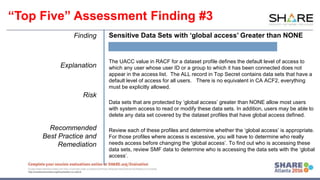
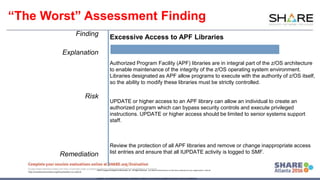
The document outlines the top security assessment findings related to mainframe security, particularly focusing on vulnerabilities such as excessive user access, poorly protected libraries, and inadequate user ID conditions. It emphasizes the need for proper configuration and monitoring of user access to sensitive data, and presents best practices for remediation. The document also highlights the skills and knowledge required for effective penetration testing and security auditing within mainframe environments.