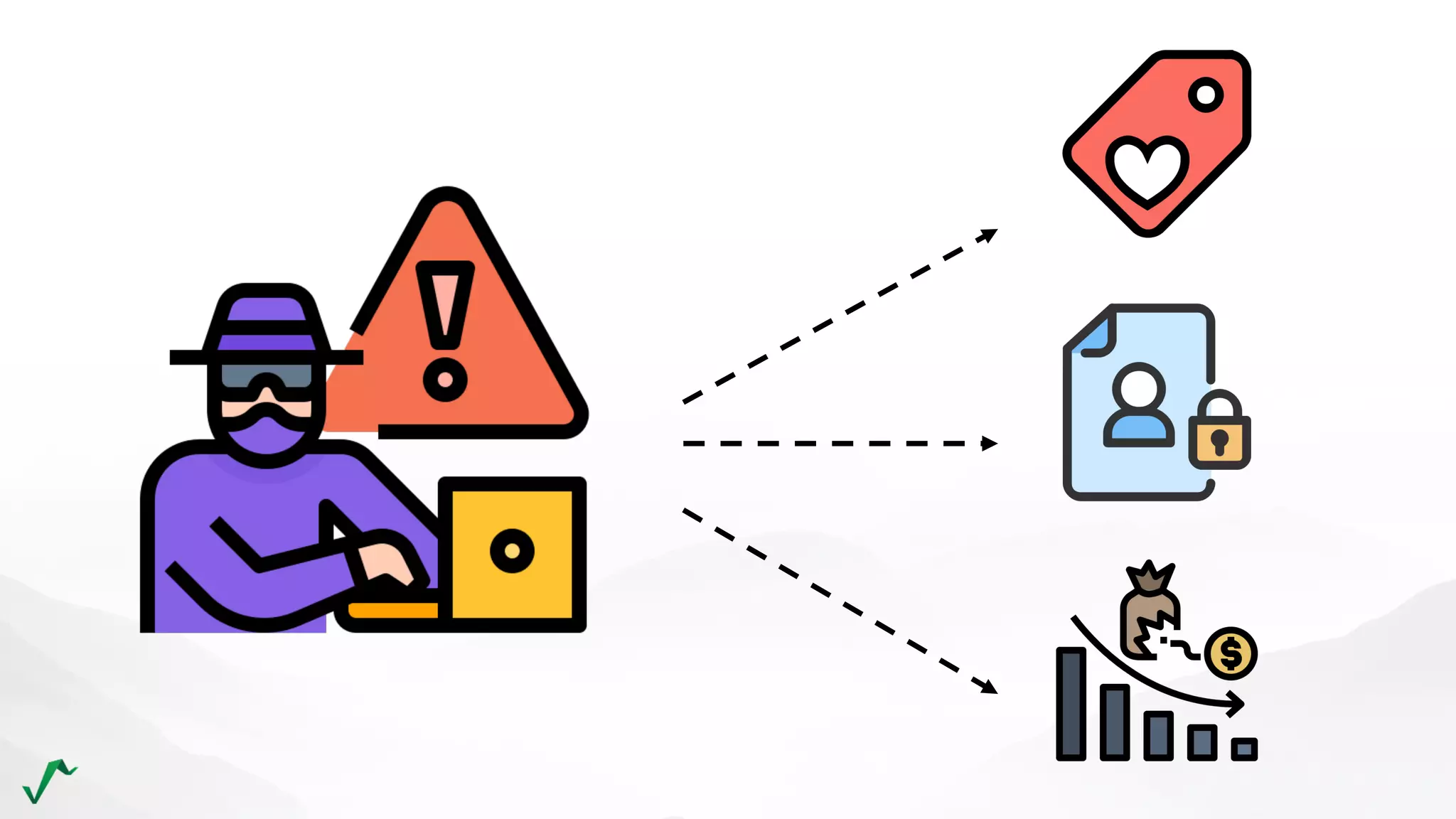
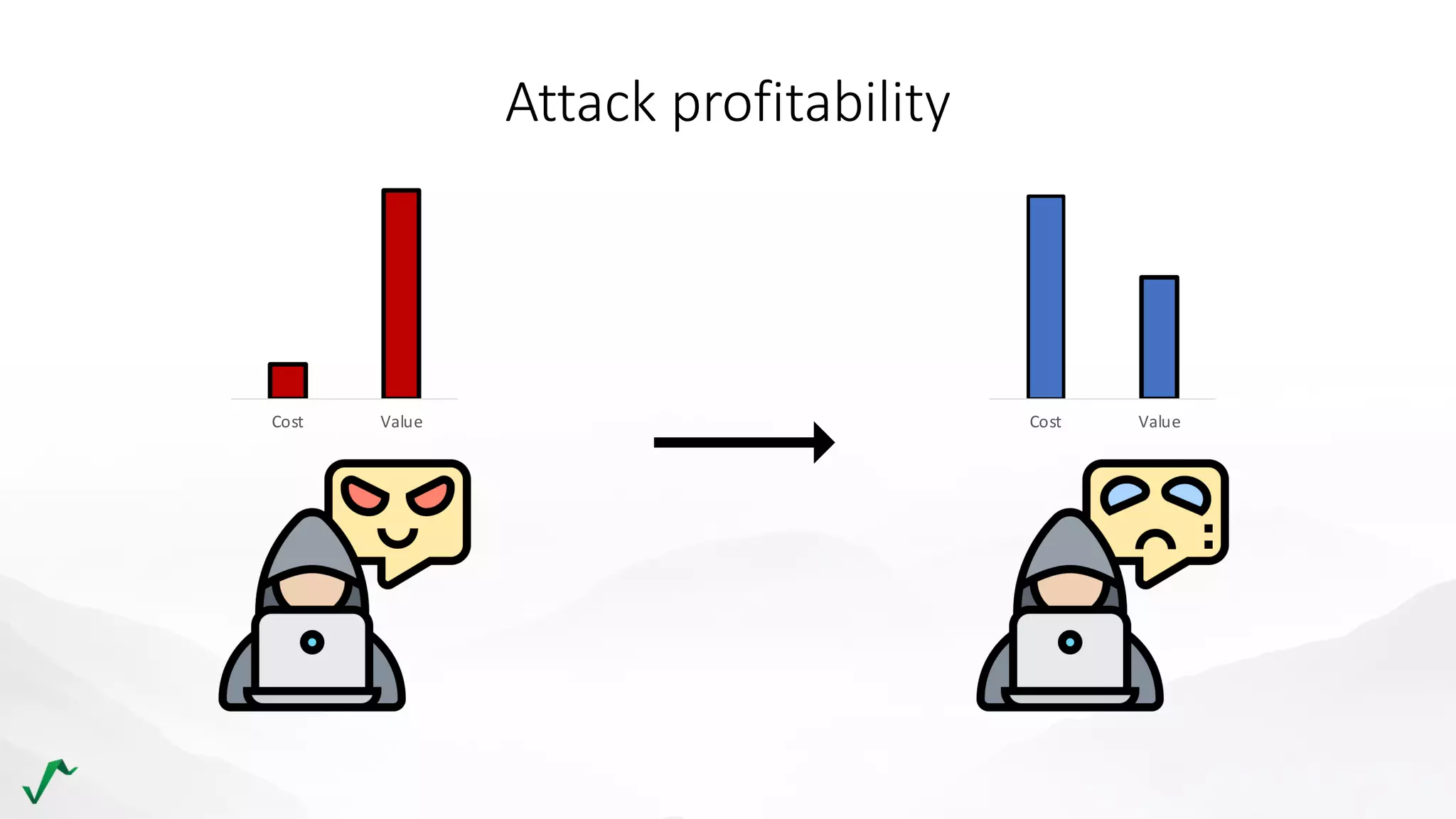
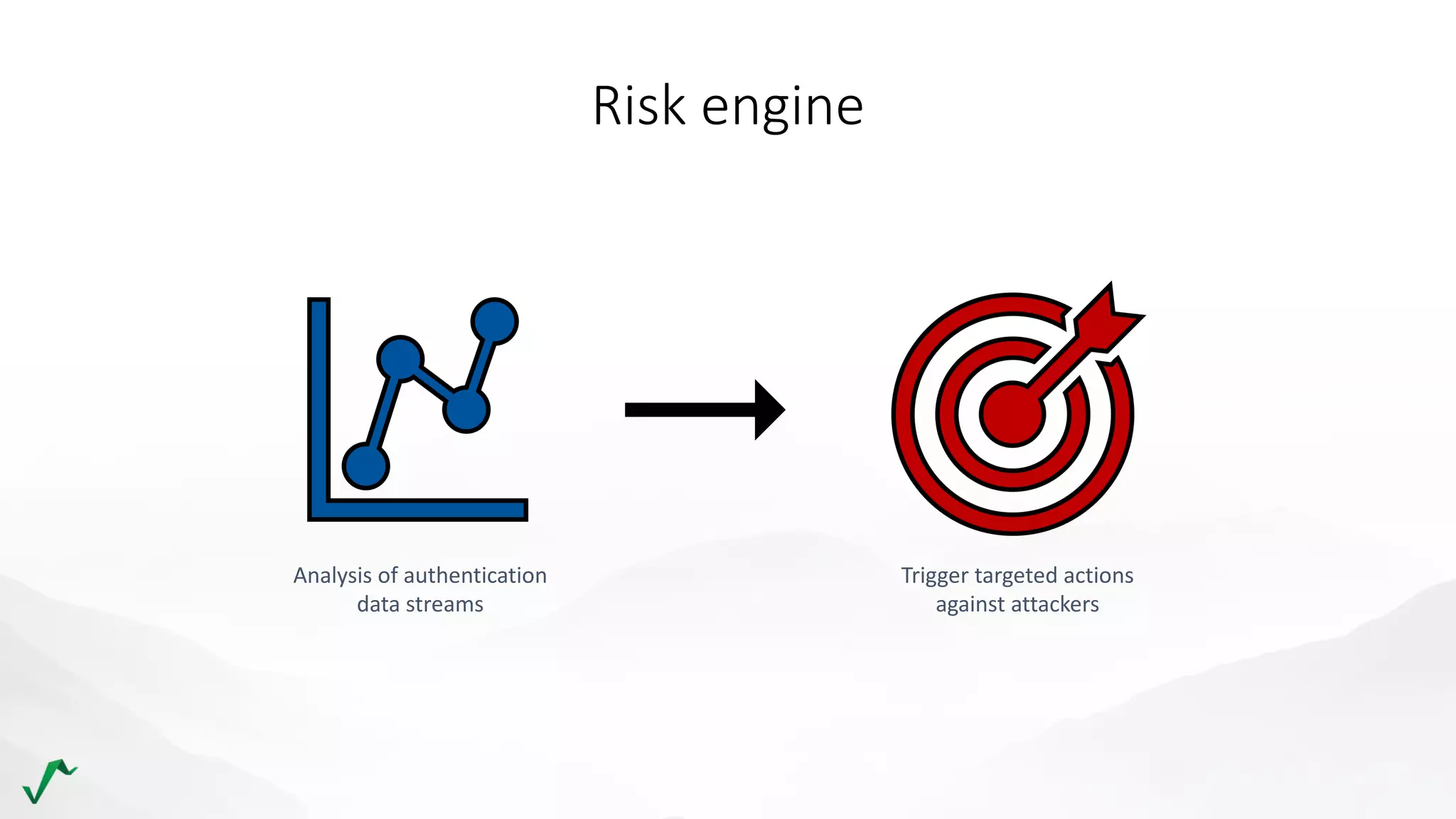
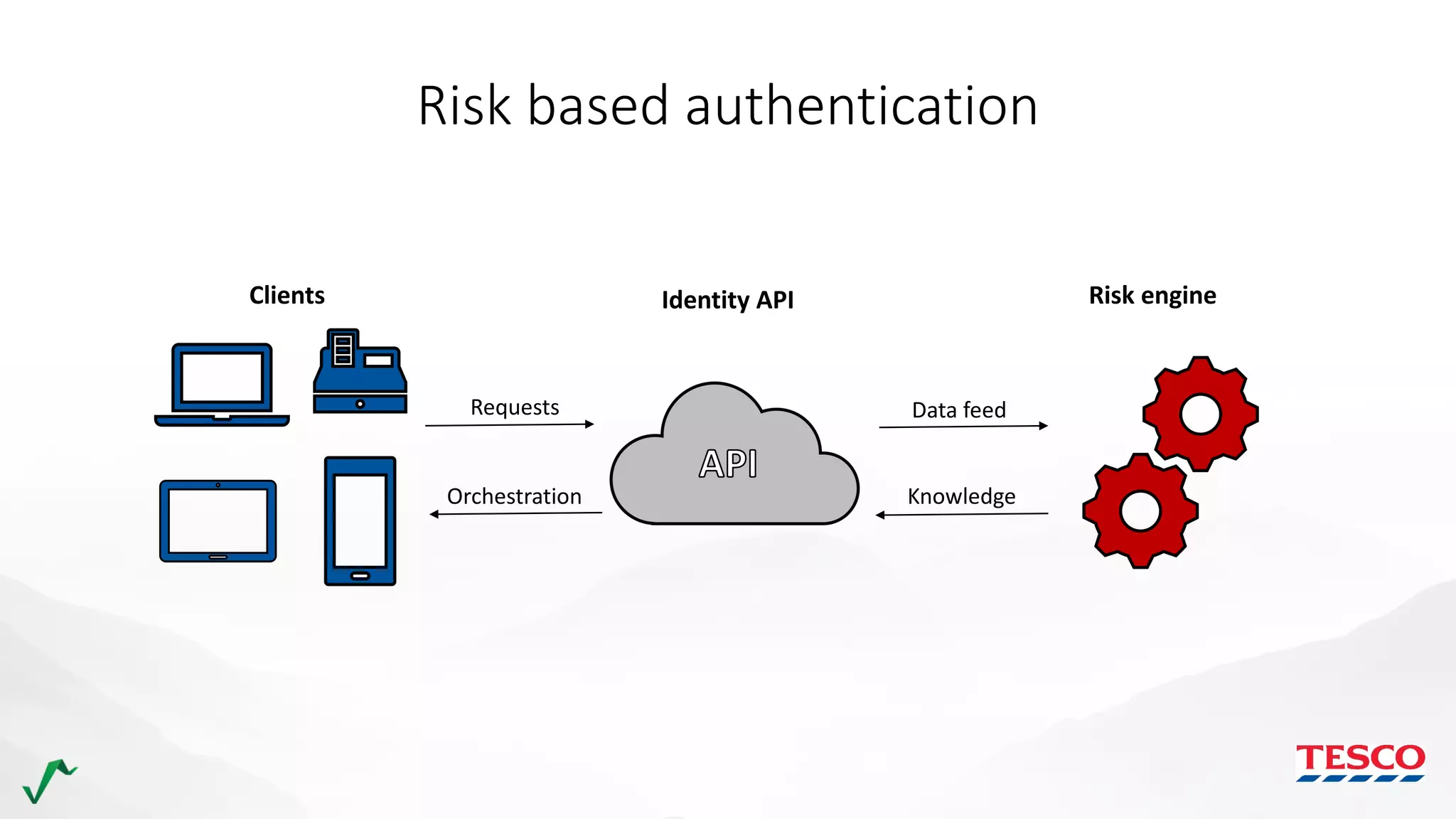
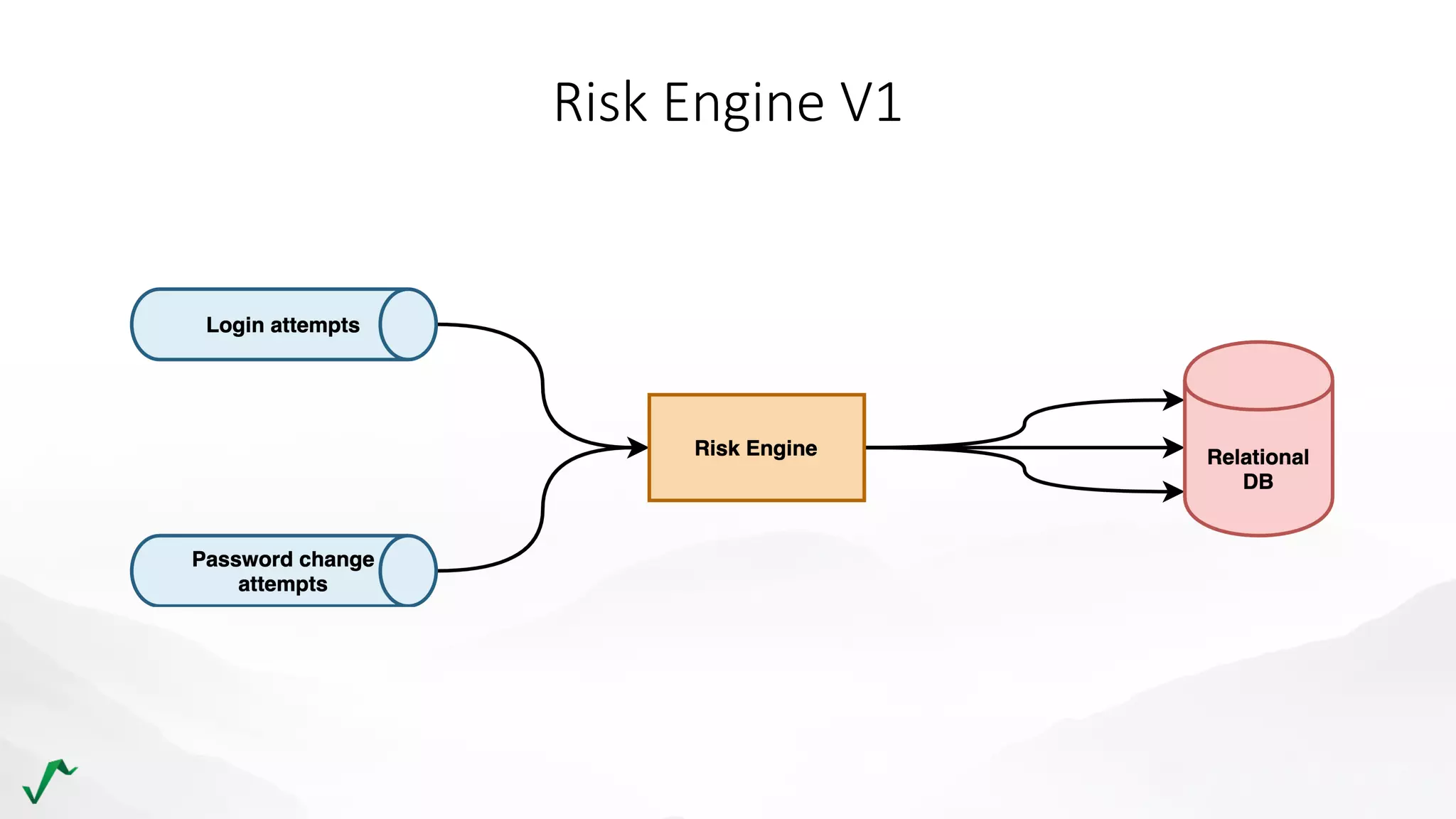
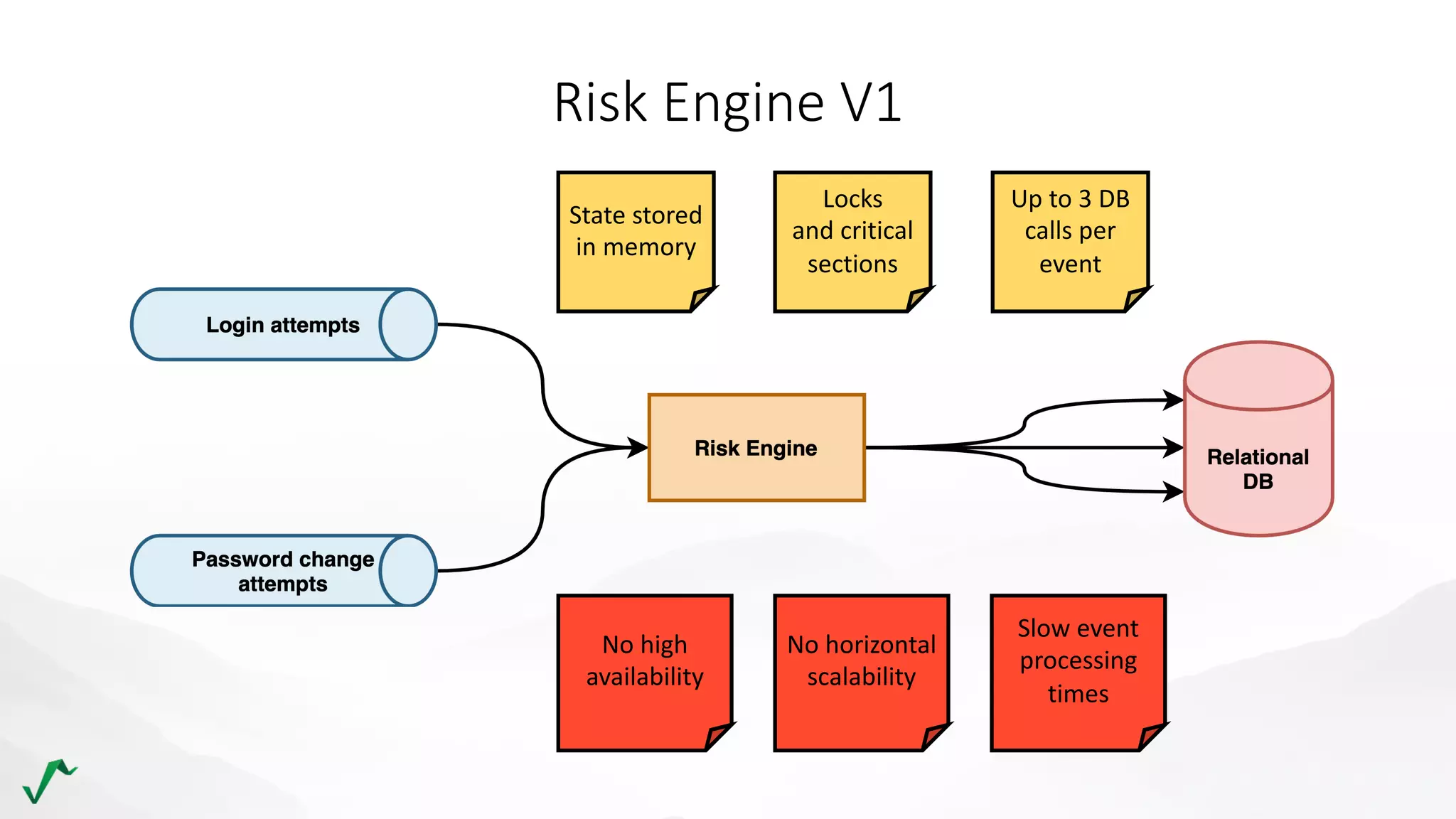
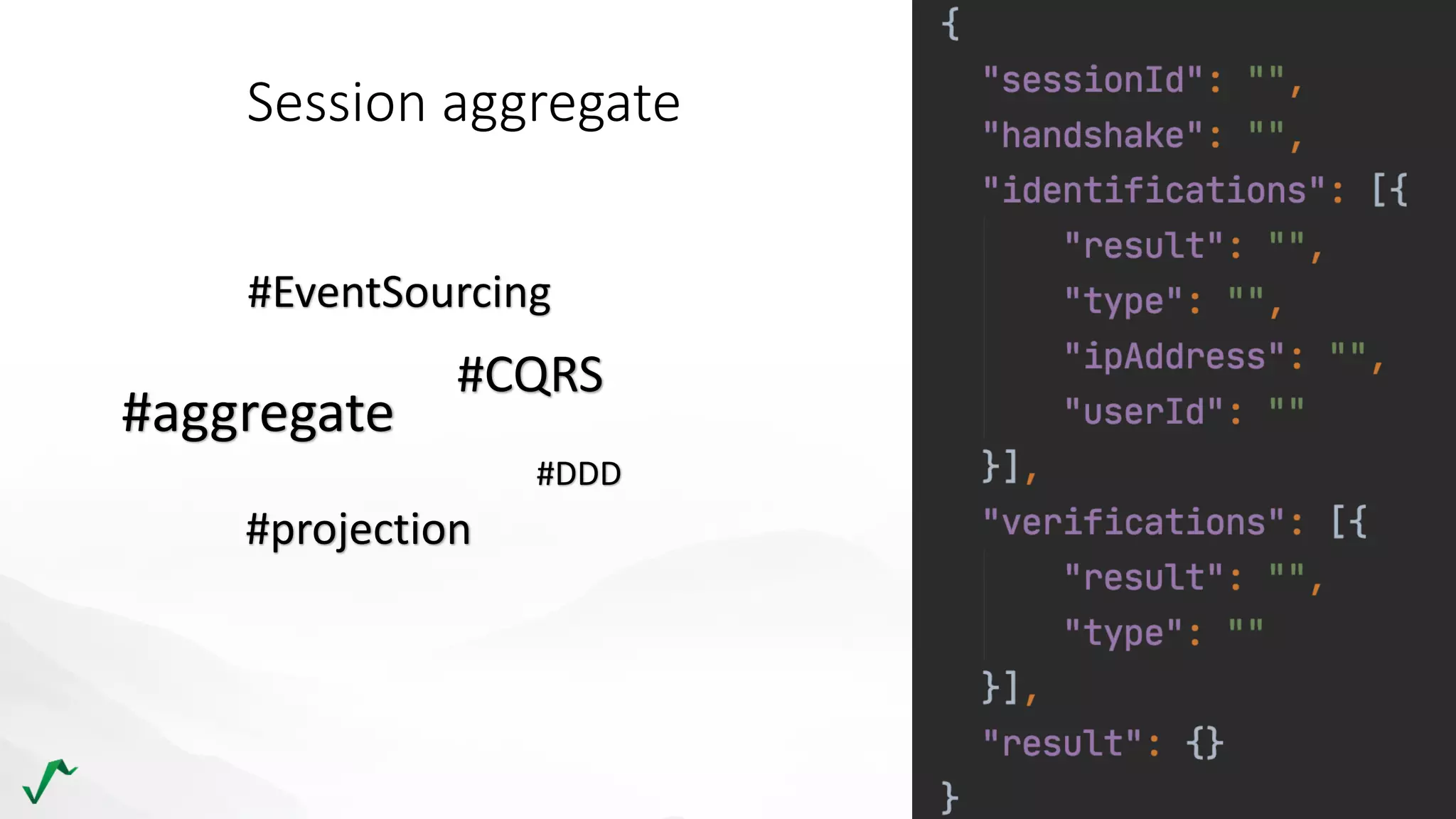
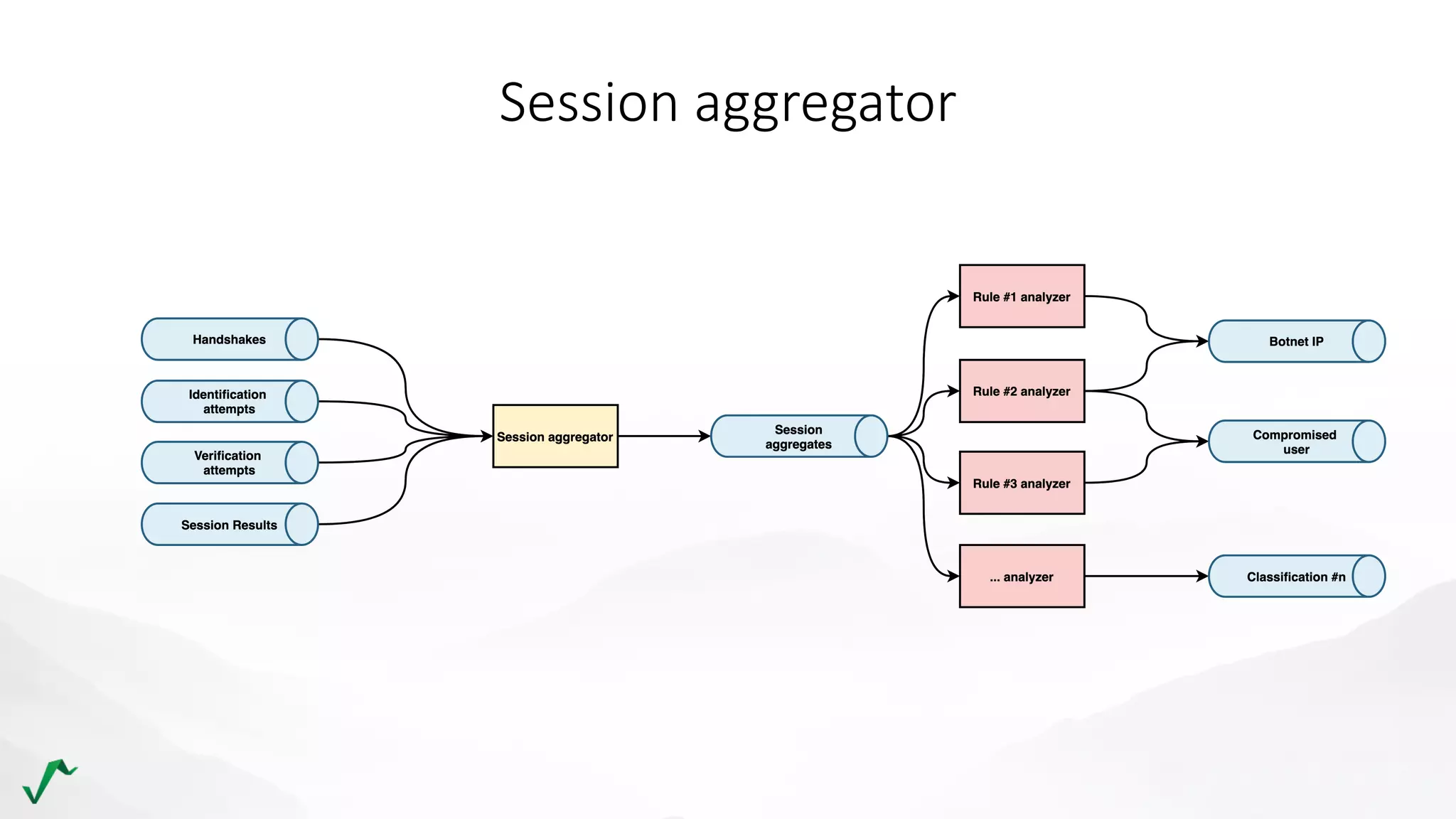
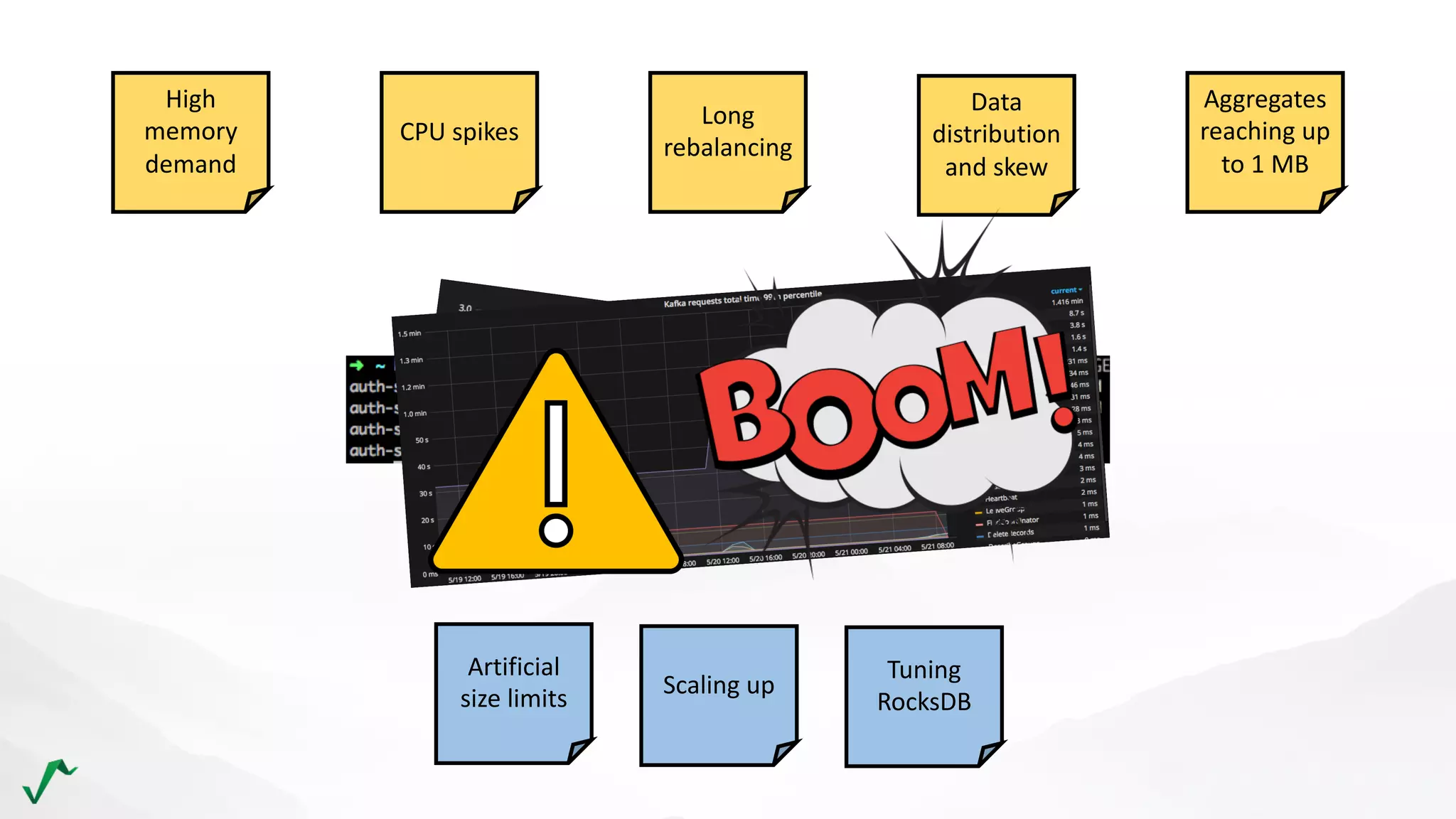
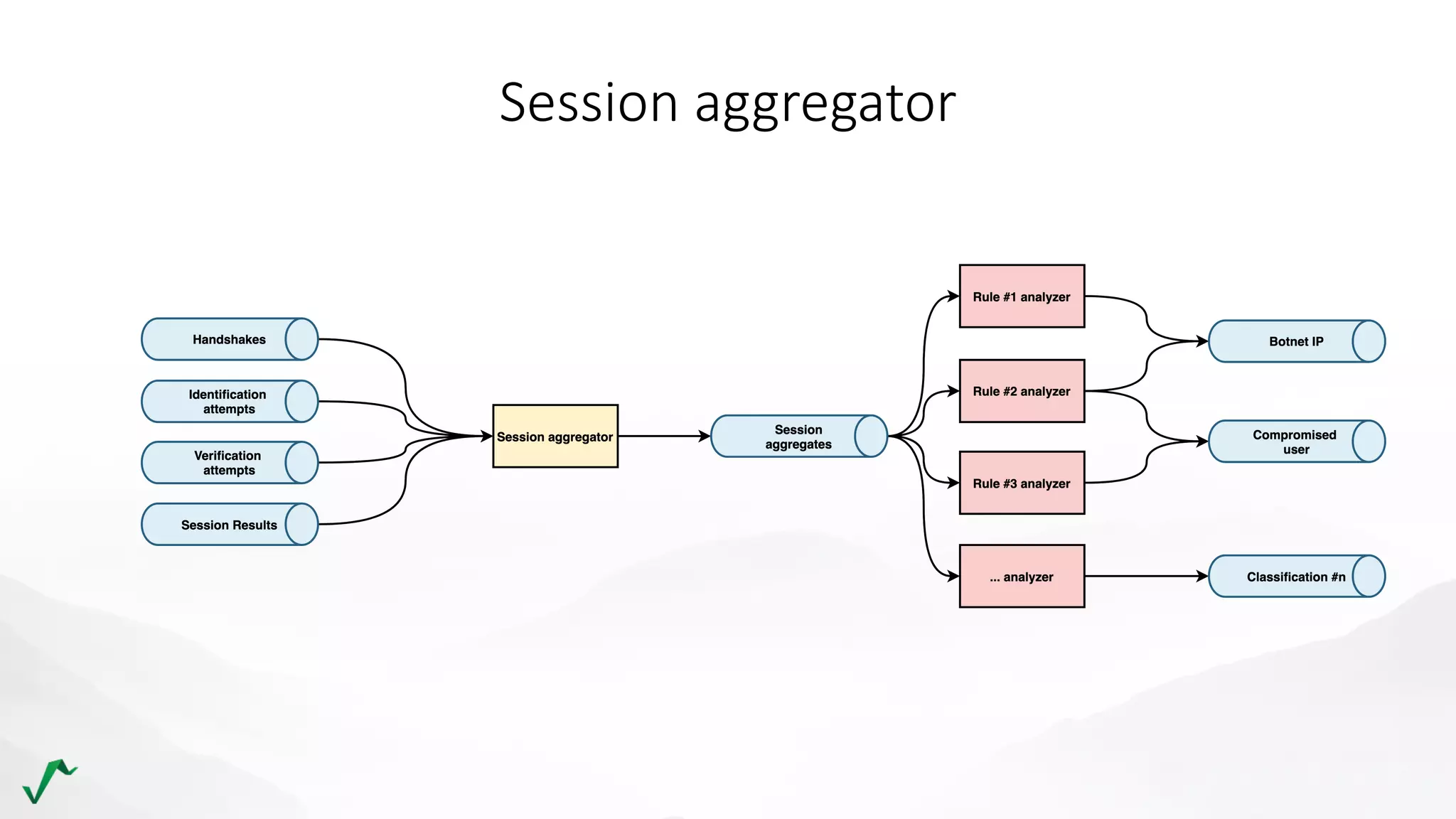
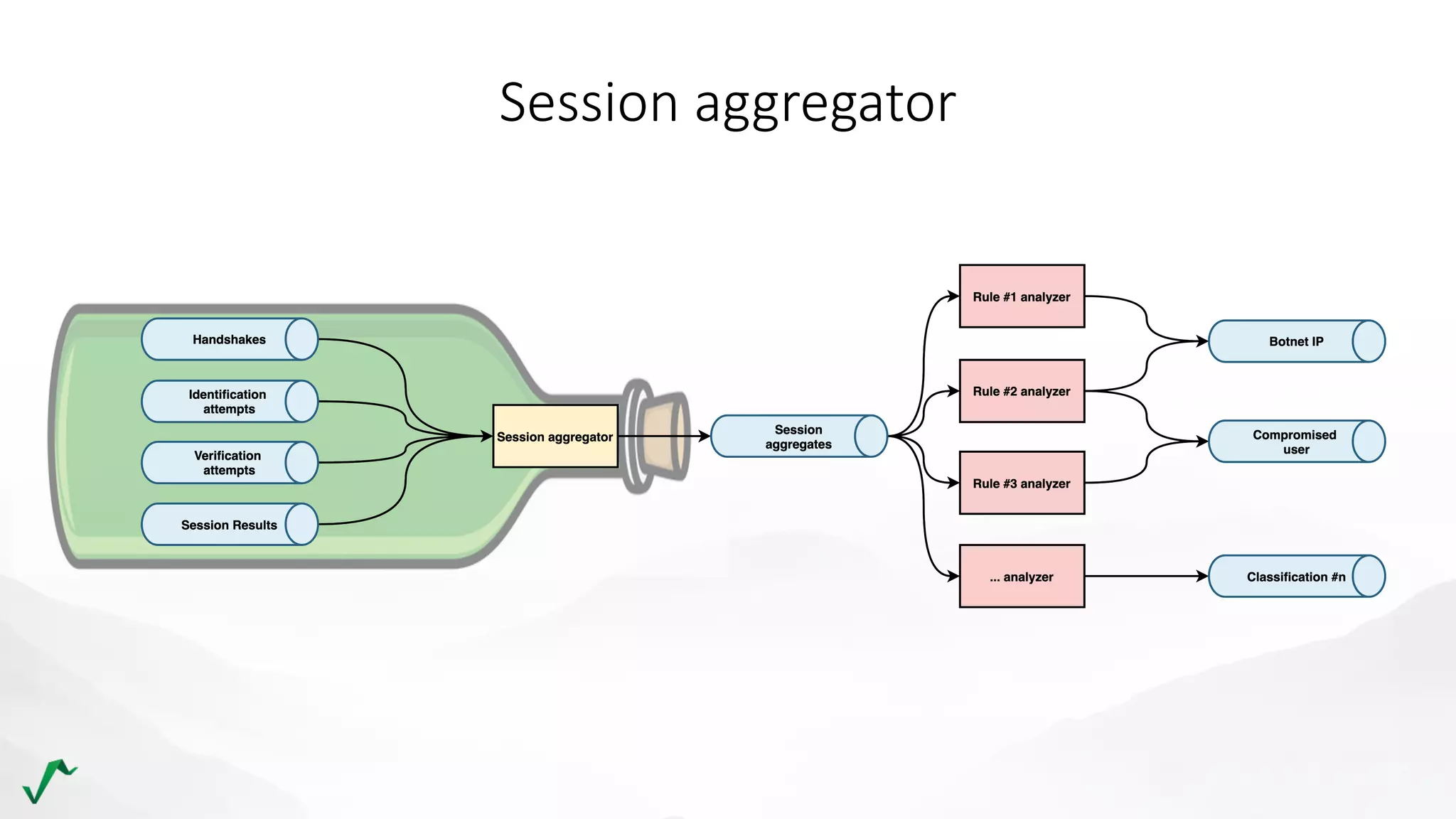
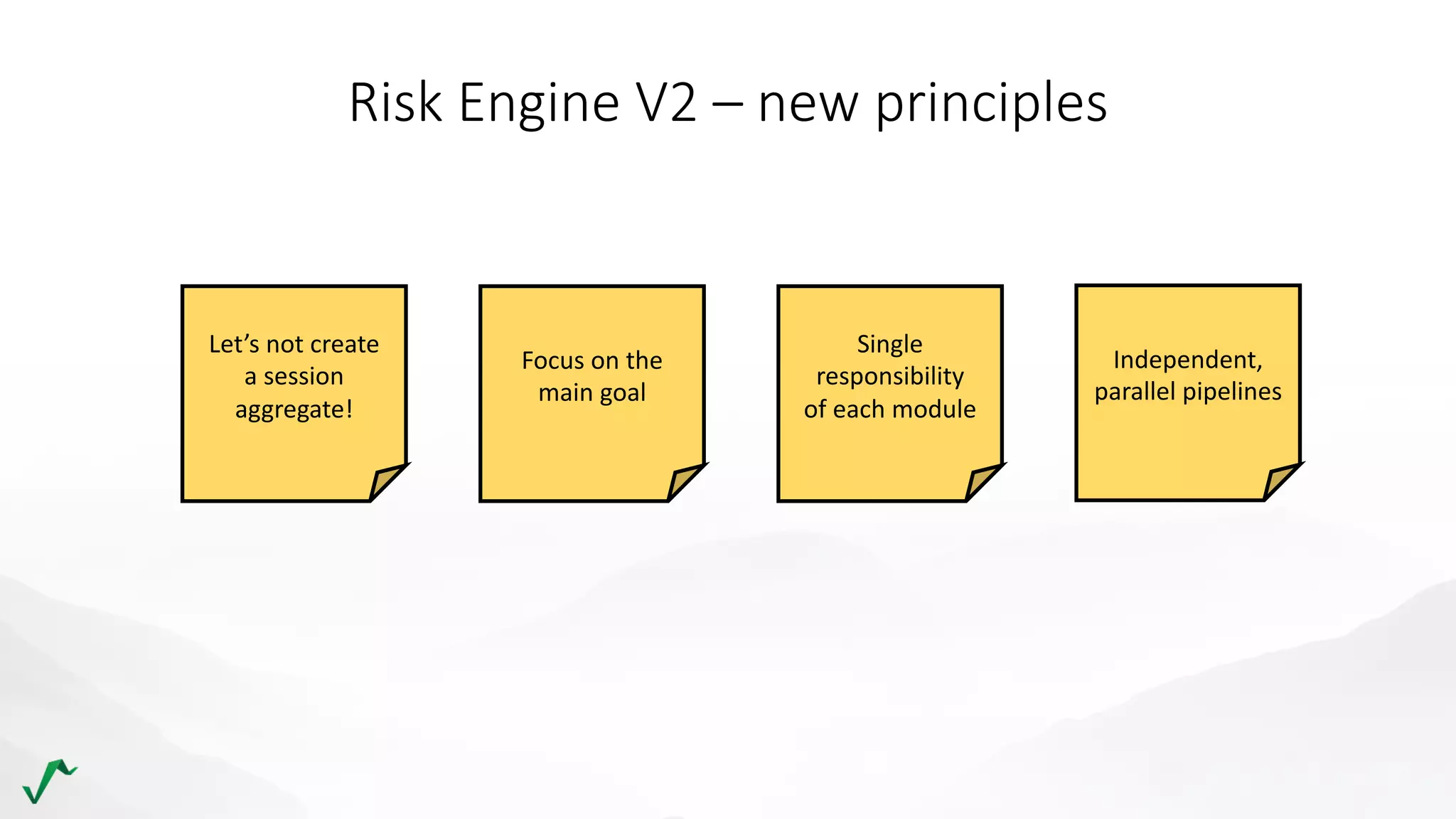
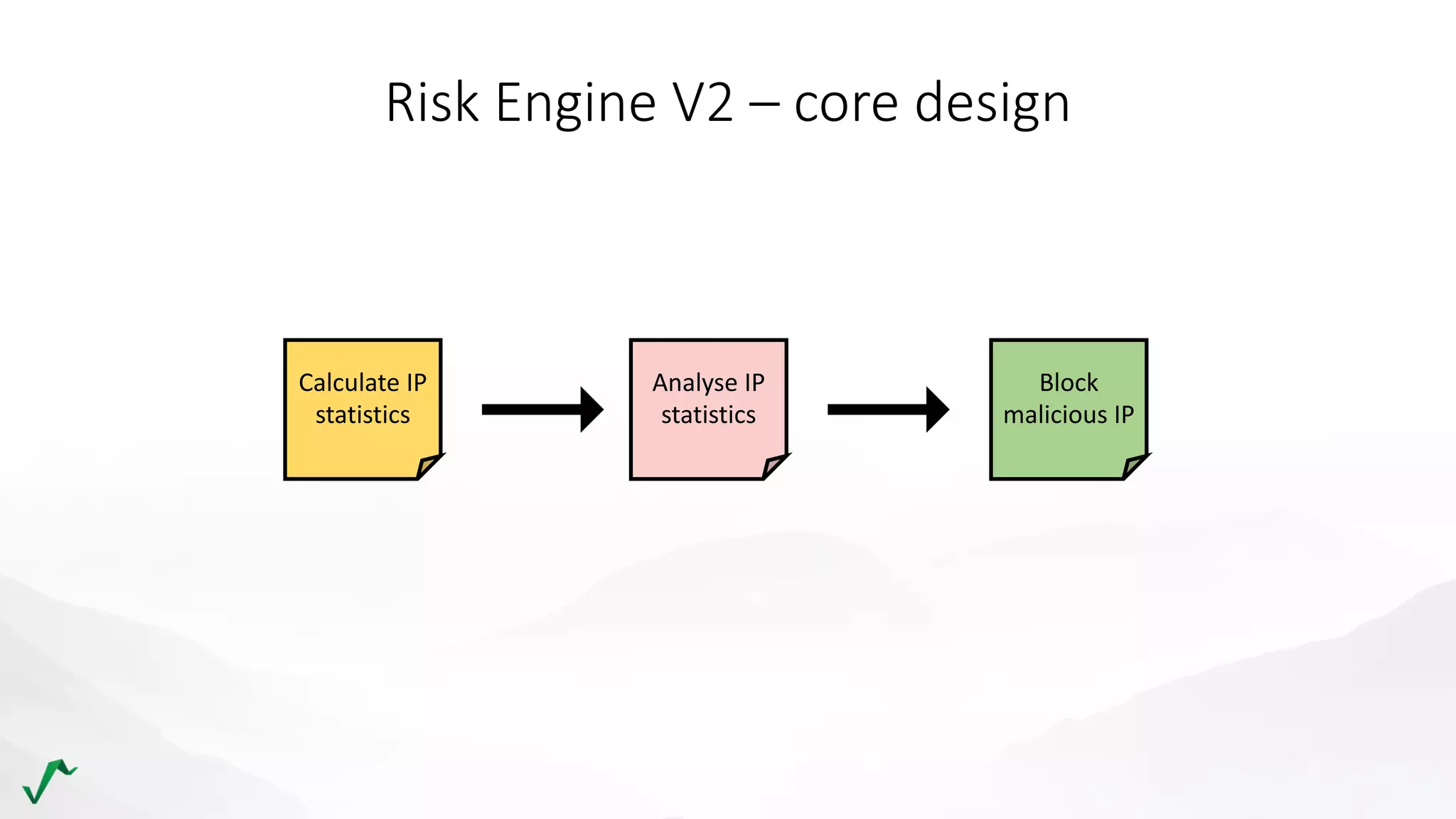
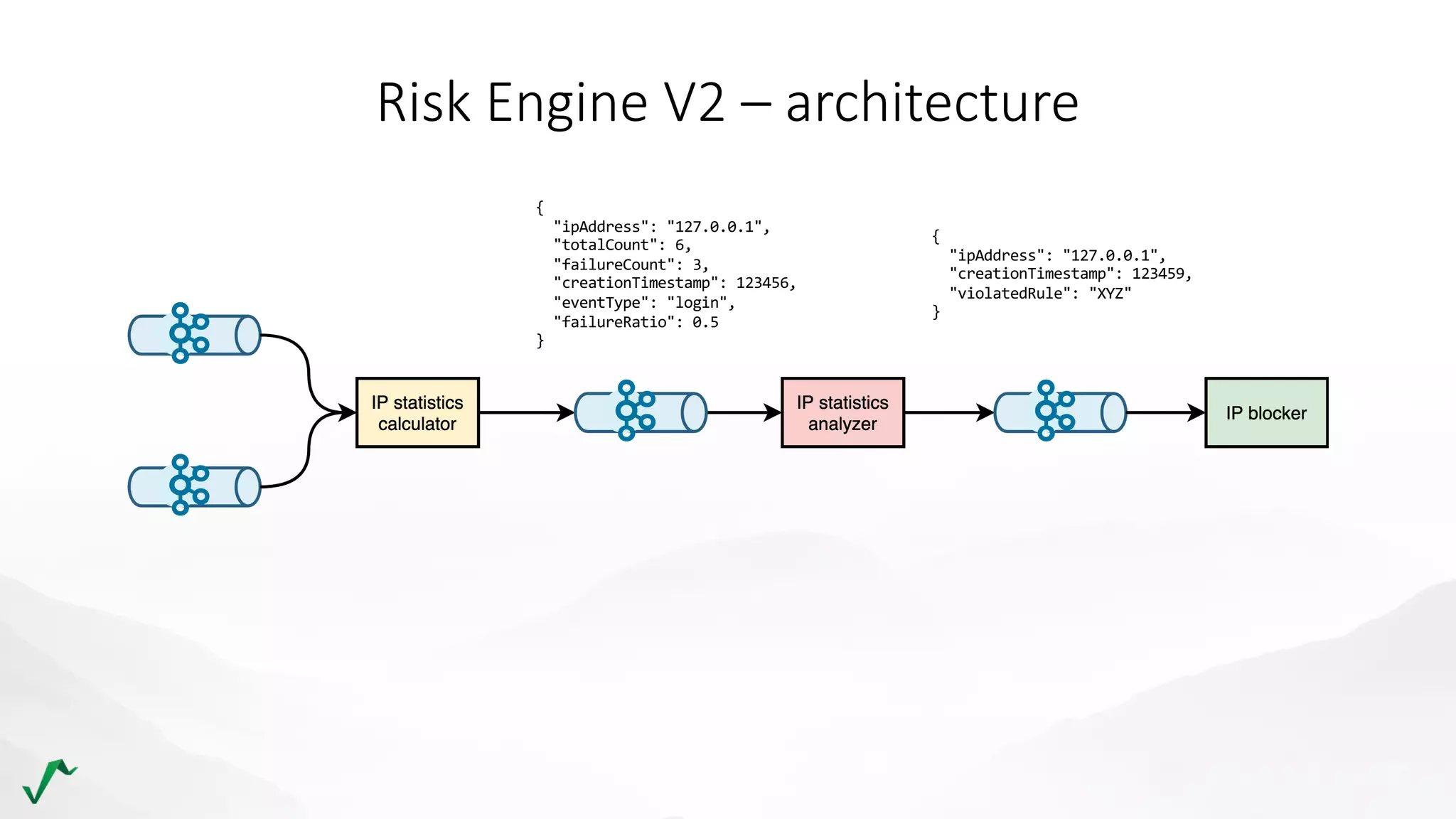
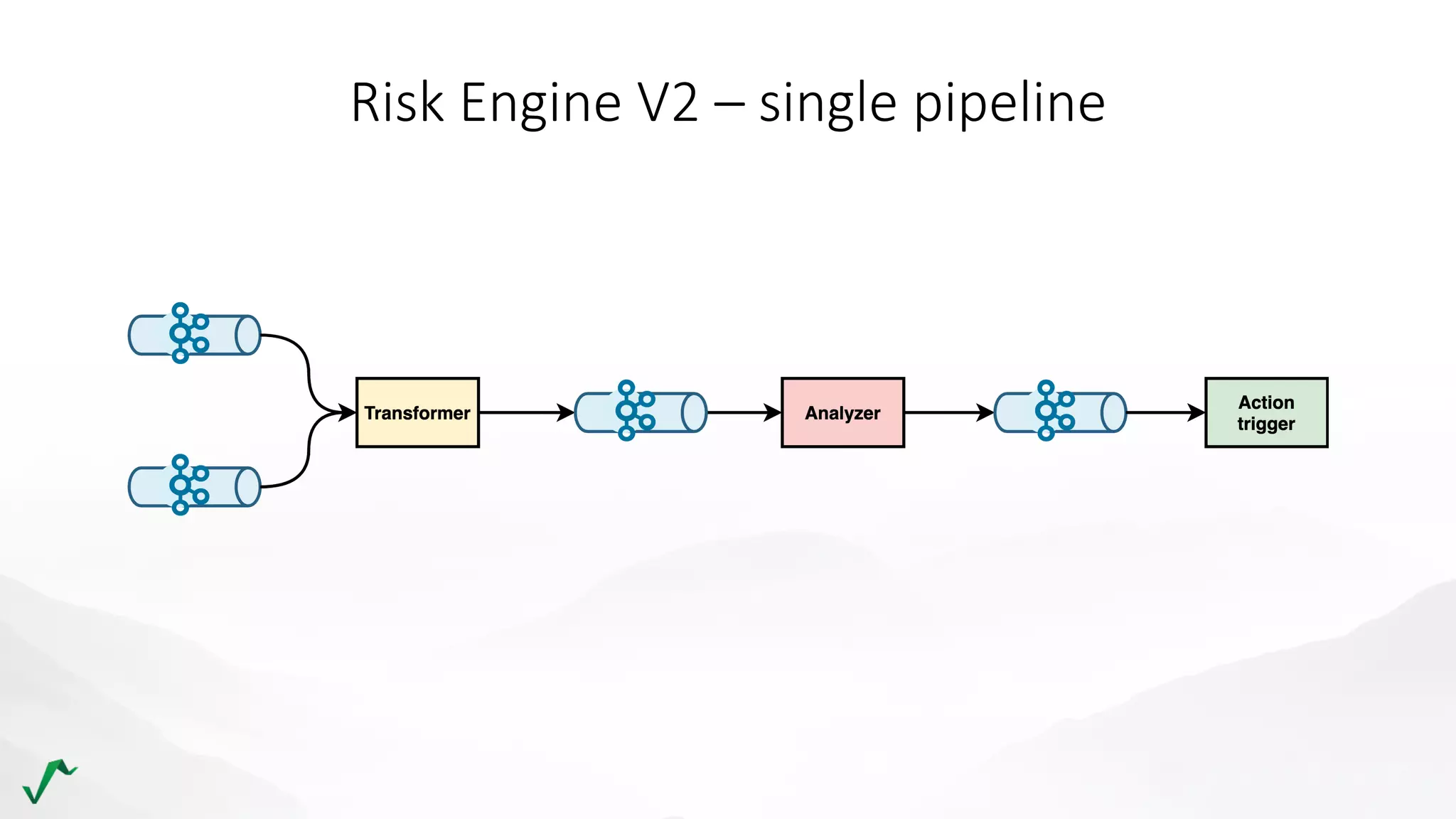
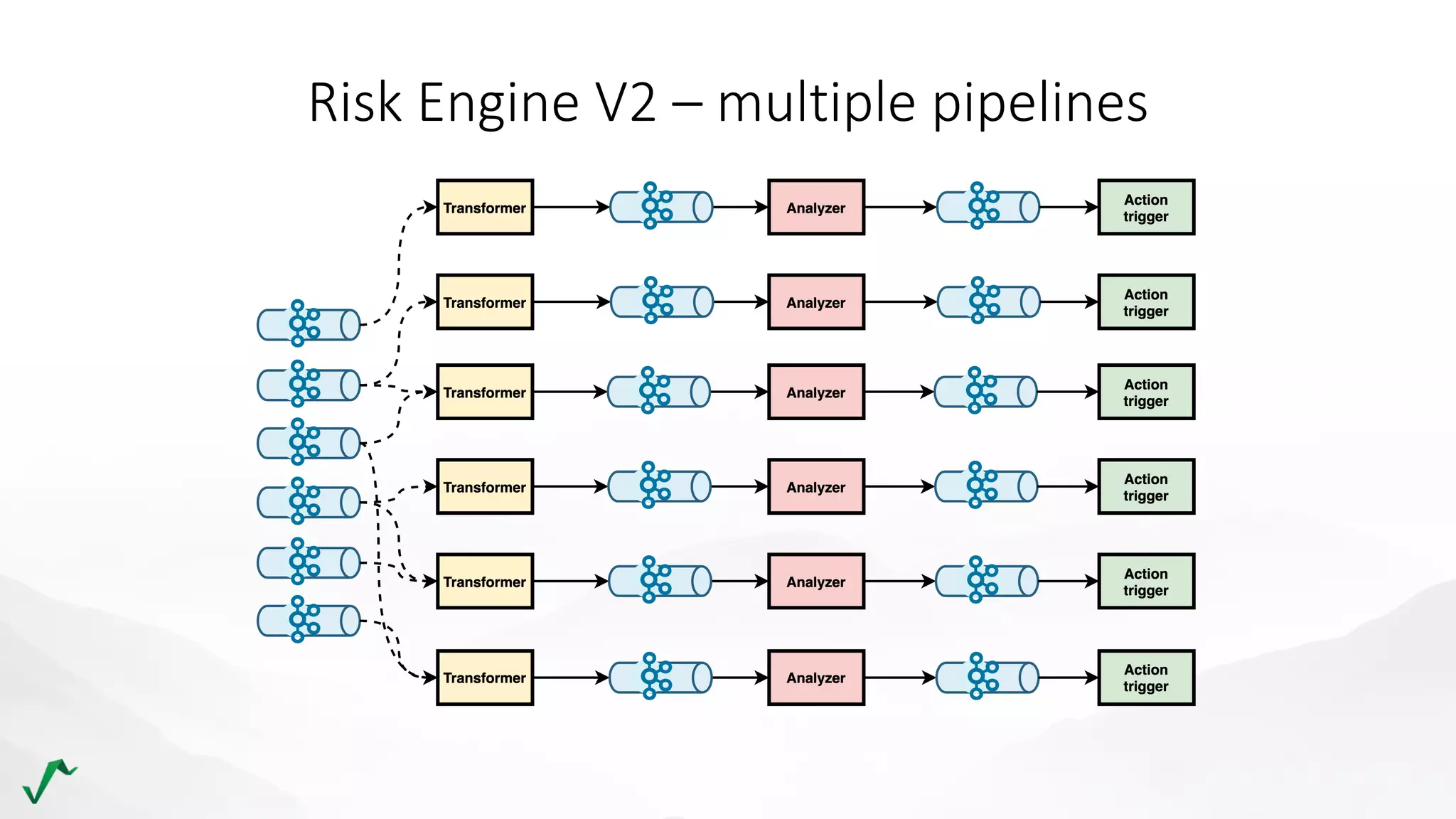
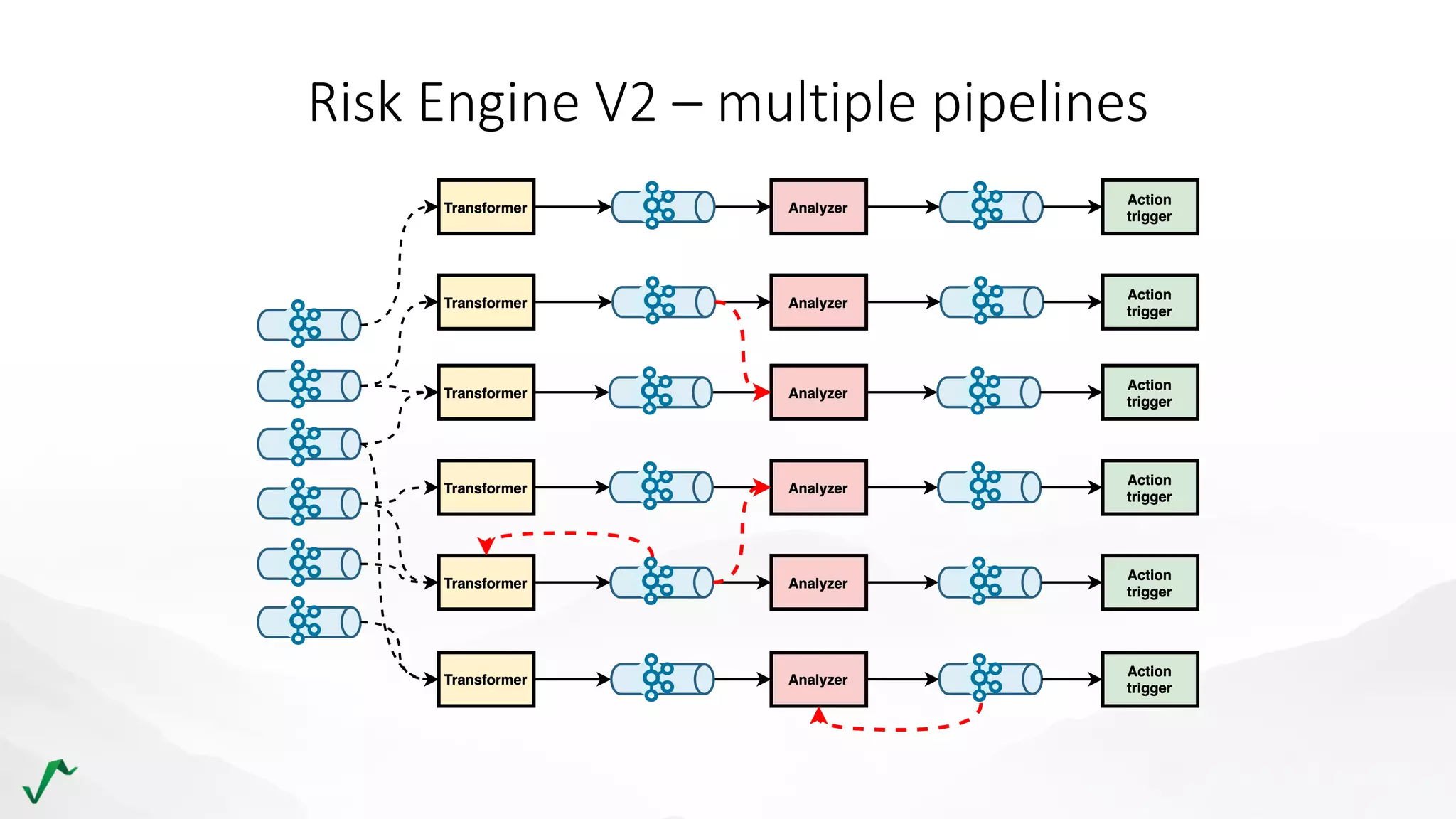
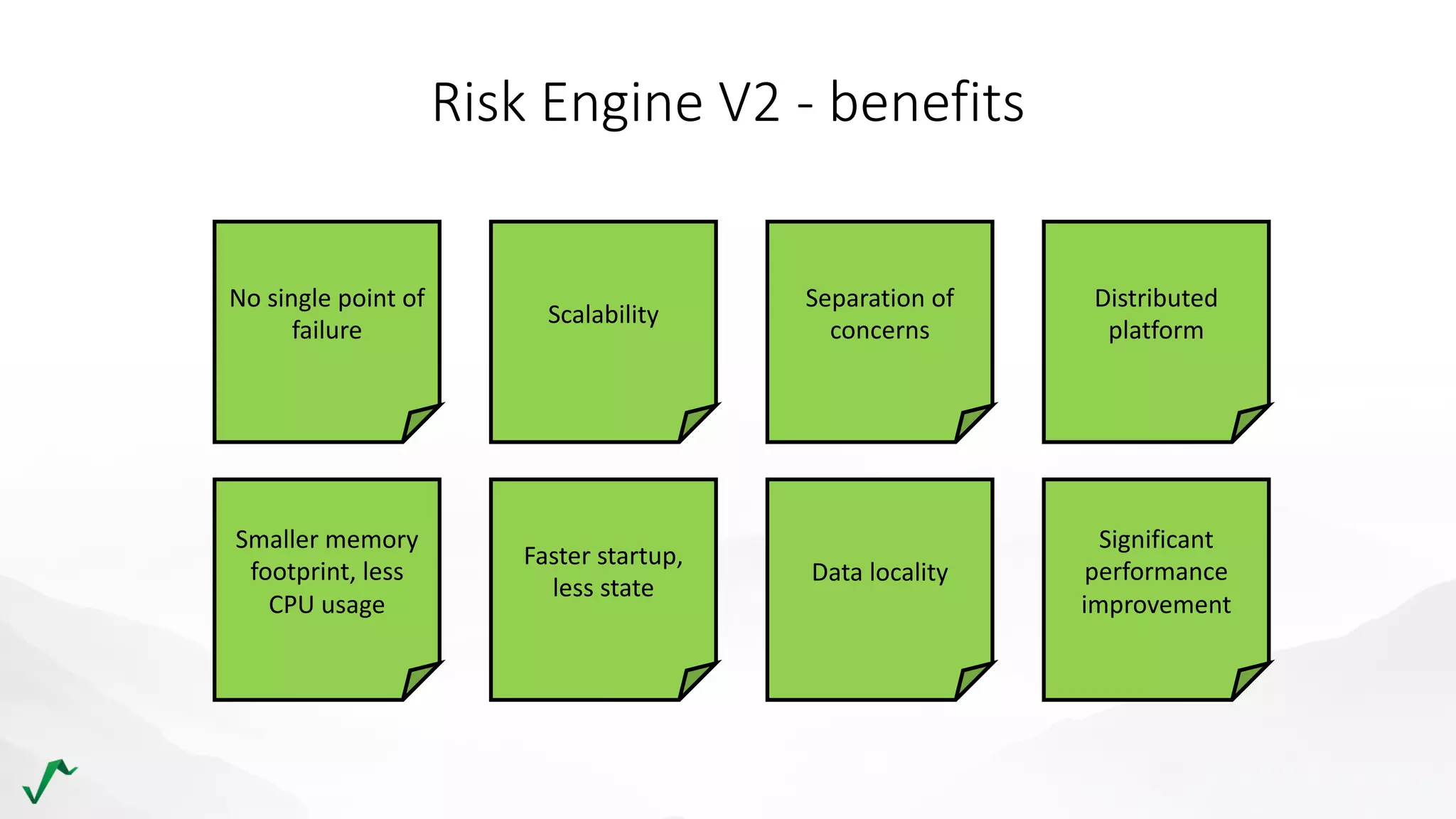
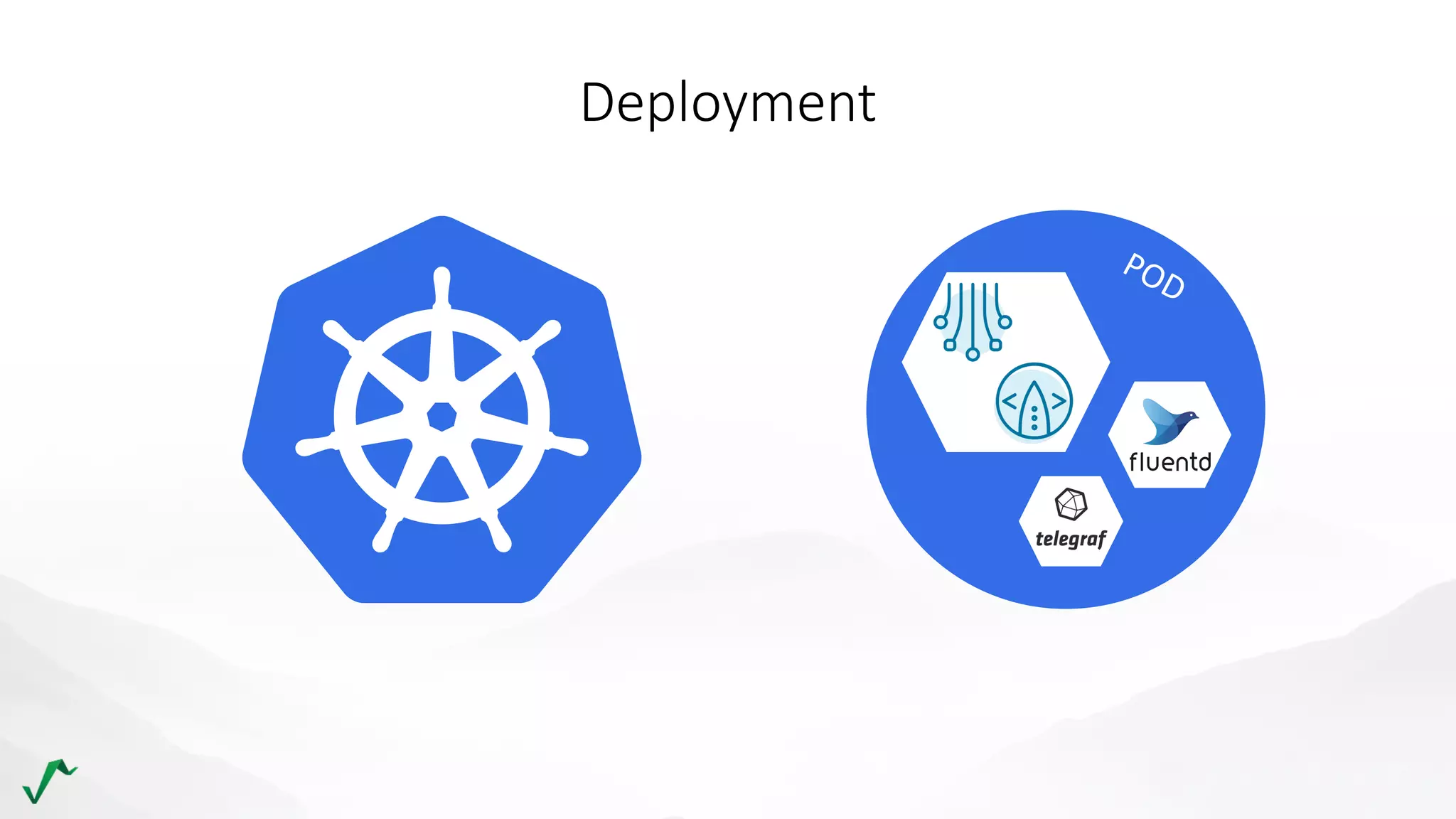
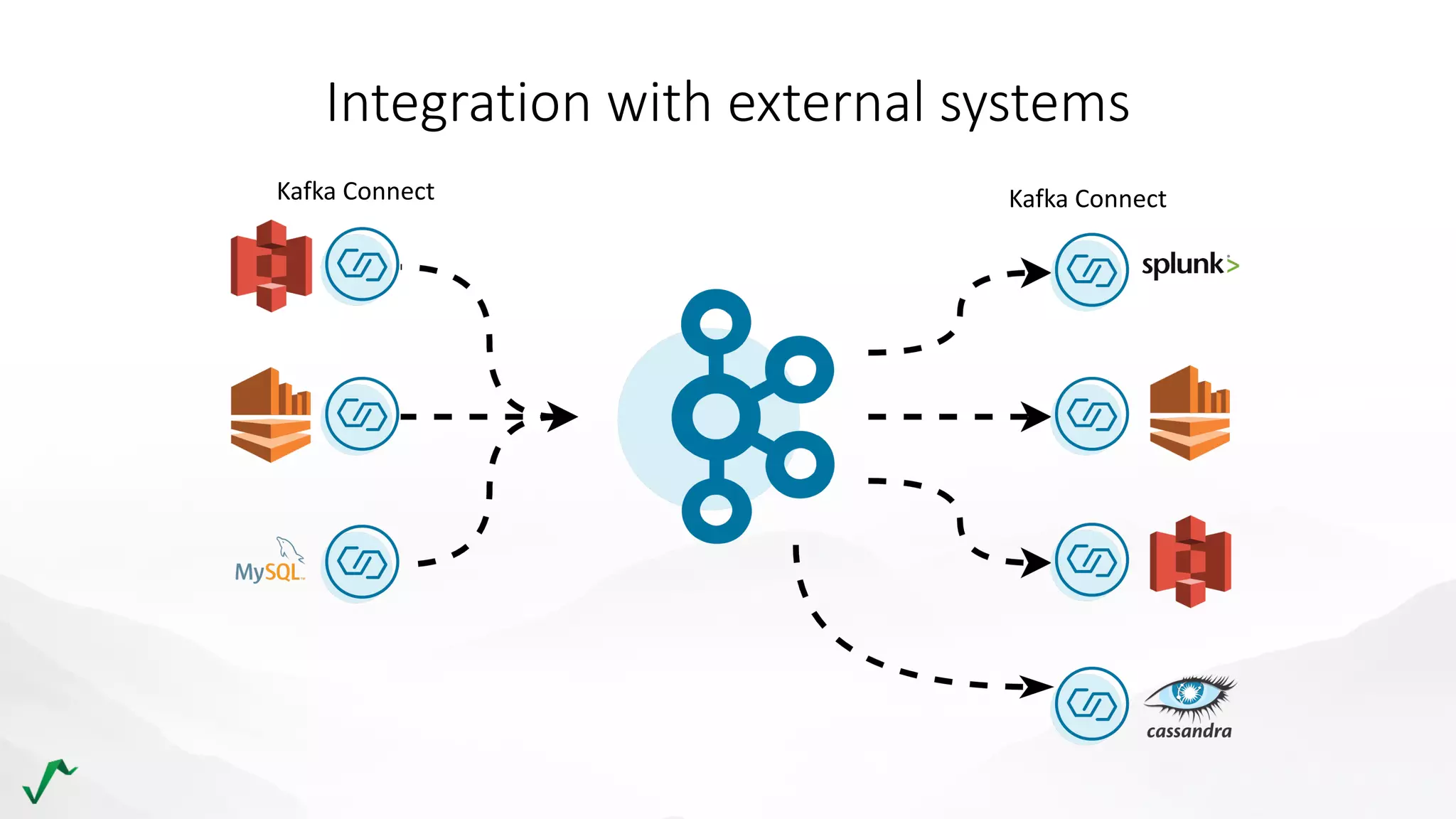
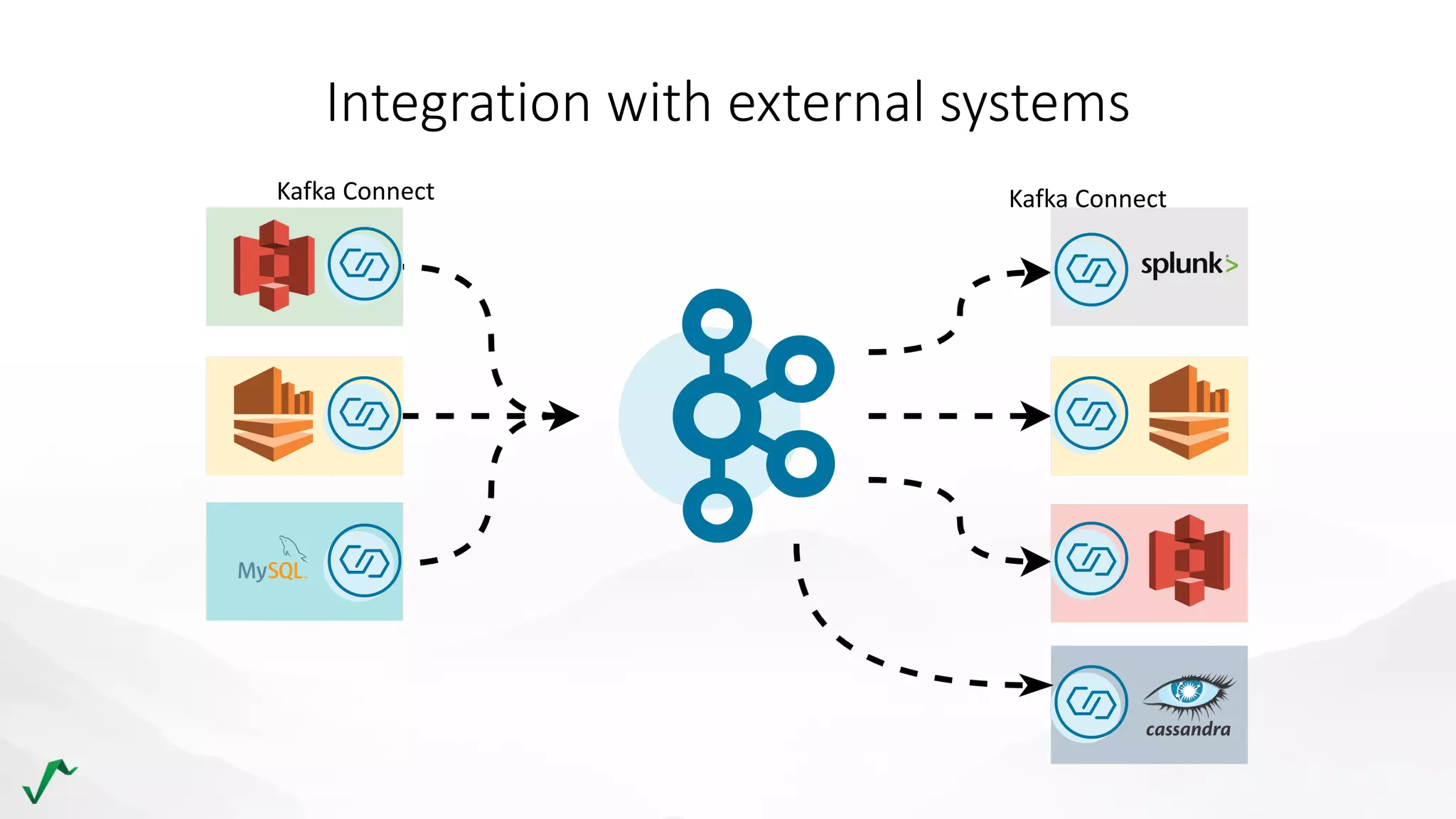
The document discusses risk management in retail through stream processing, focusing on the evolution from a first-generation risk engine to a more efficient, scalable risk engine v2. Key improvements include independent, parallel processing pipelines, reduced memory demand, and enhanced performance. The document highlights the importance of understanding data bottlenecks and emphasizes the separation of concerns in architecture design.