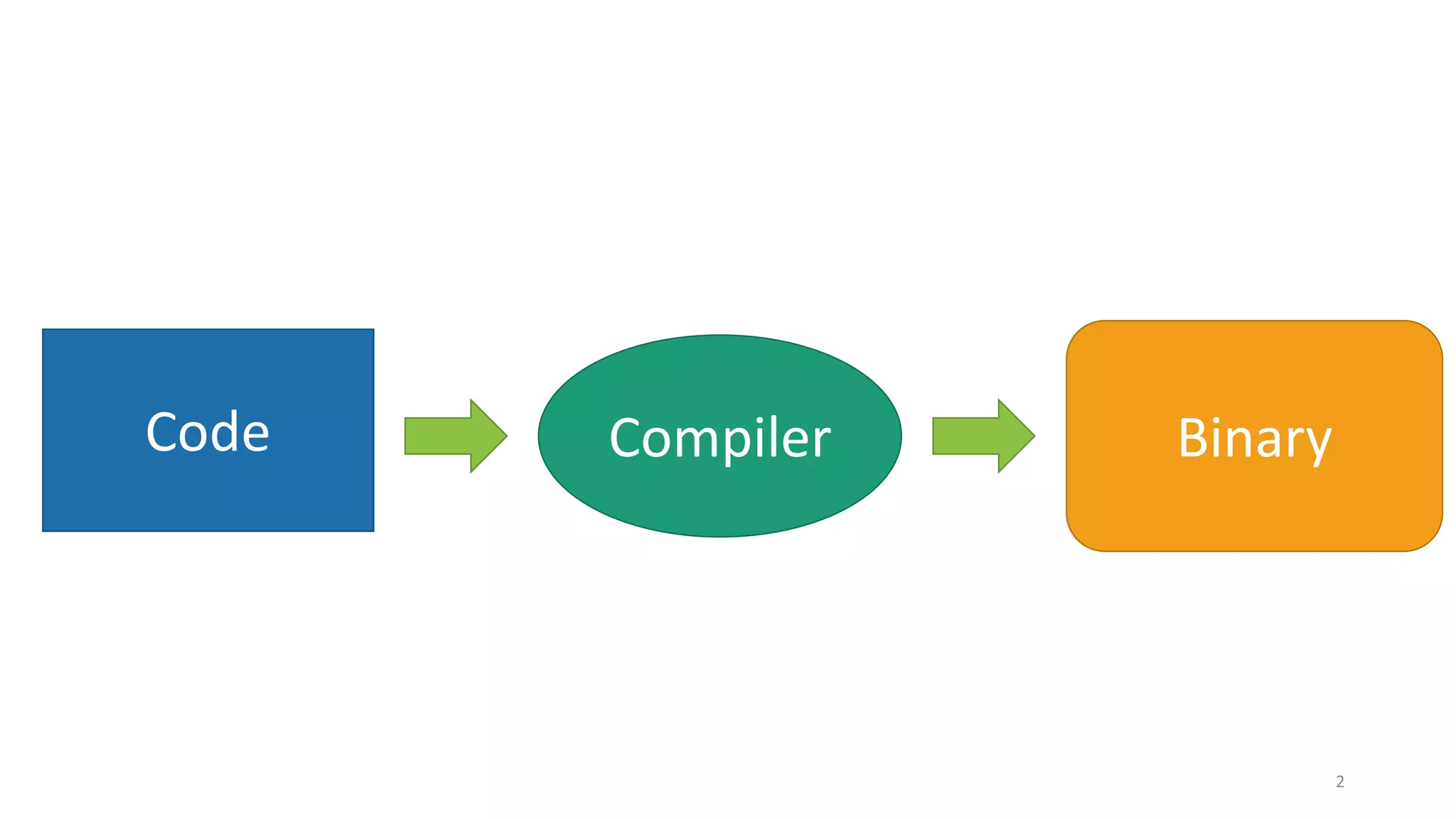
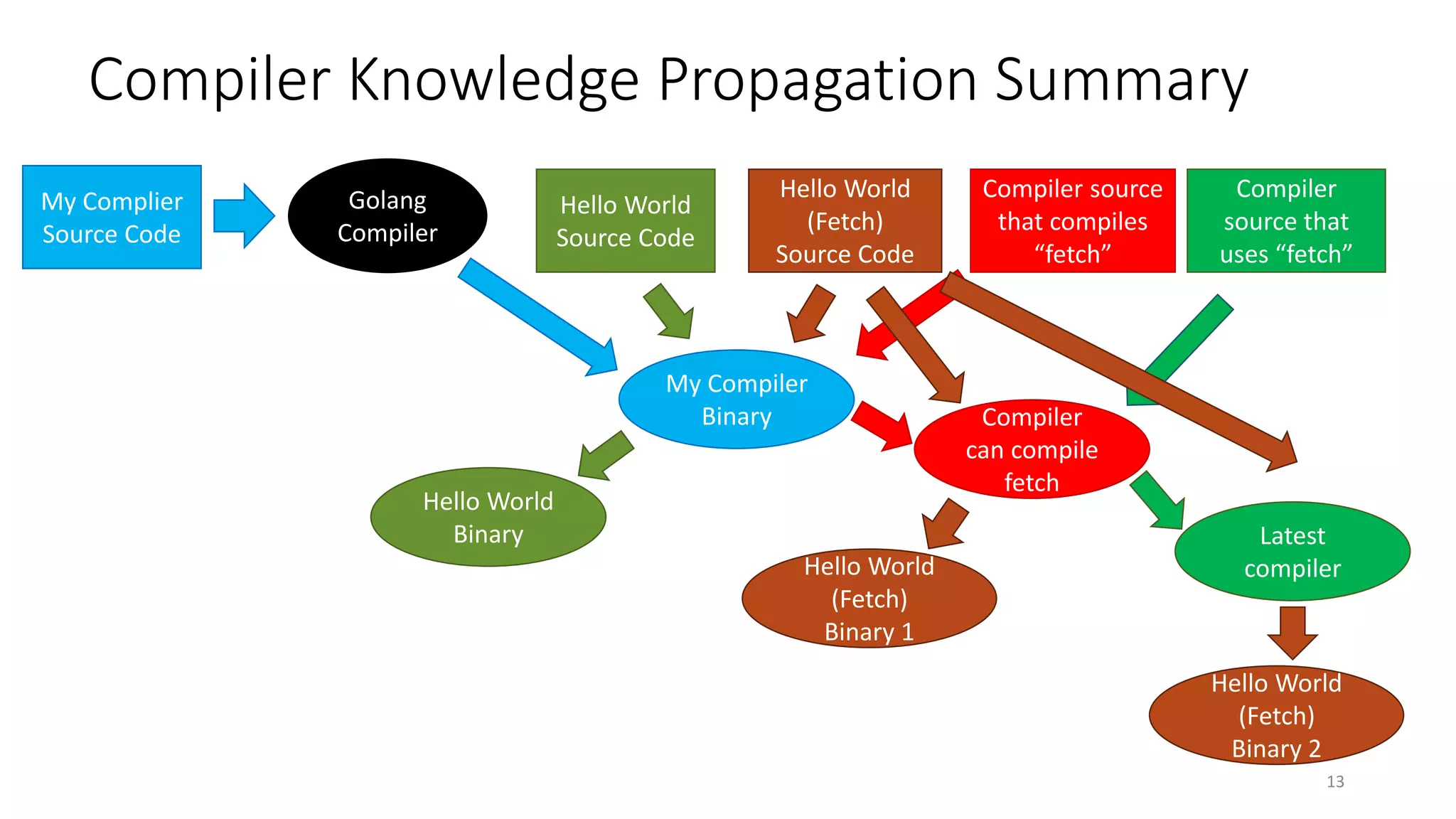
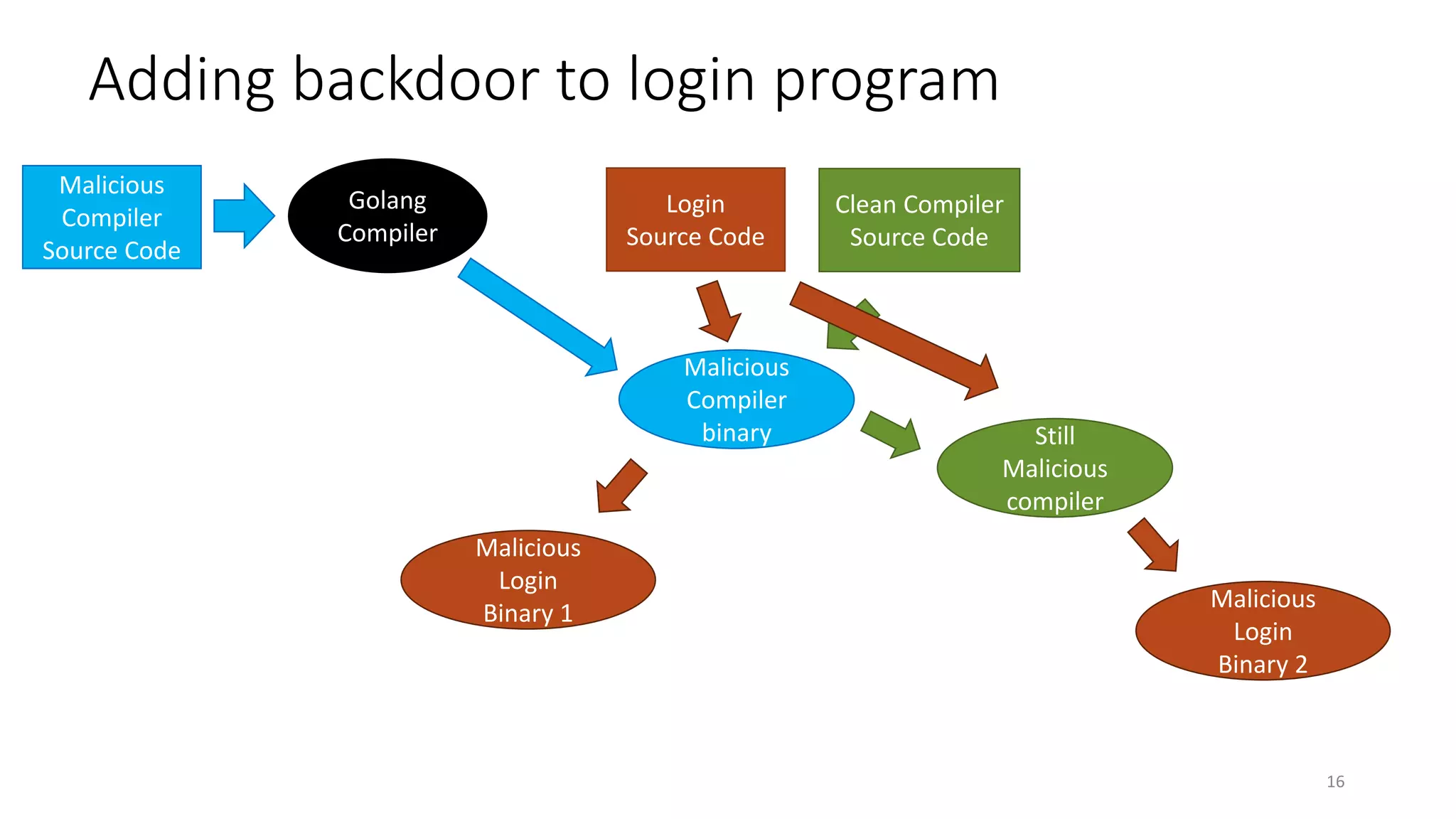
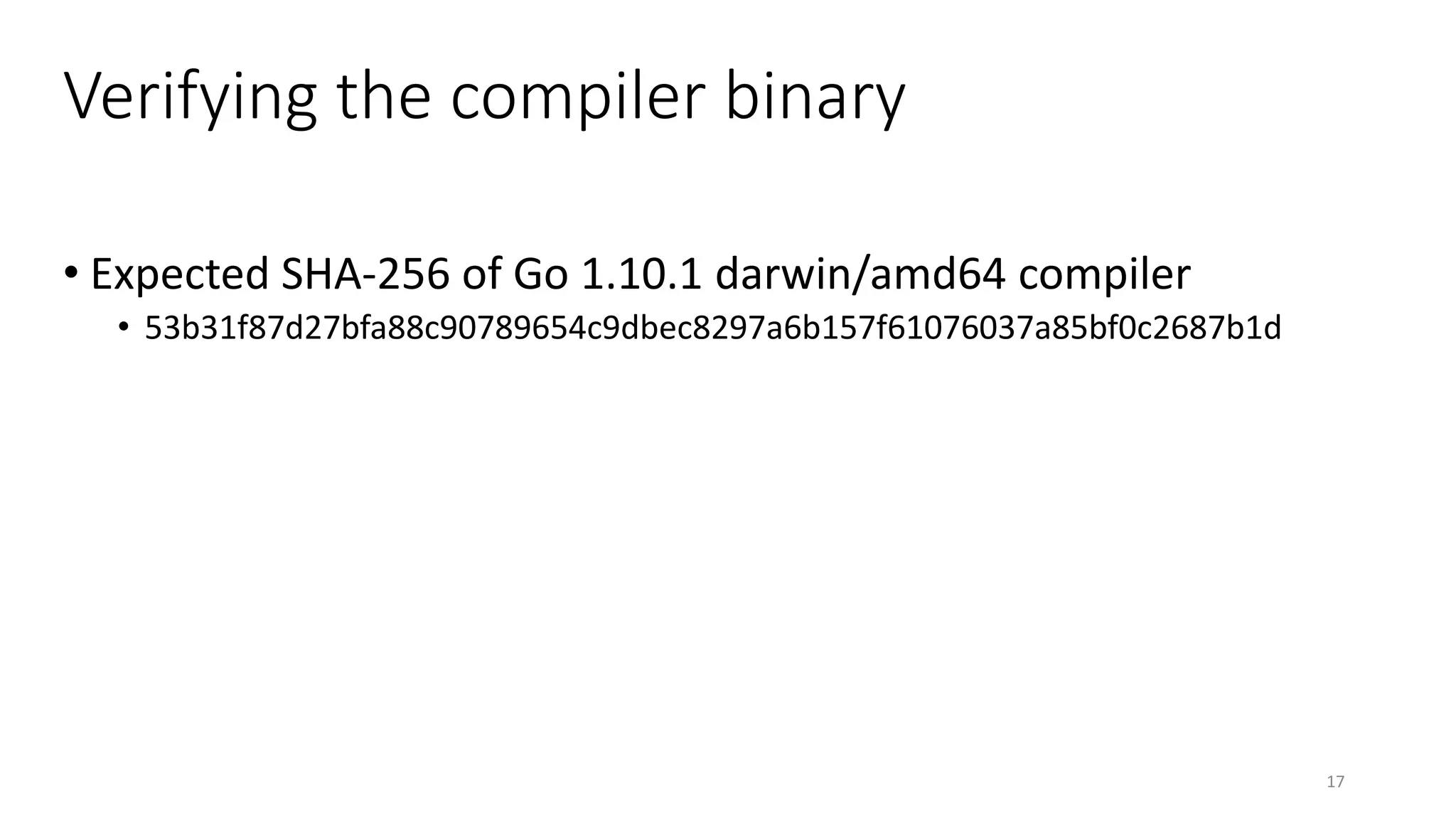
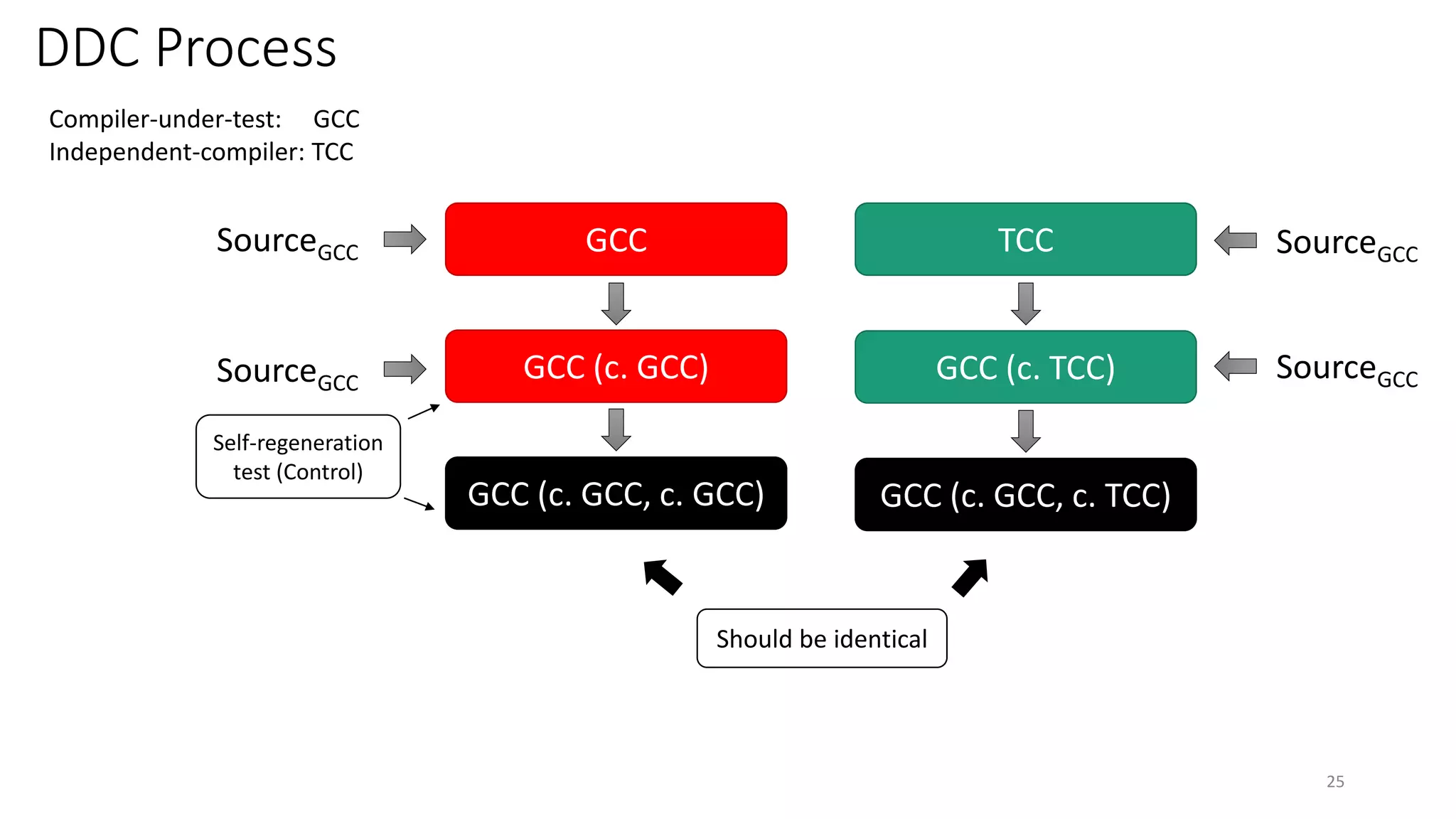
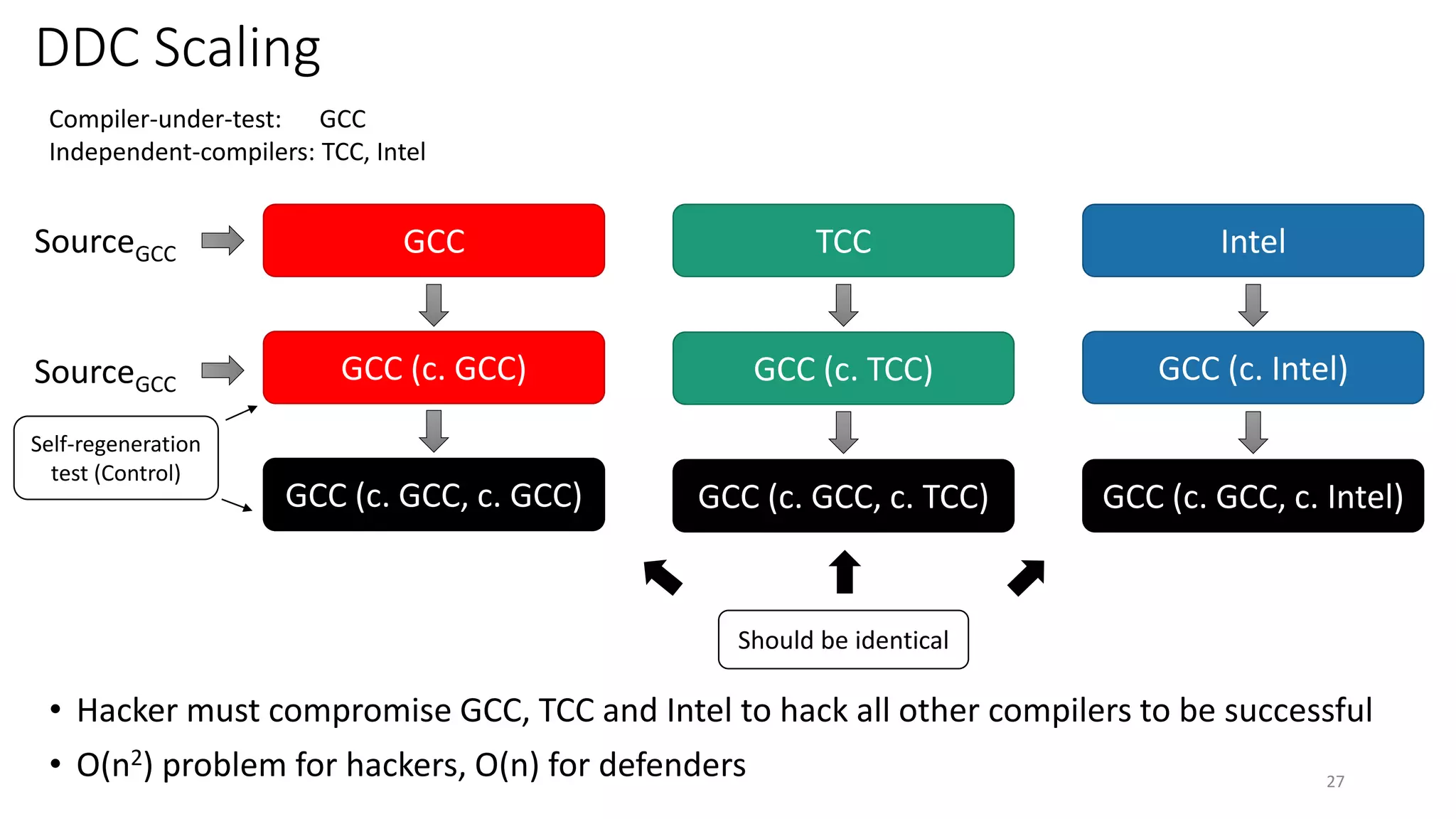
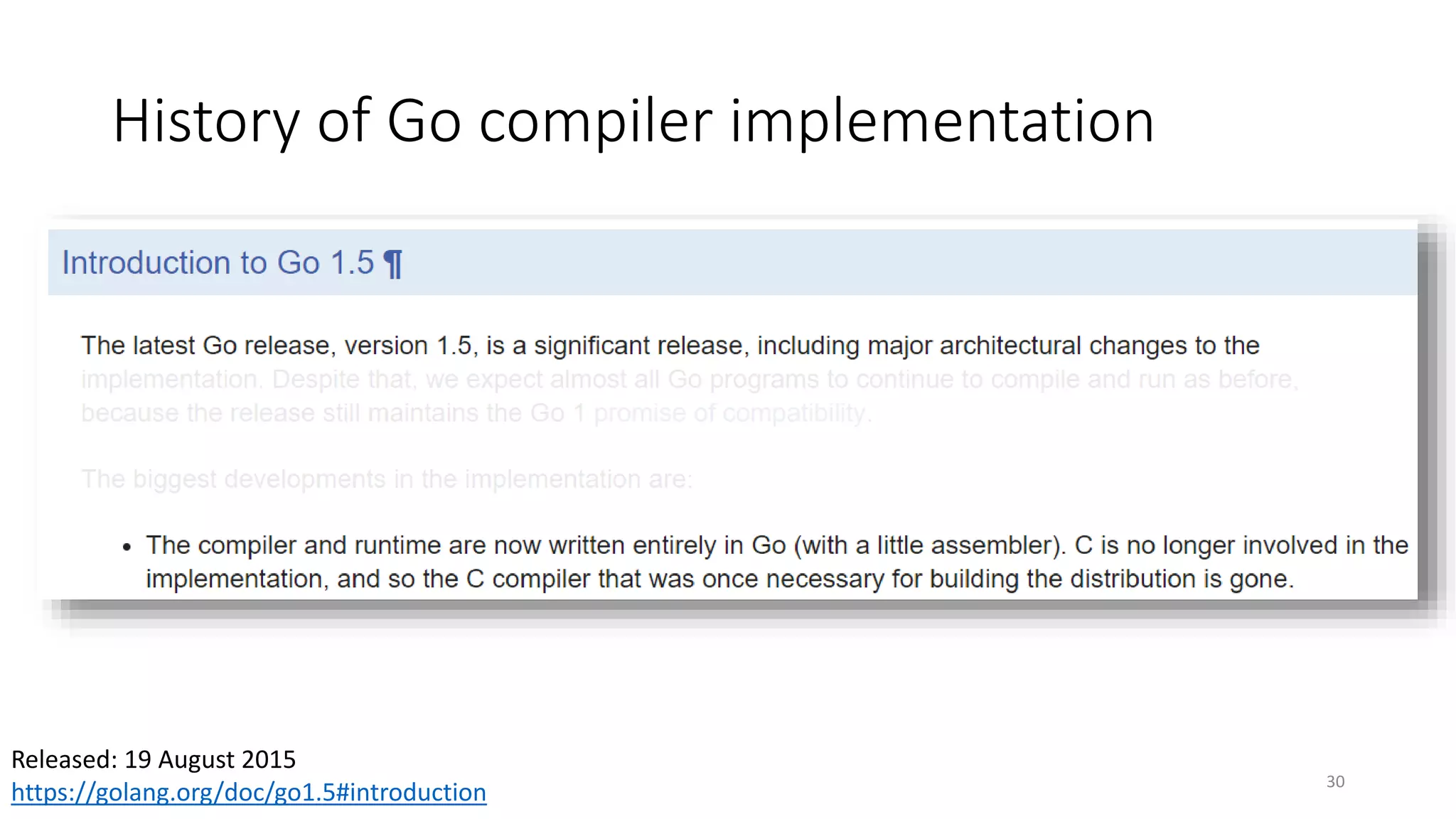
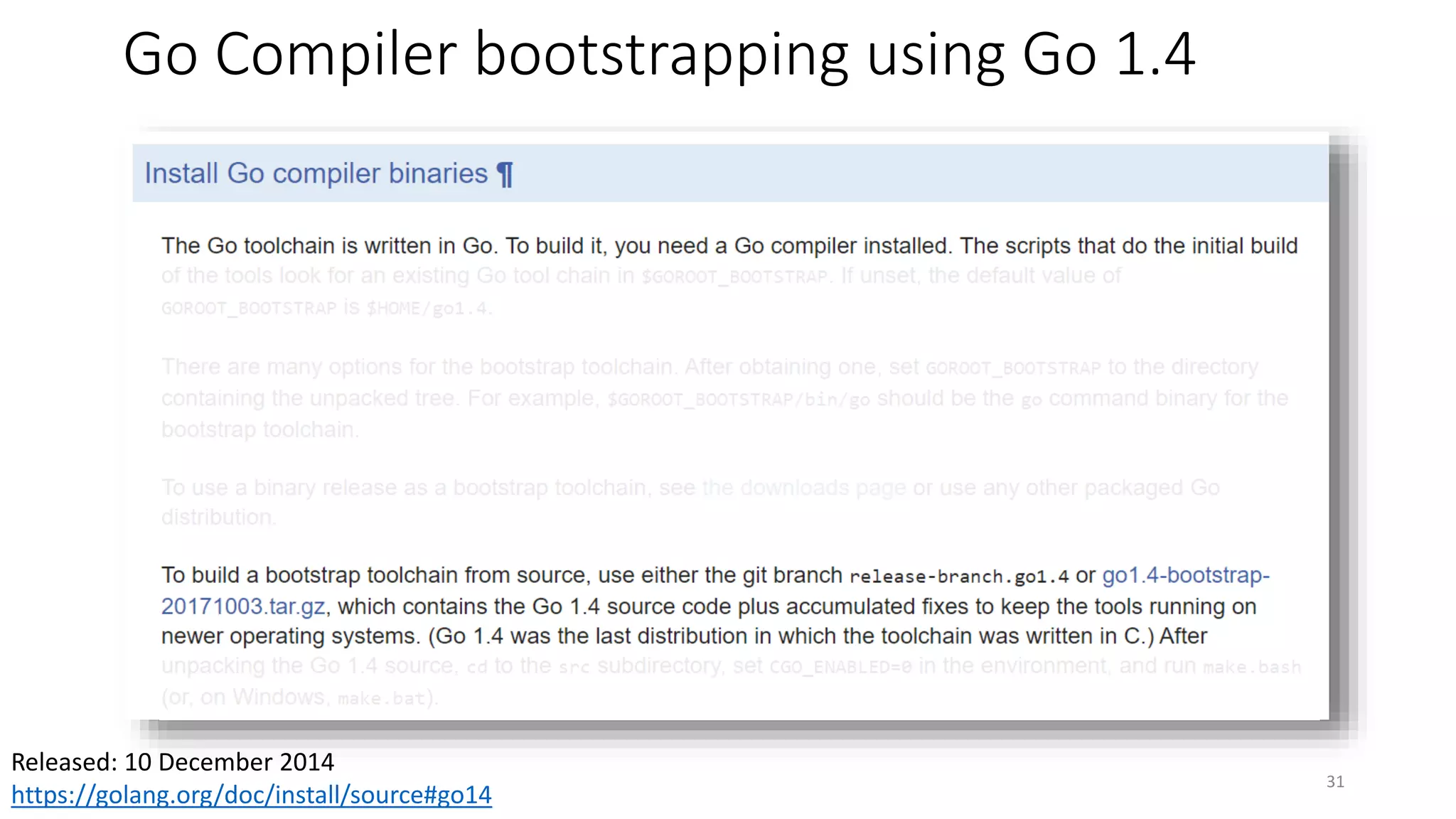
This document summarizes Ken Thompson's 1984 lecture "Reflections on Trusting Trust" and discusses how a malicious actor could subvert the trust in compilers by creating a self-propagating virus in the compiler code. It outlines how an attacker could introduce an undetectable backdoor into programs by first creating a self-reproducing "Quine" program and then using compiler bootstrapping to propagate the malicious logic through compiler iterations. Finally, it discusses the "Diverse Double Compiling" defense proposed by David Wheeler, which uses multiple independent compilers to verify each other in order to detect such compiler subversion attacks.