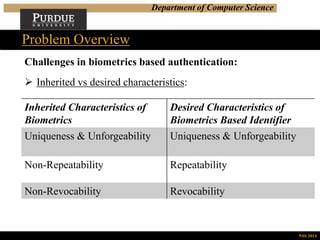
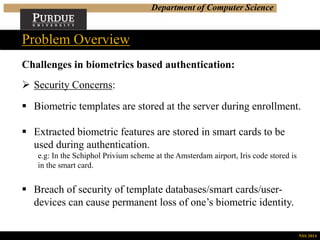
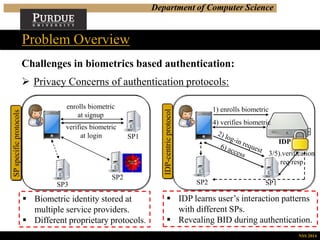
This document summarizes a research presentation on privacy-preserving biometrics-based authentication. It outlines the challenges with traditional biometrics schemes, including security and privacy concerns when biometric templates and identifiers are stored. The proposed approach generates unique, repeatable and revocable biometric identifiers (BIDs) using image hashing, classification and error correction. It also describes a user-centric, privacy-preserving authentication protocol using these BIDs and zero-knowledge proofs to authenticate users without revealing sensitive biometric data. Performance analysis shows the approach can generate commitments and run the authentication protocol efficiently. The work aims to address privacy and security issues while enabling convenient biometric authentication.




![Department of Computer Science
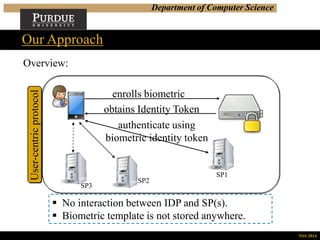
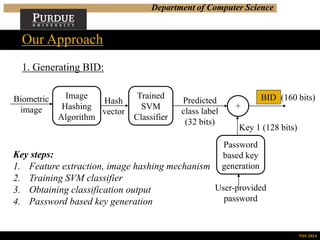
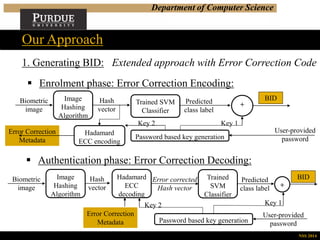
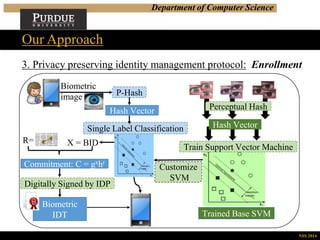
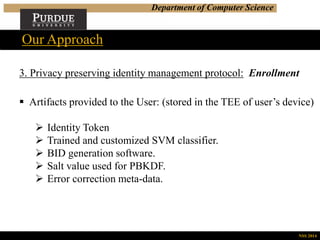
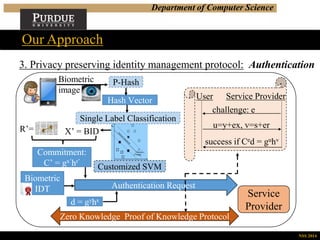
Our Approach
NSS 2014
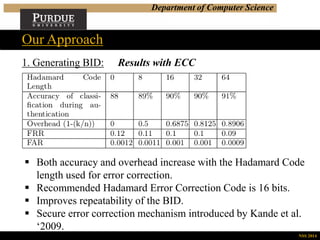
1. Generating BID: Results
P-Hash – feature
extraction mechanism
used in our approach.
SVD-Hash – feature
extraction mechanism
used in previous work
[Bhargav-Spantzel et al.
‘2010].](https://image.slidesharecdn.com/nss2014paper153-150817233720-lva1-app6892/85/Privacy-Preserving-Biometrics-Based-and-User-Centric-Authentication-Protocol-13-320.jpg)


![Department of Computer Science
Summary: Performance
Performance measure Value
Computing perceptual hash 0.0105 (s)
Training Classifier 8 (s) [with 400 training instances]
Predicting from trained classifier 0.013 (s)
Creating commitment 0.003038 (s)
Zero Knowledge Proof (without
network delay)
0.00763 (s)
Hardware Configurations:
CPU: Intel Core i7-3537U
Memory: 5GB RAM
OS: Ubuntu 13.4 OS
Our Approach
NSS 2014](https://image.slidesharecdn.com/nss2014paper153-150817233720-lva1-app6892/85/Privacy-Preserving-Biometrics-Based-and-User-Centric-Authentication-Protocol-21-320.jpg)