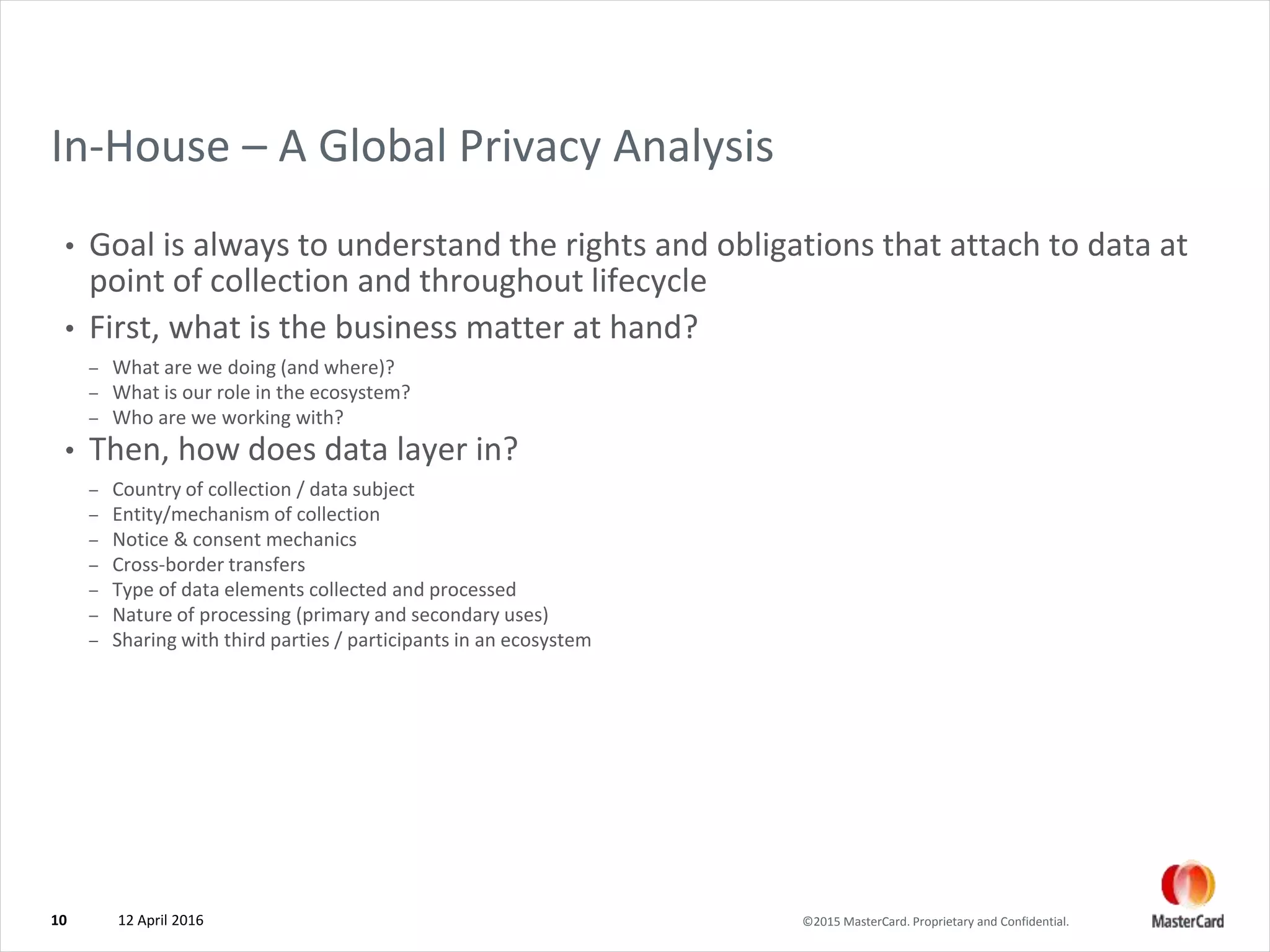
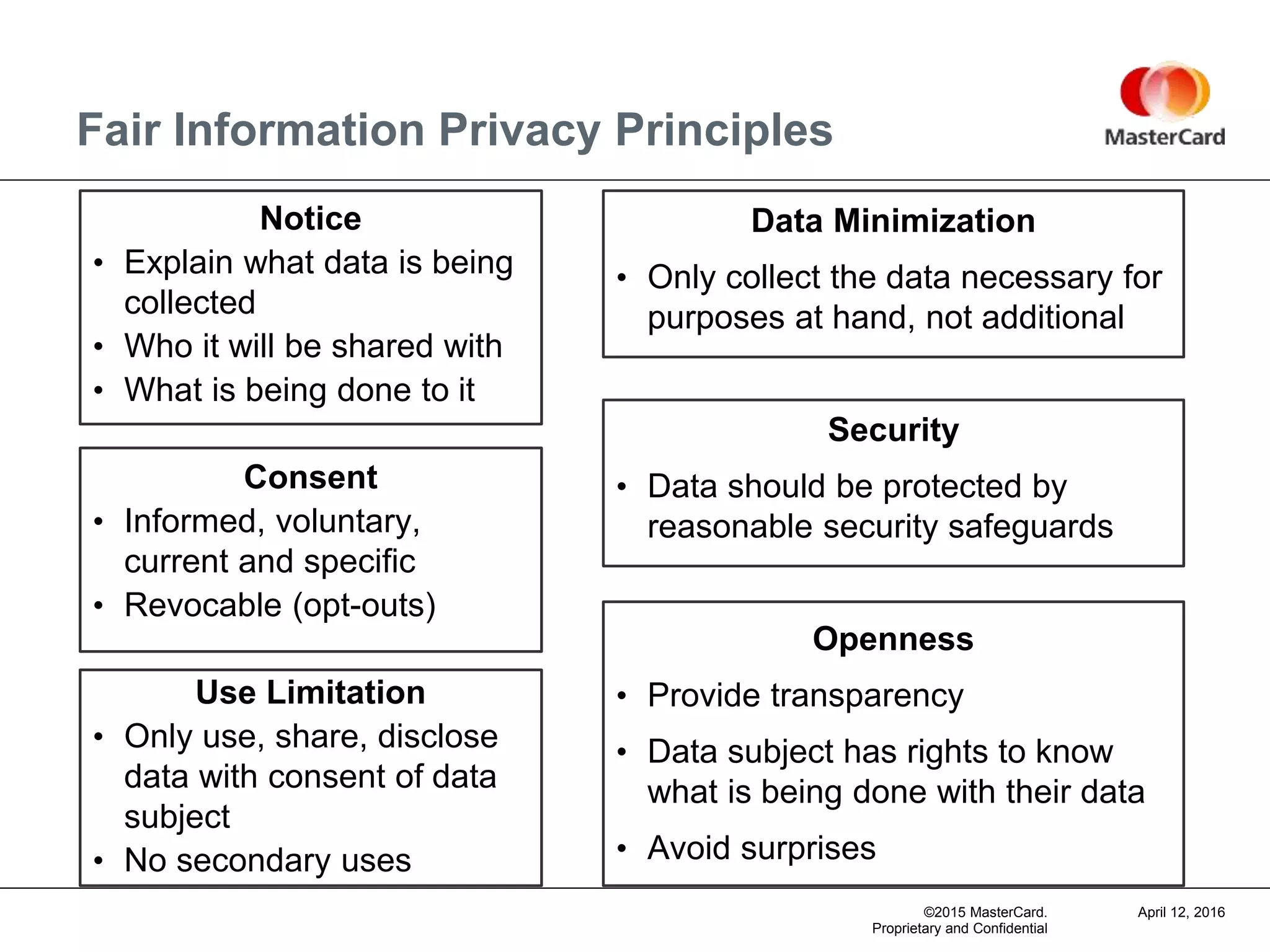
The document discusses mobile devices and the Internet of Things (IoT). It provides examples of IoT applications like smart homes, connected cars, smart buildings, and addressable medical devices. It notes both the promise and challenges of IoT regarding privacy and security. The document outlines a framework for analyzing IoT privacy sensitivity based on the level of direct action, decision making, and information sharing involved. It provides tips for successful IoT development, including mapping information flows, understanding rights and obligations, employing data minimization, conducting privacy and security assessments, and avoiding being "creepy." Resources on IoT privacy and security from organizations like the FTC, FDA, and EU are also cited.






![8Top 10 Practitioner Tips for IoT Success
• Tip: Map the personally identifiable information flows and
uses (common now), but also map other information that
could be used in analytics or otherwise combined to identify
a person (e.g., location/GPS, vital signs). [Debbie]
1. Map, Map, Map
• Tip: In IoT, information is collected and pulled in many more
directions than before and involves more parties. Mapping
now must also track the rights and obligations of each
involved party. [Seth]
2. Understand the Right and Obligations](https://image.slidesharecdn.com/benchmarkiotpresentationv2-160412195139/75/Mobile-Devices-and-Internet-of-Things-8-2048.jpg)


![12Top 10 Practitioner Tips for IoT Success
• Tip: In IoT, information is collected and pulled in many more
directions than before and involves more parties. Mapping
now must also track the rights and obligations of each
involved party. [Seth]
3. Privacy Notice Maybe Dead (or Morphing)
– How to Address in IoT
• Tip: New Technology needs new model to succeed.
Consider model for agency over permissions. [Jim]
4. Sharing and Notice](https://image.slidesharecdn.com/benchmarkiotpresentationv2-160412195139/75/Mobile-Devices-and-Internet-of-Things-12-2048.jpg)
![14Top 10 Practitioner Tips for IoT Success
• Tip: Employ data minimization and creativity for security
(e.g., keep information on the device, not networked).
[Debbie]
5. Know Where Your Data Is
• Tip: Work with engineers and set up escalation process for
sensitive activities. [Seth]
6. Privacy and Security By Design](https://image.slidesharecdn.com/benchmarkiotpresentationv2-160412195139/75/Mobile-Devices-and-Internet-of-Things-14-2048.jpg)
![15Top 10 Practitioner Tips for IoT Success
• Tip: For IoT security assessments, this is different than
historical, controls security assessments as the threat
surface and potential areas for vulnerabilities expands.
[Debbie]
7. Conduct a Cybersecurity and Threat
Assessment
• Tip: Privacy Impact Assessments (take many forms) are key
to identify potential repercussions of secondary and
unintended uses and consequences. [Jim]
8. Conduct a Privacy Impact Assessment](https://image.slidesharecdn.com/benchmarkiotpresentationv2-160412195139/75/Mobile-Devices-and-Internet-of-Things-15-2048.jpg)
![16Top 10 Practitioner Tips for IoT Success
• Tip: IoT often involves data processed, stored or analyzed in
the cloud. Be alert when data flows into many jurisdictions
outside of the US. [Seth]
9. Jurisdictions
• Tip: Avoid being creepy! [Jim, Debbie and Seth]
10. Business Judgment](https://image.slidesharecdn.com/benchmarkiotpresentationv2-160412195139/75/Mobile-Devices-and-Internet-of-Things-16-2048.jpg)


