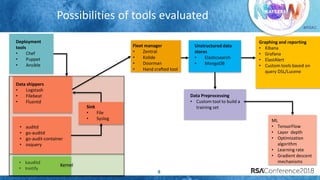
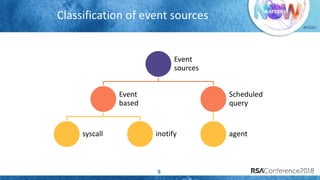
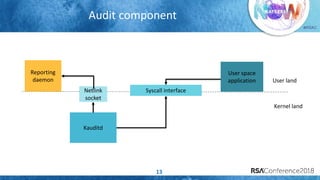
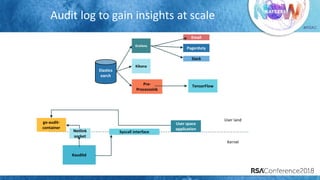
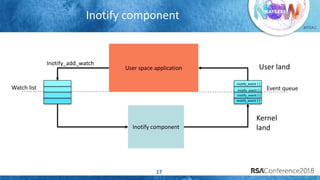
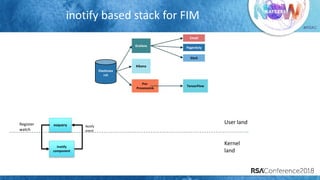
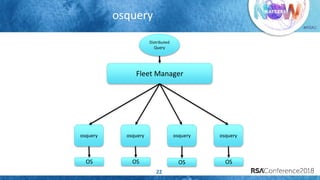
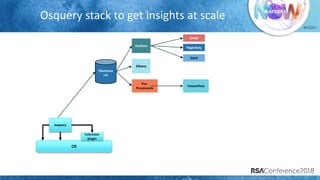
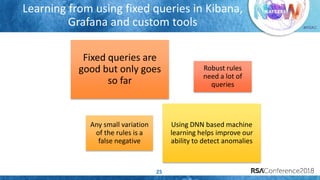
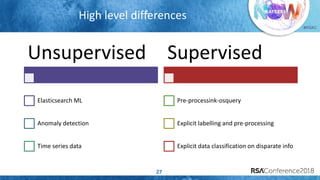
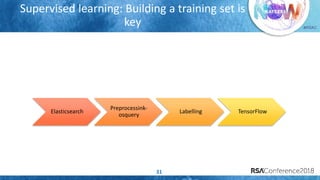
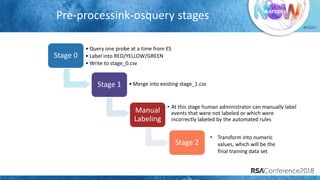
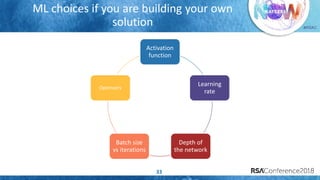
The document discusses system call auditing and file integrity monitoring in large container deployments, focusing on the challenges of processing vast log data and selecting appropriate open-source tools. It emphasizes the importance of classifying event sources and employing machine learning techniques to enhance anomaly detection while also evaluating various tools, frameworks, and stacks. The presentation also outlines a structured approach to build a custom monitoring stack based on security insights, highlighting lessons learned and future possibilities in the domain.