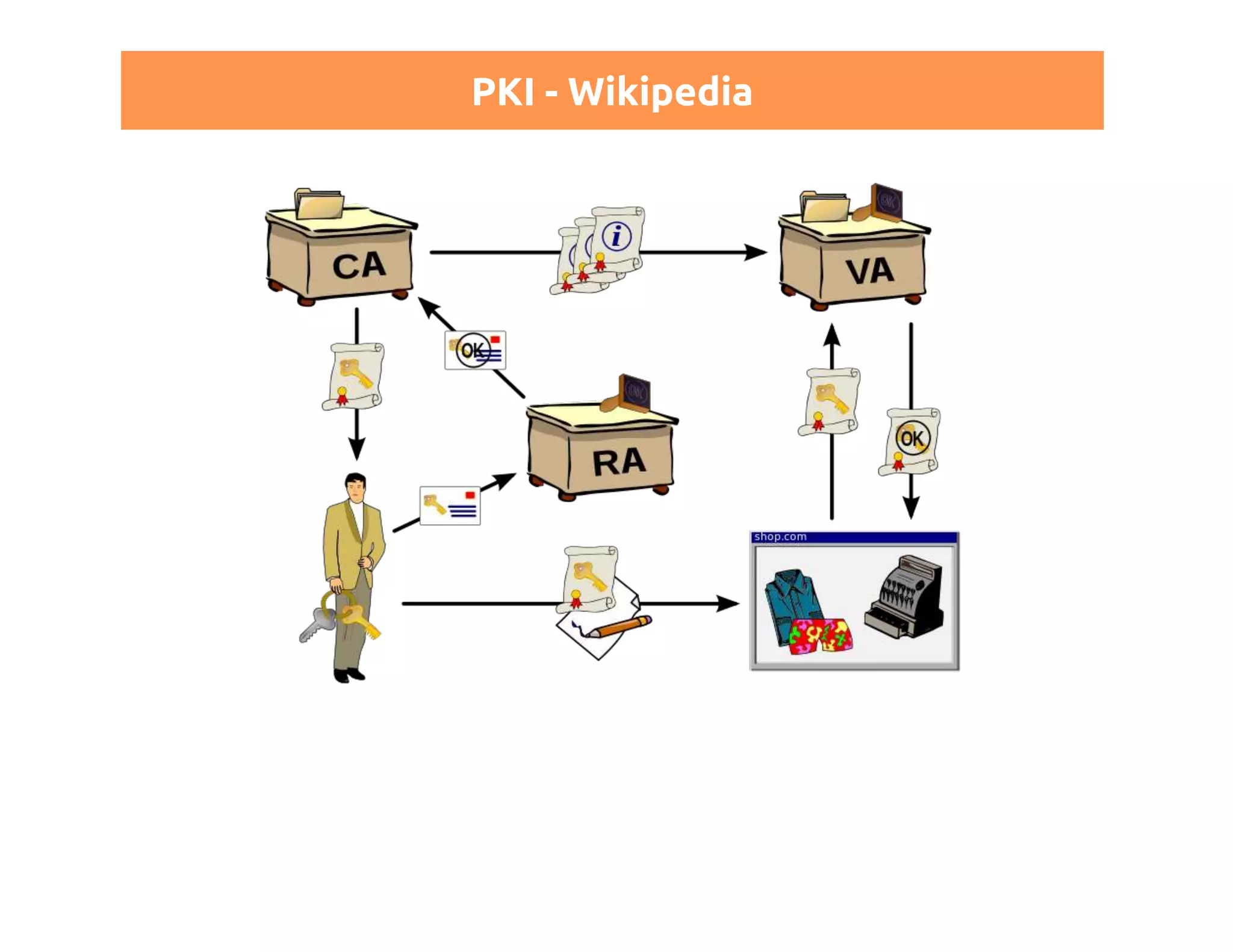
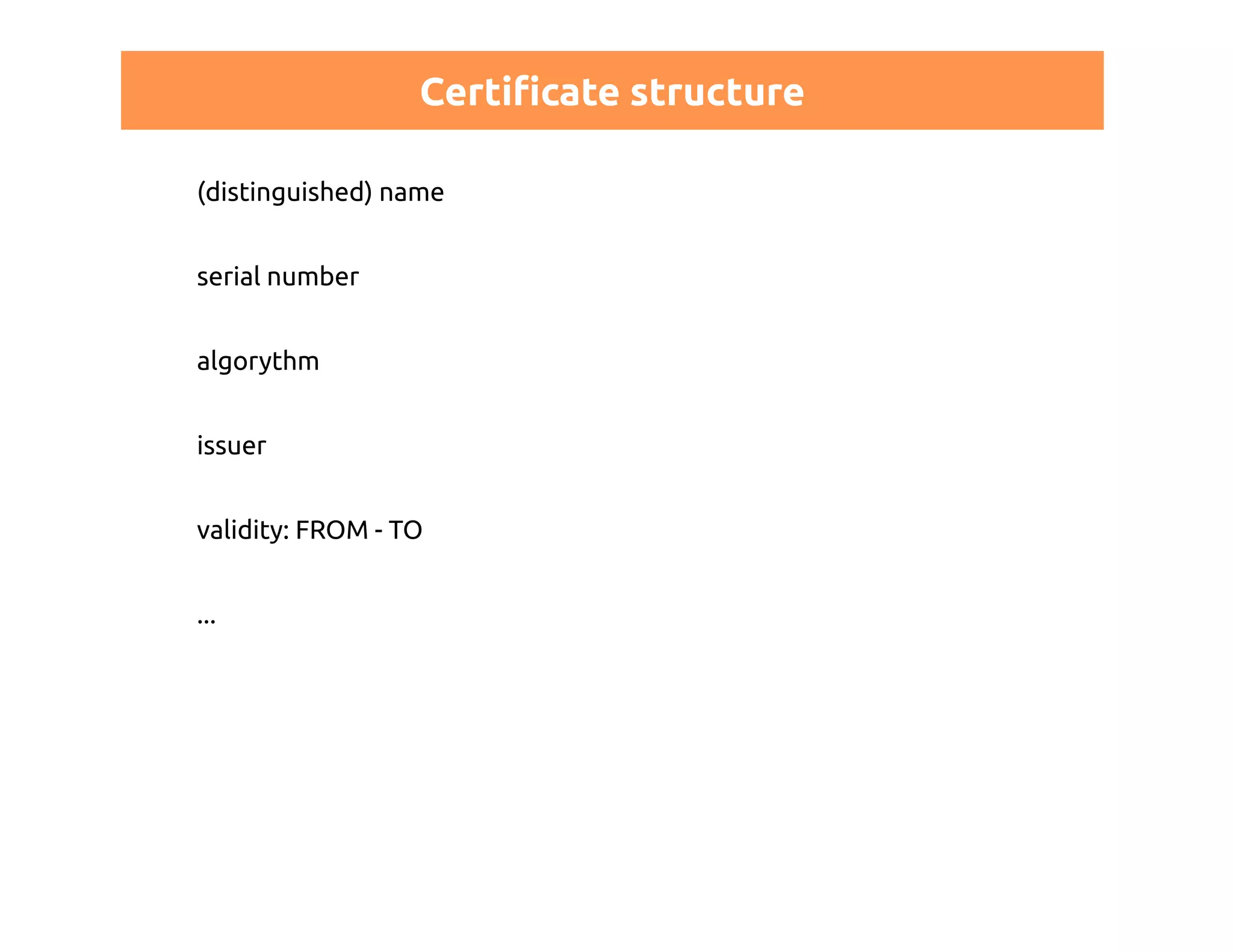
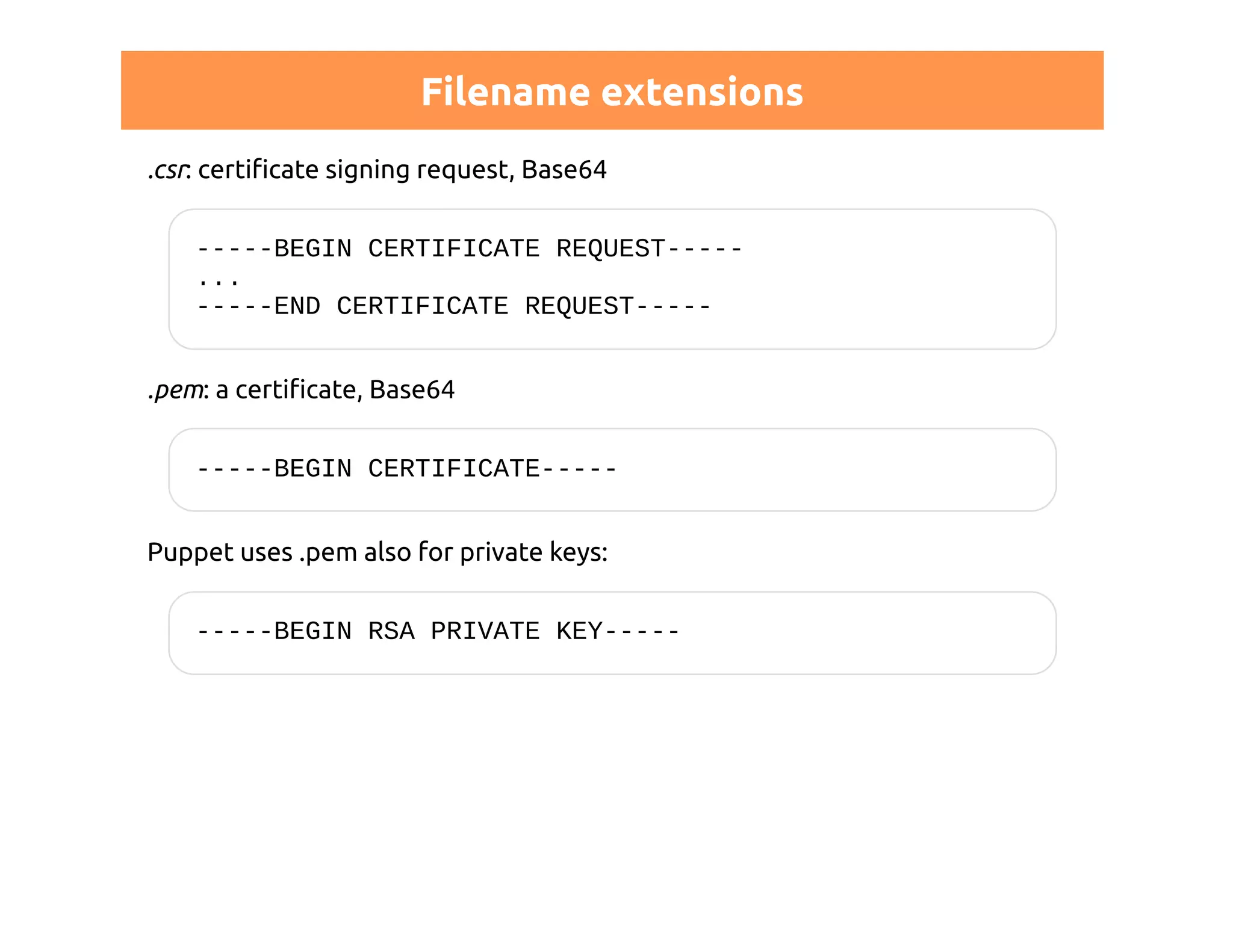
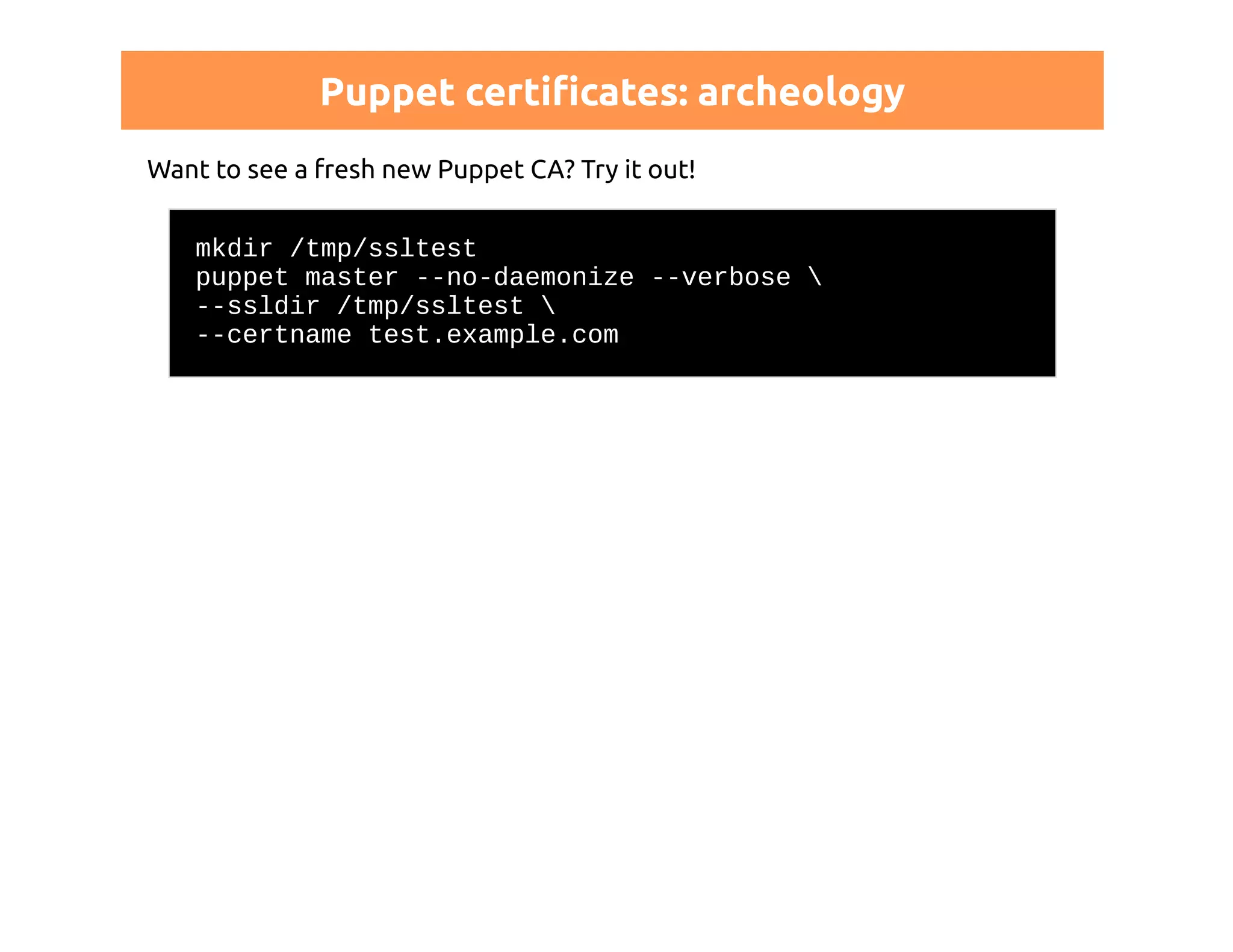
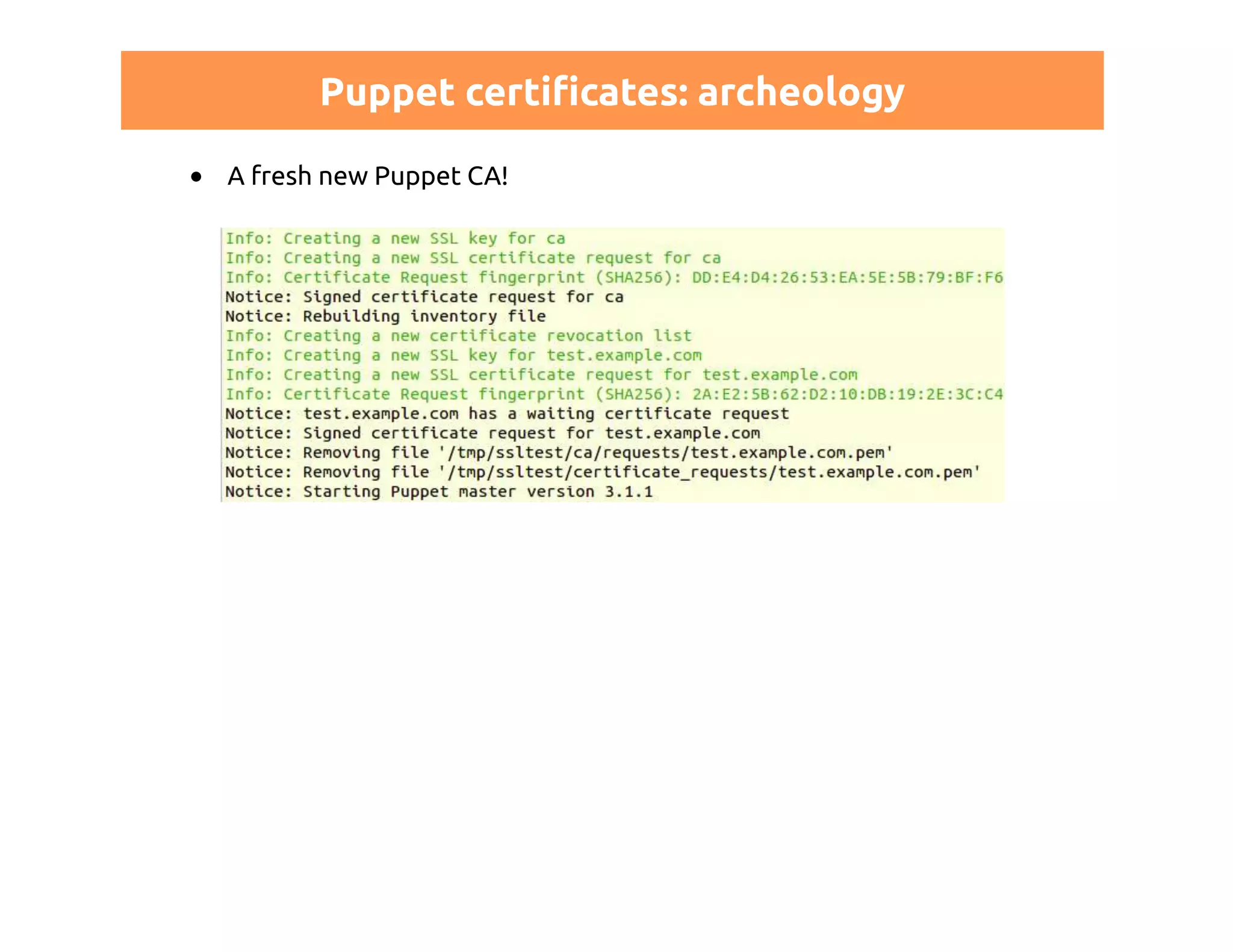
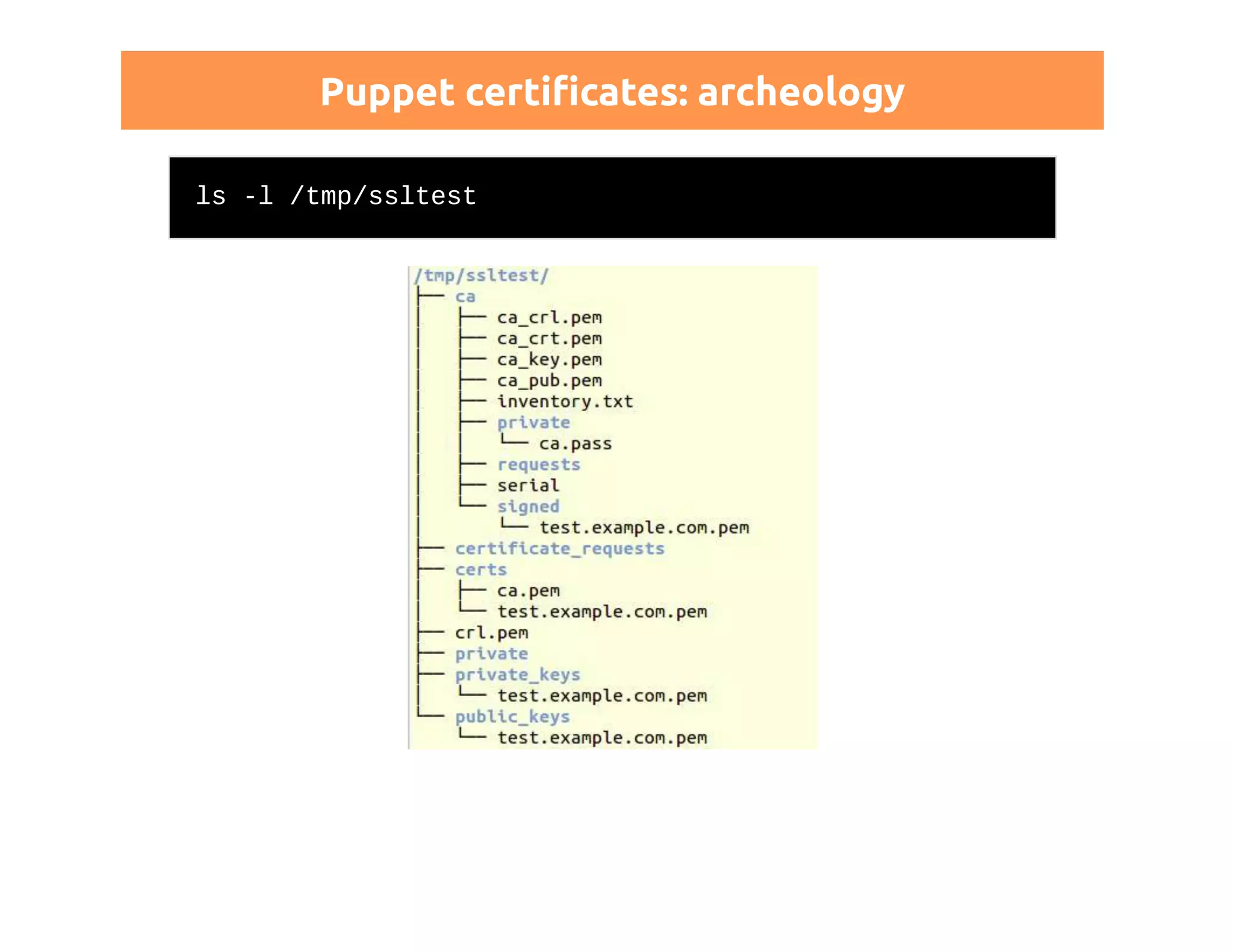
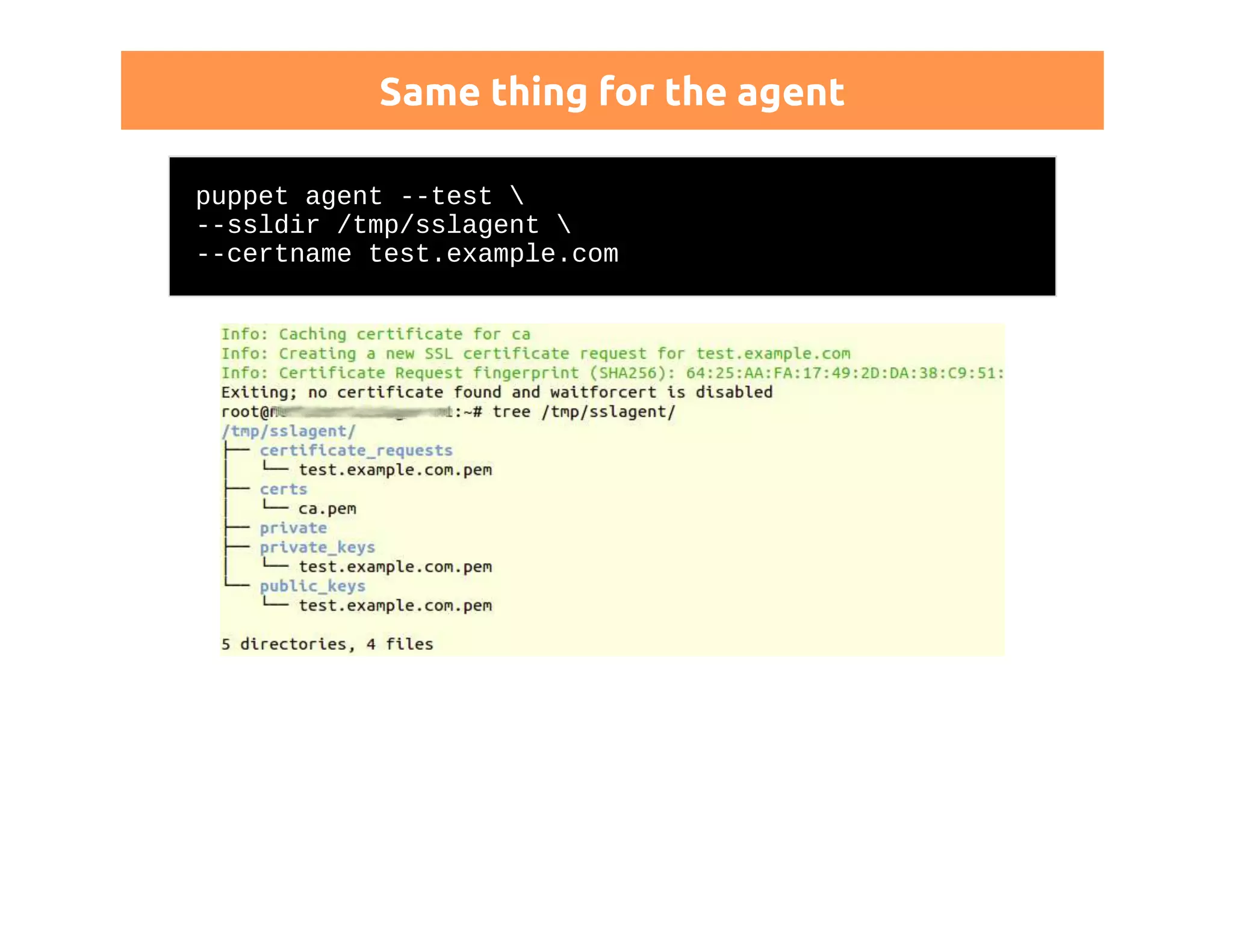
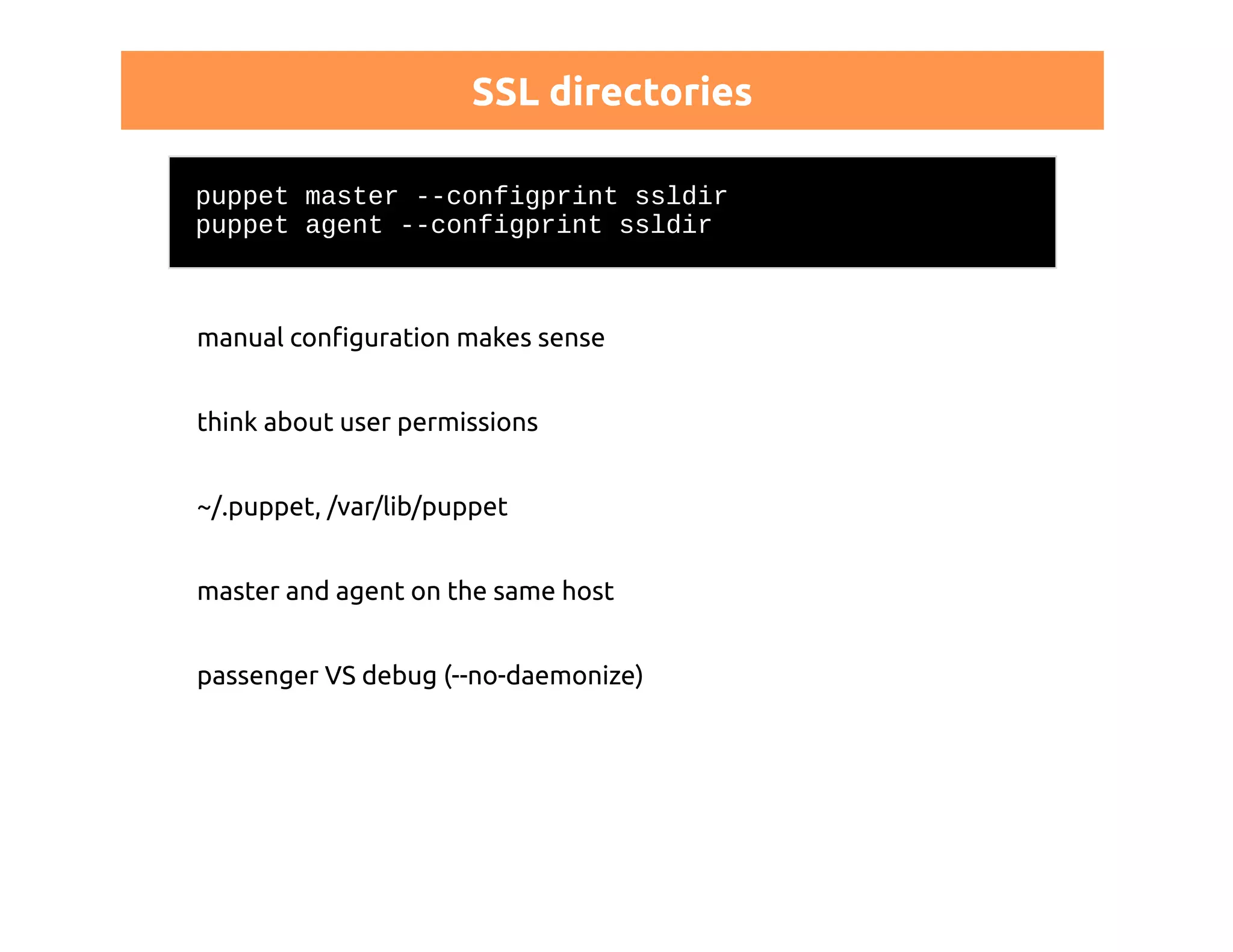
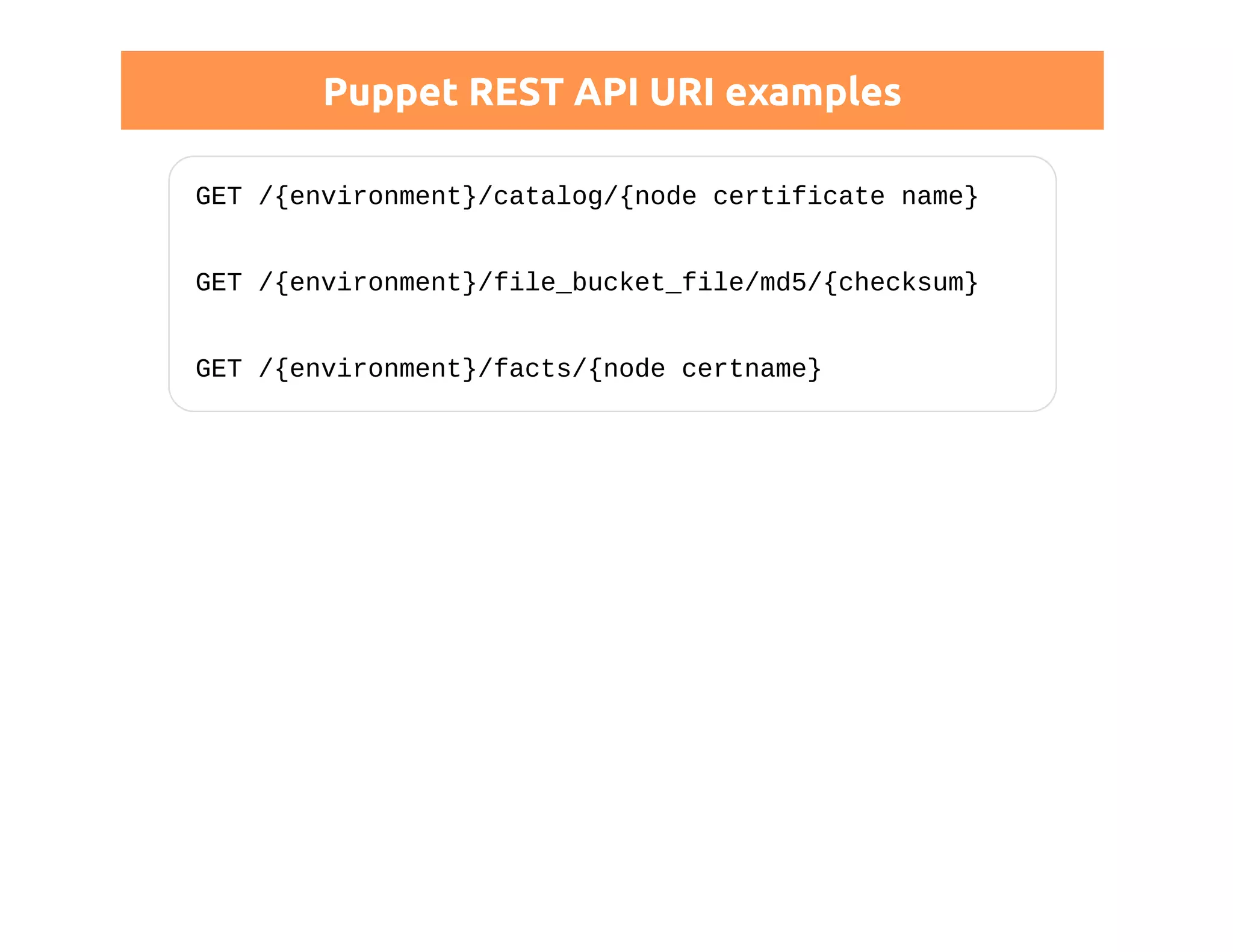
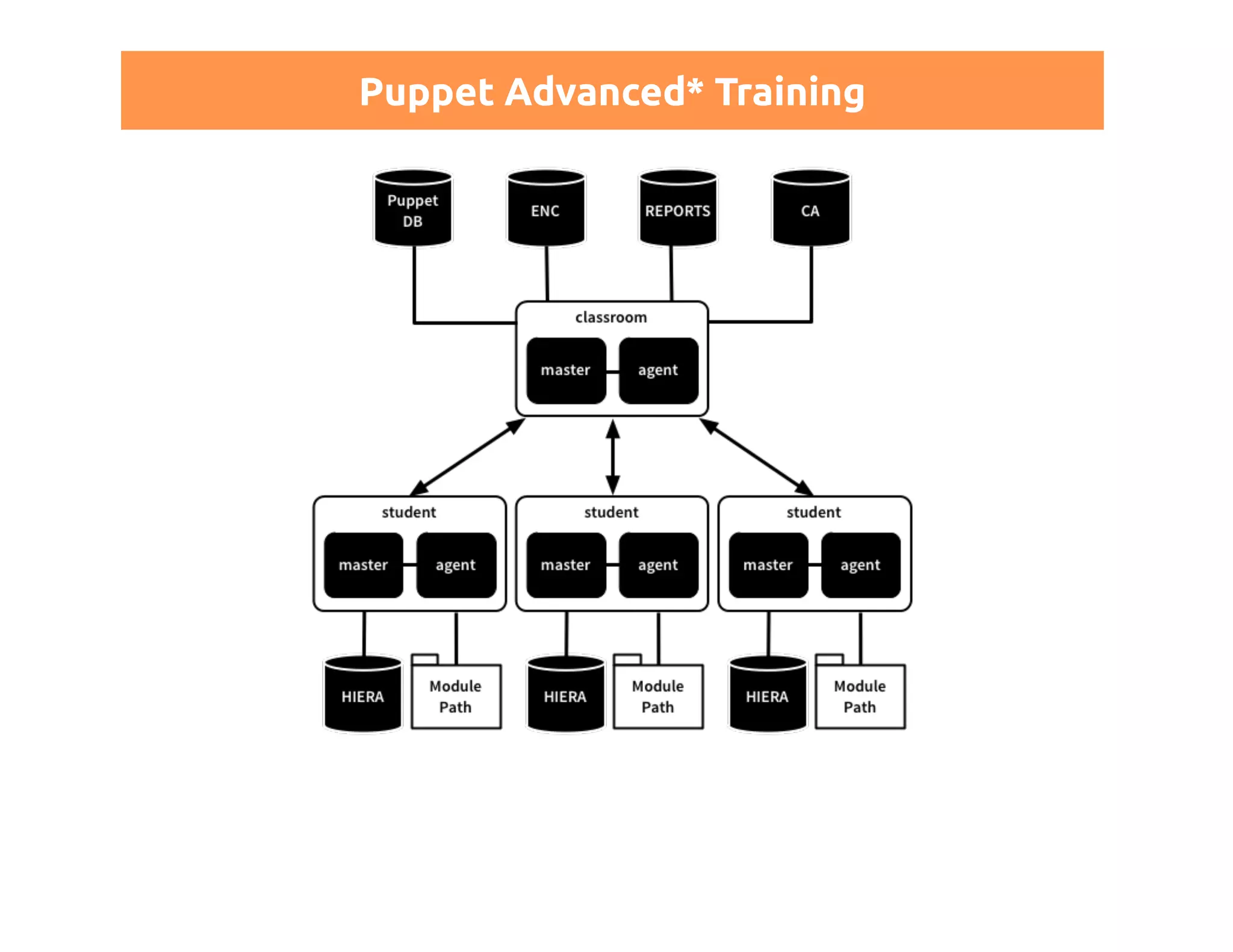
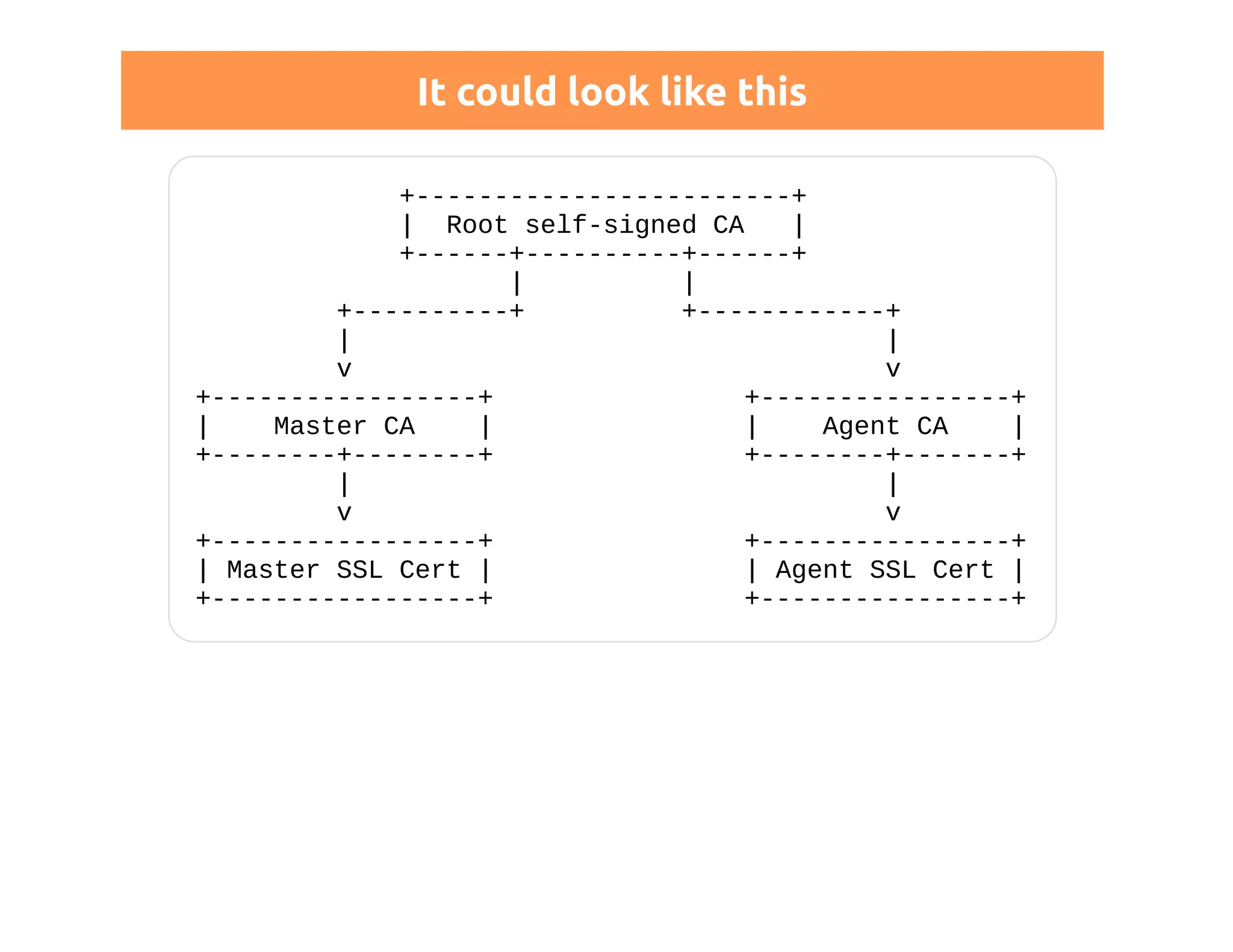
This document discusses certificates in Puppet and provides an overview of certificate management. It begins with an introduction to public key infrastructure (PKI) and the X.509 standard used by Puppet. It then covers Puppet certificate structures, filenames, and the REST API. The document also discusses setting up distributed Puppet environments with multiple certificate authorities and replacing a Puppet CA. It emphasizes the importance of security practices and guidelines for certificate lifecycle management.












![Permissions
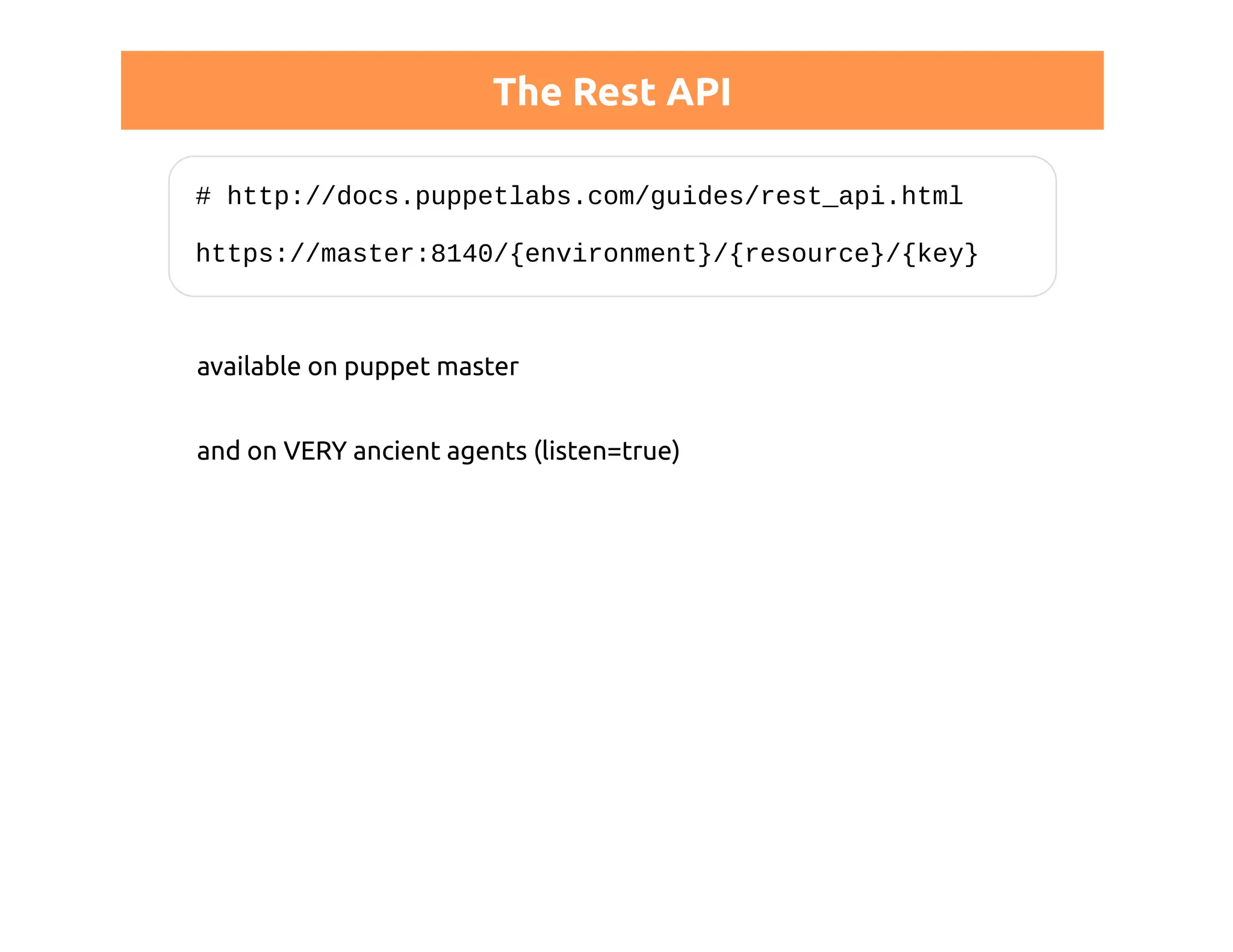
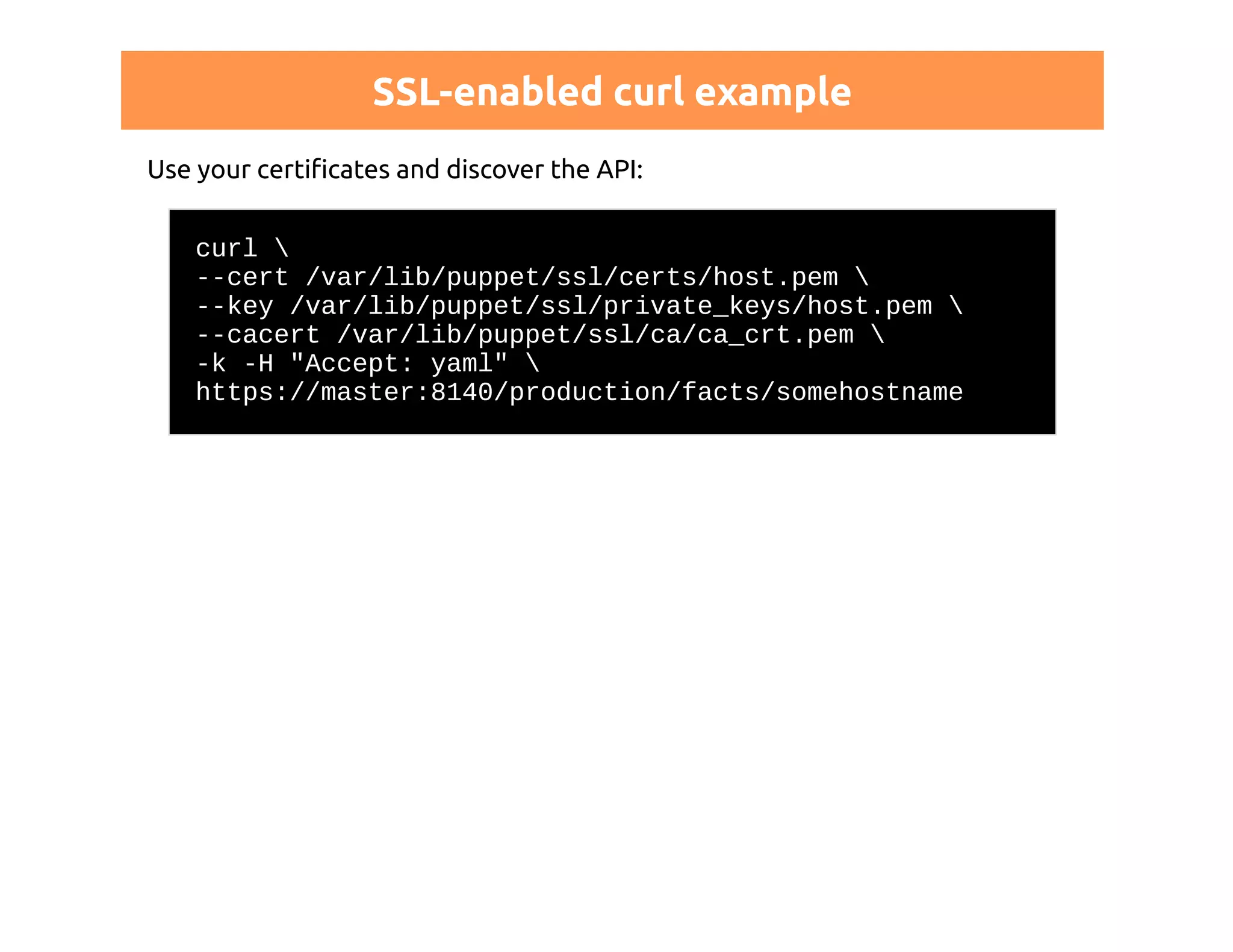
http://docs.puppetlabs.com/guides/rest_auth_conf.html
# auth.conf
# allow all nodes to store their own reports
path ~ ^/report/([^/]+)$
method save
allow $1](https://image.slidesharecdn.com/puppetca-certificatesexplained-141022185216-conversion-gate01/75/Puppet-Camp-Dusseldorf-2014-Puppet-CA-Certificates-Explained-36-2048.jpg)
![Configuration for such a setup
One CA is more than enough:
[master]
ca = false
[agent]
ca_server = ca.example.com
Optionally, still experimental: DNS SRV records](https://image.slidesharecdn.com/puppetca-certificatesexplained-141022185216-conversion-gate01/75/Puppet-Camp-Dusseldorf-2014-Puppet-CA-Certificates-Explained-40-2048.jpg)
![Chain of trust
Since 3.2.1 you can use intermediate CAs to delegate trust
# http://docs.puppetlabs.com/puppet/3/reference
# /config_ssl_external_ca.html
[agent]
ssl_client_ca_auth = $certdir/issuer.pem
Tell Apache about your chain:
SSLCertificateChainFile "/path/to/ca_bundle.pem"](https://image.slidesharecdn.com/puppetca-certificatesexplained-141022185216-conversion-gate01/75/Puppet-Camp-Dusseldorf-2014-Puppet-CA-Certificates-Explained-41-2048.jpg)





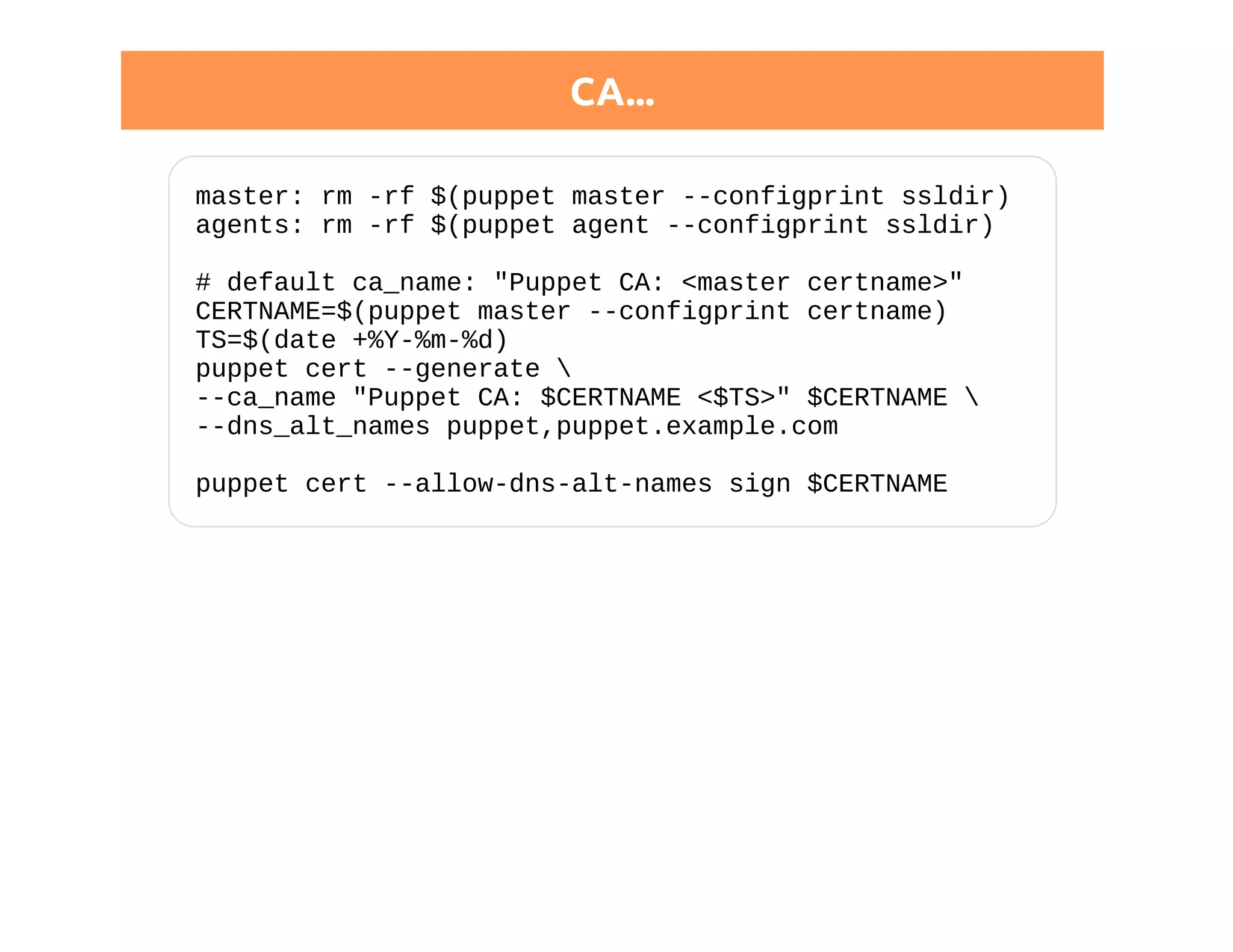
![Don't like trouble?
Before generating your CA:
[master]
ca_ttl = 20y
Leave your company in time
NB: expiration > 2038-01-19 == bad idea](https://image.slidesharecdn.com/puppetca-certificatesexplained-141022185216-conversion-gate01/75/Puppet-Camp-Dusseldorf-2014-Puppet-CA-Certificates-Explained-56-2048.jpg)