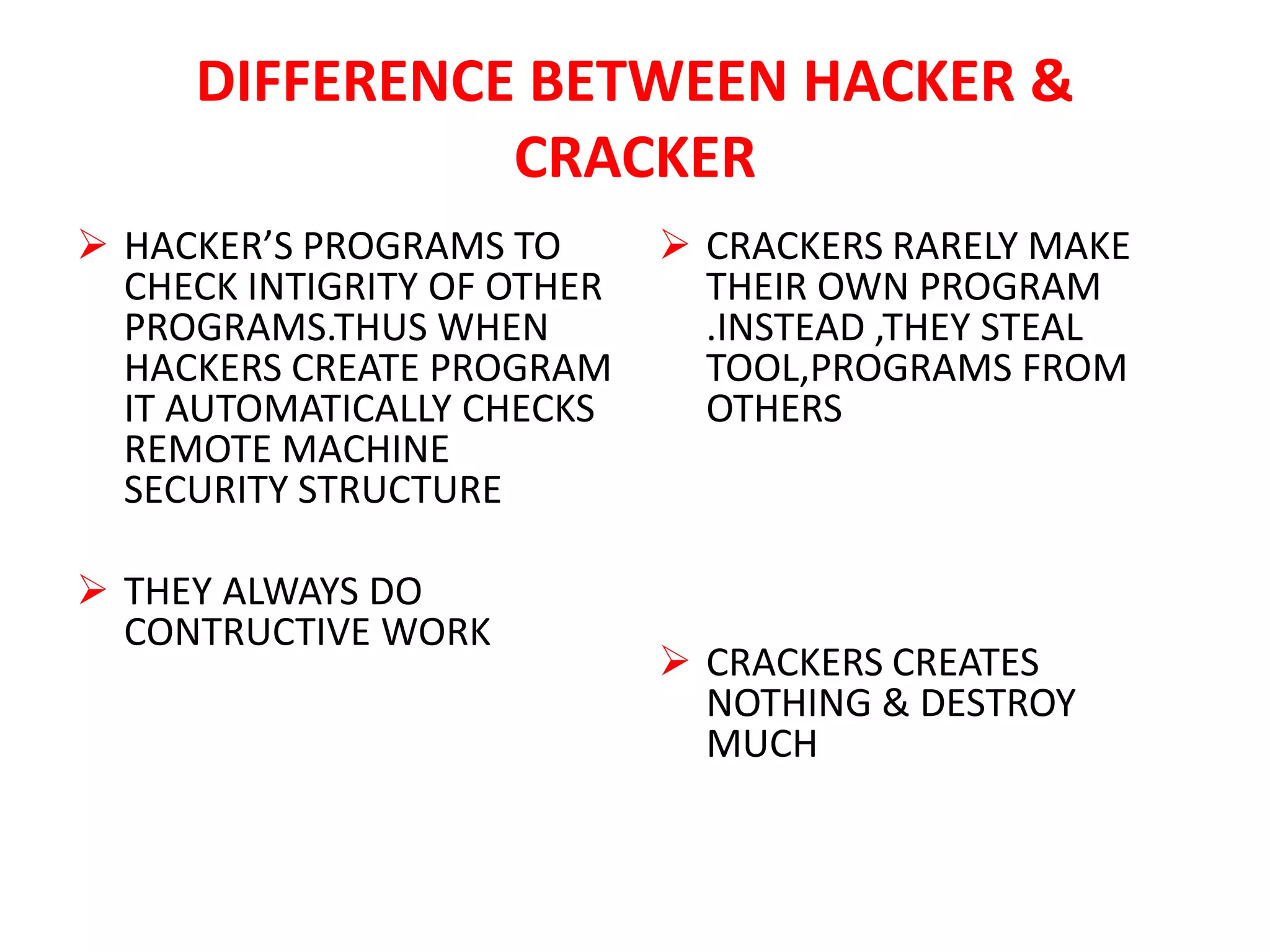
This document provides an introduction to network security and hacking. It discusses that network security involves policies, procedures, laws, human behavior, and technical aspects. It defines hacking as attempting to gain unauthorized access to computer resources, and distinguishes between hackers and crackers. Hackers use their skills constructively and never damage data, while crackers enter systems violently and cause damage. The document also discusses the operating systems commonly used by hackers, including Sun, Unix, and Microsoft.