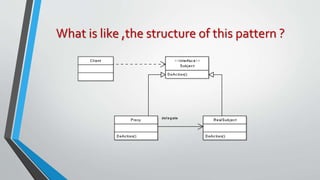
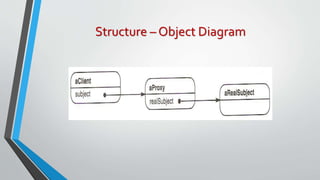
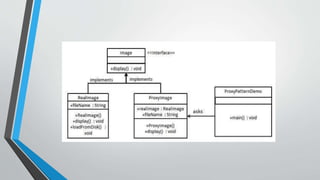
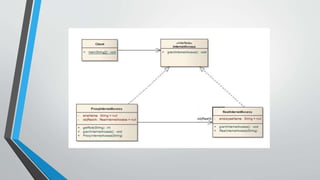
The proxy pattern provides a surrogate or placeholder for another object to control access to it. It is used when the real object needs to be accessed remotely, created on demand, or access control is required. The proxy maintains a reference to the real subject and provides the same interface as the subject so it can be substituted. There are different types of proxies like virtual, remote, and protective proxies that are used in situations like lazy loading large objects, accessing remote resources, and enforcing access control respectively. The proxy pattern structure consists of a proxy class that references the real subject and controls access to it through an identical interface.