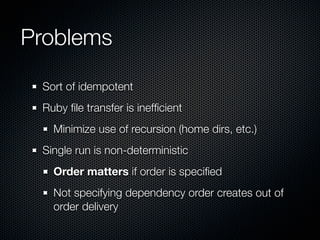
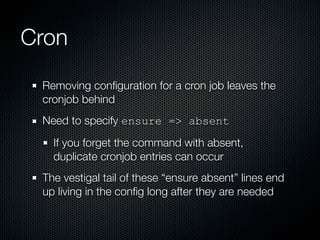
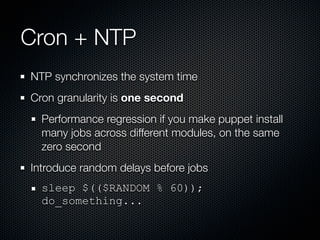
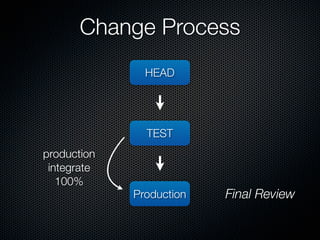
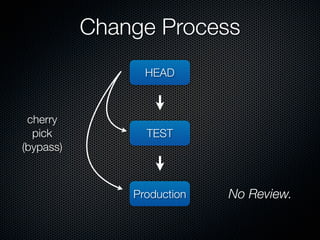
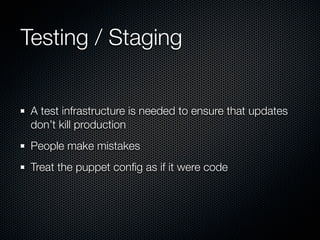
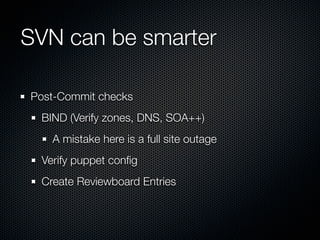
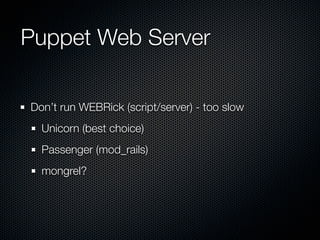
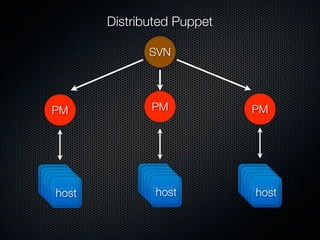
This document summarizes challenges with scaling Puppet configuration management to large environments and proposes solutions. Key issues include: lack of idempotency; inefficient file transfers; non-deterministic single runs; difficulty reviewing changes with many admins; security risks from uncontrolled SVN access; incomplete conditionals in the Puppet DSL; leftover cron jobs when ensuring absence; performance issues when configuring many cron jobs at once; lack of testing facilities; inability to easily retrieve node configurations; problems removing nodes or classes; and lack of an ad hoc scripting capability or distributed architecture. The document proposes solutions such as enforcing review processes; restricting SVN access; adding post-commit checks; managing branches; using Review Board; separating user/system accounts; implementing