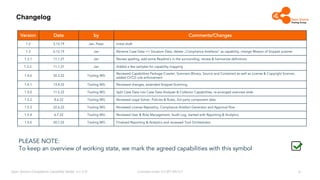
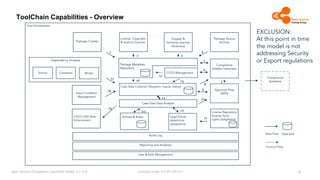
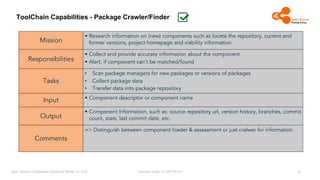
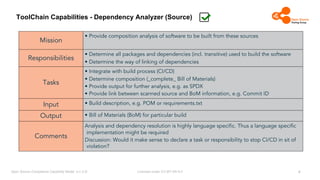
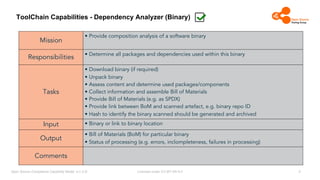
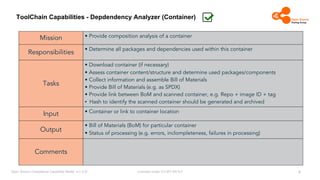
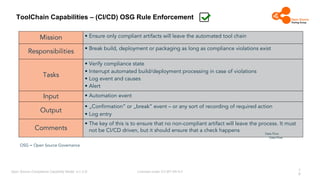
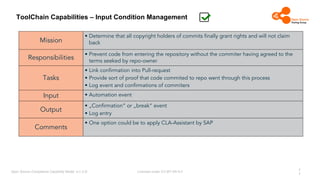
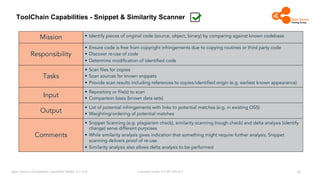
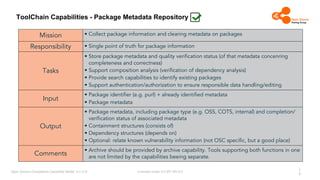
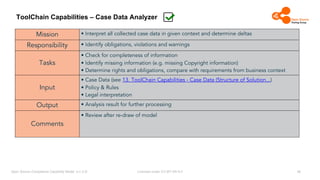
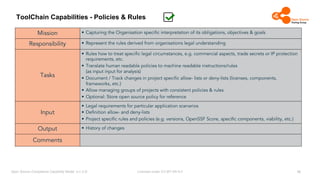
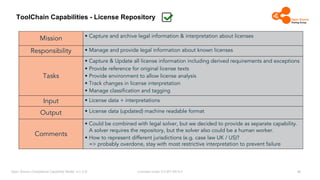
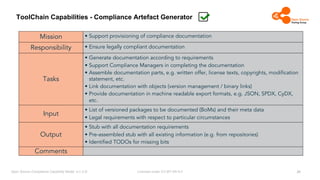
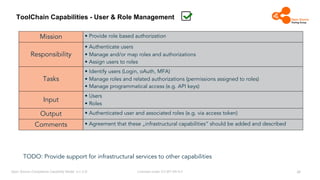
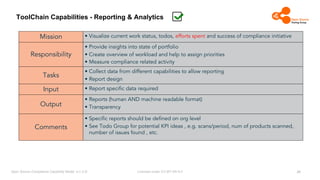
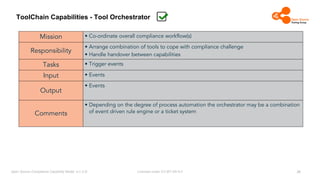
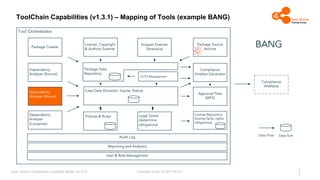
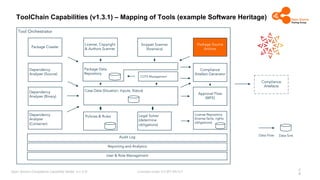
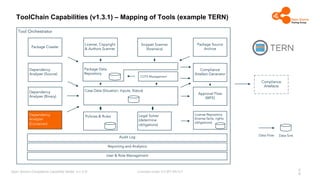
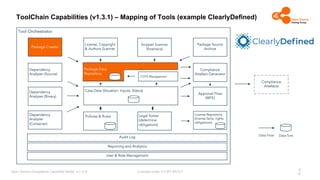
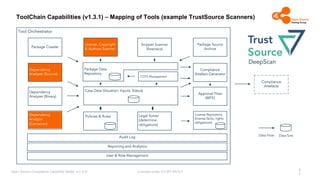
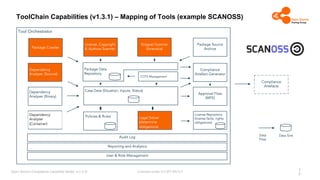
The document outlines the Open Source Compliance Capability Model (v1.5.5) developed by the Open Chain Tooling Workgroup, detailing a range of toolchain capabilities essential for managing open source compliance. It includes a changelog of revisions, descriptions of various capabilities such as license and copyright scanning, dependency analysis, and case data collection, along with requirements for traceability and compliance. Additionally, it clarifies the responsibilities and tasks associated with each capability, emphasizing the importance of compliance documentation and legal data management.