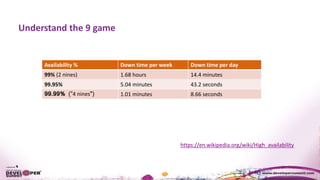
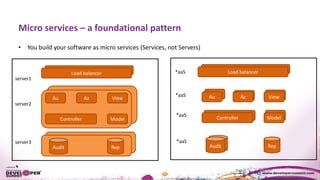
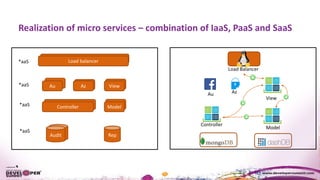
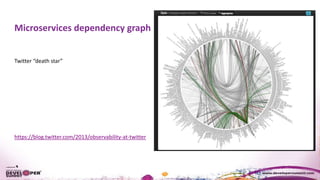
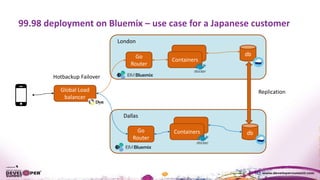
The document discusses the importance of resiliency in cloud-deployed applications, highlighting the increasing reliance on cloud services across various industries, including traditional enterprises. It emphasizes the significance of achieving high availability beyond 99.99% for mission-critical applications and presents architectural patterns like microservices, retry mechanisms, and circuit breakers to enhance application resilience. Best practices and tools for deploying on cloud platforms are also outlined to assist organizations in mitigating downtime and improving overall performance.