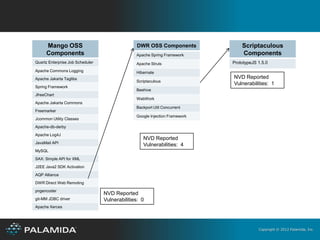
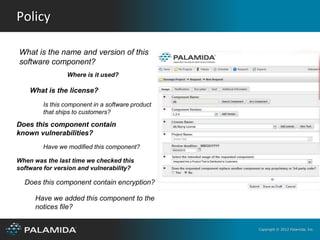
The document discusses open source software, intellectual property, and security. It notes that open source software use has increased dramatically in recent years. While open source can help organizations develop software faster and with smaller budgets, it also poses intellectual property and security risks if not properly governed. The document recommends that organizations establish an open source review board to review and approve policies around externally sourced software and conduct audits to evaluate compliance and risks.
























![Key Questions to Ask…
• How High is the Bar?
• What is “Good Enough”?
• Have You Scanned Everything? [Probably Not!]
• What’s Out There That’s Hard, But Important?
Copyright © 2012 Palamida, Inc.](https://image.slidesharecdn.com/intersectionv2-120522141559-phpapp02/85/Palamida-Open-Source-Compliance-Solution-30-320.jpg)


![Have You Scanned Everything [Probably Not]?
• Java: Maven becoming more prevalent
• C/C++/etc…: Github remote repositories
• Commercial Source compiled on laptop
• Binary analysis bar is being raised
• Where did all these binaries come from? 1000 to 10,000+
• More naïve companies requiring scans / Bad Advice
• Web services
• Post acquisition discovery of missing code
Copyright © 2012 Palamida, Inc.](https://image.slidesharecdn.com/intersectionv2-120522141559-phpapp02/85/Palamida-Open-Source-Compliance-Solution-33-320.jpg)