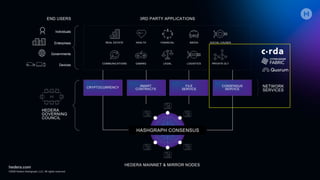
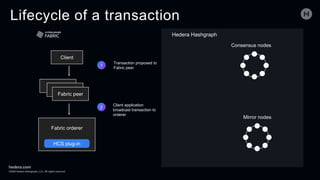
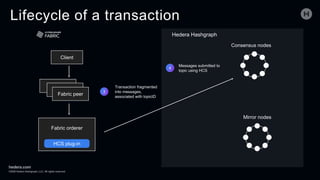
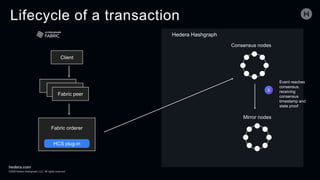
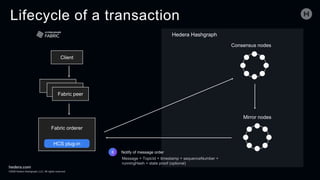
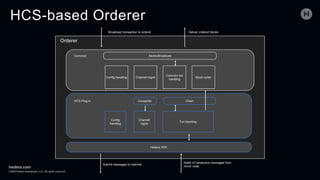
The document discusses the Hedera Consensus Service (HCS), highlighting its features of combining decentralization of a public network with the privacy controls of a private one. It outlines the integration capability with other frameworks like Hyperledger Fabric and Corda, as well as providing a lifecycle of transactions through various components in HCS. Furthermore, it covers the advantages and disadvantages of public versus private networks, focusing on aspects like privacy, performance, and governance.