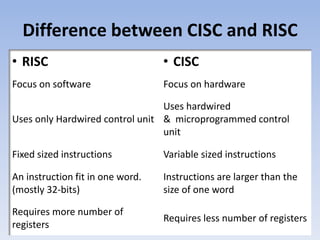
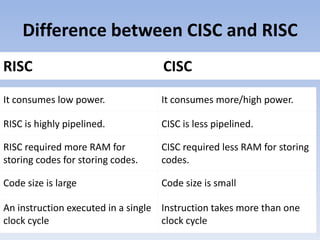
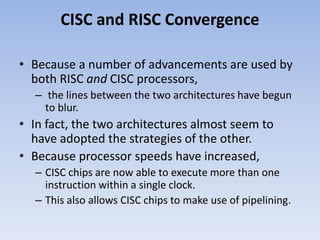
RISC and CISC are two approaches to microprocessor architecture. RISC utilizes a small, highly optimized instruction set where each instruction is simple and can be executed in a single clock cycle. CISC uses more complex instructions that can perform multiple operations in one instruction. While RISC requires more instructions, CISC requires more complex processor design and has longer execution times. Over time, the two approaches have converged as technologies allow CISC processors to better support pipelining and RISC processors to include more complex instructions.